NAT Reflection and OpenVPN Help
-
Hi folks, So it seems that I have an issue with NAT reflection and I'm looking for guidance on how I need to fix it.
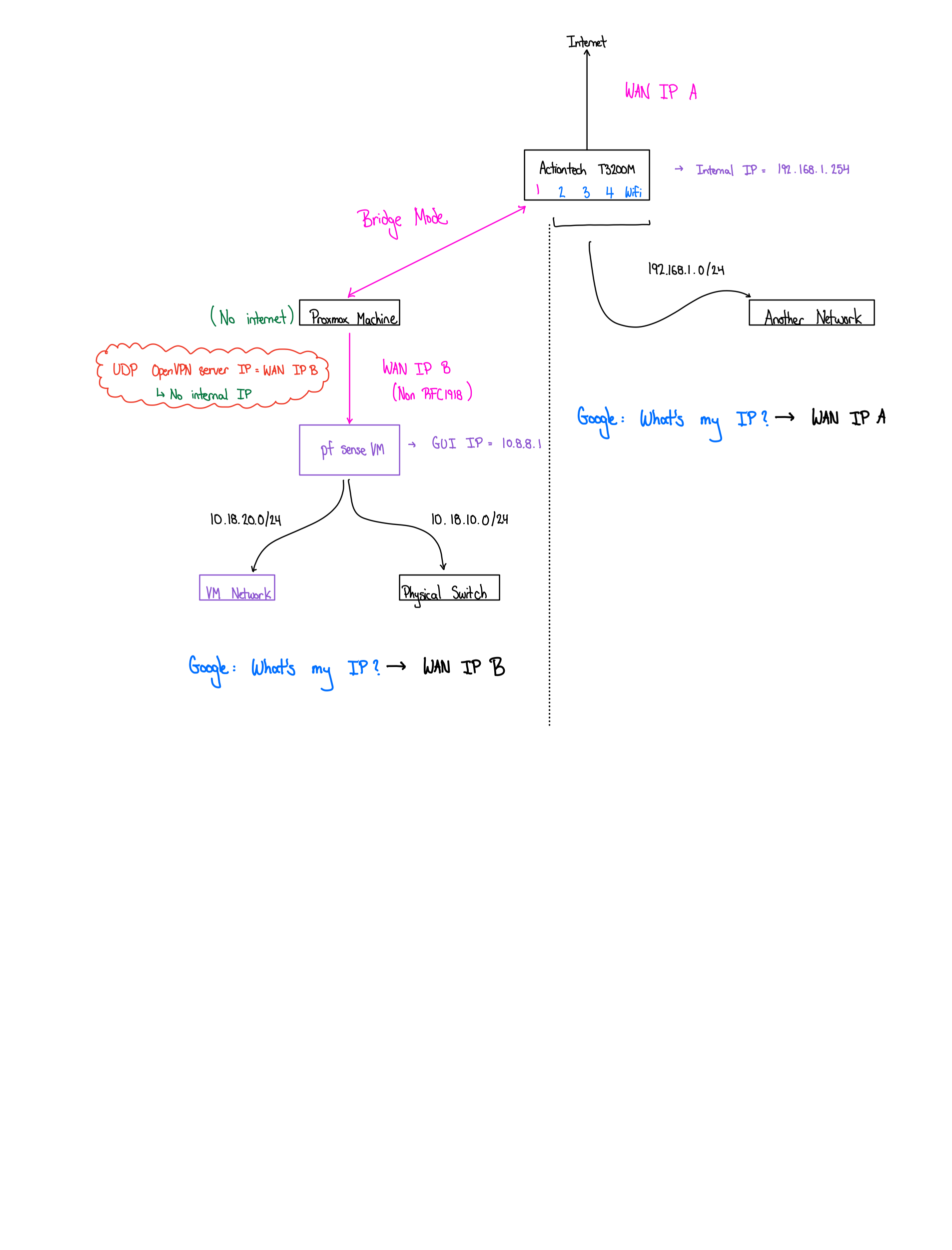
I made a post last week explaining how I am unable to connect to my pfSense OpenVPN server via UDP only (pfSense VM connected to port 1 of the ISP modem and in bridge mode) from devices connected directly to the ISP modem's other ports and wifi (outside of pfSense). I'm able to connect to my OpenVPN server just fine from other external networks as expected,
Anyways, I believe an issue relating to NAT reflection, and while the suggestion is to connect to the OpenVPN server's internal IP address instead of the WAN IP, I'm actually not quite sure how to do this, because as far as I know, the OpenVPN server does not have an RFC 1918 address.
I've come across an older post here explaining that I may be able to use 1:1 Nat rules to work around this, but I'm not at that level of understanding to know how to create these rules.
I've also included a picture of my setup here:
Any help is greatly appreciated.
Thanks!
-
@teddy-0
If it's a NAT reflection issue, it's on your ISP router, not pfSense.Check how the packets from the ISP router arrive on pfSense. Which source IP do they have?
If they are not natted on the router you can possibly enable this or solve it with a static route on pfSense. -
@viragomann Thanks for the reply. I neglected to mention this, but the ISP has disabled any NAT reflection settings on the modem
The source IP is the WAN IP from the ISP modem (so WAN IP A in the drawing in my OP).
To clarify since I'm still pretty new to networking in general: If I were to create a static route, I'd just set the destination network to be the WAN IP of pfSense via the WAN DHCP?
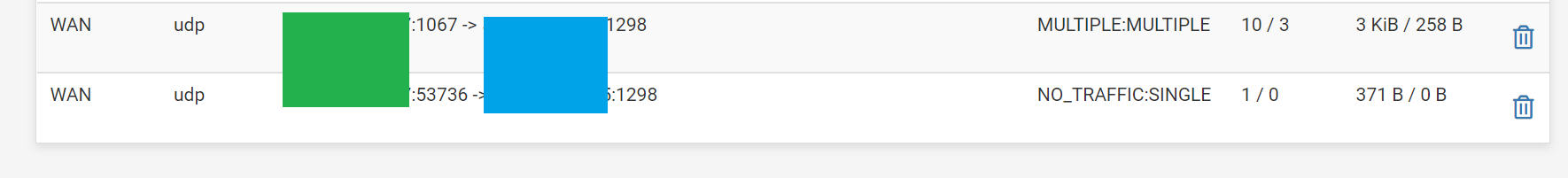
Here's a picture of the states table:
- Green = WAN IP A
- Blue = WAN IP B
- Port number of source IP (so WAN IP A) changes midstream for whatever reason
-
@teddy-0
Is the routers WAN IP within the subnet of the pfSense WAN IP?.How is the WAN IP on pfSense set? Is it DHCP or static?
What is the gateway on pfSense?Do you see the routes WAN IP in the ARP table on pfSense (Diagnostics > ARP table)?
-
@viragomann said in NAT Reflection and OpenVPN Help:
Is the routers WAN IP within the subnet of the pfSense WAN IP?
No it isn't.
- ISP combo router WAN IP (/22): 75.x.x.x
- pfSense router WAN IP (/22): 50.x.x.x
How is the WAN IP on pfSense set? Is it DHCP or static?
DHCP
What is the gateway on pfSense?
50.x.x.1
Do you see the routes WAN IP in the ARP table on pfSense (Diagnostics > ARP table)?
I'm not entirely sure what you mean by 'routes WAN IP', but if you're referring to either the WAN gateway and/or the WAN interface IP, then yes, I see the WAN gateway and WAN interface IP
On the ISP modem's ARP table, I see its WAN gateway (75.x.x.1)
-
@teddy-0 said in NAT Reflection and OpenVPN Help:
Do you see the routes WAN IP in the ARP table on pfSense (Diagnostics > ARP table)?
It should have been "the ISP routers WAN IP".
On the ISP modem's ARP table, I see its WAN gateway (75.x.x.1)
If not, all traffic between the two WAN has to flow over the ISP network. You can verify by tracing the packets to the other IP.
Possibly the routing does not work due to a failure in the ISPs network.To investigate sniff the traffic on the WANs, while you try to establish a VPN.
Maybe it could be a workaround to assign an additional private WAN IP from the routers network on pfSense. You can try it. Firewall > Virtual IPs, use type IP alias and set the network mask properly.
Just allow ping on it and check if it responses. -
@viragomann Again, I appreciate the help
Yeah, I don't see the 75.x.x.x IP on the ARP table of pfSense
If not, all traffic between the two WAN has to flow over the ISP network. You can verify by tracing the packets to the other IP.
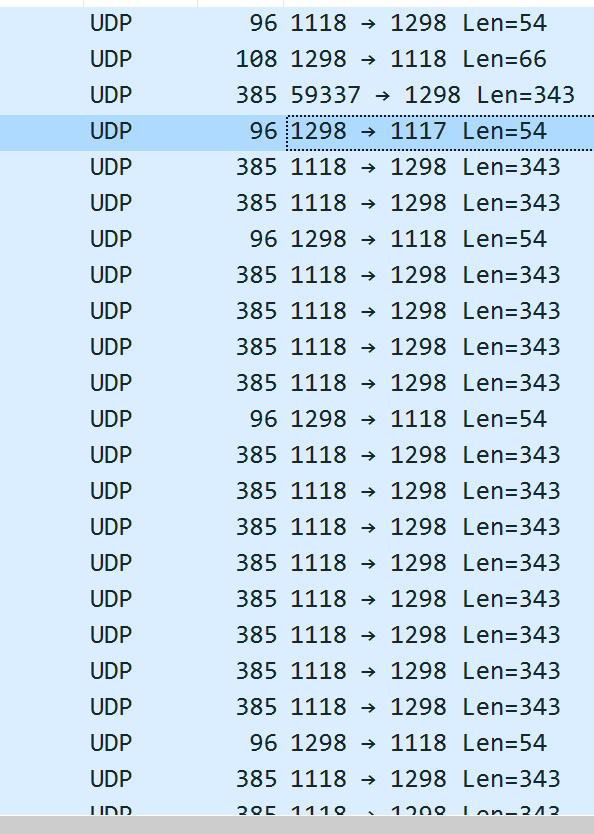
Possibly the routing does not work due to a failure in the ISPs network.So I just did a packet sniff on pfSense to show everything from the WAN IP address 75.x.x.x. I did this for both TCP and UDP, but I'm not actually quite sure how I'd determine if it's actually going out over the ISP network (even if this is actually what it's doing)
As I said earlier, I can connect to the VPN server via TCP on a device in the ISP's network, but with UDP, it's like pfSense is barely sending anything back:
Just to compare, I also connected to my VPN server via UDP on a different mobile network (which again, does work), and the back and forth was a little more even:
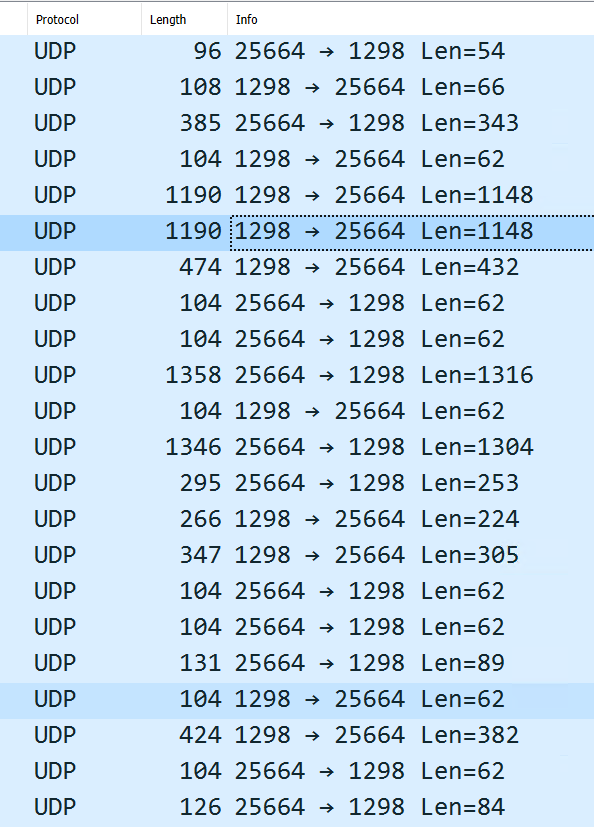
As for the Virtual IP, I'll need to do a bit more research since I'm not too familiar with what these are used for, but it didn't seem like it worked. In fact, I was no longer actually able to connect to my VPN server via TCP from a device on the ISP's network.
-
@teddy-0 said in NAT Reflection and OpenVPN Help:
but I'm not actually quite sure how I'd determine if it's actually going out over the ISP network (even if this is actually what it's doing)
You can see the destination address on the right. If this is not affected by a special route it is directed to the default gateway. What's the case can be seen in the routing table.
If you WAN is an L2 you would also see the MAC address in the capture, when running with high details.
As I said earlier, I can connect to the VPN server via TCP on a device in the ISP's network, but with UDP, it's like pfSense is barely sending anything back
Yes, I noticed this and it's quite strange to me. I'd had ideas for reasons if it would behave the other way round.
Just to compare, I also connected to my VPN server via UDP on a different mobile network
Since you don't provide IP addresses, I'm missing the needed information to investigate.
-
So I just took another look and I think I can confirm that the packets do go back over the ISP network (because I see that the packets try to go through my ONT in both directions) - thanks
Yes, I noticed this and it's quite strange to me. I'd had ideas for reasons if it would behave the other way round.
The main reason why I tried TCP in the first place was because I saw this post on serverfault.
I don't think the scenario is quite the same, but it's the only thing I've found on the internet that had any semblance to my issue (where the port #s change):
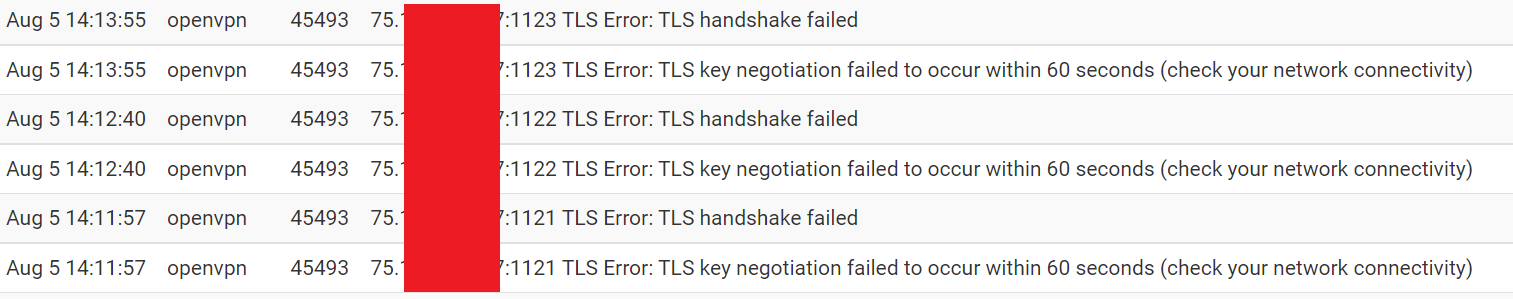
Since you don't provide IP addresses, I'm missing the needed information to investigate.
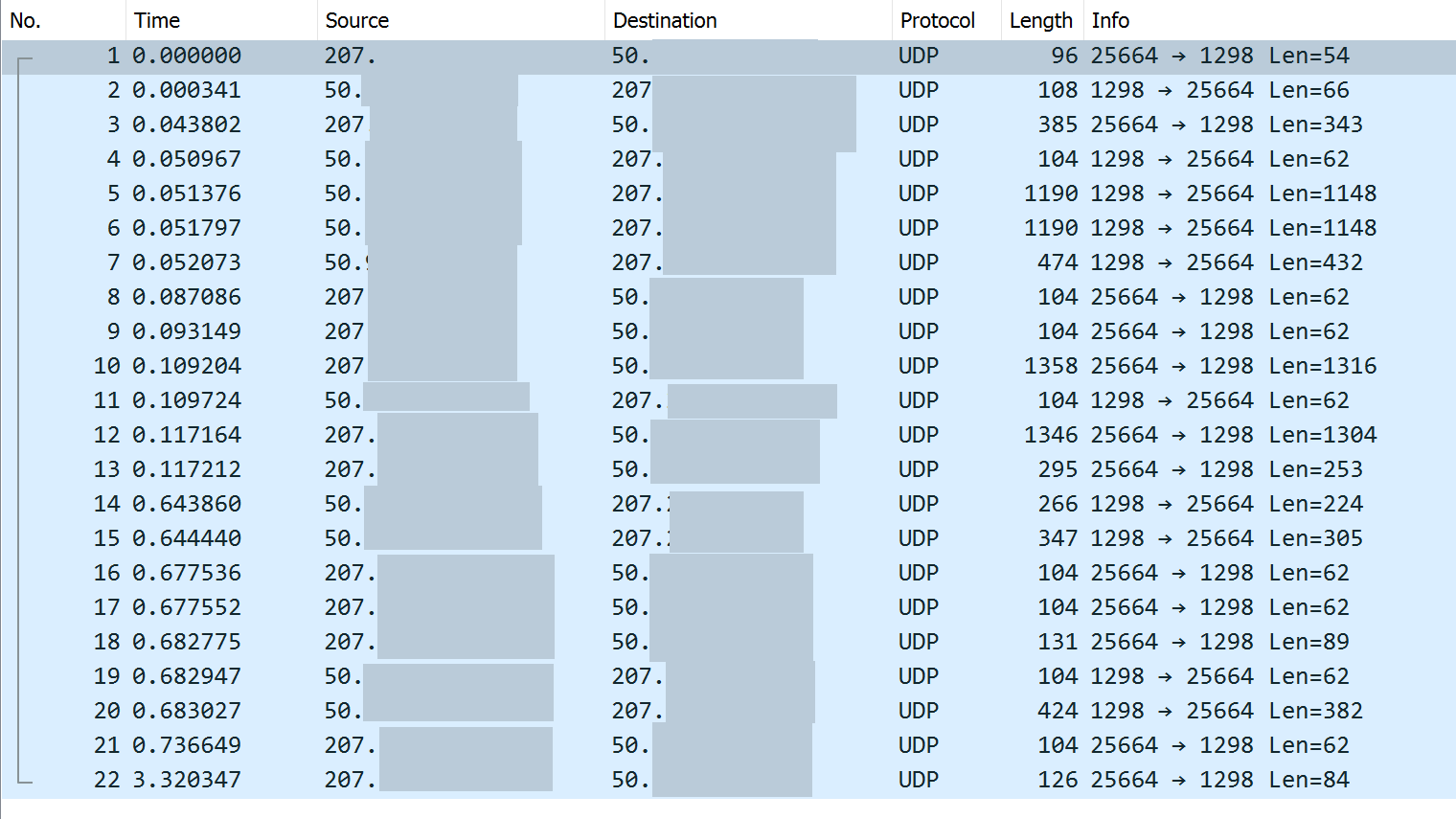
Here's the previous packet capture of when I tried to connect to the VPN server from within the ISP network (where pfSense WAN IP is 50.x.x.x, the ISP WAN IP is 75.x.x..x):
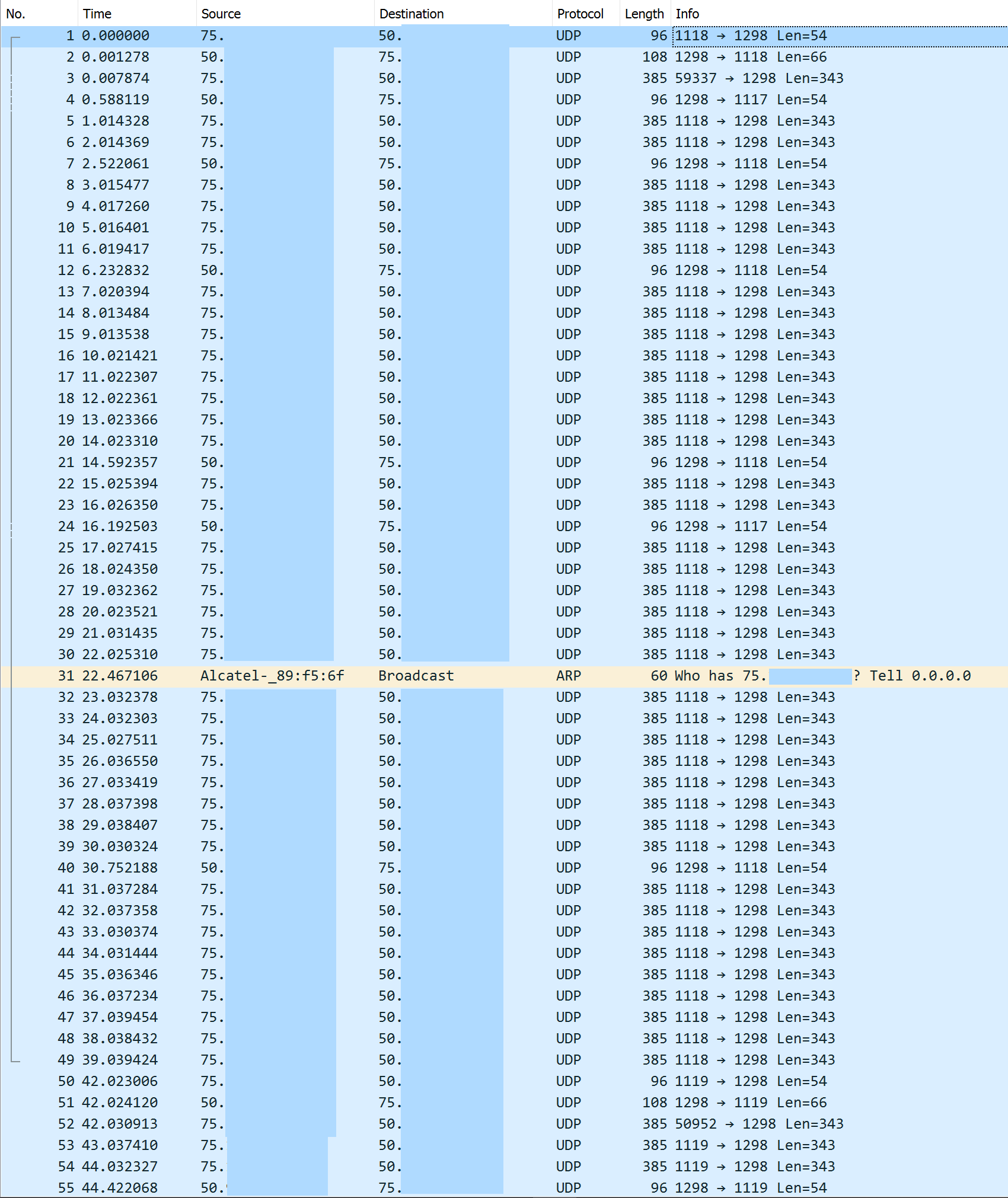
And here's the packet capture when I connect to the VPN server from an external network (where 207.x.x.x is the IP of the external network):