FTP accesable on LAN, but not to port forwarded WAN on public IP address.
-
This is almost certainly because your port forward is only forwarding 50022 and not the range of data ports required for passive mode FTP. It probably works locally because the server is sending it internal IP for clients to connect to and hence they just connect directly and you don't see that traffic in pfSense. Obviously that can't work from the remote site.
I would still expect the initial connection to work though and it's not even ACKing the SYN.
Where did you run that pcap? Which interface?What port forward rules do you have in place?
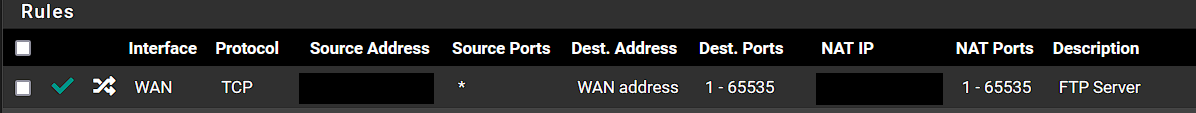
Is that the external public IP redacted in that screenshot of the WAN rules?
The port forward happens before the firewall rules so the destination there should be the internal private IP of the server.
But you need to find out the passive port range the server is configured to use and add that as a forward.
Steve
-
@johnpoz, I have a full mirror switchport for all network traffic on this server, as it runs another security appliance for monitoring that is currently disabled for testing. I am sniffing the wireshark against this so I saw all network traffic. I can switch it to just the server NIC though. The sniff is on the server that is running the FTP.
Their is a windows firewall but I have it disabled for testing purposes to make sure it is not interfering.
Here is what I get on the PFSense capture.
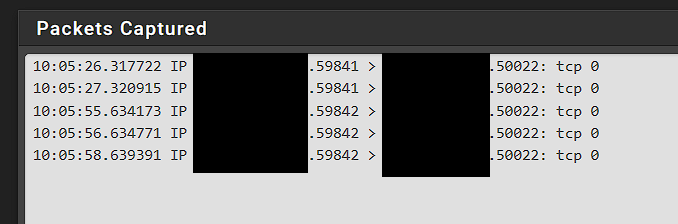
Thank you,
-
That's on the pfSense WAN?
And you see states opened for that complete with the expected NAT?
-
@stephenw10, so I found there is a setting for passive ports. It was set to 0-0 which per documentation shows default ports. I changed it to 45000-55000 as the prior request ports fall in that range. No change there.
The PCAP was ran on a full mirror interface that shows all network traffic.
The only port forward rules I have in place are for port 50022.
No, I redacted the source of the remote cameras public IP. My thinking was to open all inbound ports from that IP address. Then open all outbound ports to that IP address, and enable logging so I should be able to see all traffic that would hit from or to that IP address. I do have a rule to the internal private IP below those 2 rules, I just did not show it.
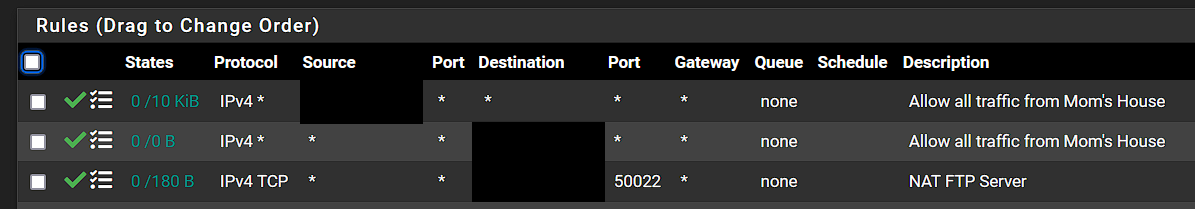
If I understood the port forwarding for all of those ports I modified the rule as follows, but am still having the same issue.
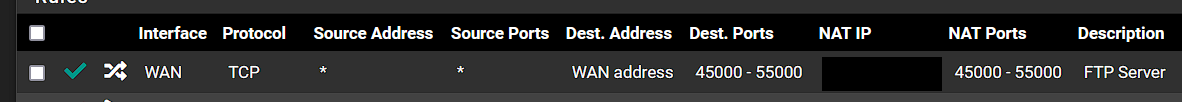
I then ran another packet trace using PFSense just to the source IP, and observed a bunch of udp traffic on other ports also, so I modified the port forward to that IP and allowed all ports incase I missed forwarding a port, but still with no change.
-
@stephenw10, Yes that was on the pfsense WAN, with the expected NAT. All inbound traffic, but nothing returning from the FTP server.
-
You don't need all ports or anything UDP. Just TCP for the FTP port and the passive port range. I would also set the source address to prevent any random thing trying to access your FTP server.
You don't actually need those firewall rules you manually added since you have the port forwards set to add the correct linked rules anyway.Do you see the states opened in pfSense? NAT'd on WAN?
-
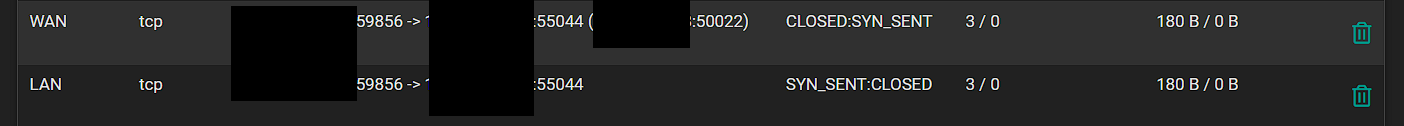
@stephenw10 I changed the NAT back to just the 45000-55000 port range. I then went and viewed the states after trying to test again, and here is what I am seeing. It looks like it is requesting on a higher port range to me?
-
@regilayt where are you sniffing? those make no sense.
Sniff on the wan interface of where your ftp server is.
-
Your port forward is wrong. It's translated the destination port. Unsurprisingly the server is not responding to FTP requests on 55044.
You should probably not have the FTP port inside the passive port range.
It still shouldn't have translated the port though. Something in that forward rule is wrong.
-
@johnpoz, I am sniffing the server switchport that is running the FTP. In wireshark I have both ip.src, and ip.dst to look at my remote IP so I should see all traffic regardless of port going to that IP. All I ever get is 3 SYN, that come in. I dont see any traffic returning.
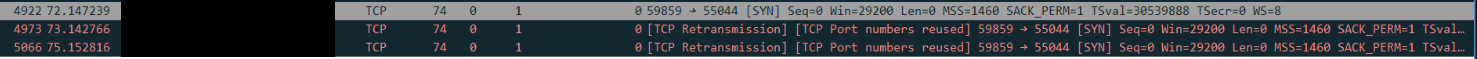
I ran the capture on the FW at the same time, and here is what is showed.
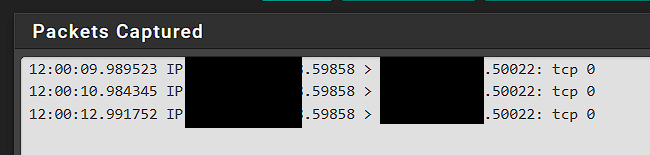
Here are the states. Source IP is my remote IP. Destination is my private local ip of the FTP server with the original destination being the WAN public IP address that has the port forward setup.
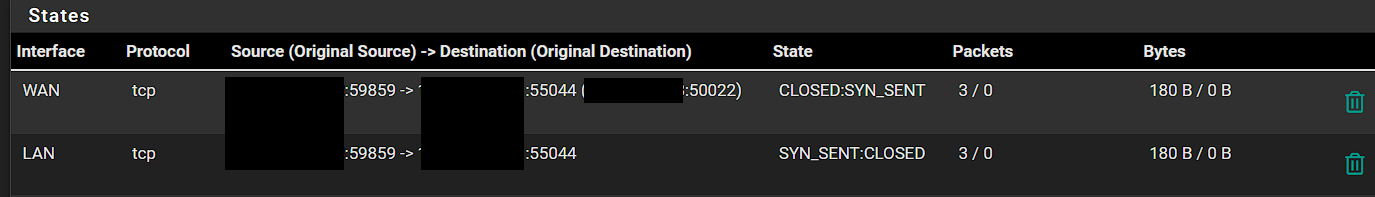
When looking at the states though, I see one is for WAN, and the other is LAN. Does there need to be some LAN rules setup for my server private IP back to something? I ran the packet capture on the LAN network and noticed there is TCP traffic from the remote IP to the private IP of the FTP server.
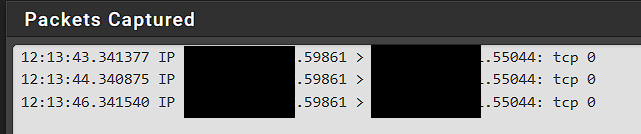
Thanks for all of your help!
-
@stephenw10 I modified the FTP server for ports 40000-50000 now. Here is the port forward rule I have.
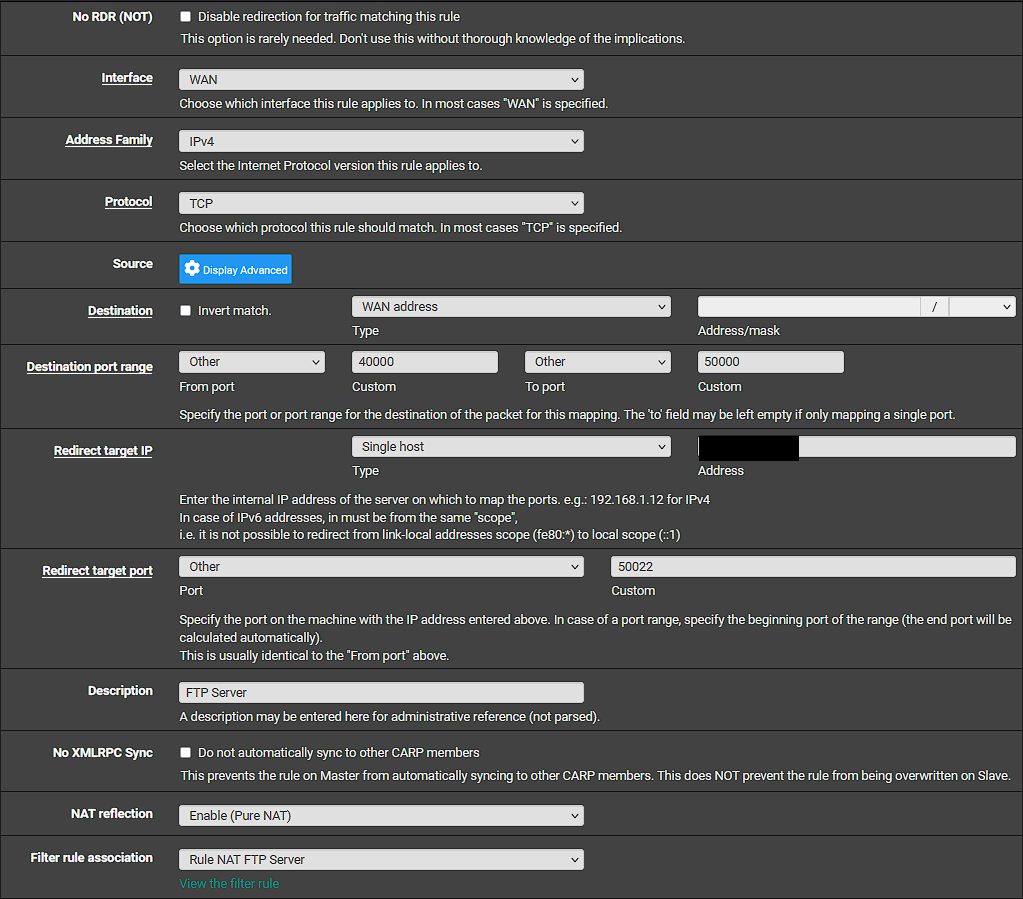
Thoughts?
-
With a port range like that, like it says there, the redirect port should be the start of the range. So 40000 on that rule.
You redacted to redirect IP but I assume it's the internal private IP of your server? There's no need to redact that.What about the other port forward for the FTP port (50022)? That's the one that appears to be wrong.
Steve
-
@stephenw10, this is the first time I have setup a port forward like this, so I may have done something incorrect. Let me ask this, it is easier for me to change the data channel port range rather than update all of the devices to look a new FTP port. So if I start the range from 50023- to 60000 and keep the FTP port at 50022. What should the settings look like on the forward rule? I had to have a Redirect target port, so I presumed that was the port I was sending to on 50022.
Thanks,
-
Yes, you can do that, probably don't need anywhere near that number of ports either. So 55000-60000 would be fine.
The destination and target ports should 50022, yes.
It was being caught by the other rule because the port range overlapped and presumably you put that rule above the single port rule. And because you had entered the start port as 50022 it ended up on a different port.With those changes the initial TCP connection should succeed. It may still fail when it switches to the passive data range though. We shall see...
Steve
-
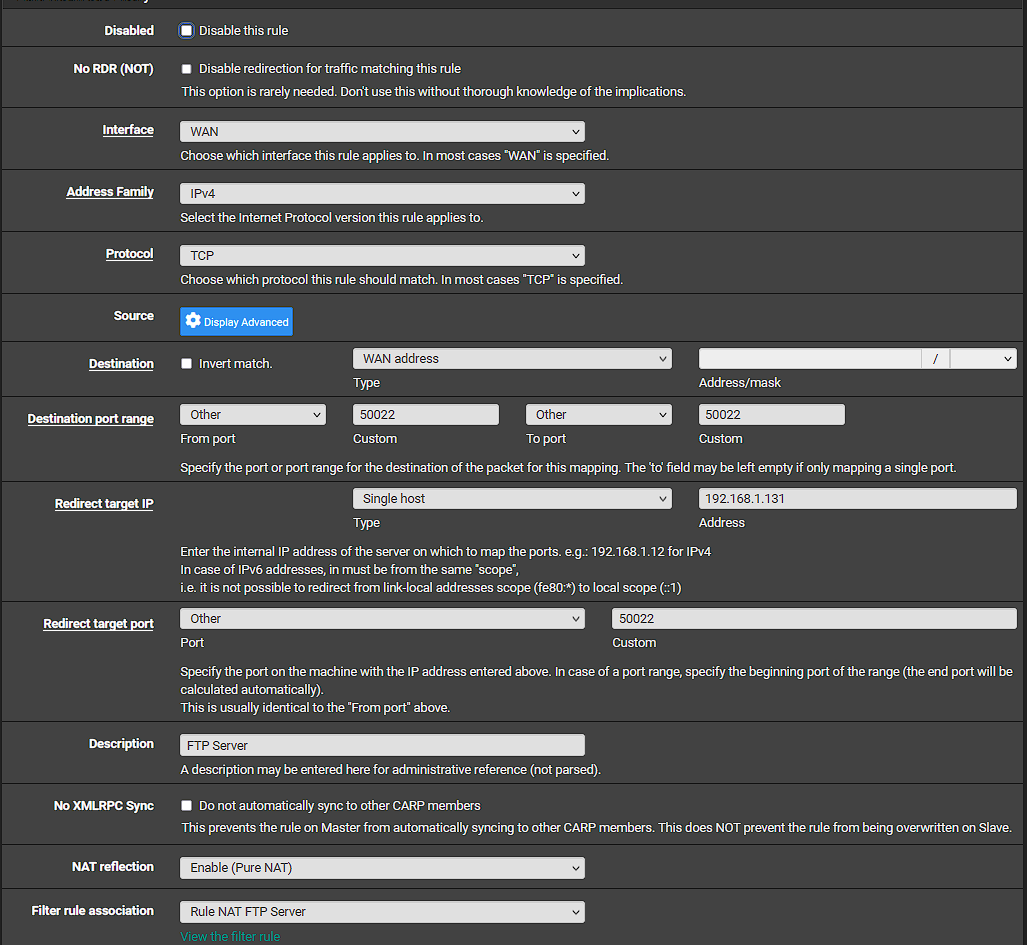
@stephenw10 so I changed my server data channel port to 55000-60000.
Here is what I modified the NAT rule to be:
I ran another capture on pfsense after these changes:
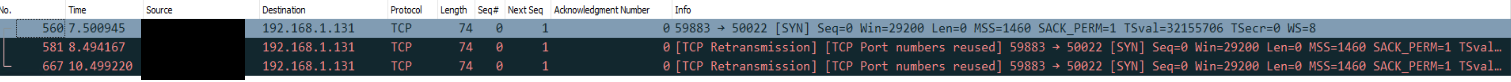
Here was the wireshark:
-
So to be clear you should have two port forward rules. That one for the FTP port, which looks correct. And another one for the passive mode data port range.
That pcap was on the pfSense WAN I assume?
If you pcap on the internal interface or the mirror port do you see traffic there?
Do the states in pfSense look correct?
Steve
-
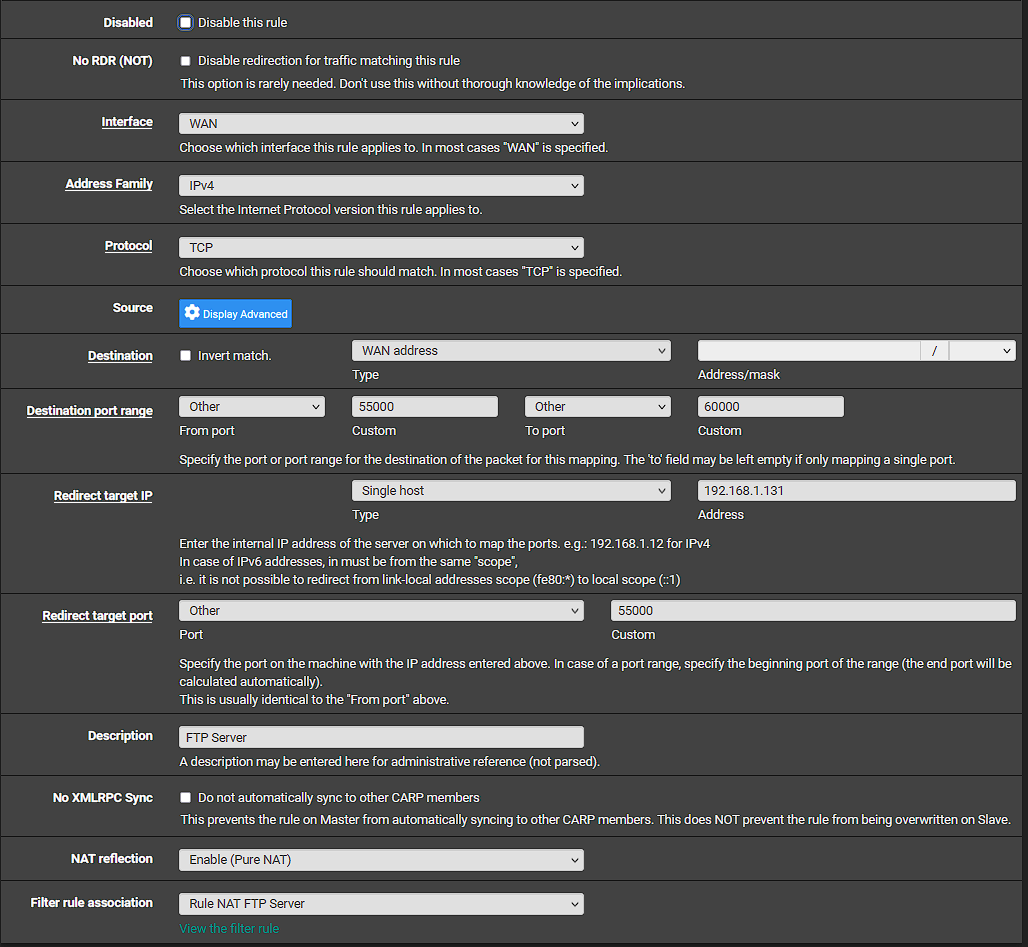
@stephenw10 I did not have 2 rules. I made a NAT rule for the data ports. Does this look correct?
In regard to the pfsense capture, yes that was on the WAN.
On wireshark mirror port I am still only seeing the 3 SYN requests.
Here are the states:
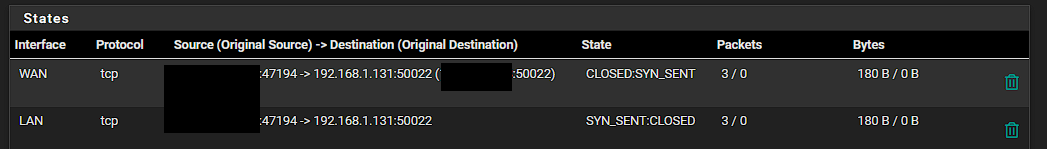
-
Ok, that all looks correct. The states are being created as expected also.
With that result it's almost certainly the server blocking the connection or unable to respond.
So that would a local software firewall rule on the server only allowing traffic from within its own subnet (the Windows default).
Or a lack of a route to be able to respond. Can the server ping out to external IPs in general?Steve
-
@stephenw10, good morning. So I worked on this some more last night, and have still not completed it, but I believe I am farther. I tried to ping the source IP from site2, and it failed. I then tried to do a packetrt that resulted in 30 timeouts.
From here I tried to log into the router at site2 and when the captive portal would display it would not take my credentials. I then observed blocked traffic that I was not seeing before from Snort to that IP. I found this was also the case of why I could not ping. However after suppressing ICMP, and the alert for the captive portal I can now login to the site2 router, but I still can not ping. I do see allowed traffic hitting an any source, any port open to that IP address. I even stopped the Snort service thinking that if it is not running, it can not filter against the block lists, but that did not seem to help.
So, I still can not get the FTP from the site2 to work at this point. Just wanted to give an update. Thanks again for your help.
-
It doesn't look like a problem at site 2 to me because you are seeing the FTP traffic arrive at site 1 and be forwarded to the server. The server just never replies.
Either the server is blocking it or it's trying to reply via the wrong route or has no route.
Can we assume the server itself is able to ping something external? Can it ping site 2 dircetly?
Steve