Another wierd routing issue. Adding an OpenVPN Server breaks port forwarding on another WAN Link.
-
First the obliagtory diagram
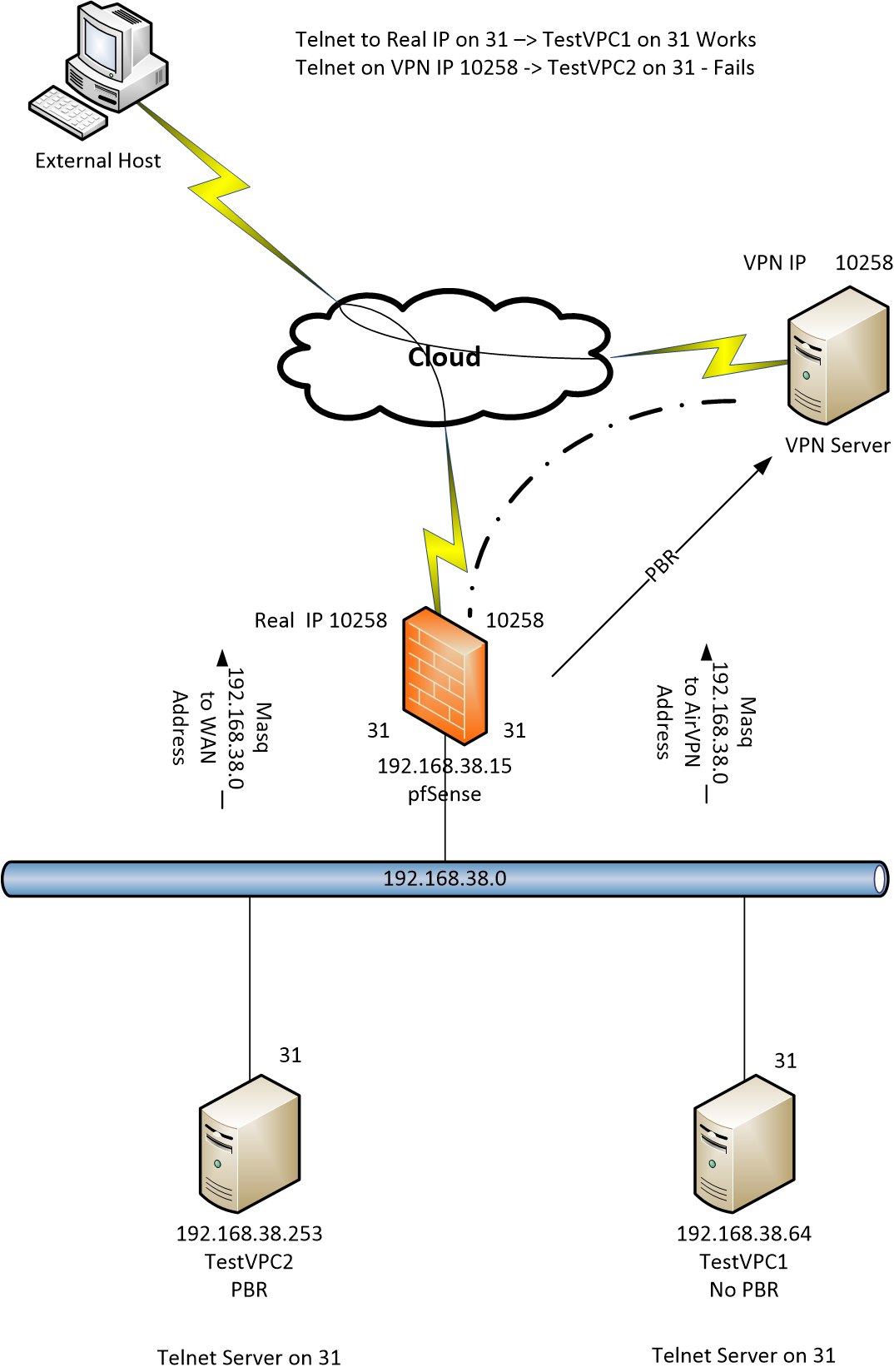
I use PBR to push some hosts down the VPN link, whilst other traffic uses the LAN.
On the WAN link I set a port forward from 10258 to 31 to a test PC that is off the encrypted_machine group. I have a telnet server on port 31 set up on this machine. The external host can see this server.I am using AirVPN, which support port forwarding. So I forward Port 10258 on AirVPN to port 31. On the firewall I then forward port 31 though to host TestVPC2 which is on the encrypted group. The external server can get access via "telnet airvpn.org IP 10258" - this works
However, if I add a VPN server (Open VPN, Port 1194 on WAN). I use a completely unused IP range for the tunnel with access to 192.168.38.0
And this stops the port forwarding on the AirVPN Interface!!
Removing the rule on the OpenVPN returns the port forward to successNow the question is can I repeat this. Yes. I created a new VPN Server (using old certs) and the port forward now fails again.
I know that removing the server and rules fixes things - but what happens if I split that downDisable OpenVPN Server - Telnet does not work - re-enable
Disable OpenVPN rule (incoming on OpenVPN Interface) - telnet works - re-enable (and does not work)
Disable OpenVPN rule (oncoming on WAN Interface) - telnet fails - re-enableLooking at the rule (incoming on OpenVPN) its kinda all encompassing - but there is nothing wrong with it that I can see

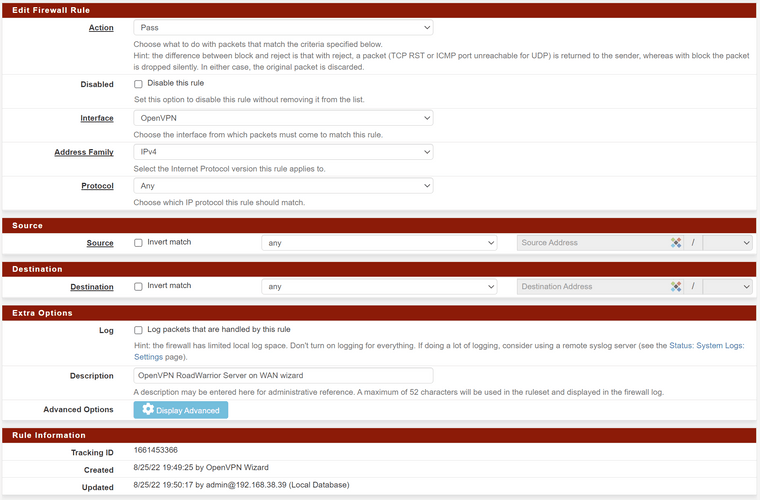
Have I found a bug?