how to get IP Attacker into the blocklist
-
@bmeeks
I've added a rule with DROP sir to the rules I created in the custom rule, but it's still not in the blockhost tab -
@steveits
if my attacker's IP has entered the suppress tab, is the IP blocked, sir? -
@ezvink said in how to get IP Attacker into the blocklist:
@steveits
if my attacker's IP has entered the suppress tab, is the IP blocked, sir?No. A suppress list suppresses the alert and therefore any associated block.
-
@ezvink said in how to get IP Attacker into the blocklist:
if my attacker's IP has entered the suppress tab, is the IP blocked
No.
The suppress list is for alerts that you never want to see again. Meaning, the alert is suppressed. Therefore, never blocked.
If you want to block an attacking IP you don't enter it anywhere. You said you were using Legacy with blocking enabled, so if the attacker triggers an Alert then the IP appears on the Blocks tab.
It sounds like you have created a custom rule. Is the rule being triggered? It is logged on the Alert tab?
-
@steveits
I do not set anything else sir, I just leave the default.but it doesn't work on the suricata/snort I installed sir, can you help me find the point where the problem is?
-
@ezvink
This is the rule that I added sir, it can be detected and goes to alerts but doesn't go to the blockhost tab
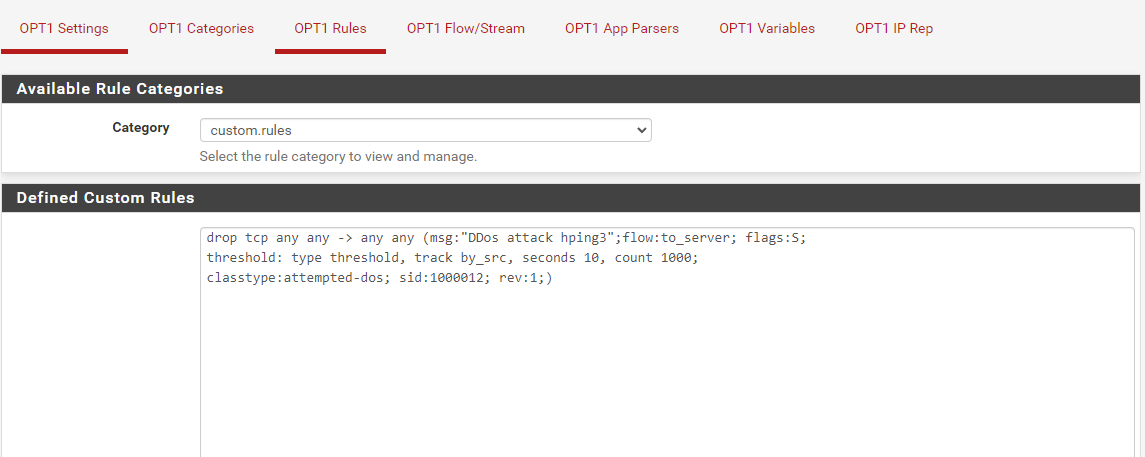
-
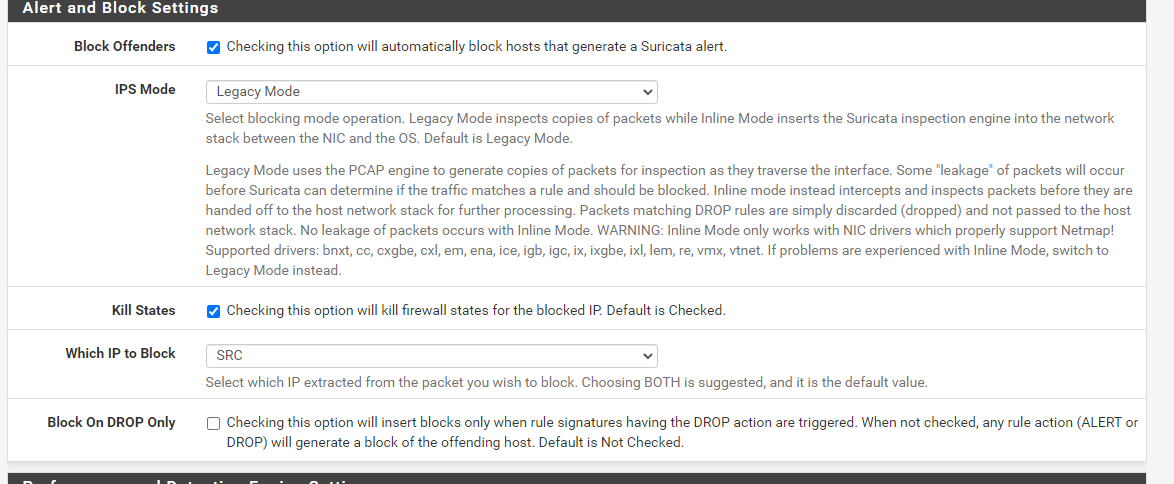
after I checked the "block Drop on only" menu, the action symbol changed to DROP before it was still alert even though the rule I added had dropped, and even then the blockhost menu pack remains empty
-
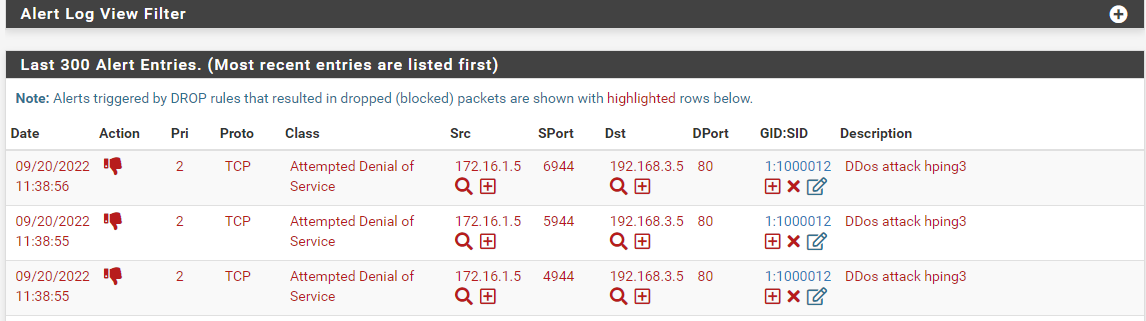
I have followed from this forum too, but still the blockhost tab is empty -
@ezvink said in how to get IP Attacker into the blocklist:
but it doesn't work on the suricata/snort I installed sir
Which is it - you don't have both running do you?
You removed the entry from the passlist?
-
I'm pretty sure your rule is not going to result in a block because of the default Pass List settings when using Legacy Blocking Mode. You have the rule running on the OPT1 interface. That is a locally-attached interface, so all IP addresses on that interface subnet are automatically added to the default Pass List. If the 192.168.3.5 address is also part of a locally-attached network, then it will also be part of the default Pass List. IP addresses covered by a Pass List entry will generate alerts, but will not result in actual blocks.
Post a copy of the current Pass List setting by going to the INTERFACE EDIT tab for the OPT1 interface, scroll down to the Pass List drop-down, then click the View List button out on the right. Post the content of that pop-up dialog. Let's see what IP addresses and subnets are listed on the Pass List currently running on that interface.
-
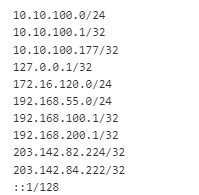
I rebuilt the VM and this is what the passlist looks like.
Yes, it seems that's where the problem is, indeed, the attacker's IP is included in the passlist.
IP 172.16.120.0/24 is the IP of the attacker
IP 192.168.55.0/24 is the IP of the webserver
-
Then, how is the solution, sir? If I give a network attacker VM that does not originate from Pfsense, attackers cannot access webserver
-
Isnt this debate intended to pinpoint how to add an attacking IP (outside source) to a blocklist?
So the list gets bigger and bigger every day, so they eventually run out of IP4 and then the admin can see who and whats on the list?
-
@cool_corona
Yes, that's right, sir, but I haven't found a way to get the attacker's IP (outside source) to connect to the webserver -
@ezvink why would you do that?
-
@cool_corona said in how to get IP Attacker into the blocklist:
why would you do that?
this is part of my final project sir
-
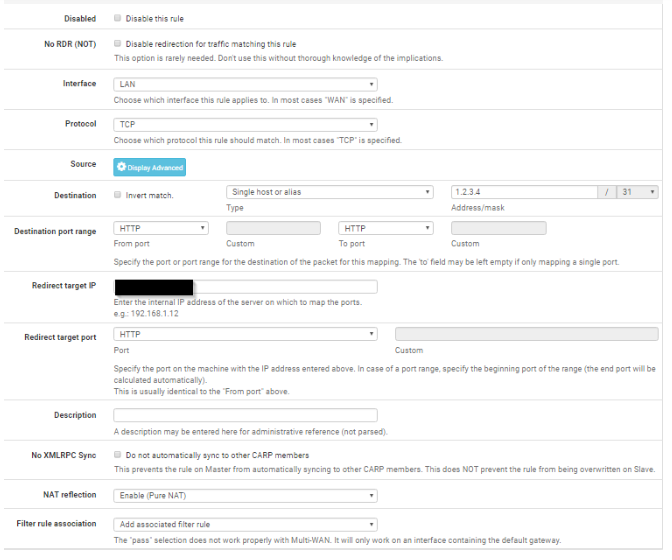
what with firewall->port forward settings will this work sir?
-
@ezvink No.
Choose WAN as interface and set NAT to Use System Default.
-
@cool_corona
ok sir, now for the ip redirect
what is it, sir? Attacker's IP? or which IP? -
@ezvink said in how to get IP Attacker into the blocklist:
what is it, sir? Attacker's IP? or which IP?
So think about that for like .2 seconds..
attacker ---> wan (pfsense) lan ---> server
Where do you think you should send that traffic hitting your wan, if you want it to get to the server?