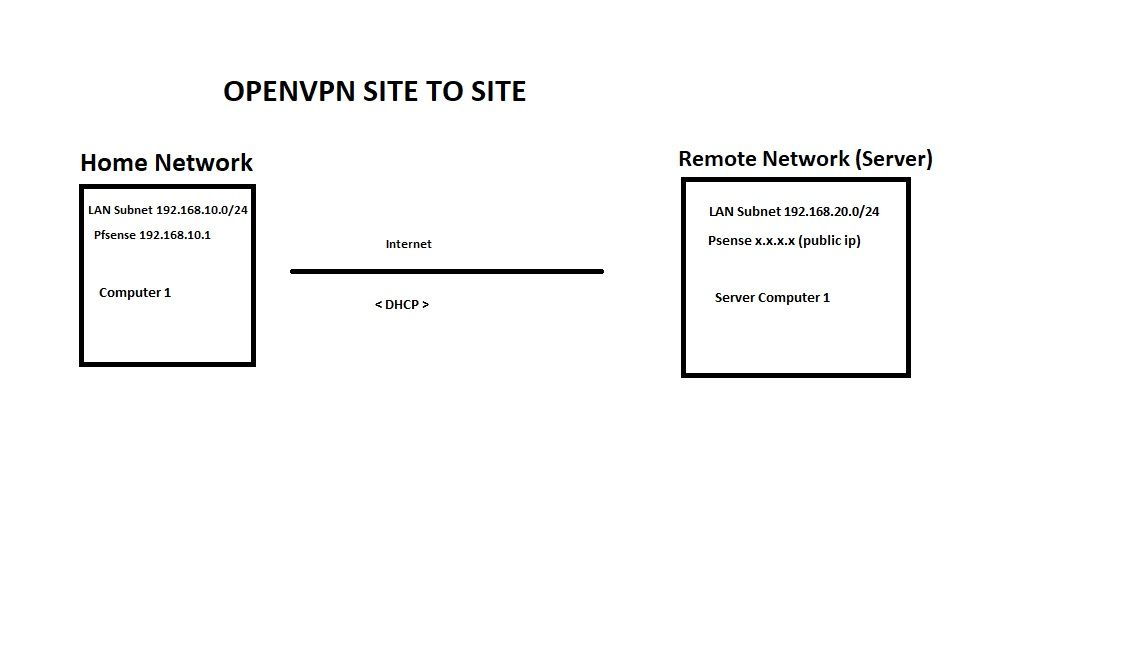
OpenVPN Site to Site
-
@brandon-lizard Do you have another interface on the remote site? You can bridge that with the vpn and set it with the same network as your home.
-
@jarhead Yes I do. Is it possible to create a vlan on my home side instead of allowing access to all of my network? I just want certain computers to be able to communicate with the remote server and be able to dhcp.
-
@brandon-lizard You can do that. Make the vlan the same subnet as the remote site if you can move those computers to a different vlan.
One thing, I don't have my tap vpn up at the moment but I do remember I had to enable the "Bridge dhcp" option to get it to work. Might wanna try it if it doesn't come up. -
@brandon-lizard It's starting to come back to me now... what I believe I did was, on the server side, enable bridge dhcp, and select the lan as the bridge (you still have to create the bridge, this doesn't do that), then set the range to one ip. The client side vpn interface will receive that address (server side will stay without an IP), and you'll be set.
Just to add, all other clients on my client side were statically assigned. You may have to expand the dhcp range if needed.
-
@jarhead Thank you. Here's what it sounds like I need to do.
- Setup openvpn in tap mode. Both sides need to be on the same subnet.
- Setup bridge mode on openvpn and lan interfaces
- Enable bridge dhcp
Firewall rules - Allow * on openvpn, Allow * on Lan.
Is there a good tutorial on this setup out there?
-
@brandon-lizard https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-bridged.html
-
@jarhead Say I created a VLAN on my home network switch. How would that work with pfsense?
-
@brandon-lizard You would create VLAN tags on pfSense and create interfaces out of those VLANs.
-
@brandon-lizard If this whole project is something you're just doing as a test, my need for a tap also needed 3 different vlans. I was able to trunk the tap and send all 3 (or more, tried 5) vlans over the vpn.
I was surprised it actually worked but I think the stigma around tap vpn's had a lot to do with the actual internet connection. It worked great for me with a 500M fiber connection on both ends and my ping time only increase by 3 -10ms when using the "other" side.
-
@brandon-lizard said in OpenVPN Site to Site:
Yes, dhcp is running on the server side.
But it is actually running on pfSense or on some other server at that site?
You might want to look at running a DHCP relay instead.
Steve
-
@jarhead said in OpenVPN Site to Site:
I was surprised it actually worked but I think the stigma around tap vpn's had a lot to do with the actual internet connection. It worked great for me with a 500M fiber connection on both ends and my ping time only increase by 3 -10ms when using the "other" side.
This is very true. Most of the bad rep TAP gets if from people who set it up over a >100ms link and then hit issues when the broadcast domain includes that.
It's possible to do some interesting combinations of routing over TAP with some manual editing. That can be useful.
Steve
-
I have got it working. I am able to pxe boot from to a server on the remote network. However the tftp is super slow. How can I speed that up?
-
How slow? What's the latency to the server?
What bandwidth do you see across the tunnel for other protocols?
TFTP is a basic protocol, there's not much you do there.
-
@stephenw10 I am not sure exactly where to look for that information. The server on my remote side runs a custom linux operating system and has a dhcp, pxe and tftp server.
Here is my setup:
Client Computer -> VLAN Switch -> Local Pfsense Firewall -----> OPENVPN TAP ------> Remote Pfsense Firewall -> Remote Lan with server -
When you say it's 'super slow' what are you actually seeing?
If you ping the server across the tunnel what are the ping times?
Steve