2 clients to connect to each other
-
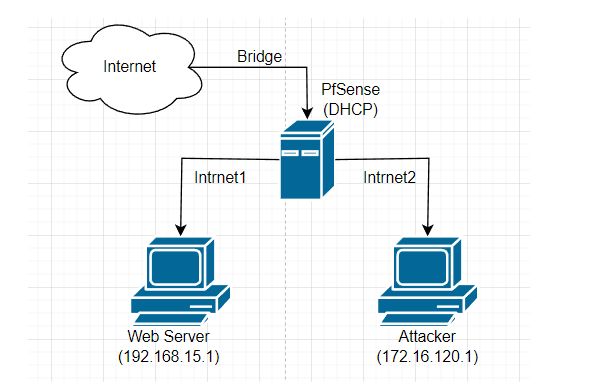
I have an example VM that I'm using, and the network settings are like this:
for this VM, pfsense can connect to any vm using the network interface provided by pfsense, but the vm client cannot connect to pfsense.
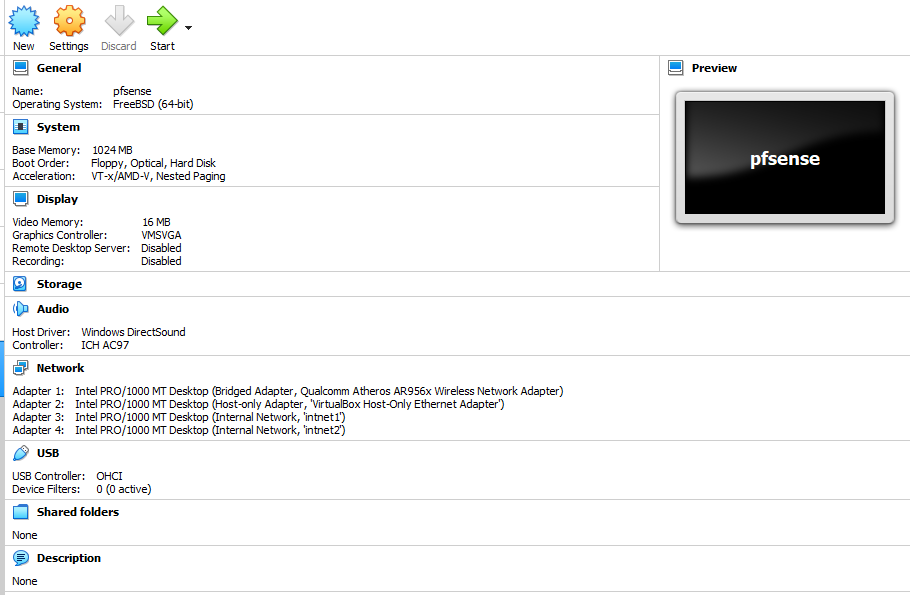
meanwhile, this VM is pfsense and interface "intrnet1" can connect and can access webgui, but interface"intrnet2" can't connect anywhere
-
Put this firewall rule on the "Intrnet2" interface :
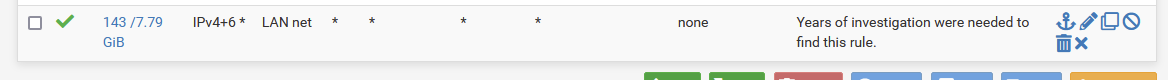
Where my image reads "LAN net" (Source) yours should read "Intrnet2"".
Now you can throw whatever on the device called "Web Server".
The other way around, on the Intrnet1 interface, put an identical rule.
This time Source would be "Intrnet1 net".edit : oh ... it's a pfSense in a VM.
That can add other, non pfSense related issues, of course. -
@ezvink said in 2 clients to connect to each other:
but the vm client cannot connect to pfsense.
Well what rules did you put on the new interface you created in pfsense?
Out of the box the "lan" network of pfsense has any any rules so it can go anywhere - but when you create a new interface/vlan there would be no rules. So no wouldn't be able to go anywhere, it would get an IP via dhcp from pfsense since when you enable dhcp on an interface, hidden rules are created to allow for that.
-
I didn't add any firewall rules on any interface, the firewall settings are still default
-
@ezvink well then no you wouldn't be able to go anywhere then.
The first interface "lan" default to any any, but as stated new interfaces have no rules - so deny is the default.. You need to add the rules you want on these new interfaces to allow the traffic you wan.
If you want both of your networks to freely talk between each other, then create an any any rule like is default on the "lan" interface.
-
@johnpoz
so what kind of firewall settings should i add sir? -
@ezvink Its your firewall, what do you want to allow.. See my edit, if you want free for all between your 2 networks - then any any would be the rule you would want. Like the default lan rule.
-
@ezvink said in 2 clients to connect to each other:
@johnpoz
so what kind of firewall settings should i add siLook above. You missed it.
-
@gertjan
which VM is it for sir? I have an example of 2 VMs and the network interfaces are different -
@ezvink said in 2 clients to connect to each other:
which VM is it for sir?
I don't know what your using .... I can't tell, you didn't mention.
I have this : https://docs.netgate.com/pfsense/en/latest/virtualization/index.html with some good examples.
-
@gertjan
I use both sir, I also ask which one is better than the network interface that I show -
@ezvink At a loss to what your asking.
If you have client A on Lan 192.168.15/24, and B on OptX 172.16.120/24 and you want to let B talk to lan, then you need rules on interface OptX to allow that
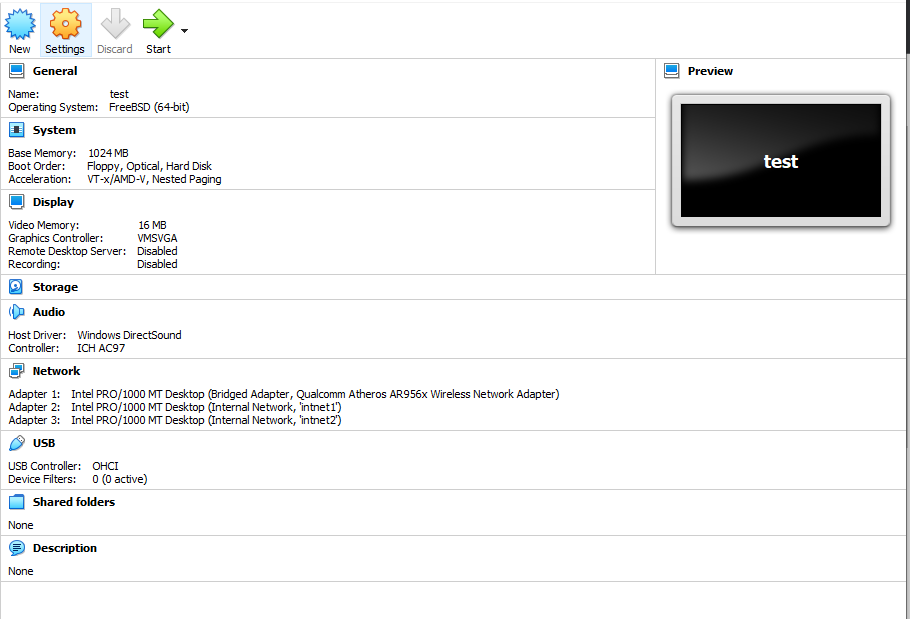
Looking at your vms, one is a pfsense with 4 different network connections, and then test with 3 connections.
If test is your client and you want this in your optX network, then it should only have 1 connection.
And on your pfsense do not understand why you would connect it to the virtualbox host only network?
Also your bridging some wifi adapter on your host? This more than likely going to be problematic in its own right.
-
The VBox 'bridge' interface type to wifi should be fine. It doesn't really care what the host NIC is.
However I would certainly use an Ethernet NIC on a VM host given the choice.As I read that the two examples given are both VMs to be used for pfSense and you are asking which would be better?
The answer there is they are both the same in a network topology view. One has the host-only adapter which, as we discussed at length, you don't need. But the only difference that makes is that because it's probably the LAN interface it has pass rules by default and no other interface does.
You need to add pass rules to the other interface(s) as described here.
Steve
-
@stephenw10 said in 2 clients to connect to each other:
The VBox 'bridge' interface type to wifi should be fine
Quite possible currently - but I do remember from back in the day that bridging a wifi adapter could have issues.. Depending on the nic, I believe some of the broadcom work, but I think they were doing something with arp-nat..
I haven't had to do any sort of bridging with wifi nics in really long time, but do recall depending on the actual nic, and drivers there could be problems with it.
I would use a wire on the host to get to the network.
-
Mmm, you could be right. I ran across a laptop running VBox in Windows that was doing exactly that quite recently and it worked. But I don't recall what the wifi hardware was. That might explain the difficulties connecting to the WAN via the bridge we saw previously.
Steve
-
@stephenw10 yeah like I said its be a coons age ;) since I have done anything with bridging wifi adapters.. But I do recall if all the stars were not aligned it was a big PITA, etc.
But many a moon ago I gave up all that nonsense and use a wire on anything that has a wire, and only thing that does wifi is APs (designed to do it) and mobile devices (phones/tablets) designed to use wifi.
Anything else has a wire.. My TV has a wifi adapter in it - and to be honest wifi prob be faster since its only 100mbps interface (cheap is the only reason these days).. But its a 55" tv - so its not like it moves so wire it is ;)
While working at home my laptop - again wired, because I am not moving about with it - its in my office where I work, so again wired! ;) Don't get me wrong I love wifi when its appropriate - but using a wire when you can sure cuts down on a lot of bs that can come from wifi ;)
-
[Off-topic] Yup, it kills me that I have wifi connected thermostats. They are screwed to the wall and always on the end of a wire.

-
@stephenw10 yeah same here.. Whats funny with mine is runs wire from the thermostat runs into the closet where the furnace is - and there it goes to a device on the wall that connects to my wifi.. Wish I could just plug a wire into that little box ;)
Just so stupid - its not like that is ever going to move about.. Your talking pennies to add a ethernet port, 10mbps would be all it needs..
-
@johnpoz
I want the attacker to be able to access the web server, sir, therefore the PC web server and the Attacker must be connected first, right?in a VM whose network interface has 3 interfaces, the pfsense web gui is accessed by the PC web server pak, therefore I think that I should add 1 more interface to control the web gui.
can you tell me what kind of rules so that what I want can happen? because I'm already confused, sir, looking at the video on YouTube it always can't run on my VM.
-
It's a VM : with a few clicks you can add a 4th interface.
Then start the VM, use the console access of the VM-pfSense to assign the interface to pfSense.
Connect to LAN inyterface, assign a pass-all firewall rule as mentioned earlier on the 4th interface.
You're done.Btw : yes, things will be way easier if you do not use a VM, but a bare bone PC, and a quad NIC Ethernet ports.