2 clients to connect to each other
-
[Off-topic] Yup, it kills me that I have wifi connected thermostats. They are screwed to the wall and always on the end of a wire.

-
@stephenw10 yeah same here.. Whats funny with mine is runs wire from the thermostat runs into the closet where the furnace is - and there it goes to a device on the wall that connects to my wifi.. Wish I could just plug a wire into that little box ;)
Just so stupid - its not like that is ever going to move about.. Your talking pennies to add a ethernet port, 10mbps would be all it needs..
-
@johnpoz
I want the attacker to be able to access the web server, sir, therefore the PC web server and the Attacker must be connected first, right?in a VM whose network interface has 3 interfaces, the pfsense web gui is accessed by the PC web server pak, therefore I think that I should add 1 more interface to control the web gui.
can you tell me what kind of rules so that what I want can happen? because I'm already confused, sir, looking at the video on YouTube it always can't run on my VM.
-
It's a VM : with a few clicks you can add a 4th interface.
Then start the VM, use the console access of the VM-pfSense to assign the interface to pfSense.
Connect to LAN inyterface, assign a pass-all firewall rule as mentioned earlier on the 4th interface.
You're done.Btw : yes, things will be way easier if you do not use a VM, but a bare bone PC, and a quad NIC Ethernet ports.
-
@ezvink said in 2 clients to connect to each other:
can you tell me what kind of rules so that what I want can happen?
Have already stated this, any any rule would allow all access.. Just like the default lan rule.
-
@gertjan
so basically I just need to set up the LAN interface to add pass rules to all interfaces? like that sir? -
By default, when you install pfSense, and assigned a LAN (and a WAN) interface, the LAN interface has already the correct "pas-all" firewall rule.
On every other OPT1, OPT2 etc interface you create afterwards you need to create the same rule. -
@ezvink said in 2 clients to connect to each other:
so basically I just need to set up the LAN interface to add pass rules to all interfaces? like that sir?
The default lan rule already allows this.. What you need to do is setup the rule(s) you want on your new interface..
By default the lan interface has any any rule out of the box, when you create a new interface be it native or vlan there will be no rules on it. If you want devices on this network to be able to go anywhere you need to create rules to allow what you want, if you want devices on this network to be able to talk to any port/protocol on a device in lan - this would be a any any rule..
Just like the default lan rule.
Example - here is another interface on my pfsense, any client on this network can go anywhere they want, internet, my other networks, etc..
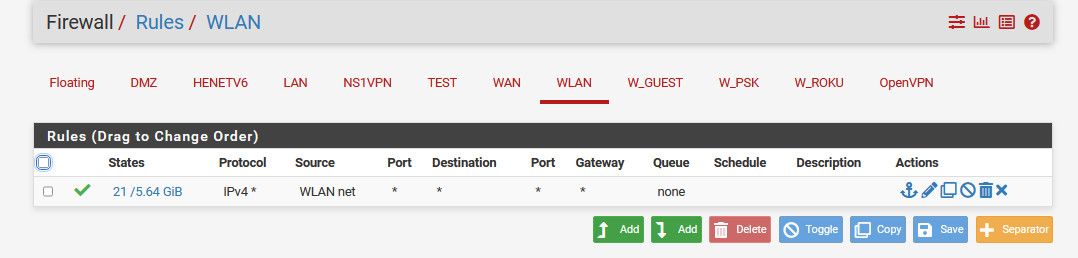
What rules you create is up to you, on what you want to allow or block.. But if there is no rules, then you can not go anywhere, default deny.
-
thank you sir, because the advice you gave I have done and it worked.
but if i add snort/suricata to pfsense and i will try to hack client IP 192.168.19.1 will the alert of hacking will appear in dipfsense?
-
@ezvink
If the 'hack' is matched by a rule set used by snort ( or surricata ) then yes. -
I've tried to hack into the webserver IP which is 192.168.20.5 while the one listed on pfsense is the webserver interface IP is 192.168.20.1, does that matter? because every time I hack the IP of the web server 192.168.20.5 it is not detected by suricata/snort
-
@ezvink From where - if your on the same network pfsense never sees that traffic.
If your using IPS, what do you have it running on what interfaces, what rules are you using in the IPS? As mentioned it can only detect what it has signatures for, etc.
What "hack" are you doing?
-
@johnpoz
IP webserver and Attacker are different sir.I added DDOS,ICMP,etc rules sir
I tried to do DDOS to the web server but it was not detected by Snort/Suricata.
I mean is it possible that the IP I'm supposed to be hacking is the IP listed on pfsense? but I've also added DHCP Server to the IP of the webserver pak and the host of the webserver gets the IP 192.168.20.5 while the IP listed in pfsense is 192.168.20.1.
Even when I did Nmap it wasn't detected, even though I managed to do the Nmap. -
@ezvink again what interface do you have IPS listening on? What specific rule(s) specific, what attack specific.. What specific dos attack did you send, 1 box isn't going to send a DDOS.. Could send some specific DOS attack, but not a ddos.. the first d stands for distributed.. Which normally means a volumetric sort of attack by flooding traffic.
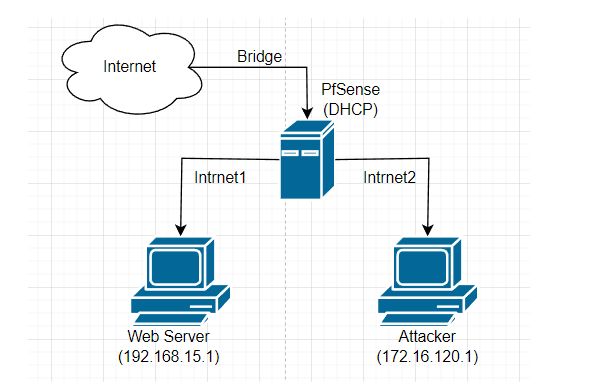
Where are you attacking from? In your first drawing your list 172.168.120.1 as attacker and webserver at 192.168.15.1
So you have your IPS on intrnet2 in your drawing?
If you have your networks setup and talking to each other now, and you want to ask other users of ips/ids how to "test" it and use it prob better off starting a thread in the ips/ids section of the forum
-
@johnpoz
sorry sir, I forgot to give the example, but the topology I made remains the same as drawn, it's just that I recreate the VM with a different IP.No sir, I installed the IDS/IPS on pfsense, and Snort/Suricata will secure the network (intrnet1), namely the web server itself.
I've added a topic to the link you provided, please respond back, sir