webConfigurator certificate expiry notification - any action required?
-
I recently enabled SMTP notifications and today I received this:
3:01:00 The following CA/Certificate entries are expiring:
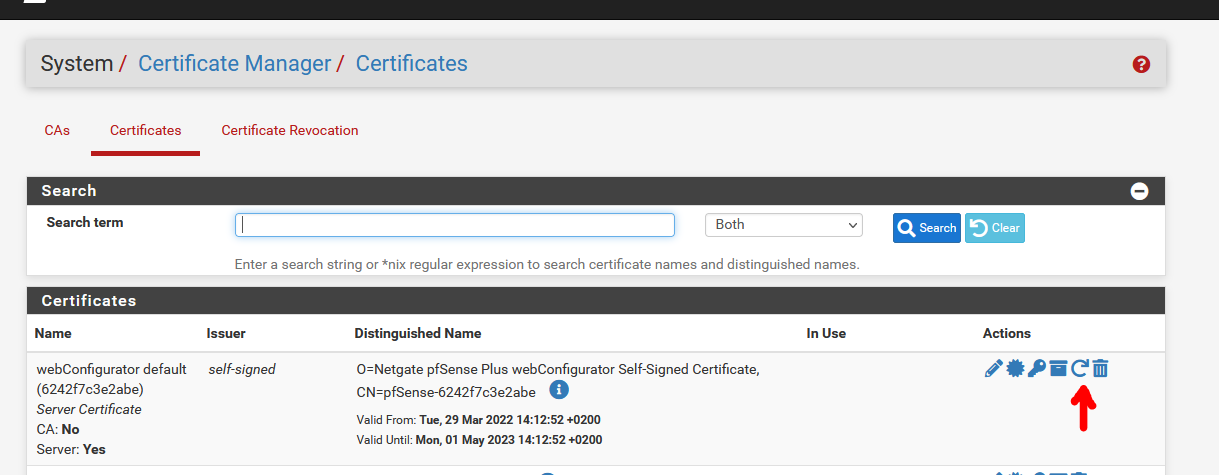
Certificate: webConfigurator default (611e6eab692a2) (611e6eab692a2): Expiring soon, in 27 daysDo I need to take any action here? Or will the certificate auto-renew and the notification is more just an FYI?
Thanks.
-
-
@gertjan Thanks, that did the trick. Bit surprised there isn't an auto-renew mechanism for this certificate. Ah well, it is only once a year so no big deal I guess.
-
@chrisjenk said in webConfigurator certificate expiry notification - any action required?:
isn't an auto-renew mechanism for this certificate
I never have to click or think about renewing my pfSense GUI cert.
I chose not to use mine - the one I showed above. As you can see, it's not 'in use'.The mechanism is : I'm using :
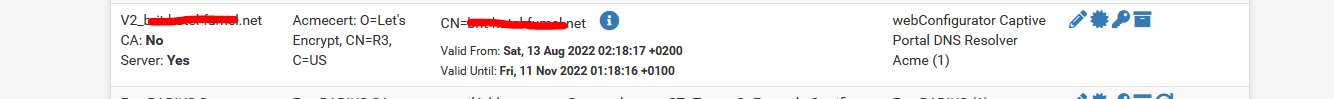
and that one is renewed automatically
 Every 60 days to be exact.
Every 60 days to be exact.And true , isn't not free : about 6 $ a year (the price of a dot net domain name).
-
@gertjan I use (free) Let's Encrypt certificates elsewhere for my domain(s). I was wondering if it was possible to set something similar up for pfSense, though as the Web GUI is not accessible outside of my LAN there is no real need. Is there an automatic Lets's Encrypt setup in pfSense for this (I couldn't immediately find one) or did you have to set this up manually? Of course, for normal Let's Encrypt setup/renewal various things need to be publicly resolvable/accessible, which for me is a bit of a no-no.
-
You can use the ACME package:
https://docs.netgate.com/pfsense/en/latest/packages/acme/index.htmlSteve
-
@chrisjenk
Letsencrypt is free, of course. Not the domain name you have to handover. Hence the 6$ I mentioned.@chrisjenk said in webConfigurator certificate expiry notification - any action required?:
Is there an automatic Lets's Encrypt setup in pfSense for this
You've missed
and

@chrisjenk said in webConfigurator certificate expiry notification - any action required?:
there is no real need
Agreed.
My 'need' is based on 3 reasons :- I use it (pfSense ACME + Letsencrypt) ) because I rent so many domain names already, one more at the end of the year won't bite me.
- And because I have pfSense at my fingertips daily, I can play with acme/Letsencrypt, try things out, and when I mess up it won't be a big deal. This is not the same for my web servers and mail servers : a cert error will break a lot, as with mails, for example, I use "DANE" and the smallest error wilt halt all mail traffic == dangerous for the company.
- I wanted to understand "how it works", as I say a lot (to myself) that all this isn't rocket science any more, but certificates, TLS etc is most often completely not understood, but it is also very important these days.
The only advantage I have when I use Letencrypt certs on my pfSense (actually all my local devices with a GUI) : all my devices trust the GUI out of the box - no need to click some extra "yeah yeah yeah I know, it's Ok -make an exception please".
-
@gertjan Makes sense. Thanks for the info/explanation. Good to know this is available should it be necessary.