FTP accesable on LAN, but not to port forwarded WAN on public IP address.
-
Hello All,
I have been dealing with this issue a number of different times now, and each time I work on it I can not determine a solution. I have searched these forums, and the manufacture, as well as working with the manufacture support. I have a number of Reolink E1 Zoom cameras that have an FTP function both locally, and remotely.
- I have a locally hosted FTP server that I want to send all camera FTP files to.
- I have setup my FTP server bound to port 50022.
- I have a NAT port forward rule set to any source address, or dest address, on source or dest port 50022 to a NAT IP of my local LAN FTP server.
- If I point to my local IP address the devices on my LAN work with no issues, and I can see all of the traffic on port 50022 on a wireshark capture.
- If I point to my public IP address for the devices on my LAN, I continue to get FTP test failed, and I do not see any traffic on my wireshark capture.
- If I point to my public IP address for the remote devices, I continue to get FTP test failed, and I do not see any traffic on my wireshark capture.
- Working with the manufacture support the cameras can hit their remote FTP server with no issues, so I know the camera works to remote FTP.
I have even tried to create explicit FW rules for floating, WAN, and LAN on port 50022 with logging just to see if I have any traffic hitting the firewall, and I get 0 states. I can not figure this out. I even tried installing the FTP Client Proxy with no luck. Anyone have ideas by chance? Thank you,
-
Is this actually FTP? Because just port 50022 would not pass FTP. It looks more like SFTP if it is.
Your port forward should have a destination address set, usually the WAN IP.
It should not have a source port set, that would usually be a random port.To use your public IP locally you would need to enable NAT reflection. If the server is on the same subnet as the cameras you would also need 'Enable automatic outbound NAT for Reflection':
https://docs.netgate.com/pfsense/en/latest/config/advanced-firewall-nat.htmlBut if they are why not just use the local IP? Otherwise you are passing all that traffic through the firewall unnecessarily.
Steve
-
@stephenw10, Thank you for your feedback. I will try this. To answer your questions, Yes it is FTP, the cameras unfortunately do not use SFTP, and although someone could run an NMAP against my network, most users only try for common ports, this is why I went so high in the port range. I will remove the source port, again that was for testing as I wanted to pickup anything that was using port 50022. I did not figure that would hurt anything.As to the question of why connect the cameras to the NAT locally, it was to test for my off site cameras. I can make changes easier to my local configuration to test connectivity, and then get the remote cameras working. Once I am able to get the WAN working for the remote cameras, the local will be pointed to the LAN address so it is not hitting the FW and only passing through the router. I will let you know what happens.
-
This post is deleted! -
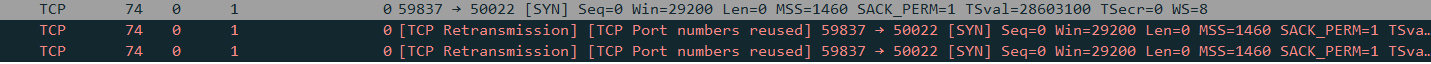
@stephenw10, Thank you for your help. Setting the NAT to pure NAT and the destination to WAN address, with reflection allowed traffic to pass. The LAN to WAN now works, so I tried the remote and it is still failing. I get a SYN, then 2 TCP Retransmissions before the connection fails. So the connection is not fully establishing but now to figure this out. Thanks again!

-
Ok, so you set the FTP port in the server to be 50022 instead of 21?
Is the server running as active or passive?
It's probably passive mode in which case:
https://docs.netgate.com/pfsense/en/latest/recipes/ftp-without-proxy.html#server-behind-pfsense-softwareSteve
-
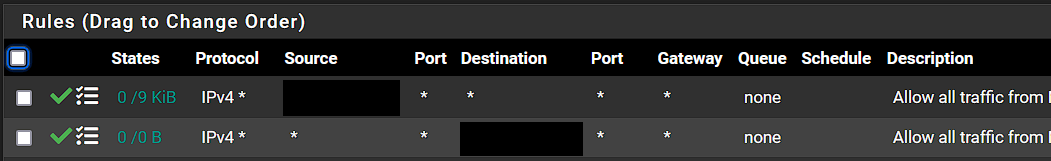
@stephenw10, I can not determine the mode it is running in. From my research it looks that it by default can accept both passive and active. When I was working with Reolink support they had me change the Transport Mode to "PASV". I have also tried putting in back in "port", and "Auto" with no luck. From my Wireshark capture it looks like the FTP server is not sending back an SNY, ACK when it received an SYN from the remote cameras. To ensure it was not being blocked I made a WAN rule to allow all traffic from my source IP, and enabled logging. When I test I see allowed traffic in the log, and if I view the states it shows State: Multiple:Multiple. In an attempt to make sure the FW was not dropping the return SNY, ACK I also disabled the Windows FW for testing, and made both a LAN, and WAN rule to allow any protocal/port back to the destination IP of my remote camera public IP to see if there was any traffic there, but nothing hit the rule.
-
An FTP server must be set to active or passive mode. If you set 'Transport Mode to "PASV"' that is passive mode.
Can you confirm that you changed the FTP port from 21 (the default FTP port) to 50022?
In order for a passive connection to work you will need to forward both the FTP port and the configured data port range the server is using. Usually a few thousand ports in a high range like 50000-55000 for example.
You also need to server to send it's external address for the client to connect to in the passive range. Some clients, notably Filezilla, can see when a server is sending it's internal IP and ignore that but most FTP clients are crude and will just fail. If you test externally with Filezilla and it works when the cameras are failing that's probably what's happening. You can also see that in a packet capture since FTP traffic is all unencrypted.FTP should have been deprecated years ago but unfortunately still lingers on.
Steve
-
@stephenw10 said in FTP accesable on LAN, but not to port forwarded WAN on public IP address.:
you changed the FTP port from 21 (the default FTP port) to 50022?
I highly doubt some camera would allow for that to be honest.
Working with the manufacture support the cameras can hit their remote FTP server with no issues
So your camera behind pfsense is trying to talk to a remote ftp server?
-
Right. This feels like it was the sftp port that was changed and internally the cameras and server are still using the default ports. Though I wouldn't expect the NAT reflection to work if that was the case.
I read that as a test Reolink support did. Their FTP server is likely directly available or behind a proxy which fixes all the bad settings.
-
@stephenw10 So where are the cameras where is the ftp server.
So you have some cameras at site A, and your your trying to get them to ftp to some server you have at site B, which is behind your pfsense?
Or are the cameras and the ftp server on the same site behind pfsense?
-
@stephenw10, Thank you for the response.
- The FTP is running on IIS, on a Windows 2016 server, there is no setting to specifically define the mode on the FTP settings.
- Yes, this FTP is running on port 50022.
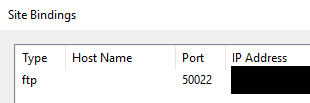
- Here are the settings on one of the local cameras point at the WAN that work.
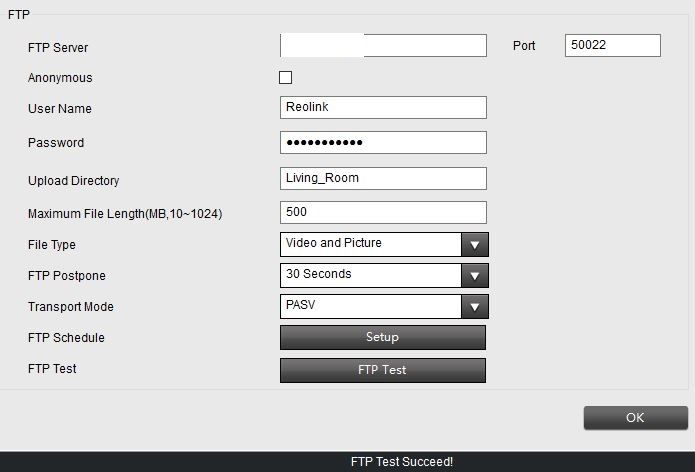
- Here is one of the Wireshark packets from the working camera showing it working on the 50022
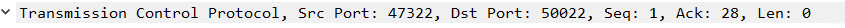
- It looks like on the Wireshark capture of the SYN from the remote camera it is sending to port 50022 from port 59824. I presumed as I had the WAN open port rule to that IP address it would automatically have all 65000 ports open to that designated IP address.
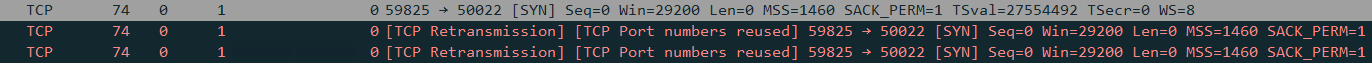
- Unfortunately I do not have a PC that I have remote access to at the remote site to do any additional testing on that end. Just the cameras.
- What I dont understand is that I have the excat same model camera(s) at the remote site, that I do local. I have verified all of the settings are the same, and yet the local ones can hit the WAN IP and route to the FTP, but the remote can not.
Thank you for your assistance, I truly appreciate it.
-
@johnpoz Apologies for not clarifying. I will use site1, and site2.
Site1 is local lan that hosts an FTP server, and a few cameras.
Site2 is a remote site 40 miles away with the same cameras.I am trying to configure the cameras at site2 to upload their footage via FTP to my FTP server at site1.
To test the FTP server I setup my port forward and pointed my local cameras at site1 to my public WAN IP to test and see if I could get traffic to my FTP server. Originally I could not as I did not have the NAT set to pure, and did not have reflection on. Working with @stephenw10 I made those changes, and now I can get the cameras at site1 to hit the WAN public IP and route to the FTP at site1. I plan on changing these back to look at the local IP for the FTP, this was just to test, as I do not have a computer with remote access at Site2 to test with.
Now that the site1 cameras access the FTP via the WAN public IP, I presumed that the site2 cameras also would as they are setup identical. However it seems that the FTP server is not sending an SYN,ACK back after recieving the SYN, so the connection fails, and on the remote side site 2 I get an error showing
Thank you for your help.
-
@regilayt so basics..
Some device is trying to hit your pfsense public wan IP On port 50022, ok sniff on pfsense wan - do you see that traffic hit your pfsense wan?
Where exactly did you do those sniffs?
If you see that traffic, then port forward that to the port your ftp server is listening on..
Are you running a firewall on this 2016 box? Are you allowing that traffic? Have you setup passive mode, did you enable the passive ports to use? IIS has always been horrible for ftp. I would suggest atleast for testing fire up say the filezilla ftp server, this allows you to set the passive ports, it allows your ftp server to hand out the public IP your clients would connect too.
When using passive, the server sends the passive port to connect to, and the IP. If this is not your public IP, and the client doesn't have a helper to know hey change that stupid rfc1918 IP to the public IP talking to, then it will fail. These passive ports also need to be forwarded to your ftp server behind pfsense.
First things first when trying to do port forward is validate the traffic actually hits your pfsense wan, not possible to do anything with a port forward if pfsense does not see the traffic to forward.
So on pfsense packet capture under the diagnostic menu, select your wan interface the port 50022 and now do a test from your remote camera - do you see it hit pfsense wan on 50022?
step 1 is even getting a control channel connection. Then you can see what the ftp server is sending back for its IP and what port it says to connect too.
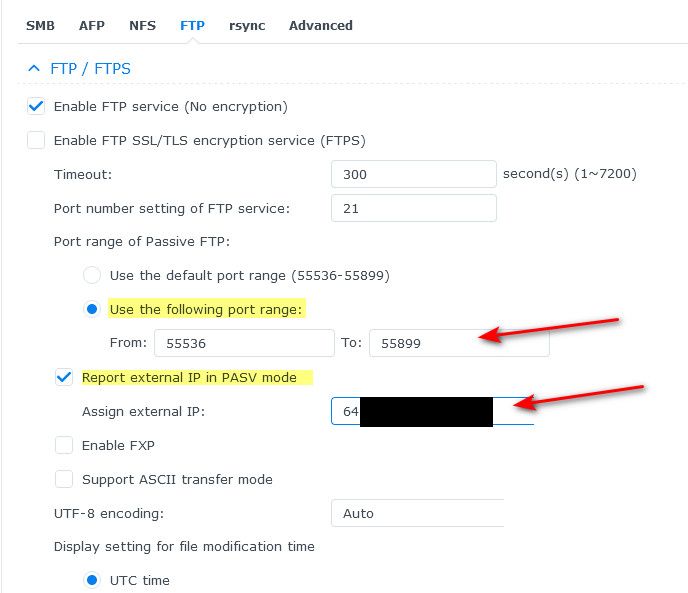
edit: here is example configuration of ftp to allow for passive ports, and report external public IP.
But again step 1 is just to make sure pfsense is seeing the traffic on 50022, and if so then we need to be able to get a control channel connection. The data channel is never going to work, if you can not even get the control channel connection.
In my above example I would forward 21 to my ftp server on pfsense, and I would also need to forward those 55536 to 55899 ports. A firewall rule allowing those ports is not a port forward.
-
This is almost certainly because your port forward is only forwarding 50022 and not the range of data ports required for passive mode FTP. It probably works locally because the server is sending it internal IP for clients to connect to and hence they just connect directly and you don't see that traffic in pfSense. Obviously that can't work from the remote site.
I would still expect the initial connection to work though and it's not even ACKing the SYN.
Where did you run that pcap? Which interface?What port forward rules do you have in place?
Is that the external public IP redacted in that screenshot of the WAN rules?
The port forward happens before the firewall rules so the destination there should be the internal private IP of the server.
But you need to find out the passive port range the server is configured to use and add that as a forward.
Steve
-
@johnpoz, I have a full mirror switchport for all network traffic on this server, as it runs another security appliance for monitoring that is currently disabled for testing. I am sniffing the wireshark against this so I saw all network traffic. I can switch it to just the server NIC though. The sniff is on the server that is running the FTP.
Their is a windows firewall but I have it disabled for testing purposes to make sure it is not interfering.
Here is what I get on the PFSense capture.
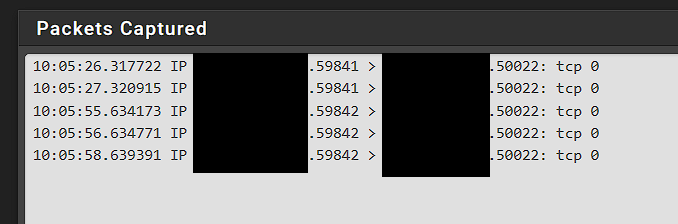
Thank you,
-
That's on the pfSense WAN?
And you see states opened for that complete with the expected NAT?
-
@stephenw10, so I found there is a setting for passive ports. It was set to 0-0 which per documentation shows default ports. I changed it to 45000-55000 as the prior request ports fall in that range. No change there.
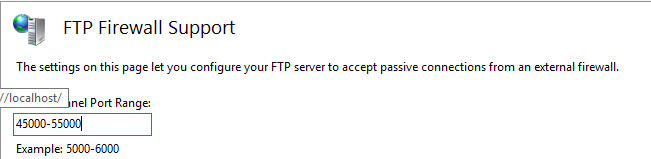
The PCAP was ran on a full mirror interface that shows all network traffic.
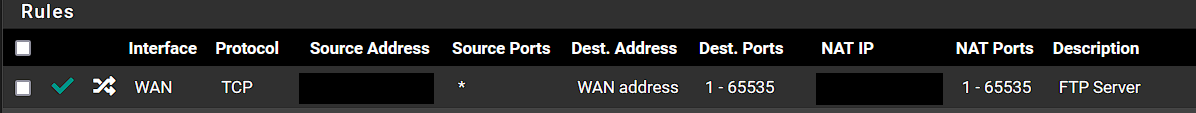
The only port forward rules I have in place are for port 50022.
No, I redacted the source of the remote cameras public IP. My thinking was to open all inbound ports from that IP address. Then open all outbound ports to that IP address, and enable logging so I should be able to see all traffic that would hit from or to that IP address. I do have a rule to the internal private IP below those 2 rules, I just did not show it.
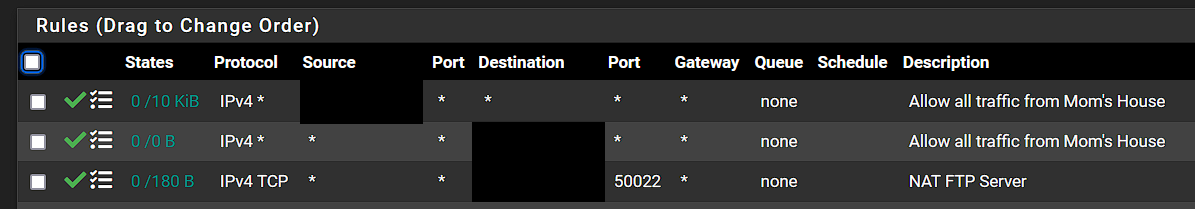
If I understood the port forwarding for all of those ports I modified the rule as follows, but am still having the same issue.
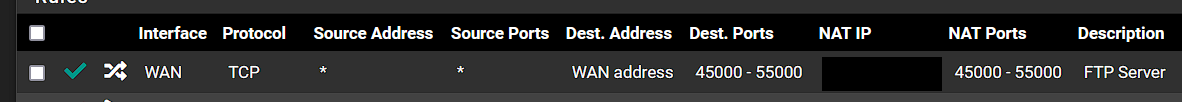
I then ran another packet trace using PFSense just to the source IP, and observed a bunch of udp traffic on other ports also, so I modified the port forward to that IP and allowed all ports incase I missed forwarding a port, but still with no change.
-
@stephenw10, Yes that was on the pfsense WAN, with the expected NAT. All inbound traffic, but nothing returning from the FTP server.
-
You don't need all ports or anything UDP. Just TCP for the FTP port and the passive port range. I would also set the source address to prevent any random thing trying to access your FTP server.
You don't actually need those firewall rules you manually added since you have the port forwards set to add the correct linked rules anyway.Do you see the states opened in pfSense? NAT'd on WAN?