IPSEC VPN Windows11
-
Hi,
my pfsense setup for the mobile Client works fine. Today i will setup the first windows11 client and it doesn't ;-(
So i struggle with this and have "no idea" to fix it.The "small information" about the VPN Configuration
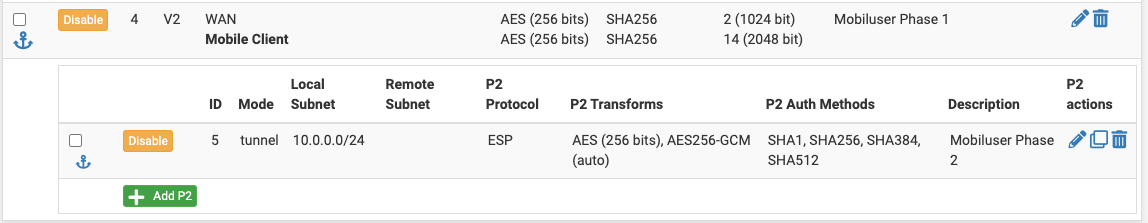
The error message on the client
and the error message on the pfsense
Aug 29 12:28:05 charon 40448 05[CFG] <130812> looking for an IKEv2 config for 116.202.109.180...37.84.117.22 Aug 29 12:28:06 charon 40448 05[CFG] <130812> candidate: 116.202.109.180...0.0.0.0/0, ::/0, prio 1052 Aug 29 12:28:06 charon 40448 05[CFG] <130812> found matching ike config: 116.202.109.180...0.0.0.0/0, ::/0 with prio 1052 Aug 29 12:28:06 charon 40448 05[IKE] <130812> local endpoint changed from 0.0.0.0[500] to 116.202.109.180[500] Aug 29 12:28:06 charon 40448 05[IKE] <130812> remote endpoint changed from 0.0.0.0 to 37.84.117.22[500] Aug 29 12:28:06 charon 40448 05[IKE] <130812> 37.84.117.22 is initiating an IKE_SA Aug 29 12:28:06 charon 40448 05[IKE] <130812> IKE_SA (unnamed)[130812] state change: CREATED => CONNECTING Aug 29 12:28:06 charon 40448 05[CFG] <130812> selecting proposal: Aug 29 12:28:06 charon 40448 05[CFG] <130812> no acceptable DIFFIE_HELLMAN_GROUP found Aug 29 12:28:06 charon 40448 05[CFG] <130812> selecting proposal: Aug 29 12:28:06 charon 40448 05[CFG] <130812> no acceptable DIFFIE_HELLMAN_GROUP found Aug 29 12:28:06 charon 40448 05[CFG] <130812> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_8192 Aug 29 12:28:06 charon 40448 05[CFG] <130812> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Aug 29 12:28:06 charon 40448 05[CFG] <130812> looking for IKEv2 configs for 116.202.109.180...37.84.117.22 Aug 29 12:28:06 charon 40448 05[CFG] <130812> candidate: 116.202.109.180...0.0.0.0/0, ::/0, prio 1052 Aug 29 12:28:06 charon 40448 05[IKE] <130812> remote host is behind NAT Aug 29 12:28:06 charon 40448 05[IKE] <130812> received proposals unacceptable Aug 29 12:28:06 charon 40448 05[ENC] <130812> generating IKE_SA_INIT response 0 [ N(NO_PROP) ] Aug 29 12:28:06 charon 40448 05[NET] <130812> sending packet: from 116.202.109.180[500] to 37.84.117.22[500] (36 bytes) Aug 29 12:28:06 charon 40448 05[IKE] <130812> IKE_SA (unnamed)[130812] state change: CONNECTING => DESTROYINGso i cant't belive that the proposals should be wrong. Does i need for the windows11 other?
Can someone give me a hint or solution?THX Stefan
-
@stefanr From the log it seems your Windows 11 is setup to use DH Group 18 only (8192 bit). So you should change your Phase 1 settings to accept DH Group 18, or use powershell on Windows 11 to reconfigure the VPN settings to DH group 14 (2048 bit) like your current pfSense Phase 1
-
THX, i check this last time... so i create the "missing" phase1 DH Group18 (8192 bit).
After this, the VPN is also not connecting...Aug 29 23:59:57 charon 40448 15[NET] <133789> received packet: from XX.XXX.XXX.XXX[500] to XXX.XXX.XXX.XXX[500] (1104 bytes) Aug 29 23:59:57 charon 40448 15[ENC] <133789> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V V ] Aug 29 23:59:57 charon 40448 15[CFG] <133789> looking for an IKEv2 config for XXX.XXX.XXX.XXX...XX.XXX.XXX.XXX Aug 29 23:59:57 charon 40448 15[CFG] <133789> candidate: XXX.XXX.XXX.XXX...0.0.0.0/0, ::/0, prio 1052 Aug 29 23:59:57 charon 40448 15[CFG] <133789> found matching ike config: XXX.XXX.XXX.XXX...0.0.0.0/0, ::/0 with prio 1052 Aug 29 23:59:57 charon 40448 15[IKE] <133789> local endpoint changed from 0.0.0.0[500] to XXX.XXX.XXX.XXX[500] Aug 29 23:59:57 charon 40448 15[IKE] <133789> remote endpoint changed from 0.0.0.0 to XX.XXX.XXX.XXX[500] Aug 29 23:59:57 charon 40448 15[IKE] <133789> received MS NT5 ISAKMPOAKLEY v9 vendor ID Aug 29 23:59:57 charon 40448 15[IKE] <133789> received MS-Negotiation Discovery Capable vendor ID Aug 29 23:59:57 charon 40448 15[IKE] <133789> received Vid-Initial-Contact vendor ID Aug 29 23:59:57 charon 40448 15[ENC] <133789> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02 Aug 29 23:59:57 charon 40448 15[IKE] <133789> XX.XXX.XXX.XXX is initiating an IKE_SA Aug 29 23:59:57 charon 40448 15[IKE] <133789> IKE_SA (unnamed)[133789] state change: CREATED => CONNECTING Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable ENCRYPTION_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> no acceptable INTEGRITY_ALGORITHM found Aug 29 23:59:57 charon 40448 15[CFG] <133789> selecting proposal: Aug 29 23:59:57 charon 40448 15[CFG] <133789> proposal matches Aug 29 23:59:57 charon 40448 15[CFG] <133789> received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_128/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_192/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_192/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_192/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_GCM_16_128/PRF_HMAC_SHA1/MODP_1024, IKE:AES_GCM_16_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_GCM_16_128/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_GCM_16_256/PRF_HMAC_SHA1/MODP_1024, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/MODP_1024 Aug 29 23:59:57 charon 40448 15[CFG] <133789> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_8192 Aug 29 23:59:57 charon 40448 15[CFG] <133789> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024 Aug 29 23:59:57 charon 40448 15[IKE] <133789> remote host is behind NAT Aug 29 23:59:57 charon 40448 15[IKE] <133789> sending cert request for "CN=pfsense-ca, C=DE, ST=XXX, L=XXX, O=XXXX" Aug 29 23:59:57 charon 40448 15[ENC] <133789> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ] Aug 29 23:59:57 charon 40448 15[NET] <133789> sending packet: from XXX.XXX.XXX.XXX[500] to XX.XXX.XXX.XXX[500] (353 bytes) Aug 29 23:59:58 charon 40448 15[NET] <133789> received packet: from XX.XXX.XXX.XXX[4500] to XXX.XXX.XXX.XXX[4500] (580 bytes) Aug 29 23:59:58 charon 40448 15[ENC] <133789> parsed IKE_AUTH request 1 [ EF(1/3) ] Aug 29 23:59:58 charon 40448 15[IKE] <133789> local endpoint changed from XXX.XXX.XXX.XXX[500] to XXX.XXX.XXX.XXX[4500] Aug 29 23:59:58 charon 40448 15[IKE] <133789> remote endpoint changed from XX.XXX.XXX.XXX[500] to XX.XXX.XXX.XXX[4500] Aug 29 23:59:58 charon 40448 15[ENC] <133789> received fragment #1 of 3, waiting for complete IKE message Aug 29 23:59:58 charon 40448 15[NET] <133789> received packet: from XX.XXX.XXX.XXX[4500] to XXX.XXX.XXX.XXX[4500] (580 bytes) Aug 29 23:59:58 charon 40448 15[ENC] <133789> parsed IKE_AUTH request 1 [ EF(2/3) ] Aug 29 23:59:58 charon 40448 15[ENC] <133789> received fragment #2 of 3, waiting for complete IKE message Aug 29 23:59:58 charon 40448 15[NET] <133789> received packet: from XX.XXX.XXX.XXX[4500] to XXX.XXX.XXX.XXX[4500] (548 bytes) Aug 29 23:59:58 charon 40448 15[ENC] <133789> parsed IKE_AUTH request 1 [ EF(3/3) ] Aug 29 23:59:58 charon 40448 15[ENC] <133789> received fragment #3 of 3, reassembled fragmented IKE message (1536 bytes) Aug 29 23:59:58 charon 40448 15[ENC] <133789> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 0e:ac:82:60:40:56:27:97:e5:25:13:fc:2a:e1:0a:53:95:59:e4:a4 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid dd:bc:bd:86:9c:3f:07:ed:40:e3:1b:08:ef:ce:c4:d1:88:cd:3b:15 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 4a:5c:75:22:aa:46:bf:a4:08:9d:39:97:4e:bd:b4:a3:60:f7:a0:1d Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 5c:b8:69:fe:8d:ef:c1:ed:66:27:ee:b2:12:0f:72:1b:b8:0a:0e:04 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 6a:47:a2:67:c9:2e:2f:19:68:8b:9b:86:61:66:95:ed:c1:2c:13:00 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 01:f0:33:4c:1a:a1:d9:ee:5b:7b:a9:de:43:bc:02:7d:57:09:33:fb Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 88:a9:5a:ef:c0:84:fc:13:74:41:6b:b1:63:32:c2:cf:92:59:bb:3b Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid f9:27:b6:1b:0a:37:f3:c3:1a:fa:17:ec:2d:46:17:16:12:9d:0c:0e Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 34:4f:30:2d:25:69:31:91:ea:f7:73:5c:ab:f5:86:8d:37:82:40:ec Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 3e:df:29:0c:c1:f5:cc:73:2c:eb:3d:24:e1:7e:52:da:bd:27:e2:f0 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 7c:32:d4:85:fd:89:0a:66:b5:97:ce:86:f4:d5:26:a9:21:07:e8:3e Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 08:a0:8e:a8:20:e0:1a:b3:dd:ca:39:a8:d7:64:21:56:9c:ca:d5:df Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 64:1d:f8:d5:0e:23:31:c2:29:b2:50:cb:32:f5:6d:f5:5c:8e:00:fa Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid e1:a0:5a:95:34:75:78:a7:ff:4d:cf:32:52:5d:f2:f8:2c:1a:e1:15 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 87:e3:bf:32:24:27:c1:40:5d:27:36:c3:81:e0:1d:1a:71:d4:a0:39 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 5e:8c:53:18:22:60:1d:56:71:d6:6a:a0:cc:64:a0:60:07:43:d5:a8 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 86:26:cb:1b:c5:54:b3:9f:bd:6b:ed:63:7f:b9:89:a9:80:f1:f4:8a Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid ed:0d:c8:d6:2c:d3:13:29:d8:82:fe:2d:c3:fc:c5:10:d3:4d:bb:14 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid a8:e3:02:96:70:a6:8b:57:eb:ec:ef:cc:29:4e:91:74:9a:d4:92:38 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid b5:99:33:43:ac:a2:17:c5:08:ba:88:8c:a6:92:7e:26:b3:0f:87:a9 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid f7:93:19:ef:df:c1:f5:20:fb:ac:85:55:2c:f2:d2:8f:5a:b9:ca:0b Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 30:a4:e6:4f:de:76:8a:fc:ed:5a:90:84:28:30:46:79:2c:29:15:70 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid c4:30:28:c5:d3:e3:08:0c:10:44:8b:2c:77:ba:24:53:97:60:bb:f9 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid f8:16:51:3c:fd:1b:44:9f:2e:6b:28:a1:97:22:1f:b8:1f:51:4e:3c Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 73:97:82:ea:b4:04:16:6e:25:d4:82:3c:37:db:f8:a8:12:fb:cf:26 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 9b:10:82:7a:95:03:2a:b2:6b:73:c8:2f:18:c9:2e:ca:e5:68:c2:08 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 69:c4:27:db:59:69:68:18:47:e2:52:17:0a:e0:e5:7f:ab:9d:ef:0f Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid ba:42:b0:81:88:53:88:1d:86:63:bd:4c:c0:5e:08:fe:ea:6e:bb:77 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 87:db:d4:5f:b0:92:8d:4e:1d:f8:15:67:e7:f2:ab:af:d6:2b:67:75 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 6e:58:4e:33:75:bd:57:f6:d5:42:1b:16:01:c2:d8:c0:f5:3a:9f:6e Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 4a:81:0c:de:f0:c0:90:0f:19:06:42:31:35:a2:a2:8d:d3:44:fd:08 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid d5:2e:13:c1:ab:e3:49:da:e8:b4:95:94:ef:7c:38:43:60:64:66:bd Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid d3:94:8a:4c:62:13:2a:19:2e:cc:af:72:8a:7d:36:d7:9a:1c:dc:67 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid ab:30:d3:af:4b:d8:f1:6b:58:69:ee:45:69:29:da:84:b8:73:94:88 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid a5:9d:bf:90:15:d9:f1:f5:a8:d8:c0:1d:14:e6:f1:d8:c4:fe:57:17 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid e2:7f:7b:d8:77:d5:df:9e:0a:3f:9e:b4:cb:0e:2e:a9:ef:db:69:77 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 6d:aa:9b:09:87:c4:d0:d4:22:ed:40:07:37:4d:19:f1:91:ff:de:d3 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 3e:51:59:8b:a7:6f:54:5c:77:24:c5:66:eb:aa:fb:3e:2b:f3:ac:4f Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid fd:da:14:c4:9f:30:de:21:bd:1e:42:39:fc:ab:63:23:49:e0:f1:84 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 3e:18:e5:44:f6:bd:4d:77:50:28:c9:40:3e:5c:74:f5:4c:d9:60:29 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 3e:22:d4:2c:1f:02:44:b8:04:10:65:61:7c:c7:6b:ae:da:87:29:9c Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 55:e4:81:d1:11:80:be:d8:89:b9:08:a3:31:f9:a1:24:09:16:b9:70 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 74:0b:0c:d2:1b:e6:a5:01:5e:02:42:a4:0b:e7:f1:b7:bc:bd:42:93 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid b1:81:08:1a:19:a4:c0:94:1f:fa:e8:95:28:c1:24:c9:9b:34:ac:c7 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 21:0f:2c:89:f7:c4:cd:5d:1b:82:5e:38:d6:c6:59:3b:a6:93:75:ae Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid e6:ff:c3:94:e8:38:59:7f:51:d4:80:42:19:76:27:cf:db:94:8e:c6 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid bb:c2:3e:29:0b:b3:28:77:1d:ad:3e:a2:4d:bd:f4:23:bd:06:b0:3d Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid c8:95:13:68:01:97:28:0a:2c:55:c3:fc:d3:90:f5:3a:05:3b:c9:fb Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid ee:e5:9f:1e:2a:a5:44:c3:cb:25:43:a6:9a:5b:d4:6a:25:bc:bb:8e Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 67:ec:9f:90:2d:cd:64:ae:fe:7e:bc:cd:f8:8c:51:28:f1:93:2c:12 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 17:4a:b8:2b:5f:fb:05:67:75:27:ad:49:5a:4a:5d:c4:22:cc:ea:4e Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received cert request for unknown ca with keyid 4f:9c:7d:21:79:9c:ad:0e:d8:b9:0c:57:9f:1a:02:99:e7:90:f3:87 Aug 29 23:59:58 charon 40448 15[IKE] <133789> received 54 cert requests for an unknown ca Aug 29 23:59:58 charon 40448 15[CFG] <133789> looking for peer configs matching XXX.XXX.XXX.XXX[%any]...XX.XXX.XXX.XXX[192.168.2.101] Aug 29 23:59:58 charon 40448 15[CFG] <133789> candidate "con-mobile", match: 1/1/1052 (me/other/ike) Aug 29 23:59:58 charon 40448 15[CFG] <con-mobile|133789> selected peer config 'con-mobile' Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> initiating EAP_IDENTITY method (id 0x00) Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> processing INTERNAL_IP4_ADDRESS attribute Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> processing INTERNAL_IP4_DNS attribute Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> processing INTERNAL_IP4_NBNS attribute Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> processing INTERNAL_IP4_SERVER attribute Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> processing INTERNAL_IP6_ADDRESS attribute Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> processing INTERNAL_IP6_DNS attribute Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> processing INTERNAL_IP6_SERVER attribute Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> peer supports MOBIKE Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> authentication of 'gateway.XXX.de' (myself) with RSA signature successful Aug 29 23:59:58 charon 40448 15[IKE] <con-mobile|133789> sending end entity cert "CN=gateway.XXX.de, C=DE, ST=XXX, L=XXX, O=XXX" Aug 29 23:59:58 charon 40448 15[ENC] <con-mobile|133789> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ] Aug 29 23:59:58 charon 40448 15[ENC] <con-mobile|133789> splitting IKE message (1632 bytes) into 2 fragments Aug 29 23:59:58 charon 40448 15[ENC] <con-mobile|133789> generating IKE_AUTH response 1 [ EF(1/2) ] Aug 29 23:59:58 charon 40448 15[ENC] <con-mobile|133789> generating IKE_AUTH response 1 [ EF(2/2) ] Aug 29 23:59:58 charon 40448 15[NET] <con-mobile|133789> sending packet: from XXX.XXX.XXX.XXX[4500] to XX.XXX.XXX.XXX[4500] (1236 bytes) Aug 29 23:59:58 charon 40448 15[NET] <con-mobile|133789> sending packet: from XXX.XXX.XXX.XXX[4500] to XX.XXX.XXX.XXX[4500] (468 bytes) Aug 30 00:00:27 charon 40448 07[JOB] <con-mobile|133789> deleting half open IKE_SA with XX.XXX.XXX.XXX after timeout Aug 30 00:00:27 charon 40448 07[IKE] <con-mobile|133789> IKE_SA con-mobile[133789] state change: CONNECTING => DESTROYINGso have you another hint?!
THX Stefan
-
i found the issue after changing the Phase1 settings.
The CA import from wasn't successful.After reimport... all works fine...
THX for your time and support...
Stefan