Slow DNS after 22.05
-
Could it be an issue with cache?
-
Doing more nslookups from client during the issue I noticed a few things that seem pretty consistent.
My initial request/s to pfSense seem to timeout despite my client knowing the IP of pfSense.
If I keep placing requests, eventually I get a response, and usually only to IPv6 first.
Then in the next response both IPv6 and IPv4 after more timeouts.After it does fully resolve, subsequent requests seem ok for a while.
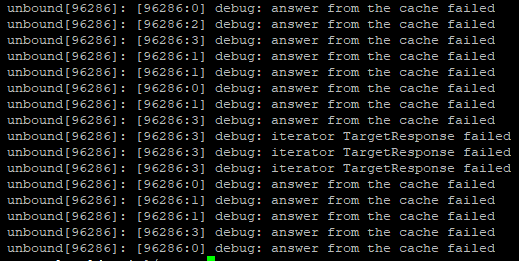
It seems like it takes a few tries to resolve some un-cached addresses sometimes.Unbound is not restarting at this time as I can see it's been running for a while now.
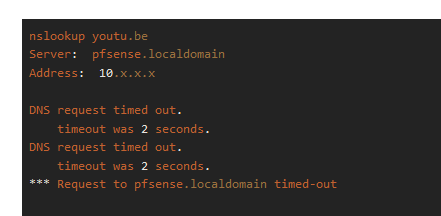
nslookup youtu.be Server: pfsense.localdomain Address: 10.x.x.x DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. *** Request to pfsense.localdomain timed-out nslookup youtu.be Server: pfsense.localdomain Address: 10.x.x.x DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. Name: youtu.be Address: 2a00:1450:4009:81e::200e nslookup youtu.be Server: pfsense.localdomain Address: 10.x.x.x DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. Name: youtu.be Address: 2a00:1450:4009:81e::200e 142.250.180.14version: 1.15.0 verbosity: 5 threads: 4 modules: 2 [ validator iterator ] uptime: 19646 seconds options: control(ssl) unbound (pid 96286) is running...total.num.queries=10304 total.num.queries_ip_ratelimited=0 total.num.cachehits=2806 total.num.cachemiss=7498 total.num.prefetch=0 total.num.expired=0 total.num.recursivereplies=7497 total.requestlist.avg=3.25433 total.requestlist.max=39 total.requestlist.overwritten=0 total.requestlist.exceeded=0 total.requestlist.current.all=3 total.requestlist.current.user=1 total.recursion.time.avg=9.417250 total.recursion.time.median=0.423254 total.tcpusage=0 -
IMHO, this says to me :
nslookup tries to contact a fist DNS server, after the time out, it decided it can't.
A next DNS server is tried. It can't neither.
A third one is tried (pfsense ?) and this time there is an answer.What do you have here ( Dashboard System information ) :
?
You have unbound running with maximum log details ?
Ok to debug, but think about putting that back to default as soon as possible.
Max logd details will overflow the (small) max log file size, so it will get rotated often == even more system and disk resources used.Run on the command line
grep 'start' /var/log/resolver.logand try the settings I showed above, under Services > DNS Resolver > General Settings, remove the check from :
DHCP Registration
OpenVPN ClientsThese two should be unchecked if you use pfBlockerng-devel anyway.
Wait a day or so and run the command again.
unbound will also restart on interface events, like a WAN that changes his IP. Or some other interface goes down and up. These events can be seen in the main system log.
@tentpiglet said in Slow DNS after 22.05:
My wife was also reporting random disconnects from an online game she was playing,
This might be a red flag.
Game playing involves no DNS interfaction.
Its here PC/device against the male server. If this connection gets interrupted, then the issue is : you have a bad connection.
It could be local, like : the wifi is plain bad. Easy to test : that issue goes away as soon as you roll out a cable.
Or worse, your ISP uplink isn't as good as you think it is.
A bad uplink would also explain unreachable remote DNS servers. -
@gertjan said in Slow DNS after 22.05:
What do you have here ( Dashboard System information ) :
Thanks for the reply @Gertjan
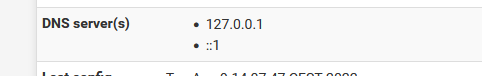
I have pfSense itself (127.0.0.1) and 2 remote name servers from quad9 listed, although my understanding is that those aren't actually used anyway because I have it set to use local ignore remote. Interestingly I don't have the IPv6 listing that you have but I may have disabled something there?

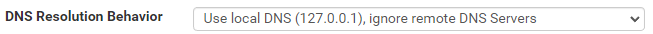
I don't see any unbound restarts (start of service messages) when checking the logs:
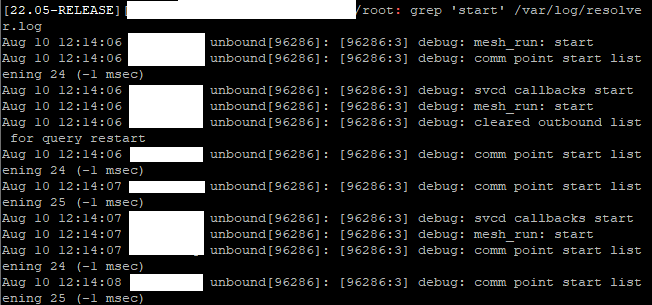
Unbound has been up for about 15 hours now:
I've removed the external DNS now just to rule that out so it should just be using local now.
From what you said, it sounds like it's failing on all DNS servers if it's trying one after the other, as you can see there are occasions it times out twice and also three times. Not sure why it would bomb out after 2 attempts if it is running through the list of DNS servers though because there are 3 and the 2 remote are supposed to be ignored anyway from my understanding.
What I find strange is it seems to be having issues contacting pfSense itself like pfSense isn't responding at all (or DNS on pfSense at least).
-
@gertjan said in Slow DNS after 22.05:
DHCP Registration
OpenVPN ClientsForgot to mention these were already disabled and have always been on my box.
-
@kempain said in Slow DNS after 22.05:
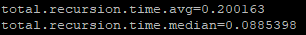
total.recursion.time.avg=1.462659
total.recursion.time.median=1.03385Your avg to resolve something is 1.5 seconds? Well that is going to be problematic for sure.. clients timeout normally at 2 seconds.
Then you have this
total.recursion.time.avg=9.417250
Yeah you have a problem with talking to the NSs for sure..
-
@kempain
Ok, good info.
Unbound is running for 15 hours already.
So no 'very frequent' restarts.Still, strange.
unbound should be listening on port 53 of every LAN interface.
Run thissockstat | grep 'unbound'to check.
Can you also check the device where you have run nslookup ?
Start withipconfig /allYou should have a line with :
Serveurs DNS. . . . . . . . . . . . . : 192.168.1.1 2001:470:1f14:5d0:2::1where 192.168.1.1 is the default pfSense IP. The IPv6 is my IPv6 LAN IP, as I'm using both IPv6 and IPv6 without issues.
Or was this :
nslookup youtu.be Server: pfsense.localdomain Address: 10.x.x.x DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. *** Request to pfsense.localdomain timed-outexecuted on pfSense ? In that case, you can see that nslookup is using 127.0.0.1 and 9.9.9.9 and 149.112.112.112 and two of them are 'unreachable'.
If nslookup was run on pfSense, and it couldn't reach unbound on 127.0.0.1 that I would ditch the entire system. As this is close to impossible.
Do you have :
?
I know, other choices are available, like :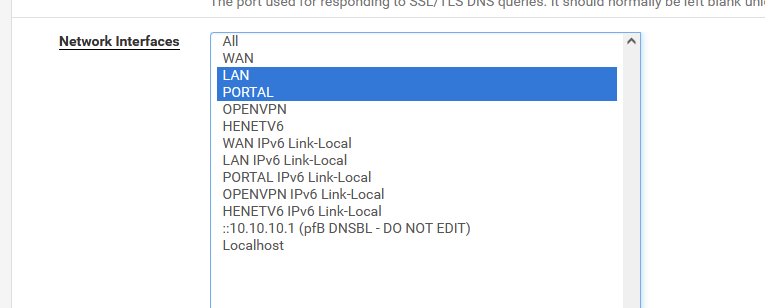
but I would kill DNS on my system and internal networks. I'll leave it up to you to understand why

And drop this one :
to a lower level, like "1"@kempain said in Slow DNS after 22.05:
Forgot to mention these were already disabled and have always been on my box.
Yeah, I get that ;)
Your unbound isn't restarting every minute or so - it restarted 15 hours ago, that's is ok ;) -
@gertjan said in Slow DNS after 22.05:
Game playing involves no DNS interfaction.
Sorry for spamming replies.
I do seem to get connection issues to all services not just web requests. This includes games also when connecting to game servers/lobbies usually which I assume must have to do some kind of lookup?
-
@kempain you can not expect to run a good resolver if your avg time to resolve is 9 seconds.. You can't it just not going to work..
-
@gertjan said in Slow DNS after 22.05:
sockstat | grep 'unbound'
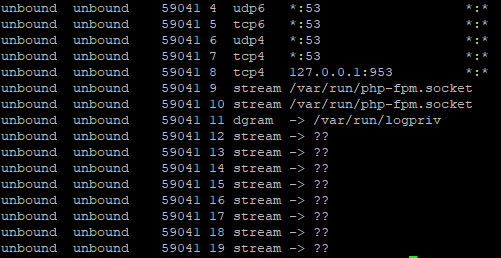
Potential problem here? I see port 953 for local.
@gertjan said in Slow DNS after 22.05:
Serveurs DNS. . . . . . . . . . . . . : 192.168.1.1
2001:470:1f14:5d0:2::1Yup I get back the pfSense IP only (no IPv6) when running this on my client.
@gertjan said in Slow DNS after 22.05:
to a lower level, like "1"
I'll lower the logging level just had it jacked up to capture as much as possible when troubleshooting.
@johnpoz said in Slow DNS after 22.05:
@kempain you can not expect to run a good resolver if your avg time to resolve is 9 seconds.. You can't it just not going to work..
Thanks @johnpoz
Any ideas how I begin to troubleshoot this issue? I'm running on a Netgate SG-5100 so should be ample resources for what I'm doing with it which is pretty basic stuff.
I've removed those external NS now so let's see if that improves things.
I have DNSSEC support enabled but I think we determined that's ok earlier in the thread as long as you're not forwarding DNS?
-
@kempain I would do a dig +trace on you pfsense box - where is having issues talking to in the chain..
[22.05-RELEASE][admin@sg4860.local.lan]/root: dig www.google.com +trace ; <<>> DiG 9.16.26 <<>> www.google.com +trace ;; global options: +cmd . 26136 IN NS d.root-servers.net. . 26136 IN NS e.root-servers.net. . 26136 IN NS f.root-servers.net. . 26136 IN NS g.root-servers.net. . 26136 IN NS h.root-servers.net. . 26136 IN NS a.root-servers.net. . 26136 IN NS i.root-servers.net. . 26136 IN NS j.root-servers.net. . 26136 IN NS k.root-servers.net. . 26136 IN NS l.root-servers.net. . 26136 IN NS m.root-servers.net. . 26136 IN NS b.root-servers.net. . 26136 IN NS c.root-servers.net. . 26136 IN RRSIG NS 8 0 518400 20220822170000 20220809160000 20826 . flMR2MvFJojKfO7Ys2tb+EWssvMaUJSejiq3L4Y5Sy288C16sZOrhvdF GWY0+gtUl5C40kBOnkVdqYDgBfSjbpmPn+NWbkJZMTqwjmz2QN+28MsR bplhWzeu8HghrmCLZkBrmLoTe1e1DXNWbvQbQfmLkBSQmwqntw1QX3GZ UleYopxJngO6hdEQOXbsrcdnfSVUOgxf4wwbS9XZugf1xpaSbKIPCBFd 1xGKWFr9MbcIzogRIDKH4RPZAt8aRIkwZMh53ZaZ2Zo+9n63MdI5N6zB WJlNpJqmFxhE8wVEegqm++2lQSsqYmDikIpCxn/+P8FXDr+vc6erU9jT OP9sFw== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20220823050000 20220810040000 20826 . clI/vPSk2t2LVd1WtfHI8VklYtaUPAOK/8Sr30o0VjGp7xZXZ5EhlVRz YarbopAZ+8yOIwwbIl82ByVZFf/qJEprOKW6TiG8goIoPBG6jghCoglV p4IqNUVqqwpJpAxNKbOA0cOeOr6qTwqugtJnU5J7TGG4QBi63KjYBoin gyYxaKkV/fvK9njoqxbn2hzaKB08mLlYj/9TKxS285UaxbMxYfPDJejQ FA+33Y+KjJlGhdYrCFy/o/JW+YKrfmLrMs2C3+6XGUFFDGSN9WUCF59j LMuQ0ZVAmZQkodwaKM0L1dojQtJU73fEnRkm/1ZhhiDYkQv/HPFHM3ur f3bWww== ;; Received 1174 bytes from 2001:500:2d::d#53(d.root-servers.net) in 28 ms google.com. 172800 IN NS ns2.google.com. google.com. 172800 IN NS ns1.google.com. google.com. 172800 IN NS ns3.google.com. google.com. 172800 IN NS ns4.google.com. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20220815042401 20220808031401 32298 com. If06bSVXL7llnV+iyjrWR5yStSfeLZzeCKgsfVsqNQKKnP35dCsaGffz dRWOIGK+WzMKxVCiJZLiNyG5iYR9RybjH9jXMhDyYqro3M8eplcZtHnd DN0XXqhP/UDjMThDkJHxFERmmzraaU1wQLMcse/uOLMzmZVmOalWkbC+ TtXIfd8f4KB+h/M6X23C9UZ7oyYI78gqwS3Rq0fKInDxXA== S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN NSEC3 1 1 0 - S84BUO64GQCVN69RJFUO6LVC7FSLUNJ5 NS DS RRSIG S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN RRSIG NSEC3 8 2 86400 20220816051414 20220809040414 32298 com. BI5XFgxbzwBugDjaV04ygejNaUOMRGmTaJvdufqfRnJPaDEHLnqVpw7p 8UdjQnXLbtO4Fns2BpPOTD9DSSaWGRjxeZxlb6Rwxw1n4RGmJGe9QyaI f/zBXzn69uRXpgeRP6FFBmUuFCb7OQTBqoReLat+3fwKkebSv7epenW1 SvO4dXilsSZzTAUN8RvIdz9SgkBe+QxG8TiioAFYuTqdkw== ;; Received 840 bytes from 192.5.6.30#53(a.gtld-servers.net) in 13 ms www.google.com. 300 IN A 142.251.32.4 ;; Received 59 bytes from 216.239.34.10#53(ns2.google.com) in 22 ms [22.05-RELEASE][admin@sg4860.local.lan]/root:Notice the times to get answers from the different NS in the chain - they are only a few ms..
Here with almost 80k queries my avg is less than 0.1 of a second.
total.recursion.time.avg=0.088754 total.recursion.time.median=0.0410133 -
@kempain said in Slow DNS after 22.05:
Potential problem here? I see port 953 for local.
Looks fine.
unbound is listing on all interfaces, using port 53,, TCP and UDP.
@kempain said in Slow DNS after 22.05:
Yup I get back the pfSense IP only (no IPv6)
No IPv6 on LAN => Consider what @johnpoz proposed :
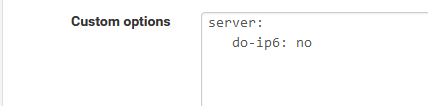
Just make a note : the day IPv6 becomes a thing for you, you have to remove this option.
( see other unbound threads for the "why" part )@kempain said in Slow DNS after 22.05:
I have DNSSEC support enabled but I think
Mine is activated since day 1 ( many years ago ).
DNSSEC is only useful if your are resolving, not forwarding.
For myself, I even went haywire buy activating this :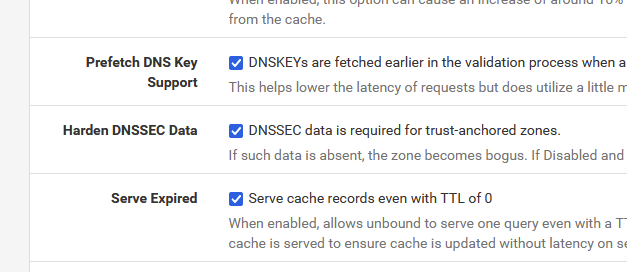
but I would activate these only if you have nothing else to debug / to do.
I don't recall what the default values are. -
@kempain could you do a simple test to see if your dns queries are being messed with.
if you do a directed query to something that shouldn't answer and you get an answer - then your dns is being intercepted.
example..
[22.05-RELEASE][admin@sg4860.local.lan]/root: dig @1.2.3.4 www.google.com ; <<>> DiG 9.16.26 <<>> @1.2.3.4 www.google.com ; (1 server found) ;; global options: +cmd ;; connection timed out; no servers could be reached [22.05-RELEASE][admin@sg4860.local.lan]/root:1.2.3.4 doesn't answer dns - if you query it and you get an answer than your dns is being intercepted.. Much like you can do on your own dns queries with pfsense.. And send them somewhere else.. Like when a client tries to query 8.8.8.8 and you directed to your own dns..
Other than horrible internet connection, or bad peering with where the NS are - there should be no reason your queries take so long.. Are you on a sat connection or something? What is typical ping times for say www.google.com
$ ping www.google.com Pinging www.google.com [142.251.32.4] with 32 bytes of data: Reply from 142.251.32.4: bytes=32 time=12ms TTL=116 Reply from 142.251.32.4: bytes=32 time=12ms TTL=116 Reply from 142.251.32.4: bytes=32 time=10ms TTL=116A couple ms, or even a few hundred ms would be fine - but your avg was 9 seconds?? Yeah that is not going to work for reliable dns resolving.
Typical client timeout would be 2 seconds.. Even with 3 attempts - you would completely time out before an answer was gotten with a 9 second avg query time.
-
Thanks @johnpoz
Ran a dig and apart from the initial figures being higher than yours 85775 vs 26136, and root servers taking 64ms rather than 28ms which is a bit of a bump the rest appears ok for this particularly dig?
I'll try and capture one that's slower for a different address.
[22.05-RELEASE]/root: dig www.google.com +trace ; <<>> DiG 9.16.26 <<>> www.google.com +trace ;; global options: +cmd . 85775 IN NS c.root-servers.net. . 85775 IN NS m.root-servers.net. . 85775 IN NS f.root-servers.net. . 85775 IN NS b.root-servers.net. . 85775 IN NS l.root-servers.net. . 85775 IN NS d.root-servers.net. . 85775 IN NS e.root-servers.net. . 85775 IN NS j.root-servers.net. . 85775 IN NS h.root-servers.net. . 85775 IN NS g.root-servers.net. . 85775 IN NS i.root-servers.net. . 85775 IN NS a.root-servers.net. . 85775 IN NS k.root-servers.net. . 85775 IN RRSIG NS 8 0 518400 20220823050000 20220810040000 20826 . ldBIj1Q5BNWr/TNFQ/RebaJR/2ss3M1NFtp9BVvF8c0oBqYtsYE5lXdh x5SyEQNaY0TQedI0sUYGH1mxbb8do4TGvHlt/cHqdZlR0C4iQJZh1E2J hW7jvykFTd+GvcxoT4pd27WAKcphMxjMV0kv/nJ/R62py40o/x0q4MEh qOOX9xaXXrk9LE8+kF/xH6Hzk/FP1Tvqky5wYq3zu+0GRAGg6Ykornbd 48YZHrK4p4hMwmCfc+rqq2GA1qI///C8yE+c3JbZzMqpnA/Fd1ki7OPa uC4rdZBRTjffHYrHvPm4JQexycKi2yk1p3Zd4VUV5TXso6bQumLIMOuL w+8gXw== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20220823050000 20220810040000 20826 . clI/vPSk2t2LVd1WtfHI8VklYtaUPAOK/8Sr30o0VjGp7xZXZ5EhlVRz YarbopAZ+8yOIwwbIl82ByVZFf/qJEprOKW6TiG8goIoPBG6jghCoglV p4IqNUVqqwpJpAxNKbOA0cOeOr6qTwqugtJnU5J7TGG4QBi63KjYBoin gyYxaKkV/fvK9njoqxbn2hzaKB08mLlYj/9TKxS285UaxbMxYfPDJejQ FA+33Y+KjJlGhdYrCFy/o/JW+YKrfmLrMs2C3+6XGUFFDGSN9WUCF59j LMuQ0ZVAmZQkodwaKM0L1dojQtJU73fEnRkm/1ZhhiDYkQv/HPFHM3ur f3bWww== ;; Received 1174 bytes from 192.58.128.30#53(j.root-servers.net) in 64 ms google.com. 172800 IN NS ns2.google.com. google.com. 172800 IN NS ns1.google.com. google.com. 172800 IN NS ns3.google.com. google.com. 172800 IN NS ns4.google.com. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20220815042401 20220808031401 32298 com. If06bSVXL7llnV+iyjrWR5yStSfeLZzeCKgsfVsqNQKKnP35dCsaGffz dRWOIGK+WzMKxVCiJZLiNyG5iYR9RybjH9jXMhDyYqro3M8eplcZtHnd DN0XXqhP/UDjMThDkJHxFERmmzraaU1wQLMcse/uOLMzmZVmOalWkbC+ TtXIfd8f4KB+h/M6X23C9UZ7oyYI78gqwS3Rq0fKInDxXA== S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN NSEC3 1 1 0 - S84BUO64GQCVN69RJFUO6LVC7FSLUNJ5 NS DS RRSIG S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN RRSIG NSEC3 8 2 86400 20220816051414 20220809040414 32298 com. BI5XFgxbzwBugDjaV04ygejNaUOMRGmTaJvdufqfRnJPaDEHLnqVpw7p 8UdjQnXLbtO4Fns2BpPOTD9DSSaWGRjxeZxlb6Rwxw1n4RGmJGe9QyaI f/zBXzn69uRXpgeRP6FFBmUuFCb7OQTBqoReLat+3fwKkebSv7epenW1 SvO4dXilsSZzTAUN8RvIdz9SgkBe+QxG8TiioAFYuTqdkw== ;; Received 840 bytes from 192.35.51.30#53(f.gtld-servers.net) in 20 ms www.google.com. 300 IN A 142.250.200.4 ;; Received 59 bytes from 216.239.32.10#53(ns1.google.com) in 20 msThings do seem to have improved after dropping logging level (assume to be expected) but still very slow:
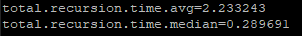
@gertjan said in Slow DNS after 22.05:
No IPv6 on LAN => Consider what @johnpoz proposed :
Updated this now. I plan on sorting out IPv6 in future but it's way over my head atm.
Early days but this setting might have had a dramatic effect?
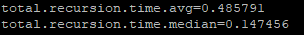
-
@johnpoz said in Slow DNS after 22.05:
dig @1.2.3.4 www.google.com
Ran this and get the same results as you thankfully but this is really good to know.
It may be that disabling IPv6 has resolved it but I'm keeping an eye on it and will report back.
Pings seem decent:
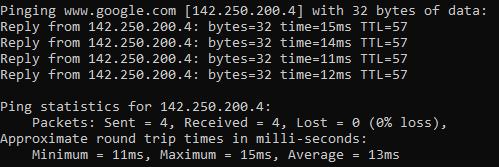
That's from a client and directly from pfSense is even faster averaging 13ms.
-
Would urge others experiencing the issue to try this and report back as so far everything is MUCH faster now. Even though it's early days I haven't received any DNS issues / timeouts yet.
Seems like user error IPv6 mis-config

@gertjan said in Slow DNS after 22.05:
No IPv6 on LAN => Consider what @johnpoz proposed :
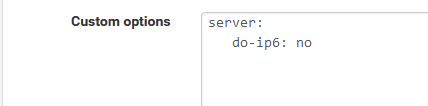
-
@kempain I’m gonna try this by reverting my forward and adding this option.
What ISP are you running btw?
-
@mikymike82 said in Slow DNS after 22.05:
What ISP are you running btw?
I'm in the UK with Virgin. They do issue IPv6 as far as I know so I think I can do full IPv6 if I knew what I was doing.
-
unbound unbound 44545 3 udp4 *:53 :
unbound unbound 44545 4 tcp4 *:53 :
unbound unbound 44545 5 udp4 *:853 :
unbound unbound 44545 6 tcp4 *:853 :
unbound unbound 44545 7 tcp4 127.0.0.1:953 :
unbound unbound 44545 8 dgram -> /var/run/logpriv
unbound unbound 44545 10 stream -> ??
unbound unbound 44545 11 stream -> ??
unbound unbound 44545 13 stream -> ??
unbound unbound 44545 14 stream -> ??
unbound unbound 44545 15 stream -> ??
unbound unbound 44545 16 stream -> ??
unbound unbound 44545 17 stream -> ??
unbound unbound 44545 18 stream -> ??
unbound unbound 44545 19 stream -> ??
unbound unbound 44545 20 stream -> ??
unbound unbound 44545 21 stream -> ??
unbound unbound 44545 22 stream -> ??
unbound unbound 44545 23 stream -> ??
unbound unbound 44545 24 stream -> ??
unbound unbound 44545 25 stream -> ??
unbound unbound 44545 26 stream -> ??dig @1.2.3.4 www.google.com
; <<>> DiG 9.16.16 <<>> @1.2.3.4 www.google.com
; (1 server found)
;; global options: +cmd
;; connection timed out; no servers could be reached; <<>> DiG 9.16.16 <<>> www.google.com +trace
;; global options: +cmd
. 238 IN NS e.root-servers.net.
. 238 IN NS f.root-servers.net.
. 238 IN NS g.root-servers.net.
. 238 IN NS h.root-servers.net.
. 238 IN NS a.root-servers.net.
. 238 IN NS i.root-servers.net.
. 238 IN NS j.root-servers.net.
. 238 IN NS k.root-servers.net.
. 238 IN NS l.root-servers.net.
. 238 IN NS m.root-servers.net.
. 238 IN NS b.root-servers.net.
. 238 IN NS c.root-servers.net.
. 238 IN NS d.root-servers.net.
. 238 IN RRSIG NS 8 0 518400 20220823050000 20220810040000 20826 . ldBIj1Q5BNWr/TNFQ/RebaJR/2ss3M1NFtp9BVvF8c0oBqYtsYE5lXdh x5SyEQNaY0TQedI0sUYGH1mxbb8do4TGvHlt/cHqdZlR0C4iQJZh1E2J hW7jvykFTd+GvcxoT4pd27WAKcphMxjMV0kv/nJ/R62py40o/x0q4MEh qOOX9xaXXrk9LE8+kF/xH6Hzk/FP1Tvqky5wYq3zu+0GRAGg6Ykornbd 48YZHrK4p4hMwmCfc+rqq2GA1qI///C8yE+c3JbZzMqpnA/Fd1ki7OPa uC4rdZBRTjffHYrHvPm4JQexycKi2yk1p3Zd4VUV5TXso6bQumLIMOuL w+8gXw==
;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 1 mscom. 172800 IN NS a.gtld-servers.net.
com. 172800 IN NS b.gtld-servers.net.
com. 172800 IN NS c.gtld-servers.net.
com. 172800 IN NS d.gtld-servers.net.
com. 172800 IN NS e.gtld-servers.net.
com. 172800 IN NS f.gtld-servers.net.
com. 172800 IN NS g.gtld-servers.net.
com. 172800 IN NS h.gtld-servers.net.
com. 172800 IN NS i.gtld-servers.net.
com. 172800 IN NS j.gtld-servers.net.
com. 172800 IN NS k.gtld-servers.net.
com. 172800 IN NS l.gtld-servers.net.
com. 172800 IN NS m.gtld-servers.net.
com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766
com. 86400 IN RRSIG DS 8 1 86400 20220823050000 20220810040000 20826 . clI/vPSk2t2LVd1WtfHI8VklYtaUPAOK/8Sr30o0VjGp7xZXZ5EhlVRz YarbopAZ+8yOIwwbIl82ByVZFf/qJEprOKW6TiG8goIoPBG6jghCoglV p4IqNUVqqwpJpAxNKbOA0cOeOr6qTwqugtJnU5J7TGG4QBi63KjYBoin gyYxaKkV/fvK9njoqxbn2hzaKB08mLlYj/9TKxS285UaxbMxYfPDJejQ FA+33Y+KjJlGhdYrCFy/o/JW+YKrfmLrMs2C3+6XGUFFDGSN9WUCF59j LMuQ0ZVAmZQkodwaKM0L1dojQtJU73fEnRkm/1ZhhiDYkQv/HPFHM3ur f3bWww==
;; Received 1174 bytes from 193.0.14.129#53(k.root-servers.net) in 16 msgoogle.com. 172800 IN NS ns2.google.com.
google.com. 172800 IN NS ns1.google.com.
google.com. 172800 IN NS ns3.google.com.
google.com. 172800 IN NS ns4.google.com.
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20220815042401 20220808031401 32298 com. If06bSVXL7llnV+iyjrWR5yStSfeLZzeCKgsfVsqNQKKnP35dCsaGffz dRWOIGK+WzMKxVCiJZLiNyG5iYR9RybjH9jXMhDyYqro3M8eplcZtHnd DN0XXqhP/UDjMThDkJHxFERmmzraaU1wQLMcse/uOLMzmZVmOalWkbC+ TtXIfd8f4KB+h/M6X23C9UZ7oyYI78gqwS3Rq0fKInDxXA==
S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN NSEC3 1 1 0 - S84BUO64GQCVN69RJFUO6LVC7FSLUNJ5 NS DS RRSIG
S84BKCIBC38P58340AKVNFN5KR9O59QC.com. 86400 IN RRSIG NSEC3 8 2 86400 20220816051414 20220809040414 32298 com. BI5XFgxbzwBugDjaV04ygejNaUOMRGmTaJvdufqfRnJPaDEHLnqVpw7p 8UdjQnXLbtO4Fns2BpPOTD9DSSaWGRjxeZxlb6Rwxw1n4RGmJGe9QyaI f/zBXzn69uRXpgeRP6FFBmUuFCb7OQTBqoReLat+3fwKkebSv7epenW1 SvO4dXilsSZzTAUN8RvIdz9SgkBe+QxG8TiioAFYuTqdkw==
;; Received 840 bytes from 192.54.112.30#53(h.gtld-servers.net) in 12 mswww.google.com. 300 IN A 142.250.181.196
;; Received 59 bytes from 216.239.36.10#53(ns3.google.com) in 8 ms -
All seems ok as far as I know.
Key metric seems to be total recursion time so try:
unbound-control -c /var/unbound/unbound.conf stats_noreset | grep total