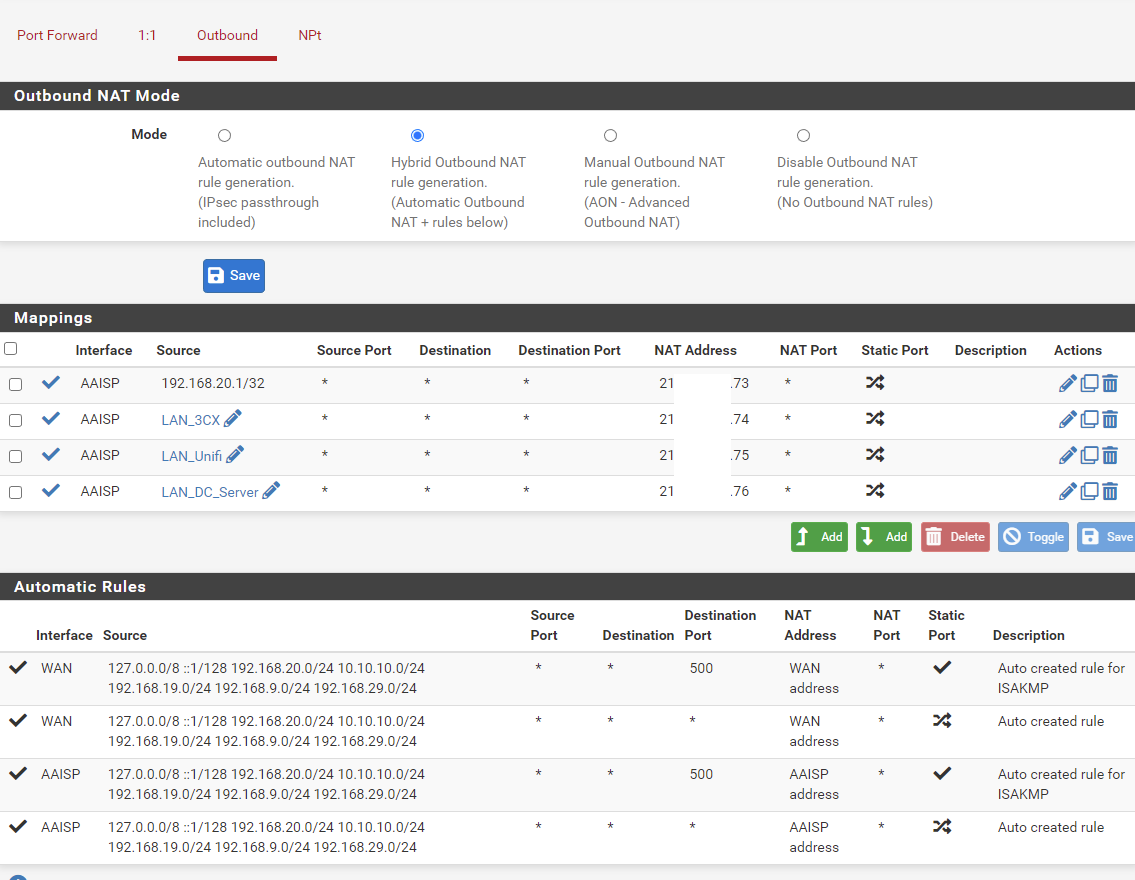
Outbound NAT
-
Help me out here I'm going around in circles.
I have an internet connection DHCP wan address all working ok.
I have a L2TP service that gives me a IP pool ie. 1.2.3.72/29
I can set the port forwards up inbound to allow services on them IP's to work but I want a number of devices on the network when they are outbound to get one of the IP's in the pool that I allocate as such.
i.e. voice 74, server1 75 and server2 76.
I have the virtual IP's setup, I have looked at 1:1 NAT but no joy, and outbound I have it set on hybrid but have tried auto, hybrid and manual and no joy. The 3 things I want to have an IP from that pool all sit on the same /24 network.
What am I missing here.
-
@mattl88 Can you post what you have? In essence, for hybrid, add one mapping:
interface: WAN
source: server_private_ip
NAT Address: .74And that's about it. Any open states may need to be deleted but new connections should go out on the .74 IP.
No rules are needed if using 1:1 NAT as that is automatic.
-
That is my current setup, the sources are just the IP's of the 3 servers for example, the top one is a test PC.
The interface is the L2TP tunnel.
-
@mattl88 And if you pull up a (new) web browser on the Windows DC and go to http://checkip.dyndns.com/ you get the WAN IP not .76?
How are the .73-.76 IPs configured on pfSense? As virtual IPs?
-
@steveits It shows my WAN address. All are virtual IP's.
Ok looking at this I might have done something stupid, my default gateway has been set to WAN address/automatic. If I change that to the L2TP it then gives me the right addresses.
Do I need to force all traffic out the L2TP tunnel as the default gateway?
Can I have different gateways for different devices?
-
@mattl88 I don't know if I've set up outbound NAT and multiple WANs. Huh.
pfSense has policy routing which I think is what you're looking for.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html -
@steveits That might just do it, thanks, will have a play with that, never noticed the option below regarding gateway on a rule. Just done some testing and looks good but need to do some more. Thanks for that.