Cloudflare "reserved IP" records not resolving on pfSense DNS server
-
Hi everyone,
In order to get some certificates to work on my local network, I've created some A records on my cloudflare DNS which point to IPs on private address ranges.
eg. example.domain.com / 10.0.0.1 / DNS only - reserved IP
DNS Query Forwarding is enabled on pfSense.
When I try and resolve the record by pinging the FQDN, pfSense doesn't resolve it. Interestingly, the record can be resolved at any of the major DNS servers: 1.1.1.1, 8.8.8.8 etc.
Any DNS experts who could help me out with this please? Many thanks in advance.
dig @10.11.12.1 example.domain.com.au ; <<>> DiG 9.10.6 <<>> @10.11.12.1 example.domain.com.au ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4737 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;example.domain.com.au. IN A ;; Query time: 10 msec ;; SERVER: 10.11.12.1#53(10.11.12.1) ;; WHEN: Fri Aug 05 12:33:10 AEST 2022 ;; MSG SIZE rcvd: 48dig @8.8.8.8 example.domain.com.au ; <<>> DiG 9.10.6 <<>> @8.8.8.8 example.domain.com.au ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58881 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;example.domain.com.au. IN A ;; ANSWER SECTION: example.domain.com.au. 300 IN A 10.11.12.5 ;; Query time: 28 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Fri Aug 05 12:34:20 AEST 2022 ;; MSG SIZE rcvd: 64 -
@gyrex well that would be a rebind - and in general a bad idea. So no unbound would not provide that answer, since rebind protection is on. You would have to turn off rebind, or set the domain to private to allow rfc1918.
It is not a good idea ever to have public dns resolve to rfc1918 space.
What do you think that would accomplish exactly even?
If you want whatever fqdn to resolve to local rfc1918 address on your network, just setup a host override for that fqdn so your local clients resolve the local address.
https://www.ietf.org/proceedings/52/I-D/draft-ietf-dnsop-dontpublish-unreachable-01.txt
https://www.rfc-editor.org/rfc/rfc1918.html
If an enterprise uses the private address space, or a mix of private and public address spaces, then DNS clients outside of the enterprise should not see addresses in the private address space used by the enterprise, since these addresses would be ambiguous. -
Thanks for your comprehensive response, I really appreciate it.
@johnpoz said in Cloudflare "reserved IP" records not resolving on pfSense DNS server:
What do you think that would accomplish exactly even?
I did this so that LetsEncrypt can authenticate a public DNS record and I could issue a certificate to a web server running locally on private address space.
@johnpoz said in Cloudflare "reserved IP" records not resolving on pfSense DNS server:
If you want whatever fqdn to resolve to local rfc1918 address on your network, just setup a host override for that fqdn so your local clients resolve the local address.
I figured this would be the solution, thanks again.
-
@gyrex your saying that acme put in a SAN for the rfc1918 IP? Or it just has the fqdn on the cert..
-
-
@gyrex I will have to try out this app - forcing or requiring a public cert seems counter productive, since many a proxmox server, especially the admin of such server would never be available publicly.
When I get a chance tmrw will try it from chromebook using the app and see. Since it seems that app is only available for android
-
@gyrex well my proxmox box is booting but installed the app on my chromebook - and would seem all you have to do is turn off ssl validation.
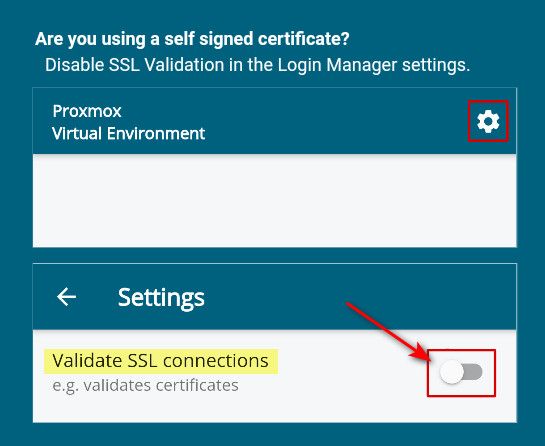
It runs thru this info when you first launch the app.
Ok was able to connect right to my proxmox just using the IP..
I was also able to use host name prox.local.lan once I enabled my dns to resolve that.. I have installed my CA into my chromebook, and it works for my nas via just chrome.. Lets see if can install cert on proxmox and see if app trusts it. Be back in a bit.
edit: well back - while I could get chrome in the chromeOS to trust the CA for the proxmox.. The app doesn't seem to like it when turning on validate ssl.
I don't know enough about chromeOS as of yet, just got the chromebook for the wife a few days ago.. But turning off validate ssl works just fine be it with fqdn or just IP.. If your just internally using it, I don't see why what wouldn't be an option.. For sure the simpler solution..
-
The problem is that you won't be able to connect to a console of a VM unless you enable "Validate SSL connections" and the app will only connect if you use a public SSL cert, not a self signed one.
-
@gyrex this seems like a horrible design if you ask me.. Again proxmox is not something that is normally available to the public internet. So why should it have a public cert on it, I turned of that proxmox server - its a real power hungry thing, I only turn it on when needed to test something..
So your saying you can only console to a vm in the app when you validate ssl? But you can do that via just web, I do that all the time and certs not valid its just the self signed cert.
It has to be trusting CAs from something on the the client device, in my case my chromebook - so need to see how to install its CA cert into my chromebook.
I will play with it some more later..
But my chrome browser trusts the certs, so it seems like maybe this app is not using the chromeOS store for what CAs it trusts?
-
@gyrex A host override is probably better but you can let DNS Resolver return private IPs by putting this in the Custom Options field:
server:
private-domain: "example.domain.com.au" -
@steveits yeah he can do that, but that has nothing to do with getting an ACME cert.. If he was wanting to get a acme cert via it actually talking to the box vs say dns record, it wouldn't work anyway.
If he was going to allow acme to come talk to the box to validate he owns the domain, etc. then the dns would need to point to his public IP, and he would have to setup a port forward to his proxmox local IP.
Not sure I buy the needing ssl validation for console access - I will fire up my proxmox in the morning and test that. It just seems like a horrible sort of setup when normal operation of proxmox would not be accessed via public internet, and the selfsigned cert it generations should be fine..
I found this thread which seems to point to console working without validation - the poster says he has to turn off validation to get console to work.
https://forum.proxmox.com/threads/proxmox-android-app-novnc-console-not-working.109290/
-
@johnpoz to be honest I kind of skipped all that and answered the first question. I figured you had all that covered. :)
-
@steveits hehe - yeah already had mentioned he could you the private domain thing as well.
But @gyrex are you using the opaque app as well for spice console access, this is 3rd party app that have to buy $9 it looks like. I don't have any desire to fork over that to test something I don't use.. But I can try doing the vnc option which should work as well I think?
I have not really had any need to console into vms running on my test proxmox - I just access the vm directly to do stuff on it.
I did console into them to set them up etc., but that was using just a full browser on my PC - and sure wasn't using trusted ssl certs, just the selfsigned, etc.
-
@johnpoz said in Cloudflare "reserved IP" records not resolving on pfSense DNS server:
are you using the opaque app as well for spice console access
No, I'm just using the normal vnc via the proxmox app.
@johnpoz said in Cloudflare "reserved IP" records not resolving on pfSense DNS server:
using just a full browser on my PC
Connecting to a console via a browser on a PC works fine with or without a certificate. The app requires that you turn on SSL validation to connect to a console via the app itself.
I've resolved this issue by using a DNS override.