Secure DNS configuration with WAN and a VPN gateway
-
Hello, I am relatively new to pfSense, having started using it for my home network back in November and I have been slowly progressing from a basic installation to a more advanced as I learn all the relevant networking concepts.
Currently, my pfSense firewall is set up with two gateways: part of my Internet traffic is sent through the ISP using the WAN gateway (mostly streamers/higher speed devices) and part through NordVPN using the NORDVPN_VPNV4 gateway.
The reason why I am writing here for the first time is to get some help on the subjectt of DNS configuration, which I find rather confusing. Not least because while it is easy to check whether DNS is working or not, I find much less trivial to understand if it is working in the intended configuration, and even what the optimal configuration should be.I apologize in advance, as this is a long post, but before jumping into my questions, I thought it would be good to verify if my understanding of this matter, which I summarised in the 6 statemennts below, is correct. For my actual questions, one can skip to the DNS configuration questions further down
- If I am connected to a site with HTTPS, neither my ISP nor NordVPN or no sniffer in the middle can understand the information exchanged because it's encrypted
- The DNS queries through NordVPN are encrypted as well as the data exchanged with the connected website. Since NordVPN operates its own DNS servers, and does not send unencrypted DNS queries outside, only NordVPN knows which website I connect to, and a sniffer would see only encrypted info.
- Instead, my default DNS queries that go to the ISP are not encrypted, so in this case both the ISP and a sniffer in the middle can see this info.
- By setting up DNS over TLS in pfSense with one of the providers of this service (e.g. Cloudflare) I can encrypt my DNS queries cutting off both the ISP and the sniffer in the middle. The price to pay is that Cloudflare will now know to which website I connect to, but not the info exchanged (if the connection is HTTPS). Sort of a two-for-one gain, with the plus of cutting off the sniffer, who is potentially the most harmful party.
4b) There seems to be a known weakness in DNS over TLS during the TLS handshake when, in a step called Server Name Indication (SNI), the name of the destination server is transmitted unencrypted. Due to this weakness, both the ISP and the sniffer are still able to track the websites I connect to. - Due to the unencrypted SNI, a DNS query via NordVPN is more private than a DNS over TLS query via Cloudflare (leaving aside the question whether one can trust NordVPN more or less than Cloudflare, but purely based on the number of subjects who can see the info)
- This is a direct consequence of 5: if I send all my traffic through NordVPN I would not need to set up DLS over TLS in pfSense.
Please correct me if any of the statements above is wrong.
What makes me doubt that my understanding is fully correct is the fact that the author of the Setup DNS over TLS on pfSense 2.4.4 p2 - Guide, set up DNS over TLS to use it on a VPN gateway. If DNS via VPN was more secure, why would he want to have DNS over TLS? I would appreciate any insight on that point.DNS Configuration questions
What is the preferred way to setup DNS when part of the Internet traffic goes through a secure VPN provider?I have tried two ways to setup my DNS, but in both cases there seemed to be something that was off. This might also be due to my lack of knowledge of how to properly verify what I got.
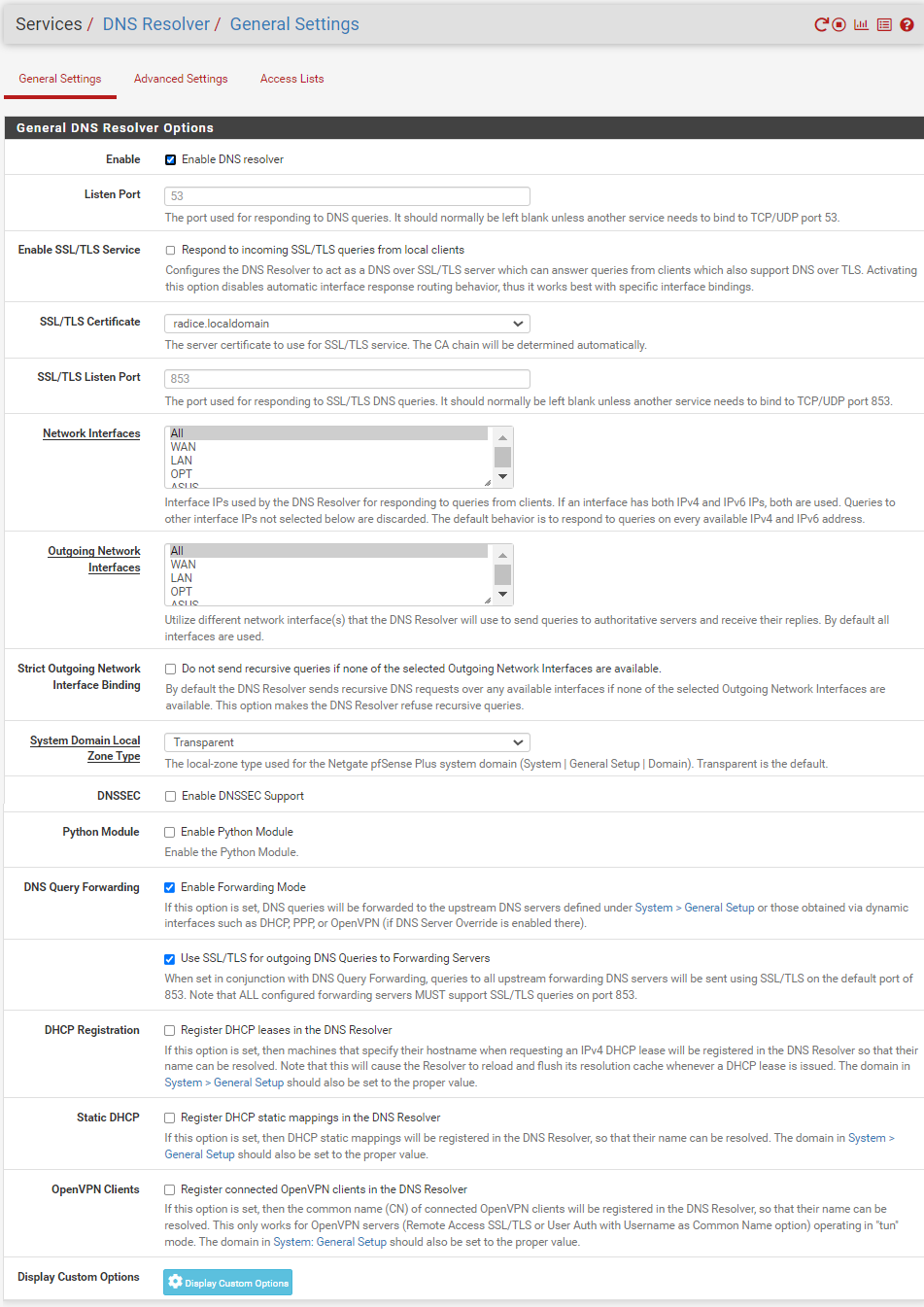
In the first setup, I specified on the General Setup page the two NordVPN DNS servers 103.86.96.100 and 103.86.99.100 for the NORDVPN_VPNV4 interface and the two Cloudflare servers 1.1.1.2 and 1.0.0.2 for the WAN gateway and then I set up the DNS Resolver according to the above-mentioned setup guide. Screenshots of my setup pages are below.
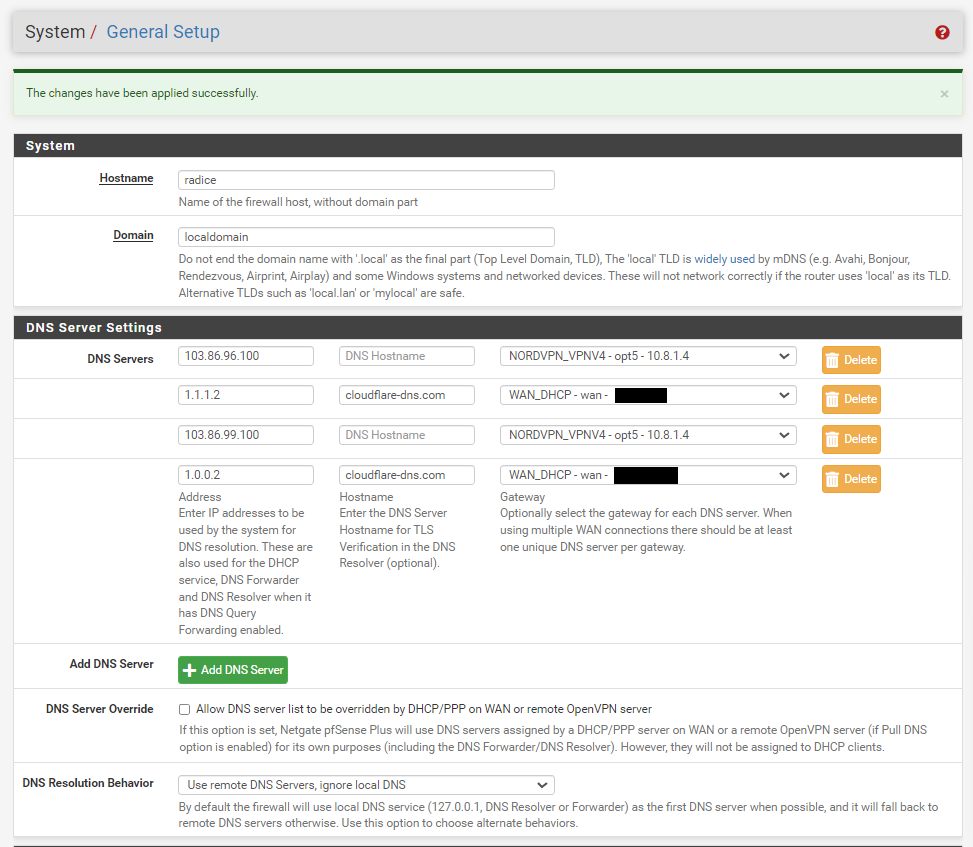
The problem in this case is that when I look on pfTop I see only the Cloudflare DNS servers and not those of NordVPN, so I believe that with this setup all my DNS queries are sent via Cloudflare, which does not seem to be good.
In the second setup, I eliminated the Cloudflare servers, leaving only the two NordVPN DNS servers available for queries from either gateway (i.e., gateway value set to none).
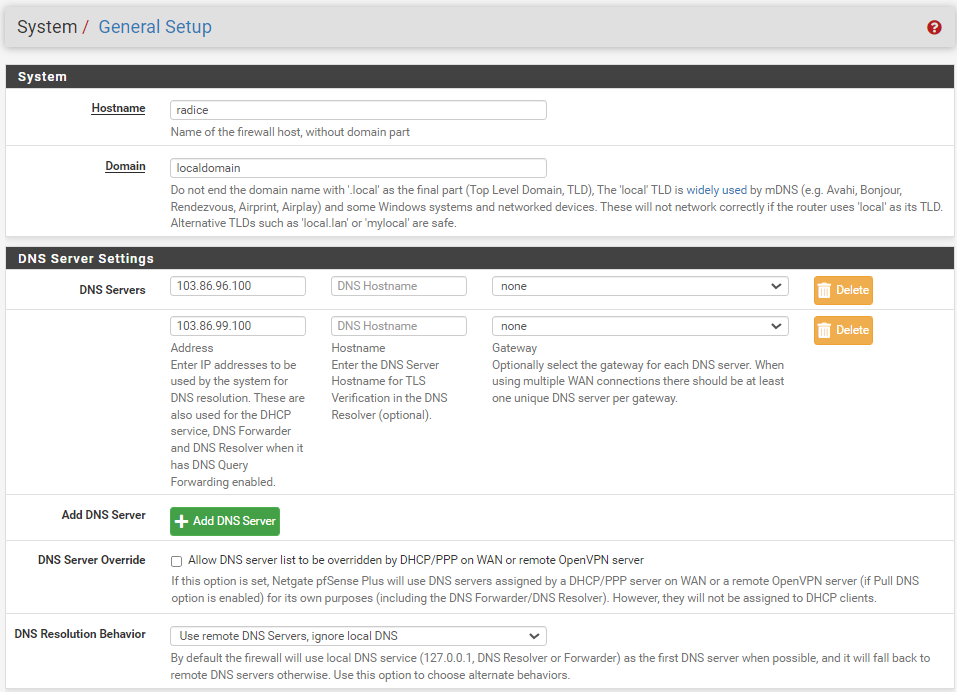
This scenario raises a lot of questions in my mind: is it desirable to separate on WAN the DNS queries from the data exchange, by sending the former to NorthVPN while the latter goes via the ISP? Is DNS over TLS needed at all in this case, since I am not using Cloudflare or any other provider of that service? In practice, it seems to work, however looking on pfTop, in this case it seems that while the queries on WAN go through port 853, those on NORDVPN_VPNV4 go through port 53. Is this acceptable as all DNS queries go through the tunnel anyway? Or is it a sign of a bad implementation.
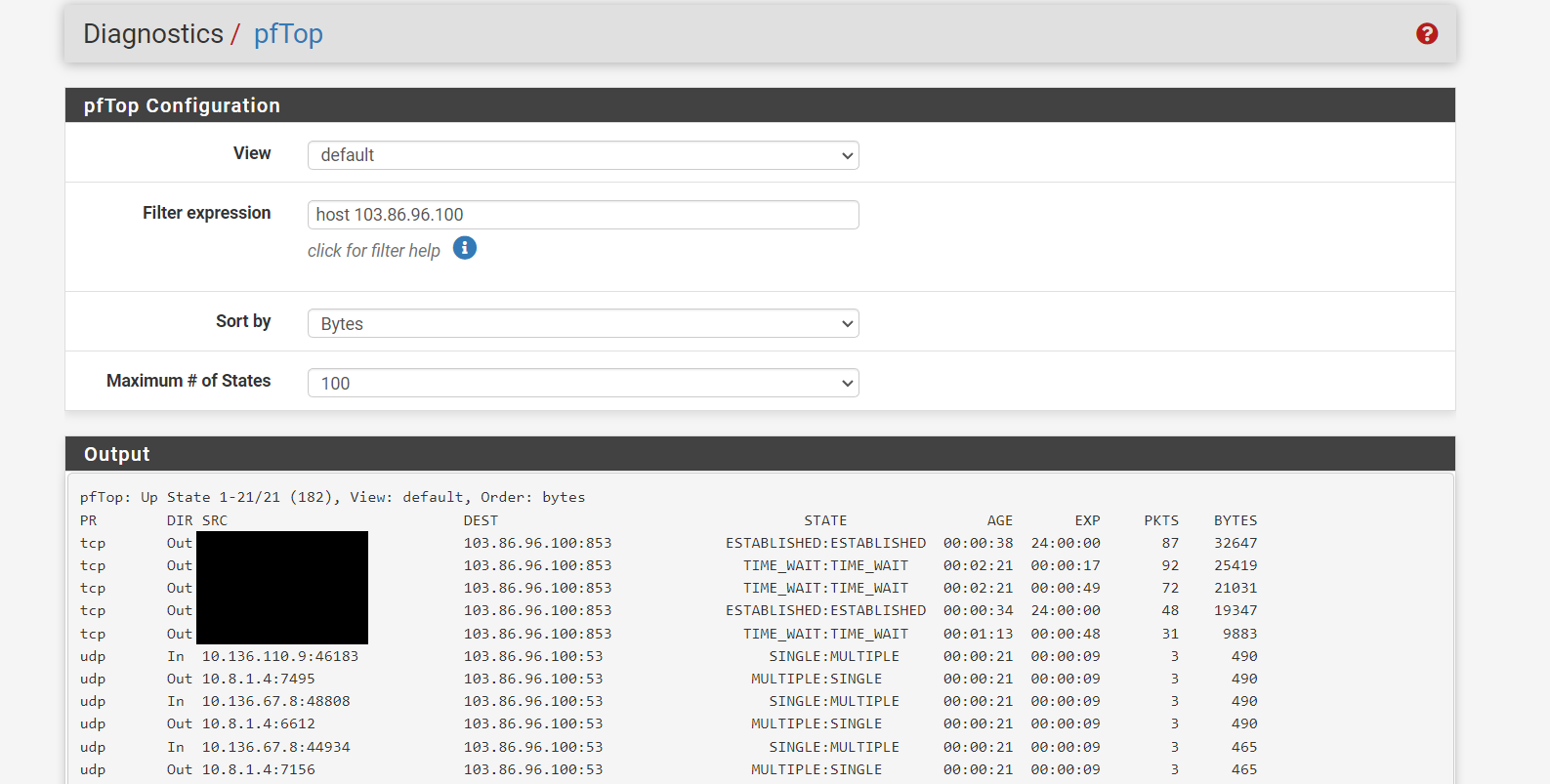
A final point I find hard to grasp are the floating firewall rules that are suggested in the Setup Guide for DNS over TLS. I do not understand why floating rules are needed. In my previous implementation I was guaranteeing that all my internal subnets/vlans could access DNS but nothing else on the firewall with these two rules (which I specified for each internal vlan)
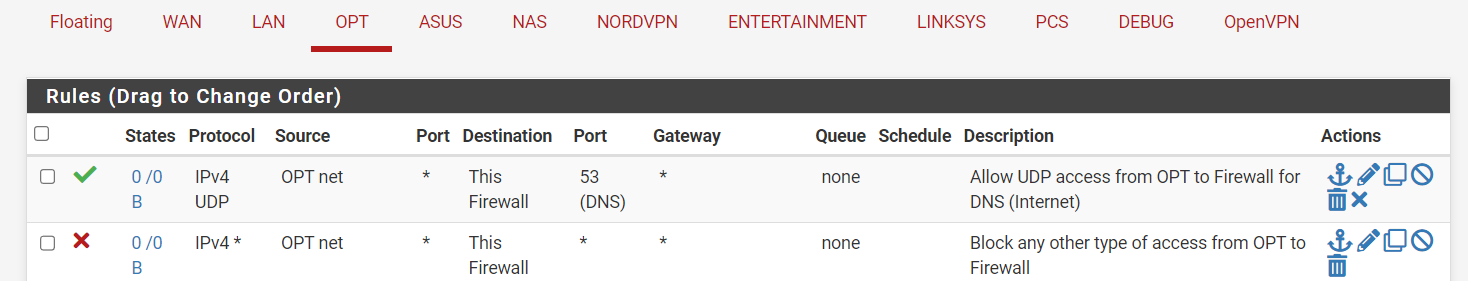
By modifying the first rule as below (i.e., changing protocol from UDP to TCP and port from 53 to 853), wouldn't the two rules below achieve the equivalent results of those floating rules, by directing all DNS queries to port 853 and blocking access to 53? Or would I need additional firewall rules in WAN and NORDVPN_VPNV4 as well to specify access to the DNS servers (as one of the floating rules does)?
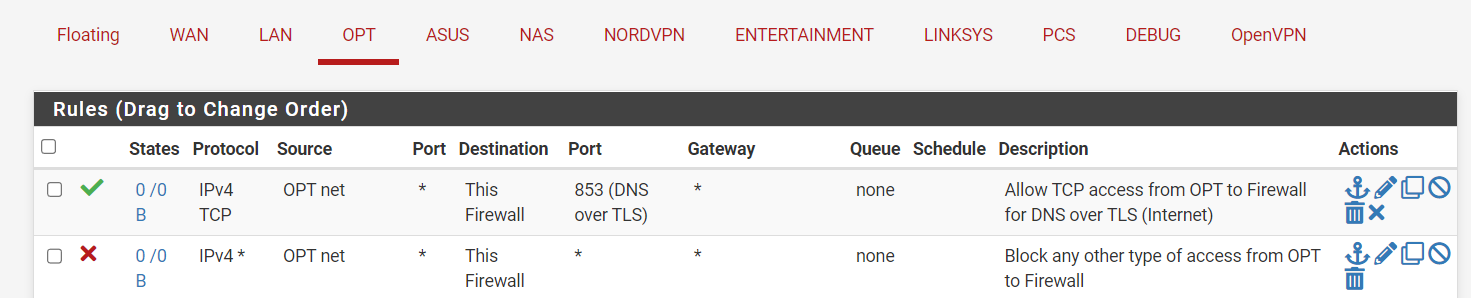
Thanks to everyone brave enough to make it till here. I really appreciate any recommendation on the best DNS configuration for my two-gateway setup and also on the best way to verify if it is working as expected. It seems to me that all these dns leak detectors on the web (e.g., dnsleaktest.com) are only partially useful to vet a DNS connection because they only allow to check if the DNS queries go to the expected server, but they do not show whether the query is encrypted or not.
-
@italnsd An additional variable. I was wondering whether having selected UDP over IPV4 as protocol when I set up NordVPN as OpenVPN client had any effects on the DNS configurations I showed. I have changed it to TCP over IPV4, but I do not seem to see any significant difference in pfTop, which again might be just a problem of me not really knowing where is the relevant info to look at