Need help configuring PfSense on Protecli Vault
-
This post is deleted! -
@fiyawall
Add your own mappings.
Forget about the lines 500 (ISAKMP), as you probably not need them.Add your mapping rules for 127.0.0.0/8 - WAN and all your interfaces, like mine :
192.168.1.0/24 WAN ( my LAN )
192.168.2.0/24 WAN (my OPT1 )
192.168.3.0/24 WAN (my OPENVPNINTERFACE)
192.168..100.0/24 WAN (another OPT2) -
i dont know why that confused me. i guess i was looking for an upload tab. Thanks.
well here it is:
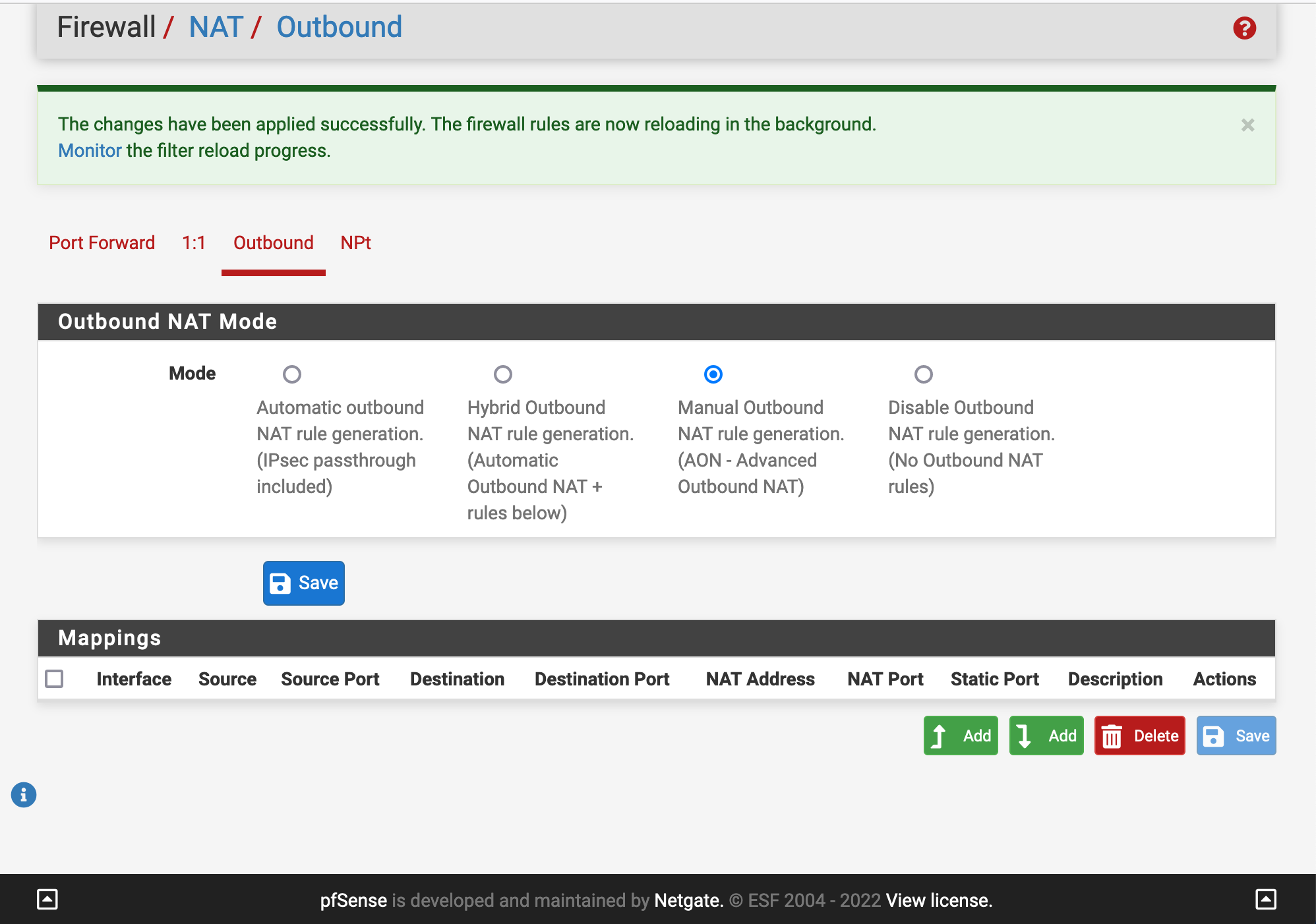
-
This post is deleted! -
Not sure what to do. It seems like pfsense 2.6 doesn’t have the same dispaly on the outbound section. Maybe I could download 2.5 somewhere? Any ideas?
-
@fiyawall
Hey there,
Have you tried clicking one of the "add" buttons (green)?
Then just fill in as shown in Screenshot posted by @Gertjan
Then "save" or apply...No, you should not look for an older pfsense version, rather look for a newer book. Or still better, read that book. Try to understand the way it works then apply that knowledge no matter how the gui looks...basics do not change. :)
Also, netgate's documentary is quite good... -
Thing is I honestly don’t even understand what I’m doing, so I don’t know how to follow those instructions above for manually mapping.
I’m a total novice when it comes to this stuff. I was following step by step instructions until that one point.
-
Setting up pfSense doesn't need you to visit the Outbound NAT page, less alone remove it from Automatic outbound NAT rule generation. (IPsec passthrough included) to Automatic outbound NAT rule generation. (IPsec passthrough included) or the hybrid mode.
Depending your interfaces creates, you should have this :
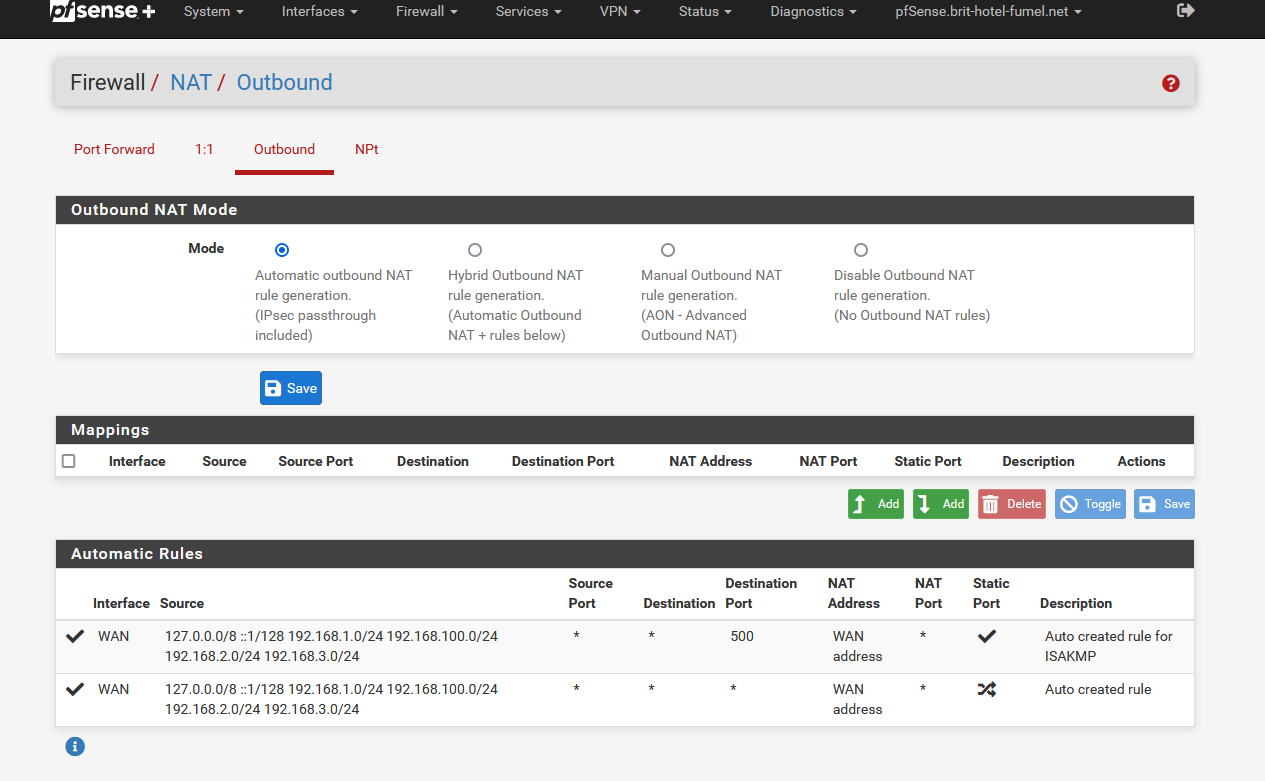
and this will work out of the box.
When you see "(IPsec passthrough included)" and you don't use, or don't plan to use IPSEC, you might as well delete (or not create) the rule that mentions "Auto created rule for ISAKMP ".
You know that the page is on the NAT tab.
What this means (my words, so bare with me):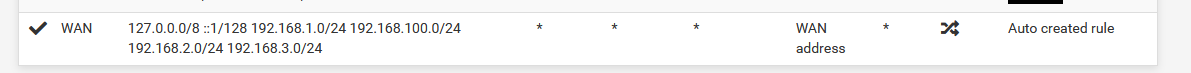
For devices on any LAN type network (LAN, OPTx, OpenVPNclient instance), for any outgoing connections from this LAN to the WAN, LAN addresses in the traffic have to be remapped from, for example, 192.168.100.2 to the WAN address, and then send to the destination somewhere on WAN (somewhere on the Internet).
When info comes back, pfSense knows now how to remap the traffic (packets) back again to the right LAN type address.When you have a multi WAN setup, or a WAN plus an OpenVPN client setup, you might want to choose what traffic, from what LAN, goes to what WAN or outgoing interface.
That's where this page comes into play.
For 95 % of all pfSense users, you will never have to visit this page.
Now read Outbound NAT.
And telle me, what documentation are you reading, that it tells you to edit these settings ?
I'll bet it's related to an OpenVPN client setup ;) -
It is from a book focused on privacy. So the goal is to instal pfsense on my protecli firewall which routes all my internet traffic through my ProtonVPN.
Apparantly this step is where this is made possible. I’ve already configured the router and the ports and everything.
Maybe if I supplied the text in the book it might help. I’ll try to decipher what you wrote here
-
So your issue isn't NAT, but more a how to set up a OpenVPN client to XXXVPN with pfSense as a client.
This page https://protonvpn.com/support/pfsense-2-6-x-vpn-setup/ seems actual to me.
Still, before you proceed, I advise you to read about the subject. Intermixed with some youtube videos. And even if they are old, look also the videos from here.
If you don't 'master' this subject, you won't be adding security and privacy, it will be more matter of danger (insecurity) for yourself, or plain routing issues.
Btw : you are aware of the fact that everything that enters and leaves your home, through the WAN interface, is already TLS encrypted. If not, then stop now retrieving and sending mails "in clear", and stop visiting "http" sites, use only https sites ;)
If DNS worries you, forward over TLS to some TLS capable DNS resolver like 1.1.1.1.
Now, your ISP can only see the IPs your visiting. IMHO, that can't be a big deal. -
@gertjan Hi so actually, the author of this book has some custom scripts on his website. This is to make the process easier for configuring the firewall.
So i went ahead and uploaded a custom script with all the settings i need.
However, my issue now is that in the "status" of "OpenVPN" is never showing as "up". It is either "pending" or "down" or "failed". See
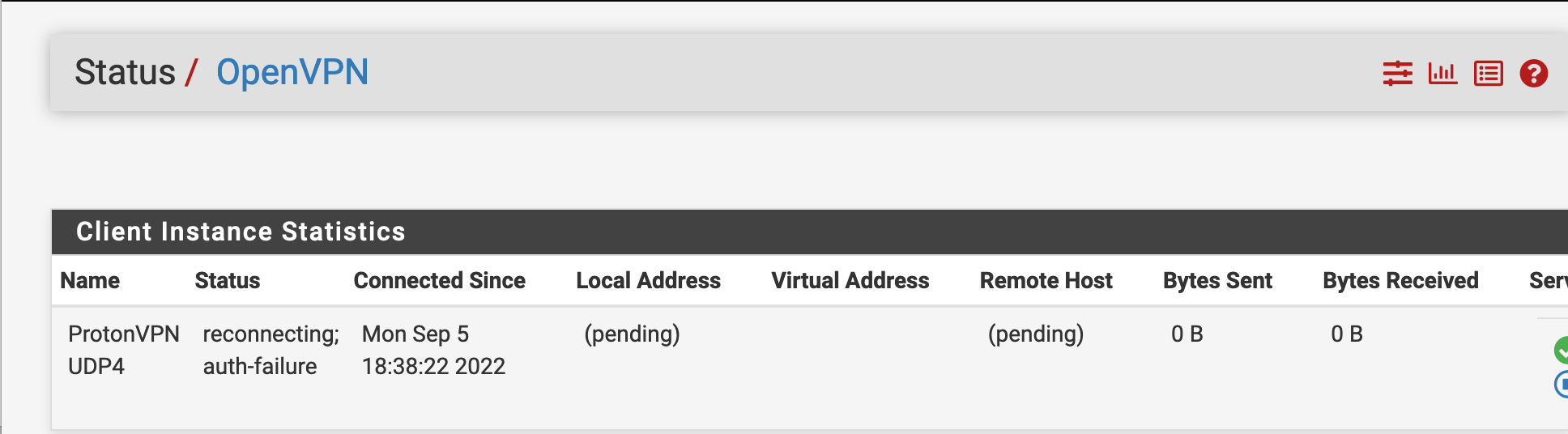 :
:Part of the additional instructions is to designate a custom server IP address from my ProtonVPN service. Basically you choose a server from a list on ProtonVPN's site, and then download a file. I was instructed to open it in a text editor and identify the IP address and manually enter it. That way all my internet traffic is being routed through that specific server.
However, in the file looks like this:
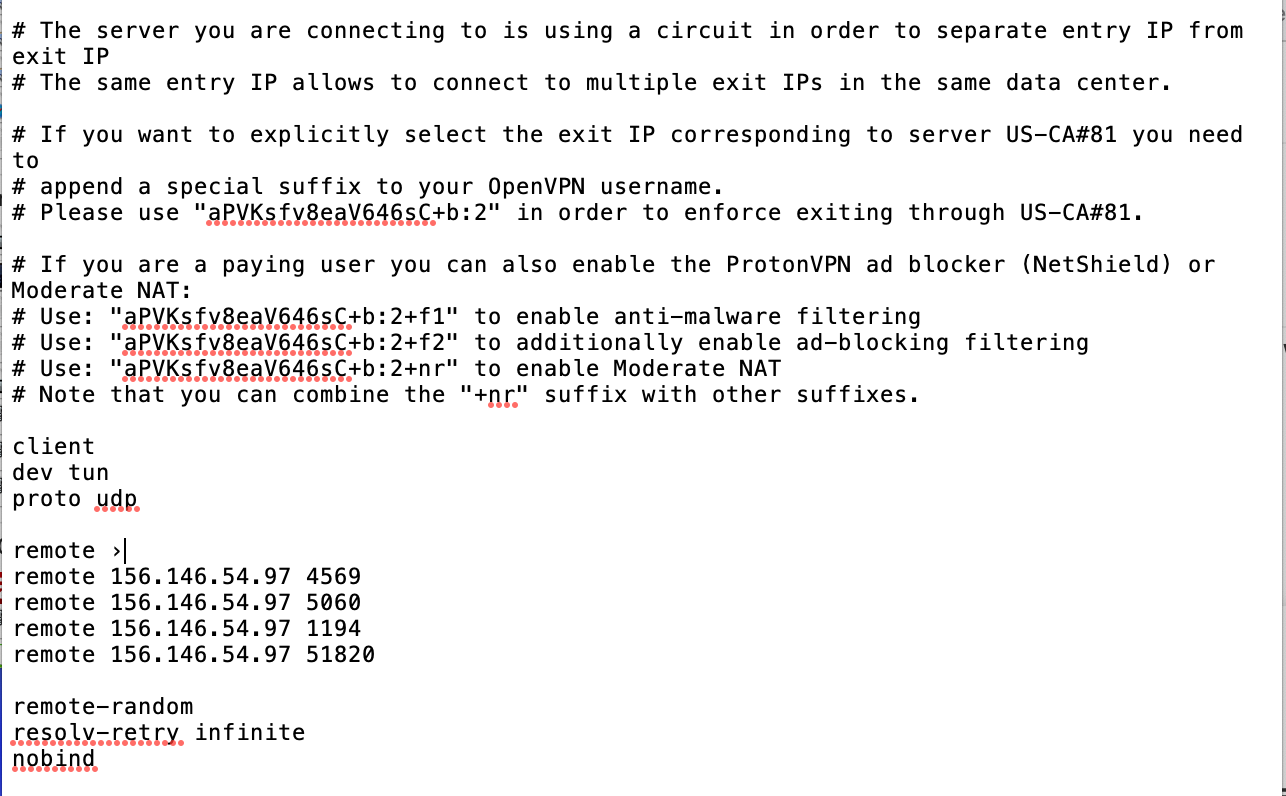
If i enter any of those full IP addresses, it gives an error, saying its no t a valid address. When i use the root address 156.146.54.97, it will accept it. So i'm not sure if that is correct or not.
In the end, my status on OpenVPN is not showing "up" and thats the end goal according to my instructions.
Any ideas?