Netgate 6100 or Potential DIY Build - Which is Better and Why?
-
@bingo600 said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
By all means go for it, but cpu power also comes with a cost ...
Energy consumption, and fan noise...The 6100 is a better energy and noise choice. But I don't believe those differences are determining factors in my choice. Location placement helps isolate noise concerns, plus the DIY model is a tiny PC so it isn't super loud anyhow. Energy consumption is nearly double on the DIY option, but has a pretty low cost impact of less than $6 per month using local energy rates. Although from an environmental perspective, I'd prefer the 6100.
If you feel your need is 1Gb VPN capacity , then i guess you have already excluded the 6100 your self. So go for a bigger iron.
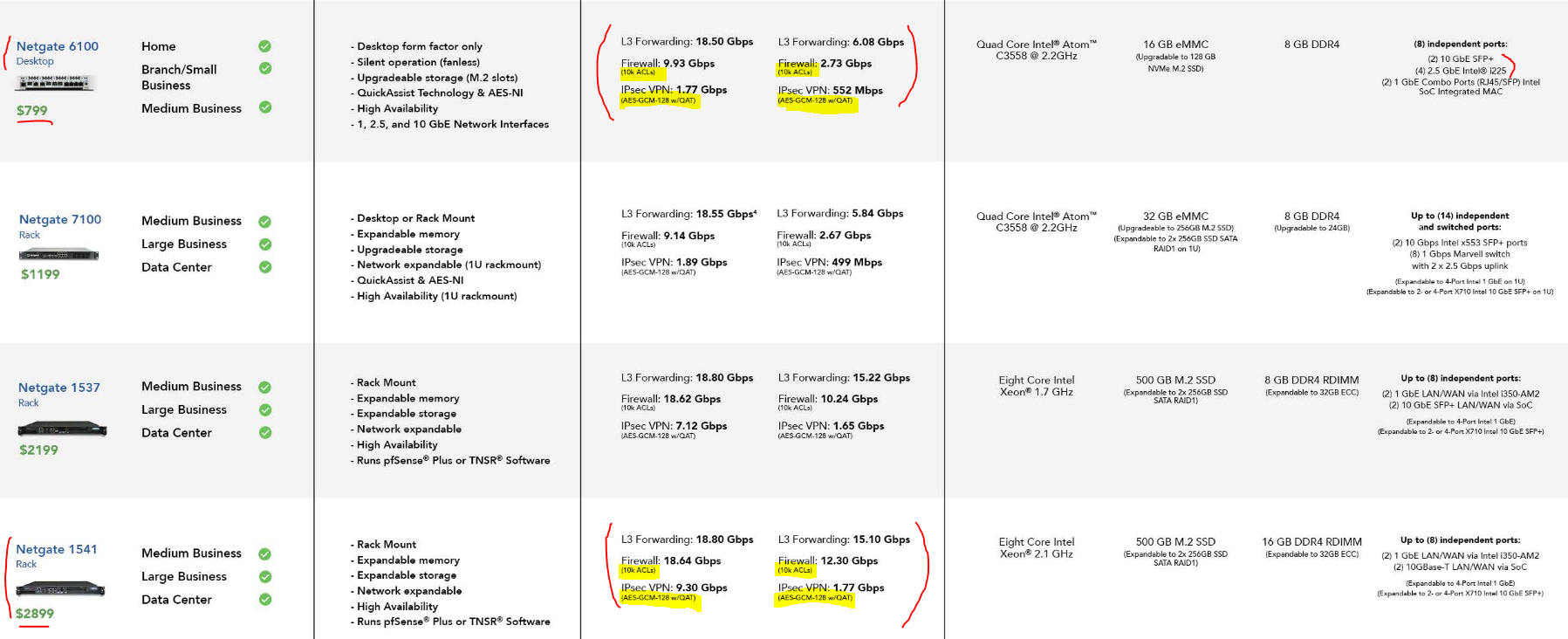
I don't think I need 1gb VPN capacity. I think it would be nice to have if reasonably possible but I am good with 550mb. I haven't eliminated the 6100 and actually like the fact it's something off the shelf I can buy and know will work with some published performance rates. It offers peace of mind.
Depending on which VPN you'd like to use:
OpenVPN is afaik still CPU speed bound (single threaded), meaning get as high CPU clockrate as possible.
That said afaik people tend to get 200-300Mbit when connectiong to a VPN provider , and usually needs to start up (bundle) several tunnels to the ISP go get higher speed. That means each tunnel can be bound to a new thread, and be "Multithread a'like"IPSec - I don't know, but think pfSense's implementation is "Multithread capable".
Ignoring QAT...am I correct to think the i5-11500 with 6 cores, 12 threads and 12mb cache would likely outperform the 6100?
Btw:
Afaik only Netgate HW has Quick assist supported.
QAT Makes the 6100 so powerfull w. VPN.With QAT factored in, is the performance a wash? Do you have any additional information about the performance gains of QAT? I saw a YT video by Lawrence Systems that said something about marginal gains of 10-15% with QAT.
I am very curious because when you factor in QAT card costs ($650 Netgate site, or $350+ on eBay) and Plus license cost (assuming $200-ish) there are some major costs to consider that the DIY unit doesn't currently have included.
Edit:
Forgot Wireguard (if you trust that beast .. I don't yet) ...
"They say" it does a super BW vs CPU load/Bingo
Forgive my ignorance, but again I am not a networking guru, what is it about Wireguard that I need to know? I have heard it's faster and the stuff I have read is it may even be preferred. I wasn't aware it may not be trustworthy.
-
@stephenw10 said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
@bingo600 said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
Afaik only Netgate HW has Quick assist supported.
Anything running pfSense Plus can use QAT if is has supported hardware.
Steve
I got a similar answer here in another thread when I asked about what all hardware had QAT built-in. Here is a copy/paste of a response from elsewhere:
From the FreeBSD man page: The qat driver supports the QAT devices integrated with Atom C2000 and C3000 and Xeon C620 and D-1500 chipsets, and the Intel QAT Adapter 8950. -
@johnpoz said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
@bingo600 said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
What on earth do you have in the other end that would "Service 1Gbit VPN"
This is such a good point.. He is remote on his phone he sure isn't going to be needing his home firewall to be able to handle 1gig via vpn from his phone on some bar wifi ;)
I would question this as well
I plan on using DPI/IPS services on most items.
What exactly are you expecting to see when pretty much all traffic these days is encrypted.. What services are you hosting to the wild west internet.
So your going to allow free access from say your iot network into your lan network, and then just let the IPS protect you from bad stuff it might do, or wouldn't it just be simpler to block it from taking to your Lan in the first place.
Before you go thinking you need some box to handle IPS for multiple interfaces and stuff - I would make sure its actually going to be doing something other then sucking cpu and power watching packets go by that it can't see inside because they are encrypted.. So hows it going to warn you hey this is bad..
I am new to pfSense and this level of networking, but it was my understanding that after establishing the various VLAN's I could then write firewall rules that could isolate them from each other. So in other words, my guest or IOT networks couldn't get into the rest of my LAN.
Admittedly I still need to think through some of the finer details. I am not 100% sure I need DPI/IPS on every VLAN but my overall thought process was simple in the fact if I got hardware that would support it then I would be covered. Also, because we deal with medical patient information then I want to ensure we are covered and due diligence is more than provable should HIPPA question anything.
In regards to VPN access back to our server, I would see that being when on vacation or business trips. During business, we may be using an out of state office (contract status) to link back to our primary office and I would expect them to have a good strong connection. Okay, maybe the bar too, but don't tell my wife, lol. But those are probably 20% or less of the time.
The 80% will be working with data that we want protected inside our network and also when transmitting to patients, other medical providers, etc. Ideally all traffic that goes through the work VLAN would be encrypted.
-
@sledge said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
my guest or IOT networks couldn't get into the rest of my LAN.
Yeah that is easy enough to do with pfsense.
As to ips/ids
in the fact if I got hardware that would support it
You don't need a rocket ship to do basic ips/ids - turning it on without configuration and maint and turning isn't going to do much good.. But again as you stated you want everything encrypted - which yeah is pretty common these days, and sure with hippa you prob not going to be ftping stuff across your network, you would use sftp, or scp, etc.
So there really isn't going to be much for the ips/ids to do, since all your traffic would be encrypted that flows across pfsense.. Even if you had smb copies going across vlans - I would assume you would want that encrypted, which is easy enough to accomplish as well.. But has nothing to do with pfsense.
-
Curve ball….I had a 2014 Mac Mini (server edition) drop in my lap. It has a dual core i7 4578U, 3.0ghz, 16gb DDR3 and 256gb SSD.
https://www.cpubenchmark.net/cpu.php?cpu=Intel+Core+i7-4578U+%40+3.00GHz
It only has 1 gigabit port so I would need to buy a thunderbolt to gigabit adapter to add a second. But those are only $30.
My initial knee jerk reaction is it will probably be overkill for routing and firewall but “fall short” on VPN as it won’t have QAT. I’m just not sure how to gauge VPN speed. As already noted it would be nice to have 1gb speed but that seems improbable with my budget constraint. I am hopeful it could crank out 500-ish. If not maybe sell and put funds towards other hardware.
-
@sledge said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
buy a thunderbolt to gigabit adapter to add a second. But those are only $30.
Check if a Tbolt Gbit NW adapter is supported in FreeBSD V12/13 ...
FreeBSD can be "picky" at times w. the HW support -
@bingo600 said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
@sledge said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
buy a thunderbolt to gigabit adapter to add a second. But those are only $30.
Check if a Tbolt Gbit NW adapter is supported in FreeBSD V12/13 ...
FreeBSD can be "picky" at times w. the HW supportAppreciate the heads up. :-)
I was also worried about that and had started searching for others that had already taken the path. There were 2 posts on this forum back in 2018. As you read later into them, it appears they had good luck with a cheap USB adapter along with the official Apple TB2 adapter.
Im not sure which version of FreeBSD that version of pfSense was based on but it appears there is some hope of it working.
I will continue to search.
https://forum.netgate.com/topic/127049/can-i-install-pfsense-on-a-macmini
https://forum.netgate.com/topic/135801/mac-mini-pfsense-system-hardware
-
@dobby_ said in Netgate 6100 or Potential DIY Build - Which is Better and Why?:
pfSense CE is free of charge and the pfSense+ (Plus) edition is for Lab and home usage also free of charge!
- What ISP modem is in front of pfSense?
- Is it a modem with 2,5 GBit/s ports or not?
- How many snort or suricata rules you are setting up?
- How many pf-Blocker-ng lists will be in game?
- HotSpot (captive portal) with vouchers or radius cert.?
eBay
Supermicro miniITX board and case Intel Xeon E3-xxxxv5/v6 4C/8T (3,2 - 4,5 GHz) with 2 / 4 / 8 / 16 / 32 or
64 GB ECC RAM, mSATA with 32/64/128/256 GB or M.23 with 1TB or 2 TB, a single or dual port card intel i225 NIC- You use PPPoE
- AES-NI is enough
SuperServer E300-9A-16CN8TP
Supermicro Board with 16 Core Intel C3958 CPU
with 8 / 16 / 32 or 64 GB ECC RAM, mSATA with 32/64/128/256 GB or M.23 with 1TB or 2 TB, a single or dual port card intel i225 NIC, Supermicro case and PSU.- You use not PPPoE
- QAT is important
Thank you @Dobby_
Maybe the below helps a little more.
-
I have fiber. No modem, but I do have an ONT on the outside of the house. It enters the garage where all my Cat 5e drops are located. I can then choose to make whatever drop I want hot and connect to the router with an RJ45 connection.
-
No PPPoE.
-
Again, it’s ONT so no 2.5gb port. However, currently the max package currently available is 1gb up/down. Even if 2.5gb+ was available I don’t think I would upgrade, unless it’s offered as a free speed bump. At that point I would need to rewrite my house as well with better cabling.
-
I’m not really sure how many snort/suricata rules we will be using. I haven’t got that deep in the weeds yet. I would guess something reasonable and not over the top. Also as pointed out I would want to setup so that we aren’t taxing the system on encrypted transmissions.
-
In regards to pfBlockerNG, I would think we may be more restrictive in this area. Having not dove into the details I can’t say with certainty the exact lists. The caveat being I have read where some users have experienced NG not working as they expected.
-
I think RADIUS for primary access to employees (currently myself and wife, but potential to add 1-2 lower level support/administrative personnel). Ideally, we would authenticate using machine login (mix of Apple and Windows devices). Captive portal would be nice for business guest Wi-Fi access but currently that is not required. If we shift to a commercial building where patients would visit then this may be a FUTURE need.
Definitely open to further guidance/discussion on items 4-6. To date, we have been “Wild West” using a home Wi-Fi mesh system with a primary network and guest network (that we keep off, until specifically required). Practically anything we do will be better than now.
-
@bingo600 @johnpoz @stephenw10 @Dobby_
I am having a hard time finding something about the Apple adapter and freeBSD. I can find posts on this forum (and others) where they have got pfSense + Mac Mini to play together using the adapter. Just can't find it on freeBSD specifically.
On a Gentoo Linux Wiki site, I found this additional information about the adapter, Model A1433 EMC 2590. The other posts I have found wasn't as specific to list the exact model number they were using but I believe this to be the one. It is currently found on Amazon and also below is a screen shot from an Amazon user review.
root #lspci -nnk Ethernet controller [0200]: Broadcom Corporation NetXtreme BCM57762 Gigabit Ethernet PCIe [14e4:1682] Subsystem: Apple Inc. Device [106b:00f6] Kernel driver in use: tg3
My concern being is that I thought the general rule was Broadcom was bad for pfSense, and that generally Intel is recommended. I did find an older post where one of the responders was using a Mac Mini + TB2 PCI enclosure and 4-port Intel 350 card.
My question -- if the $30 Apple adapter works with the Broadcom chip, what are the negatives? Will select add-on packages not work? I thought I had read where DPI/IPS didn't work with it, does that sound right?
-
Then CPU cores over GHz are counting, pending on the WAN speed. WAN speed since 2.6 is balanced over queues, more
cpu cores more queues, is "higher" speed. With PPPoE more raw CPU horse power (GHz) is counting its nailed to one CPU core .
4.
Much rules must be decompressed so it could be nice to
own some GB ram 8 GB - 16 GB also for other or more installed packets. 64 GB - 128 GB mSATA/M.2.
5.
pfblocker-ng is a really good thing in my opinion, but also
needs some ram and some SSD space. It works well with squid & squidguard and/or ClamAV but needs again, more
ram, cpu horse power and/or storage space.
6.
Knowing it before may be better to own a device with 2-3
miniPCIe or M.2 slots for SSD and/or 2 WiFi cards. -
@dobby_ I have 1gb fiber up & down. Current consumer grade mesh system shows consistent 950-ish speeds at the wire.
If I’m understanding you correctly I would be better served with more cores over clock speed and 8-16gb RAM plus some hard drive space?
As noted a few posts up I had a Mac Mini drop in my lap and would at least like to try to use it to help keep my costs low. However, getting a reliable and fast working device > cost savings.
The Mac Mini is a dual core i7 4578U @ 3.0ghz with 16gb DDR3 and a 256gb SSD. Based on what you said my concern is I need a quad core or more.
Also I am concerned with the Broadcom NIC. Others report getting the internal and TB2 to Ethernet adapters to work. But I was reading some info earlier today and I didn’t see Broadcom in the netmap so I am not sure how well Suricata will run. At least I think I interpreted that correctly. So much info that I’m trying to digest.
-
I have 1gb fiber up & down. Current consumer grade
mesh system shows consistent 950-ish speeds at the
wire.The consumer grade router comes often sorted with an ASIC or an FPGA and is only routing not more! It is doing
SPI and NAT and that`s it. pfSense is a firewall and on top
it can be turned into a fully UTM device with captive portal
and voucher system over sms if needed. So if you say today you will 100 % know what you will be installing and using or how much you will turn it into "something" including ids and pfblocker-ng rules it might be the best
to work two different roads;-
- You will get nearly the use case you know before
that all is matching and running fine for you.
- You will get nearly the use case you know before
-
- You will be buying a "diy" rig (pfSense box) that comes with much power in backgrounbd you and be able to push it up if needed with ram, ssd and wifi or LTE if needed.
Squid & SquidGuard, ClamAV, IDS, pfBlocker-ng, firewall, = UTM
- You will be buying a "diy" rig (pfSense box) that comes with much power in backgrounbd you and be able to push it up if needed with ram, ssd and wifi or LTE if needed.
If I’m understanding you correctly I would be better
served with more cores over clock speed and 8-16gb
RAM plus some hard drive space?
With not using PPPoE, yes of course this might be the best solution for you in my eyes, because;- you will be able to balance the wan queues over the CPU cores, so they count.
- If you need more ram you should be able to insert it fast
- If you need a greater ssd space you will be able set it up
- if you need wifi with captive portal for your clients you will be able to realize it.
- you turn on more rules and lists for suricata snort or pfblocker-ng you have not problems at all!
As noted a few posts up I had a Mac Mini drop in my
lap and would at least like to try to use it to help keep
my costs low. However, getting a reliable and fast
working device over cost savings.Make sure that the usb port to ethernet adapter is not your wan, it is often reasigning and then you will be
really p****d by configuring it new.The Mac Mini is a dual core i7 4578U @ 3.0ghz
with 16gb DDR3 and a 256gb SSD. Based on what
you said my concern is I need a quad core or more.- 3,0 GHz CPU
- 4C / 4T or 4C / 8T
- 8 - 16 GB
- 64 GB - xyz GB/TB (M.2 / miniPCIe slot)
- able to add 2 WiFi cards
Would be my setup in your situation based on what you were telling here around.
So this is what you will see it is nice to go only with the things you need pfSense such suricata, firewall and and and, for this they are selling appliances, being sure you will be on the save site or you will be setting up your own rig, you should be better sorted using the two way;
- near by the point all is running
- build a box with much backspace horse power.
What I was getting out of this forum actual I mean, if
netgate is able to offer you a box matching your needs go with it, if not or you will be unsure you should buy supermicro C3000 board with much ECC Ram and a mSATA to come closer to your needs, if not able go with an used E3-xxxxv5 and a miniITX board with one or two PCIe slots and ecc ram and M.2 or mSATA with it you will never fail in 80% of all cases, all other cases are greater companies with many more employees and services running. -