Help Designing Multi WAN
-
@rcoleman-netgate Perfect, thanks for the link, I'll check it out and set it up.
-
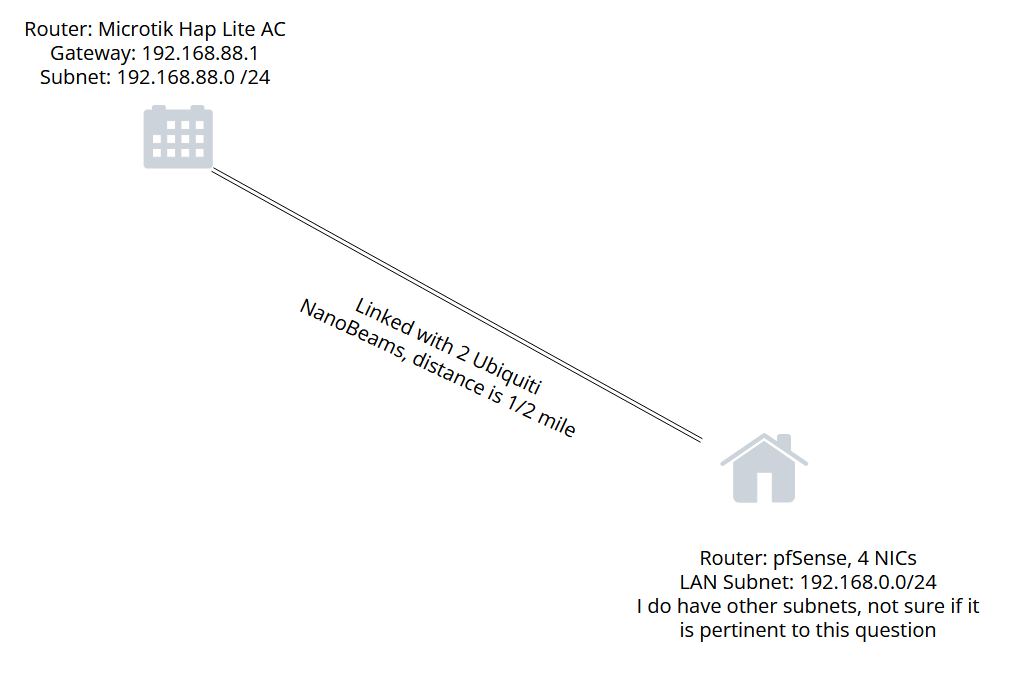
I finally got to getting the PtP setup up and running. I ended up adding an interface (SHOPBRIDGE) to pfSense on the same subnet as the remote (shop/family business) network (192.168.88.x). I can access the shop network from my house (LAN Network) and ping all devices.
I did not end up doing the VPN setup that @rcoleman-netgate recommended. A gateway has been added on the shop bridge connection with the gateway being 192.168.88.1. However, when I disable my primary WAN interface, I am not getting internet on my LAN subnet. Is there something I am missing here and is this possible to use the SHOPBRIDGE interface to use the gateway to get internet on the rest of my network?
The only things I have done was add the interface and create a gateway using that interface. Not sure the next steps.
-
@rubber_duck13
The remote site must masquerade upstream traffic from your house aside from permitting it. I suspect, it doesn't.Alternatively you can masquerade the traffic on pfSense.
Basically this should be done, if you state the gateway in the interface settings. -
@viragomann okay, not a network expert here, how do I do that?
I have an interface, ShopBridge (em3), setup with DHCP for IPv4 Config and hostname set, nothing else.
Under system routing gateways, I have the ShopBridge_DHCP with a gateway of the upstream shop router IP (set dynamically).
The only other thing, I setup is I have a firewall rule to allow any any from the Shopbridge subnet.
-
@rubber_duck13
So masquerading should be done automatically on pfSense.
Check Firewall > NAT > outbound and look if there are automatic rule created for this interface.However, for taking over the default route to the other gateway, you will need to configure a gateway group:
System > Routing > Gateway Groups
Add a group, set WAN GW as Tier 1 and the ShopBridge GW as Tier 2.
Then go to the gateways tab and switch the default gateway to the new gateway group. -
@viragomann Here are the automatic rules that were created (WAN is my main internet, WAN_2 is another WAN I setup for a 4G backup that I have been playing with. It works, but is so slow where I am that I don't really use it, SHOPBRIDGE is the interface to the shop that I am trying to get working):
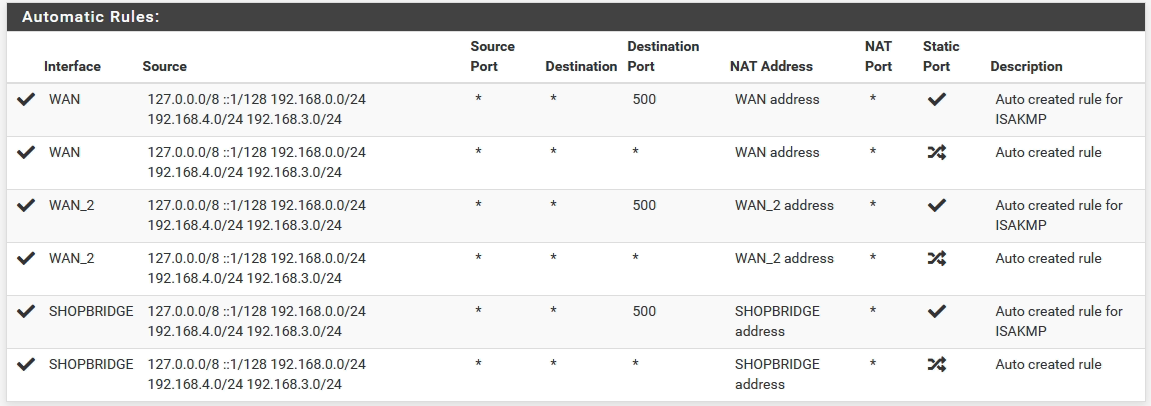
I have not created a gateway group and tested it, I will set that up then test it when I have time at home.
-
@rubber_duck13
So there are all needed rules present. Should work from this point.With these Outbound NAT rules the remote site sees only your interface IP. So only this IP needs to be permitted to access the internet (or other resources) and be masqueraded on the upstream interface.
-
@viragomann So talk to me like I don't know what I am talking about :)
On the Shop Mikrotik router, there is currently this:
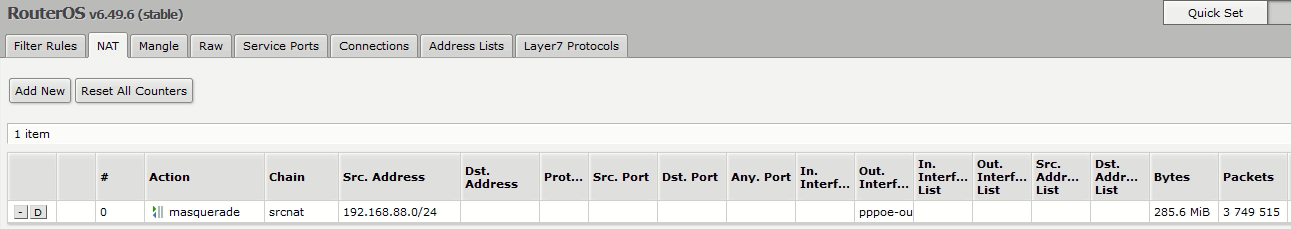
Do I need to add another one with Action of masquerade, Chain of desnat, dst address of the interface (192.168.88.17), src address of the gateway, and an out. interface of pppoe-out1?
-
@rubber_duck13
This rule is just for the local network.
You need a rule like this, but for the source of the shop interface IP of pfSense. -
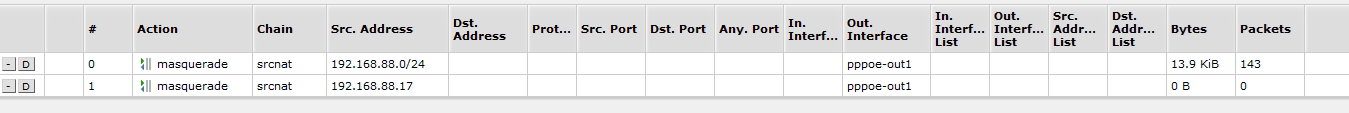
@viragomann Okay, I created the second rule in this list. Hope that is right, I am not able to test this all now, but hope to in the next couple days.
-
I applied all the changes and tested and everything works! Thanks for all the help.