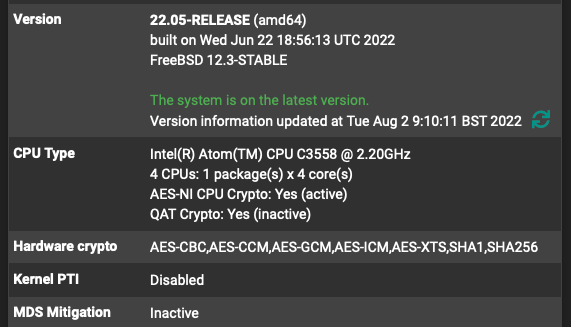
6100 openvpn (client-gateway) speed? QAT inactive?
-
@keyser Thanks! this boosted the performance to around 200Mbit/s. There are some setting that are grandfathered from the restore config.
Do you know if I need to change these too?
Thanks
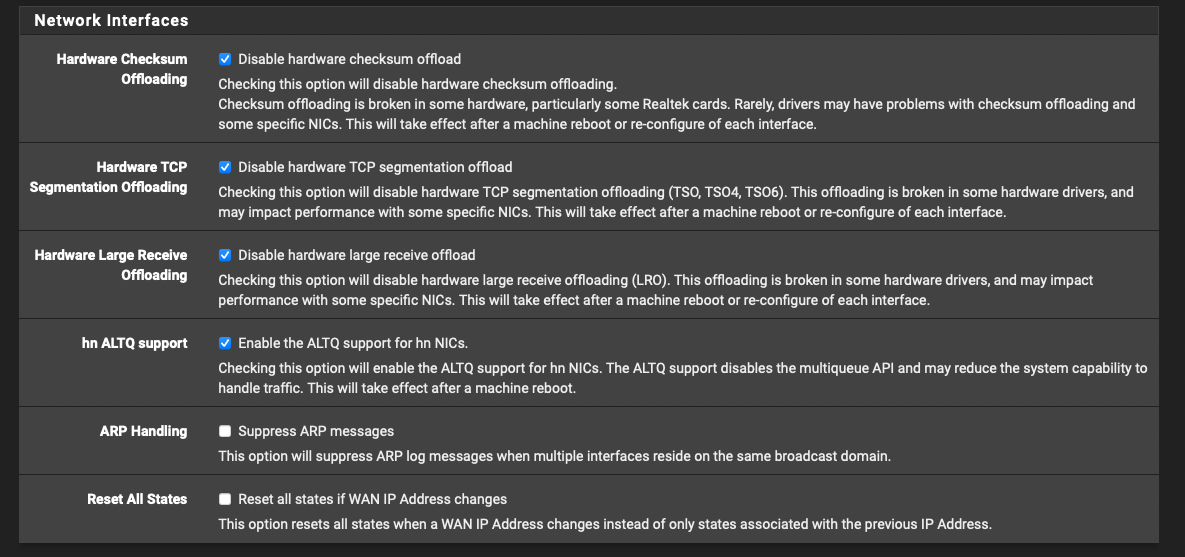
-
@daemonix you should unselect “disable hardware checksum offloading”
The 6100 can make good use of that hardware assist. The other two should remain disabled - not because the hardware doesn’t support it, But because a firewall needs to inspect Those things in software - not have them obsfuscated in hardware. They should only be unselected if you disable pffilter and use pfsense as a router only.The remaining settings are fine. Depending on usecase you might want to unselect the “hn altq support” if you ever should migrate the config to a new box with hn NICs
-
Hmm, that's interesting. Enabling QAT doesn't really make much difference for OpenVPN. Usually.
Do you have hardware crypto selected in the OpenVPN config?
What VPN speeds were you seeing on the previous hardware?
The hn NIC setting makes no difference on the 6100 as it doesn't have hn NICs. It only applies to Hyper-V installs.
Steve
-
@stephenw10 previous hardware was a "I7-3615QM" (mac mini 2012) running Proxmox, and I could do 300+Mbit/s over openvpn. (My line is 350Mbit limited via pfsense) If I remember correctly I was getting max possible or very close to it.
In the openvpn client config I have NO hardware acceleration selected.
What do you think?
Thanks
-
Ah, yes, for a single threaded process like OpenVPN that i7 is going to be faster.
I expect better than 200Mbps though with AES-GCM given low enough latency.
-
@stephenw10 Is this a bug? If so, is it something Netgate will look into fixing?
-
Not really, it's more like a missing feature.

With the inclusion of DCO in OpenVPN leveraging QAT becomes a lot easier
but still a lot of development work. (is actually already enabled).Steve
-
@stephenw10 So is the verdict at this time that QAT with OpenVPN running DCO enabled there wouldnt be any noticeable improvement in throughput because qat isnt supported within openvpn?
Also is it fair to say QAT is only for IPsec at this time?
-
@michmoor it seems so. I saw better speeds but I cant be sure (stephen said its not supposed to be better :S ). I moved to a x86 on that location and Ill use the netgate systems I got for some smaller locations.
-
No, in fact my statement above is incorrect. OpenVPN with DCO enabled, because it's all in kernel, can use the crypto framework that recognises the QAT driver already. It's significantly faster in fact.
One other thing to note there is that unlike userland OpenSSL DCO requires the AES-NI driver loaded to use it, much like IPSec. So if you enable DCO and don't have either QAT or AES-NI drivers loaded it will probably actually be slower. But with either those it's faster. Sometimes by a lot!Steve
-
@stephenw10 So im confused then on how to enable both AES NI and QAT. Or maybe they cant be enabled at the same time??
So on my 4100 i enabled QAT but i see NI is not active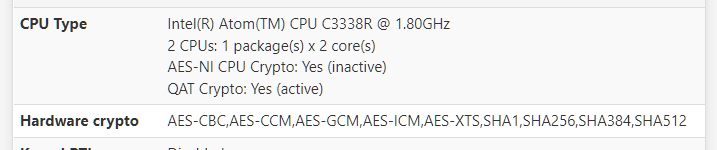
Should i switch back to AES NI then?
Then when i go under OpenVPN i see the option below which is set but no clue as to what it is as its not an avialble option to enable under System - Advanced- Miscellaneous
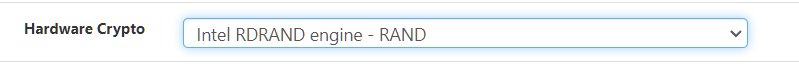
-
@michmoor your first photo tells me you a set!
Dont use the INTEL RNM on the second screenshot. leave it empty. -
@daemonix Got it.
Thanks !! -
Technically you can load both QAT and AES-NI drivers but I'm not how the crypto framework would decide when to use for which ciphers. However pfSense only exposes one at a time because the QAT driver is faster in every scenario. Choose QAT if your hardware supports it.
Steve
-
@stephenw10 said in 6100 openvpn (client-gateway) speed? QAT inactive?:
drivers but I'm not how the crypto framework would decide when to use for which ciphers. However pfSense only exposes one at a time because the QAT driver is faster in every scenario. Choose QAT if your h
So all VPNs with the exception of Wireguard should take advantage of QAT?
-
Well IPSec and OpenVPN with DCO will.
So not (yet) Wireguard, PPTP, L2TP, TINC.