pfsense and Synology port forwarding
-
Hi,
I own a Synology NAS and had it configured with a certificate to access the NAS and various clients through the address https://xxxx.synology.me:xxxx
After installing pfsense, and port forwarding the appropriate ports I can access all clients from an external network using https://xxxx.synology.me:xxxx but I cannot access them from the internal LAN. I thought adding LAN rules in addition to the WAN rules would help but it doesn't.
Any tips on what could be preventing access?
Thanks,
-
First let me start by saying this is a HORRIBLE HORRIBLE idea.. Why would you open your nas to the public. Are you atleast locking it down to known IPs?
If you want users to access your nas - have them vpn to your network.
You have 2 options when trying to access your public dns name internally - nat reflection or host overrides (split dns) where you internal clients resolve the public fqdn to the local IP your forwarding to anyway.
Or there is the 3rd option haproxy.
The simple solution is to just use haproxy. 2nd best option is host override, the last option which is just an abomination to all things networking is nat reflection.
https://docs.netgate.com/pfsense/en/latest/recipes/port-forwards-from-local-networks.html
-
@johnpoz thanks for the response. Just setting up like a had before using a pfsense. Using a VPN sounds like the way to go.
Using the NAT reflection did solve the issue in the meanwhile. Cheers.
-
@johnpoz The use case here is potential similar to what I'm trying to configure for a friend.
NAS 1 at office replicating to NAS2 at home, it uses rsync over a ssh / port 22 connection, implying I need to port forward port22 on outside onto port22 on NAS.
Now i'lll rather use something like 8022 on outside to 22 on NAS... but still implies "opening" it up.
A much nicer idea would have been a solution by Synology where it does something like a reverse tunnel... where you list your own NAS's under you profile at Sinology allowing you to connect from one NAS to the other without things like DDNS etc
So far I haven't found a solution like that.
G -
@alric22 said in pfsense and Synology port forwarding:
https://xxxx.synology.me:xxxx
Synology where it does something like a reverse tunnel...
You're close.
If I need to access my diskstation from the outside, I fire up my OpenVPN first. This connects me to my home/office network.
Now I can access https://diskstation2.my-local-pfsense-LAN-network.net:5001/ as before.But, if you have to have access your NAS from the outside : https://xxxx.synology.me:xxxx, then that's ok. All it needs is a TCP NAT rule on pfSense. The "Synology Remote access" is nice .... for occasional home user access users.
Because you use a site to site, and if these WAN IPs are static, you can even change the NAT rule to use only one pre determined source IP. This way your NAT rule is pretty safe.Btw : I'm rsyncing my dedicated web/mail/dns servers to my synoo NAS at work.
I'm hiding somewhat the access, by not using IPv4 based NAT.
I connect to my syno NAS using it's IPv6 (less known, so less visible).
There is a IPv6 firewall rue that accepts only rsync tcp port 22 traffic from my servers using their IPv6. This way, I'm safe, and my servers can backup during the night using my syno.Here are my IPv6 WAN rules :
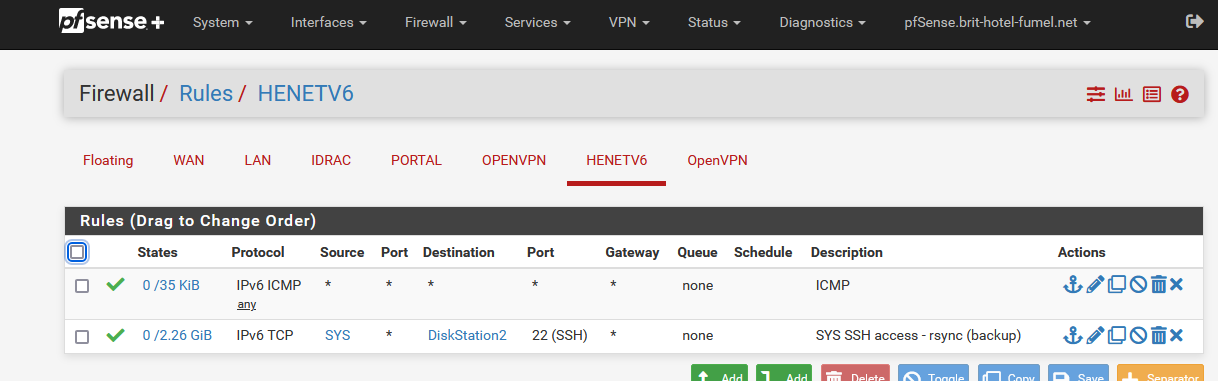
where the SYS alias is filled up with the IPv6 of all my servers on the Internet.
-
My use case is purely shared folder rsync.
got the pfsense port forward configured.
can locally on network ssh onto the NAS, but trying remote/via my external IP not getting in... lets dig dig dig.
G -
@georgelza said in pfsense and Synology port forwarding:
but trying remote/via my external IP not getting in... lets dig dig dig.
Stop digging ;)
Make a NAT rule - as I presume your still IPv4 based.
As shown above, with IPv6 : just a firewall pass and done - no NAT needed for IPv6.Here it is Port Forwards.
Have a look at See also as NATing a port is 30+ years old technology, so a 7 years old video will cover your needs just fine.
Keep in mind that you have to create a NAT rule for pfSense. pfSEnse is a firewall router.
If you have a ISP router on the pfSense WAN, you will have to create a NAT rule on this ISP firewall router also. -
@georgelza I run my pfSense as my edge router.
I have tried to do a Firewall/NAT. did not work. when trying to ssh to <NAS USER>@<DNS> 7922
with the NAT configured to take 7922 and redirect it to 22 on the NAS IP.
Did not work.
When I don't use 7922 and simply try 22 then it's trying to ssh into the pfSense itself. -
@gertjan interesting discovery, when I try and just ssh to the dns entry i noticed it was my pfsense wanting credentials and not the Synology to which I was trying to get... so scary... my port 22 is open on the WAN... now to close that... IMMEDIATELY ;)
G -
@georgelza might be answering my own panic. think it's actually my pfsense seeing my trying to get to port 22 on wan and seeing i'm coming from internal and predicting my onto internal interface, even though I specified my WAN address.
As I have a block all rule and I've dev not opened up port 22 on WAN.
All that makes sense. -
@georgelza did a little test.
have my dns maintained via Cloudflare,
so when I disable proxy, aka entering the dns name returns my WAN ip, then I can do this ssh to the dns entry,
when I enable proxy, other words dns return a ip different from the WAN ip then ssh fails.
making me believe the pfsense was auto redirecting my ssh from internal, realising I'm simply trying to ssh to itself and i'm on the LAN.Still does not fix my inability to get NAT configured for port 22, via a redirect of port 7922 on WAN to 22 on LAN/IP.
G -
@georgelza said in pfsense and Synology port forwarding:
my port 22 is open on the WAN... now to close that... IMMEDIATELY ;)
Its even worse.
By default the SSH is de activated. You've activate the SSH access. So, yeah ....
But, good news, pfSense is a firewall.
So, when you installed pfSEnse you found these rules on the WAN interface :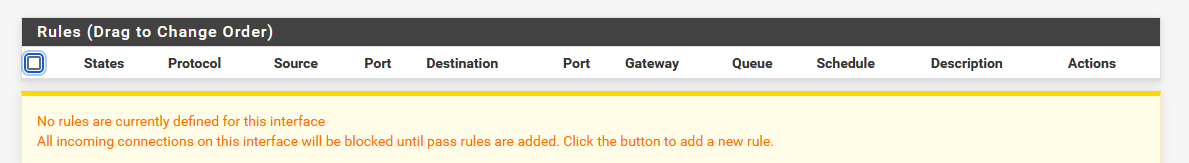
so nothing enters WAN.
So nothing i exposed.And before you de-activate SSH, take a look at the nginx process. It's the web server used by the GUI. Its also listening on the WAN interface ;)
So, back to the issue : don't worry,you'll manage.
We all open ports so devices on our LAN(s) can be used by others, from the Internet.
Look at the video's. -
@georgelza I"m actually not that worried about my pfSense, had a friend that's in the security game do a check for me before... to make sure it's locked up...
More stumped why I can't get it to take a external port and forward it onto port 22 on my internal NAS, so that i can get rsync working.
G -
This is my Synology NAS :
I'll give you a demo :
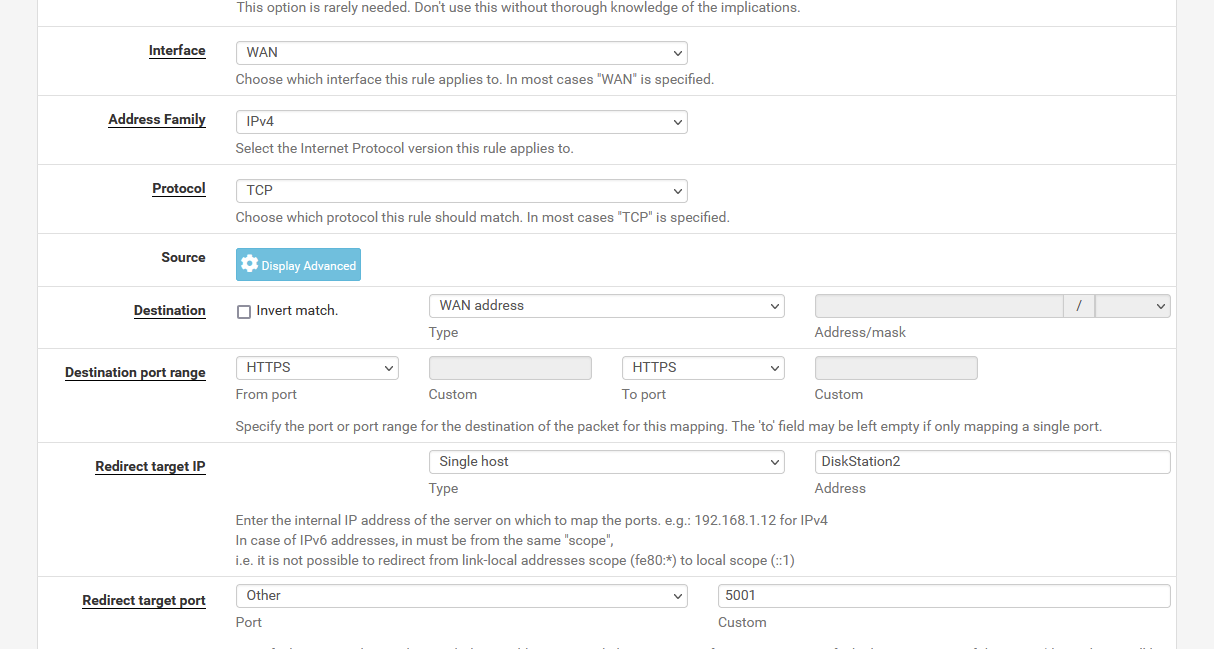
Count with me :
Protocol = TCP & IP = IPv4.
Destination == WAN Address is already filled in (as it would nearly always be "WAN Address")
Destination port range : 443
Target IP = my NAS LAN IPv4, or an alias pointing to it = 192.168.1.33
Redirect target port : 5001 ( because the NAS dies not use 443, it uses 5001)Knowing that 'diskstation2" is an alias for 192.168.1.33
The GUI of my (and your) NAS uses 5001 for the https access.Now, try it your for yourself : https://brit.test-domaine.fr
Your browser will probably complain : it knows that the cert I use on my NAS doesn't have 'brit.test-domaine.fr' in the SAN.
Just accept, and viola : you see the login screen of my NAS..I remove the NAT rule as soon as you saw my Syno liogin screen == as soon as you know how to do it ;)
You'll be using the default port 443 as https uses 443.
My NAT rule redirects (= PAT !) port 443 to 5001.I could have made as quickly a port "22" to "22" or "8022" to "22" for ssh or rsync access.
Keep in mind : check the firewall rule, created on WAN :
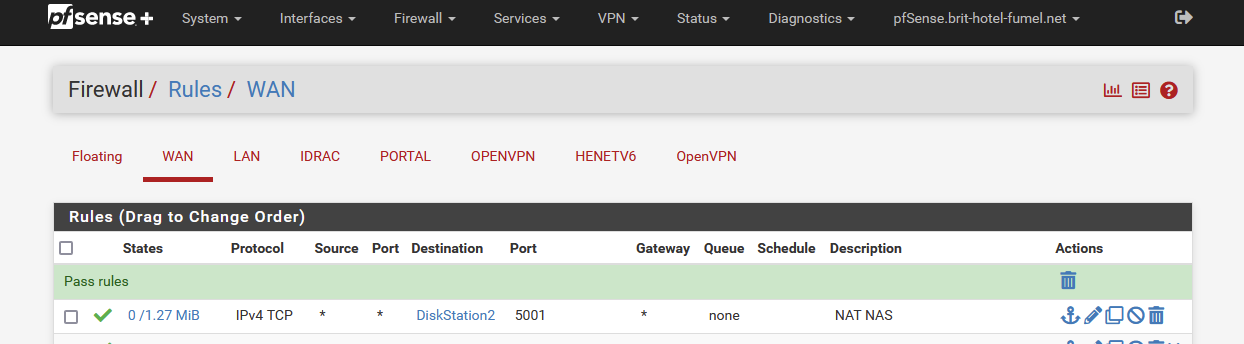
if needed, put it at the top
The counters show you that traffic is using this rule : you know the rule works or matches.
-
ye... pretty much exactly what i have, except I'm redirecting port 32 on WAN to port 22 on lan onto IP of the Synology.
bingo...
I had it close tot he bottom, below a block all. moved it to the top and working.G
-
@georgelza said in pfsense and Synology port forwarding:
below a block all.
Normally, that's a good thing, placing a final block all rule on WAN.
But that rule won't be the final rule, there is another one, hidden, on every interface, and it block everything.
When you create a NAT rule, and you have your own home made block all rule on WAN, then you need to re order the auto created firewall rule on WAN above your own block rule. Otherwise, your NAT rule might be perfect, but .... it will not work fro 'some' reason.
I know, as the same thing happens to me while preparing the NAT demo for you yesterday ;)
( I actually ditched my final block-all rule on LAN so it won't happen again if I have to crate a NAT rule )