how to get IP Attacker into the blocklist
-
I have followed from this forum too, but still the blockhost tab is empty -
@ezvink said in how to get IP Attacker into the blocklist:
but it doesn't work on the suricata/snort I installed sir
Which is it - you don't have both running do you?
You removed the entry from the passlist?
-
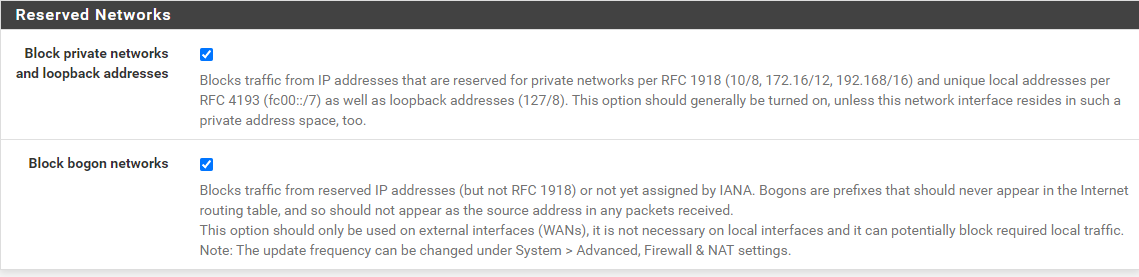
I'm pretty sure your rule is not going to result in a block because of the default Pass List settings when using Legacy Blocking Mode. You have the rule running on the OPT1 interface. That is a locally-attached interface, so all IP addresses on that interface subnet are automatically added to the default Pass List. If the 192.168.3.5 address is also part of a locally-attached network, then it will also be part of the default Pass List. IP addresses covered by a Pass List entry will generate alerts, but will not result in actual blocks.
Post a copy of the current Pass List setting by going to the INTERFACE EDIT tab for the OPT1 interface, scroll down to the Pass List drop-down, then click the View List button out on the right. Post the content of that pop-up dialog. Let's see what IP addresses and subnets are listed on the Pass List currently running on that interface.
-
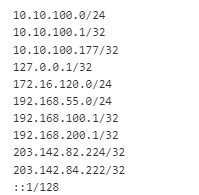
I rebuilt the VM and this is what the passlist looks like.
Yes, it seems that's where the problem is, indeed, the attacker's IP is included in the passlist.
IP 172.16.120.0/24 is the IP of the attacker
IP 192.168.55.0/24 is the IP of the webserver
-
Then, how is the solution, sir? If I give a network attacker VM that does not originate from Pfsense, attackers cannot access webserver
-
Isnt this debate intended to pinpoint how to add an attacking IP (outside source) to a blocklist?
So the list gets bigger and bigger every day, so they eventually run out of IP4 and then the admin can see who and whats on the list?
-
@cool_corona
Yes, that's right, sir, but I haven't found a way to get the attacker's IP (outside source) to connect to the webserver -
@ezvink why would you do that?
-
@cool_corona said in how to get IP Attacker into the blocklist:
why would you do that?
this is part of my final project sir
-
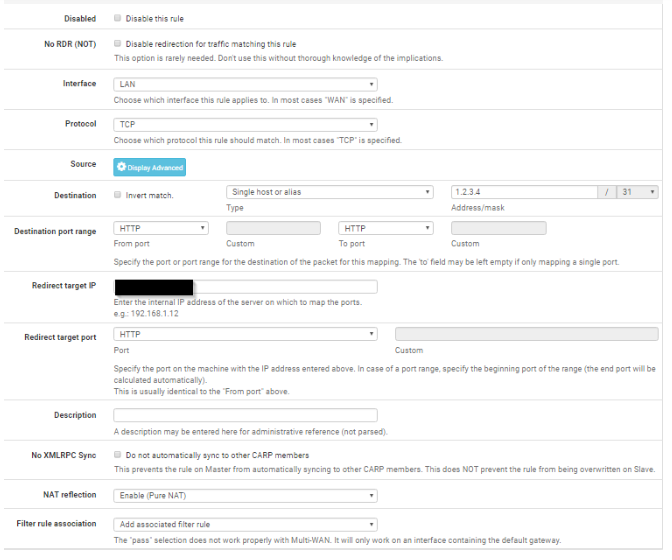
what with firewall->port forward settings will this work sir?
-
@ezvink No.
Choose WAN as interface and set NAT to Use System Default.
-
@cool_corona
ok sir, now for the ip redirect
what is it, sir? Attacker's IP? or which IP? -
@ezvink said in how to get IP Attacker into the blocklist:
what is it, sir? Attacker's IP? or which IP?
So think about that for like .2 seconds..
attacker ---> wan (pfsense) lan ---> server
Where do you think you should send that traffic hitting your wan, if you want it to get to the server?
-
@ezvink said in how to get IP Attacker into the blocklist:
Then, how is the solution, sir? If I give a network attacker VM that does not originate from Pfsense, attackers cannot access webserver
Option 1:
The WAN subnet is NOT placed in the default Pass List. Only the single IP address of the WAN interface is on the Pass List. So simply create your attacker VM and give it an IP in the same subnet as your pfSense firewall WAN for a quick test. Then create a port forward on the WAN for your victim VM (the webserver). Your attacker VM would be plumbed into the same virtual switch as your current pfSense VM's WAN interface.If you understand network routing, you can easily create the proper route table entries and use about any IP network on your pfSense WAN side to host the attacking VM.
Option 2:
Create a custom Pass List on the PASS LIST tab. Uncheck the Local Networks option. That will prevent the inclusion of all the locally-attached subnets. If desired, you can add back any desired locally-attached networks using the custom list at the bottom of the page. Save the new Pass List and then go to the INTERFACE SETTINGS tab and assign that new Pass List to the Suricata instances your attack traffic will be traversing. Save the Pass List change and restart Suricata on the interface so it sees the new assignment. -
@bmeeks
I've tried option 1 but still the port forward that I made doesn't work and the attacker can't even connect to the webserver, is there something wrong with the port forward that I made? (192.168.3.5) is the IP of the webserver.
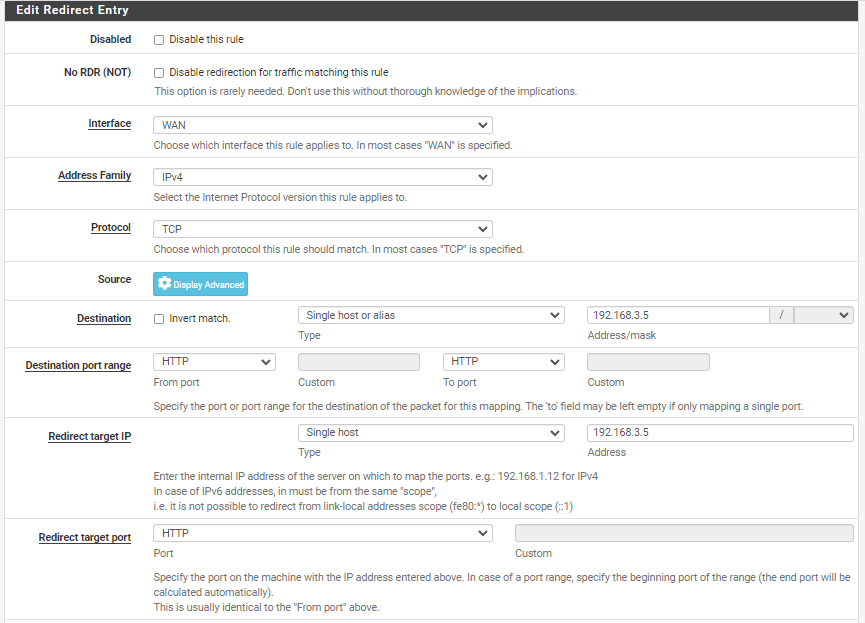
and I've also tried option 2, I've made a passlist and the IP I input is ip 192.168.18.0/24(wan ip) 192.168.3.0/24(webserver ip) but that also doesn't work sir, and when I look at the view list IP 172.16.1.0/24(attacker) is still registered even though I've changed it to a passlist that I created
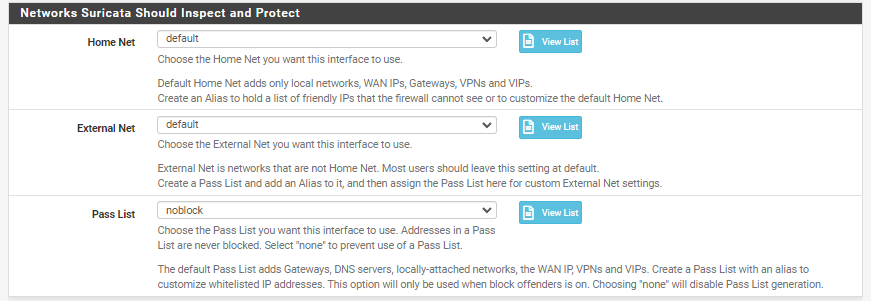
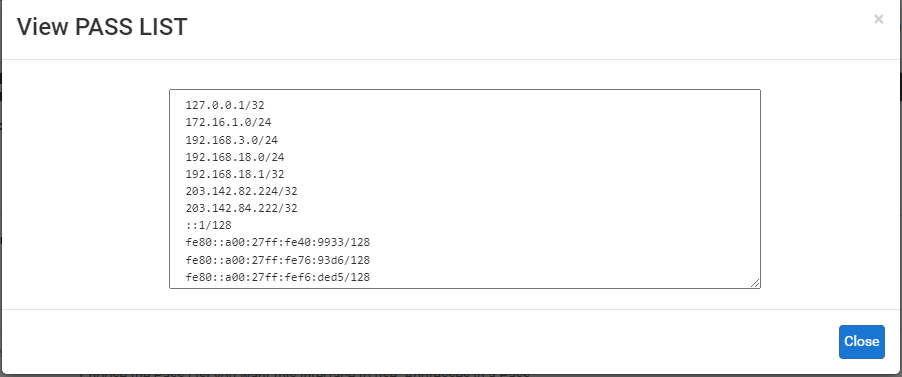
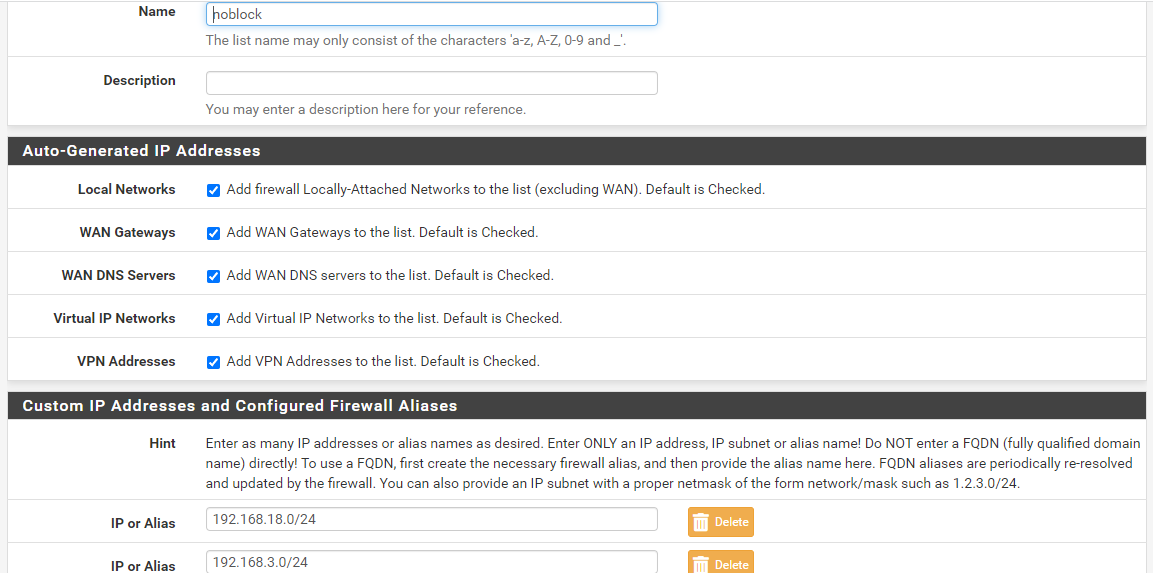
-
@ezvink Youre doing it wrong...
As I said you need to use WAN address as destination and HTTP as protocol.
Not 192.168.3.5
And redirect to 192.168.3.5 using HTTP
-
@cool_corona said in how to get IP Attacker into the blocklist:
As I said you need to use WAN address as destination and HTTP as protocol.
Not 192.168.3.5
And redirect to 192.168.3.5 using HTTPI have also done that, sir, for destination I use "wan address" and redirect "192.168.3.5" but it still works, sir.
I saw a tutorial on youtube, that the firewall settings from the ISP also had an effect, he set the firewall on the ISP webgui he was using to low so that permission to portforward could be done. does it affect me using a virtual machine? what i watch is he uses pfsense hardware sir and mikrotik
-
@ezvink what are the rules on your wan? Out of the box rfc1918 is blocked, so you could port forward all day long and it would never work if the source is rfc1918. Which it is in your setup.
edit:
Also, what IP are you sending your traffic too? Once you setup the port forward, your traffic you send from your hping will be to the pfsense wan ip, not the 3.5 server behind pfsense. -
@ezvink :
Go read the official pfSense documentation here for instructions on configuring a port forward: https://docs.netgate.com/pfsense/en/latest/nat/port-forwards.html. As @Cool_Corona mentioned, you are doing it incorrectly.And as @johnpoz stated, be sure that you are not blocking RFC1918 addresses on the WAN interface for this test. You configure that on the bottom of the page from the pfSense menu INTERFACES > WAN.
-
@johnpoz
I left this setting by default sir, so which one should I uncheck? both of them?