how to get IP Attacker into the blocklist
-
@ezvink said in how to get IP Attacker into the blocklist:
i see on youtube it works as an IP to be blocked.
What video is this exactly? Its says to put things in the "passlist" to block them?
-
@ezvink said in how to get IP Attacker into the blocklist:
ohh that passlist is not to add IP to be blocked sir?
There is no “block list” in an IDS program because one can just make a normal firewall rule to block the IP.
The Pass list is to always allow that IP.
-
@steveits
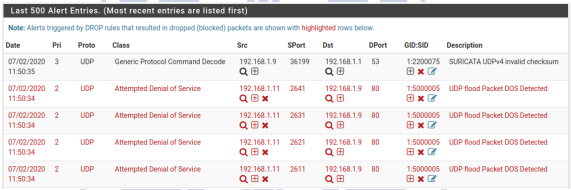
what I mean is like this, sir, when Suricata/snort detects the attacker's IP attack, it automatically enters the block list.So what I want to ask is, how do I enter the attacker's IP into the blocklist? even though the IP attack was successfully detected but not included in the blocklist, even though the rule I made was also DROP not ALERT
this is a picture of the journal that I read, and the journal does not explain how to get the attacker's IP into the blocklist list.
-
@johnpoz
I saw the video on youtube, sir, who tried to attack using Suricata and added a passlist -
@ezvink You aren’t supposed to enter any IPs manually.
Are you using Legacy mode (which adds it automatically) or Inline mode (which doesn’t use the block list, as noted in the screenshot, because the packet is simply dropped)? -
@steveits
I'm using legacy mode sir, but it doesn't have any effect. -
-
@ezvink said in how to get IP Attacker into the blocklist:
@johnpoz
I saw the video on youtube, sir, who tried to attack using Suricata and added a passlistI think you completely misunderstood the concept there. A Pass List is used to prevent an IP from being blocked. "Pass" means "to allow", so that means the traffic is not blocked but instead is allowed to pass when the IP is on a Pass List. You would use a Pass List when a rule is triggering for some host (possibly as a false positive), but you do not want that host to be blocked. IP addresses listed on an active Pass List will not be blocked, but they will still show up on the ALERTS tab when the alerting rule triggers.
If you want to block a specific IP, you can always create your own custom rule using the feature on the RULES tab (by selecting "Custom Rules" in the Category drop-down on that tab).
-
@ezvink Did you happen to click any of the [+] icons on the Alerts tab, to Suppress the alert? If you did then it won't trigger again. You can view that list on the Suppress tab.
-
@bmeeks
I've added a rule with DROP sir to the rules I created in the custom rule, but it's still not in the blockhost tab -
@steveits
if my attacker's IP has entered the suppress tab, is the IP blocked, sir? -
@ezvink said in how to get IP Attacker into the blocklist:
@steveits
if my attacker's IP has entered the suppress tab, is the IP blocked, sir?No. A suppress list suppresses the alert and therefore any associated block.
-
@ezvink said in how to get IP Attacker into the blocklist:
if my attacker's IP has entered the suppress tab, is the IP blocked
No.
The suppress list is for alerts that you never want to see again. Meaning, the alert is suppressed. Therefore, never blocked.
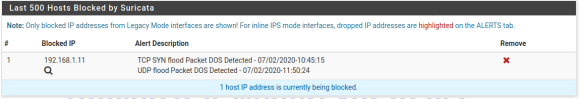
If you want to block an attacking IP you don't enter it anywhere. You said you were using Legacy with blocking enabled, so if the attacker triggers an Alert then the IP appears on the Blocks tab.
It sounds like you have created a custom rule. Is the rule being triggered? It is logged on the Alert tab?
-
@steveits
I do not set anything else sir, I just leave the default.but it doesn't work on the suricata/snort I installed sir, can you help me find the point where the problem is?
-
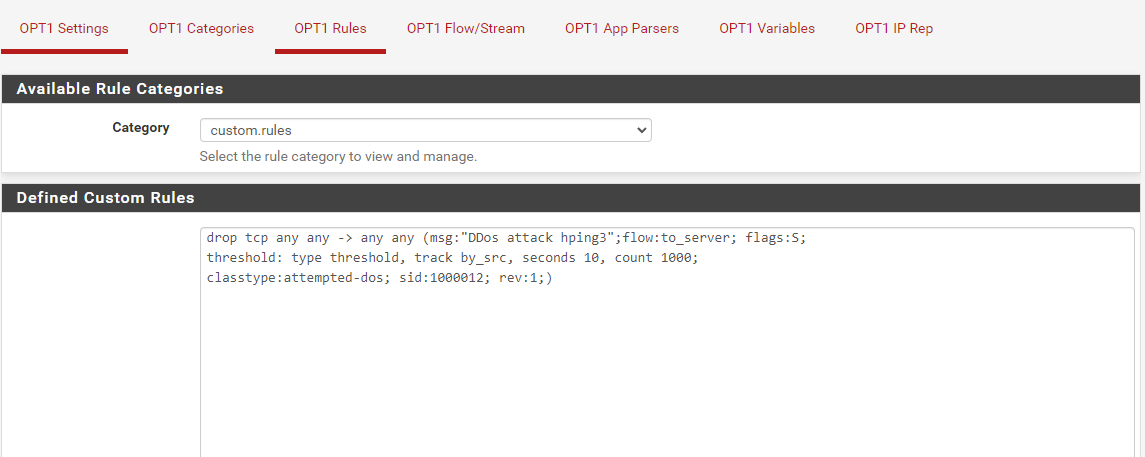
@ezvink
This is the rule that I added sir, it can be detected and goes to alerts but doesn't go to the blockhost tab
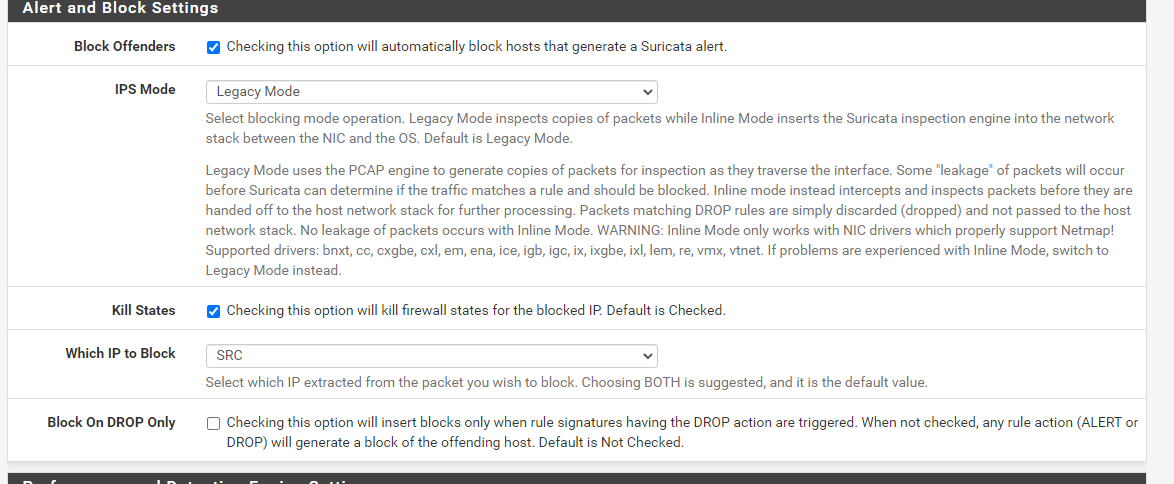
-
after I checked the "block Drop on only" menu, the action symbol changed to DROP before it was still alert even though the rule I added had dropped, and even then the blockhost menu pack remains empty
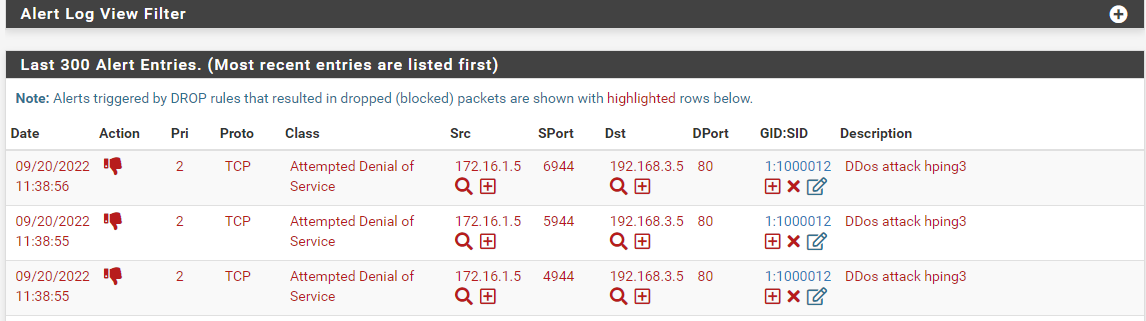
-
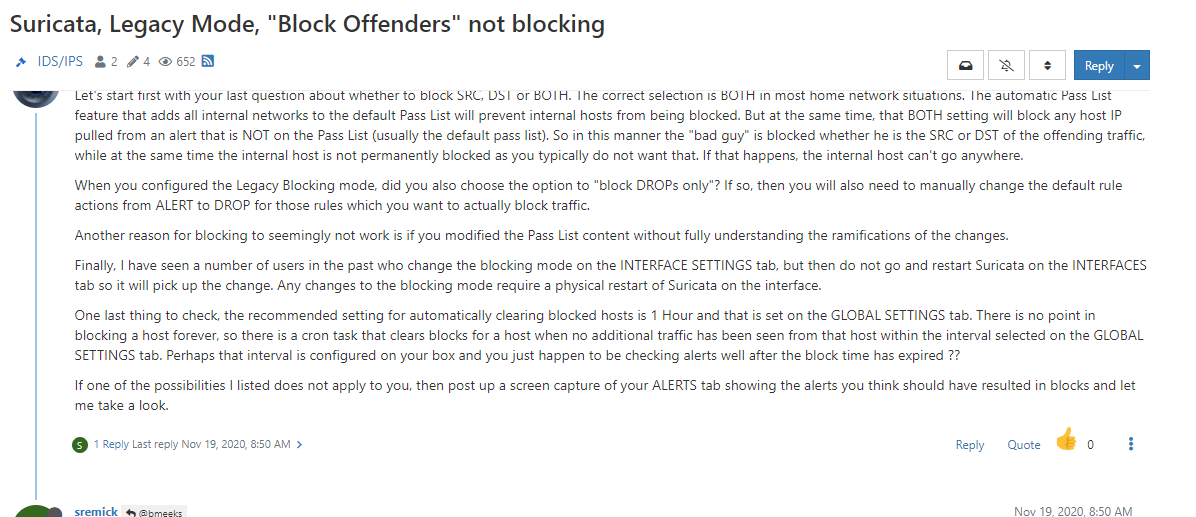
I have followed from this forum too, but still the blockhost tab is empty -
@ezvink said in how to get IP Attacker into the blocklist:
but it doesn't work on the suricata/snort I installed sir
Which is it - you don't have both running do you?
You removed the entry from the passlist?
-
I'm pretty sure your rule is not going to result in a block because of the default Pass List settings when using Legacy Blocking Mode. You have the rule running on the OPT1 interface. That is a locally-attached interface, so all IP addresses on that interface subnet are automatically added to the default Pass List. If the 192.168.3.5 address is also part of a locally-attached network, then it will also be part of the default Pass List. IP addresses covered by a Pass List entry will generate alerts, but will not result in actual blocks.
Post a copy of the current Pass List setting by going to the INTERFACE EDIT tab for the OPT1 interface, scroll down to the Pass List drop-down, then click the View List button out on the right. Post the content of that pop-up dialog. Let's see what IP addresses and subnets are listed on the Pass List currently running on that interface.
-
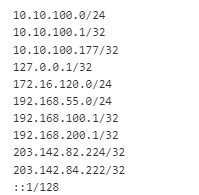
I rebuilt the VM and this is what the passlist looks like.
Yes, it seems that's where the problem is, indeed, the attacker's IP is included in the passlist.
IP 172.16.120.0/24 is the IP of the attacker
IP 192.168.55.0/24 is the IP of the webserver