pfSense on PROXMOX with HomeAssistant
-
I was addressing the "single NIC" case you mentioned, if you have more than one NIC you don't need VLANs. If you only have one NIC you would need VLANs plus a managed switch. Both can get to the same intended result but using a single NIC with only VLANs will perform poorly compared to using separate NICs.
Both ESX and Proxmox can operate on a single NIC or multiple, it's all in how you setup the networking in the Hypervisor as I mentioned.
It's a best practice to have the management isolated on its own NIC but not required. You can attach a VM to
vmbr0like any othervmbrinterface. If you put the pfSense LAN on the same Proxmox bridge as the Proxmox management they'd both be on the same network, which is probably what you want there.(Note, I would hardcode a static address in Proxmox otherwise you get into a bad chicken-and-egg scenario if it wants to pull a DHCP address for Proxmox from the pfSense VM... But that's the same for ESX as well.)
-
The process you are suggesting looks perfectly fine to me. The only thing I'm wondering about is your static IP's? Does your ISP not provide DHCP for your WAN connection? Pfsense will of course have 192.168.1.1 but that is set from within itself, not from Proxmox. Another question is why ports 0 and 3 on the new one, you are free to change now, so why not two adjacent ports? Makes it easier to remember when you start playing around with other VM's if that is what you will be doing?
And, about running other VM's on the same machine... I was running pfsense on my main server which also hosts Plex, NextCloud and a number of other servers. I was making a lot of changes and experimentation on that server which occasionally had me running into trouble or wanting to reboot. So that led me to dedicating another HW to pfsense and related VM's (PiHole, NtopNG, HAProxy and the likes).
Also, at step 3. "Configure the NEW pfsense", I would use the config from your existing one. Take a backup, load it in the new one, restart and depending on the NW cards you might have to go in an reassign your network interfaces from within the GUI of pfsense. That's all there is to it.
Regarding my comment on "all 4 ports free", I meant available to pfsense... and of course one of them would be used for WAN then. I actually have 3 ports used for pfsense, where one connects to an LTE Router as failover. So LAN, WAN and WAN2...
-
I will play with this after work (when I do not need Internet -- WFH here).
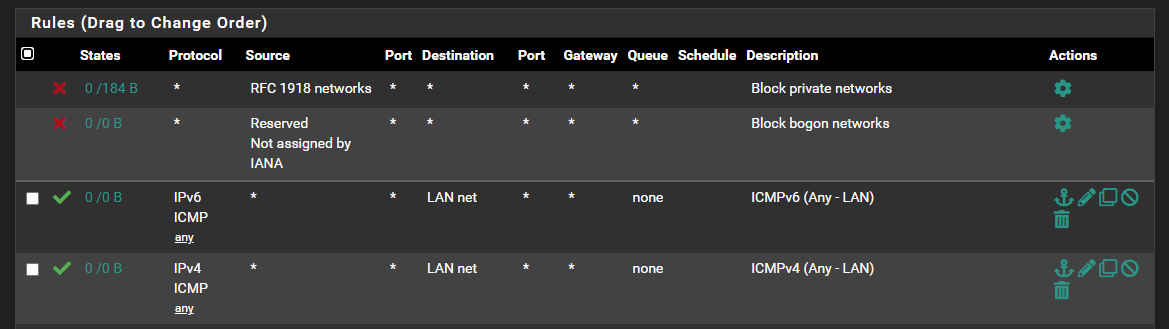
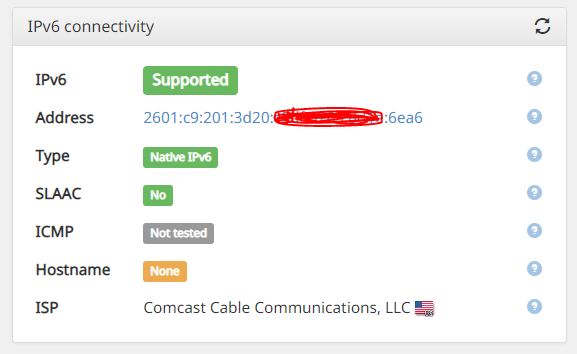
Then I gotta figure out why I am getting the ICMPv6 errors. I put the same RULE I had before in pfSense. I know Comcast will not do IPv6 Reverse DNS (as a residential customer) and still do not know why the browser is not doing IPv6. This has always worked.
-
@Gblenn @stephenw10 @Patch @jimp
Thanks again for all of your help....very much appreciated.
OK. I have put pfSense back on a stand-alone box (well the HP T620+ I had put {Proxmox on) and it is running as before. I have made a new backup and will look to put a new Proxmox install on the new HP Z240 I got for Proxmox and using all the notes from here.
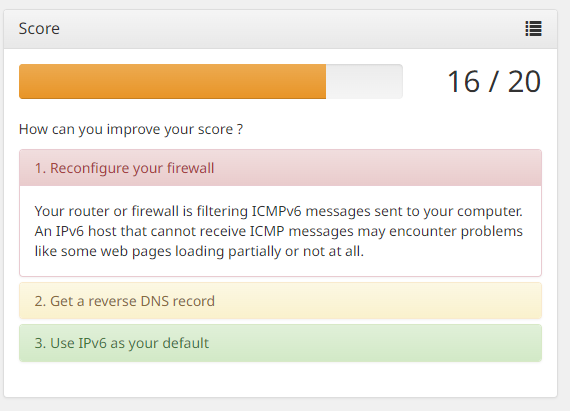
Now I cannot figure out why the IPv6 test is failing - I used to get 18/20 on this test (only because COMCAST will not do an IPv6 Reverse DNS record for residential).
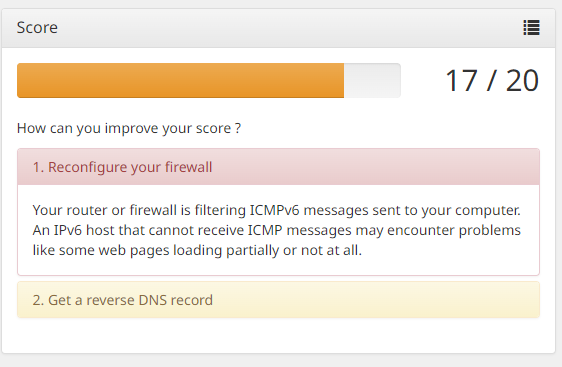
I have rules in pfSense for this. Odd that it is not working. But this also shows it was not tested. Maybe it is not me. :-)
-
Do you see it blocked in the firewall log? What rule is blocking it?
-
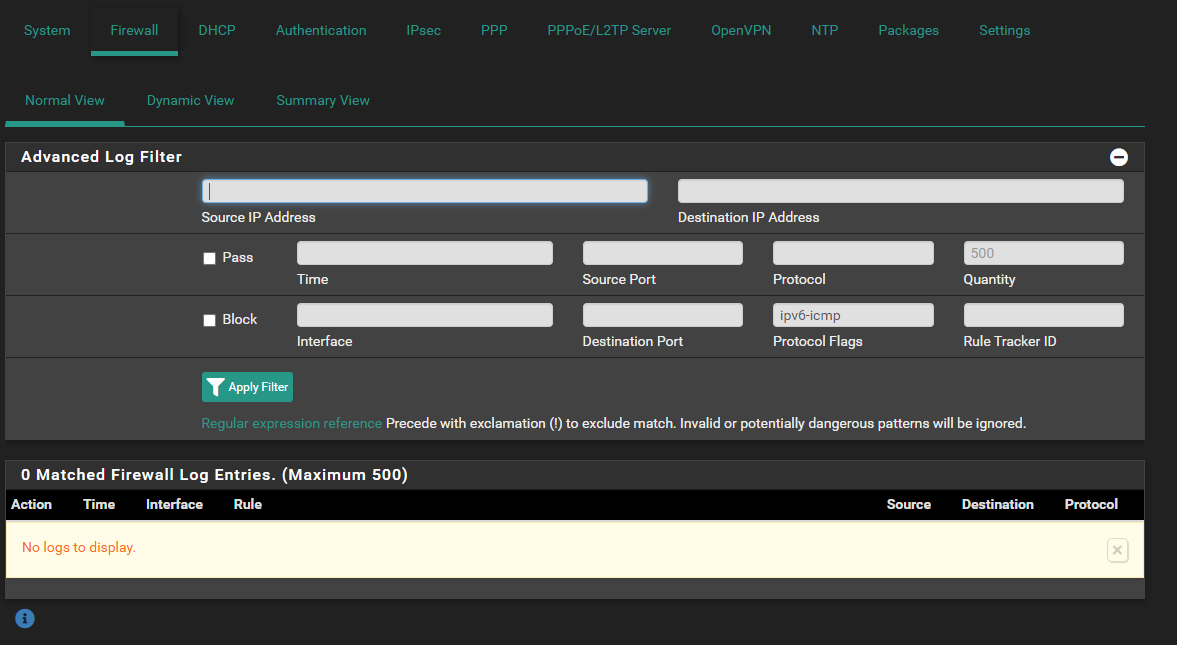
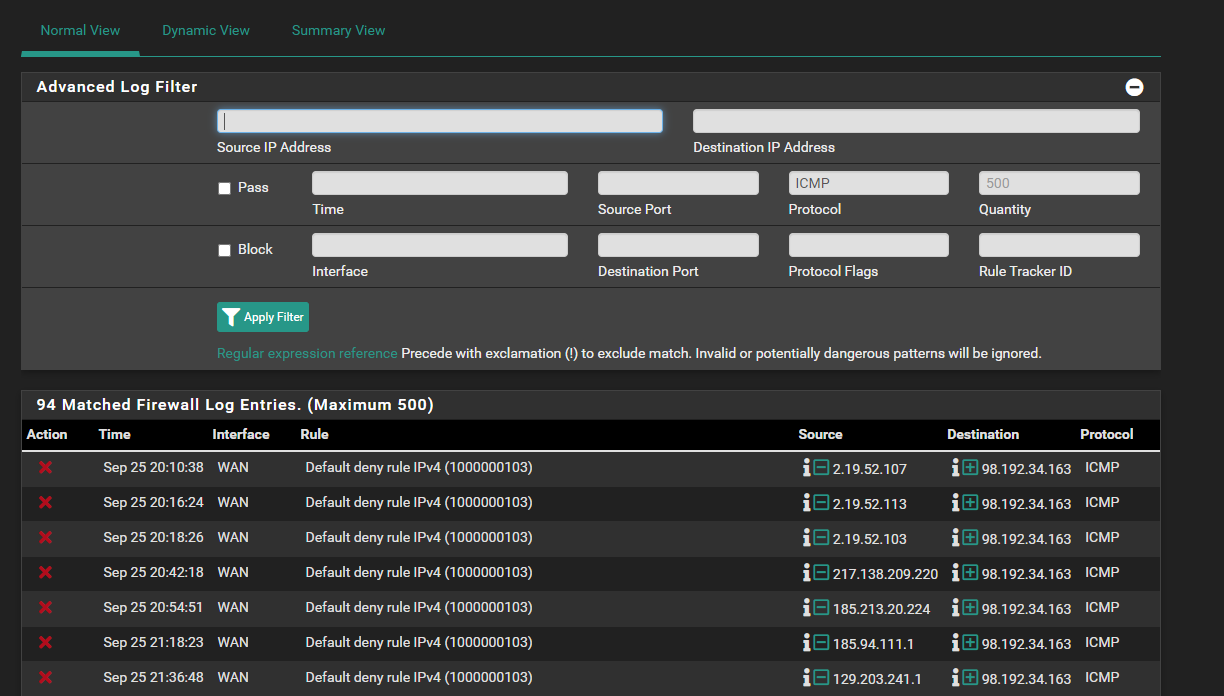
I see nothing in the logs which would be blocking it. In face the Firewall logs do not show anything that I can see ICMP.
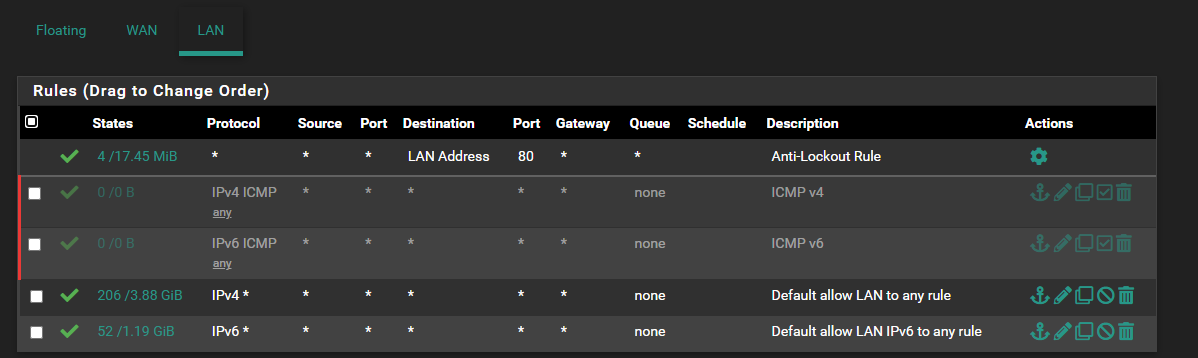
I see these when I FILTER on ICMP - but they are all IPV4. Which still should be working too.
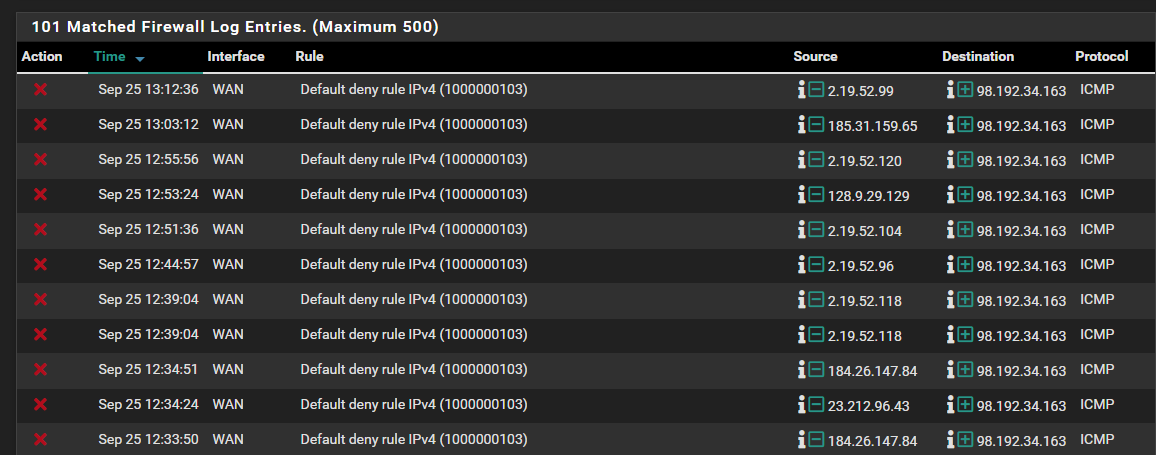
based on these rules:
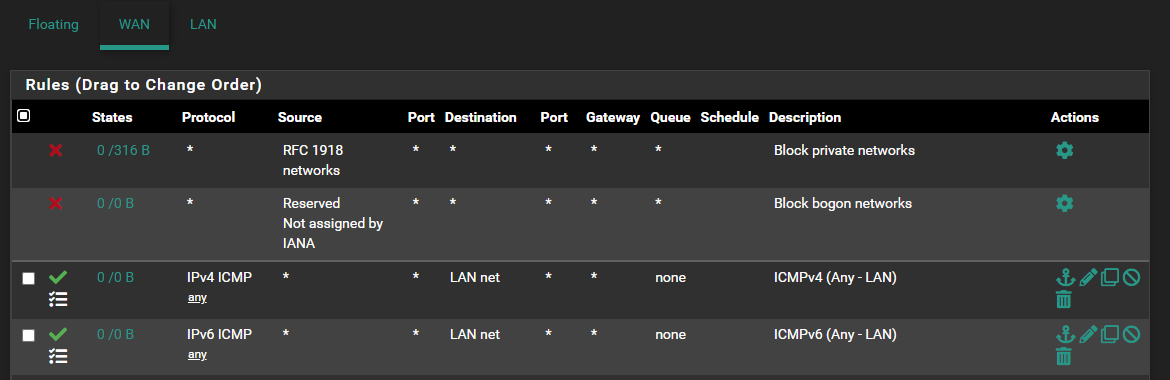
-
This one seems to get a 10/10: https://test-ipv6.com/
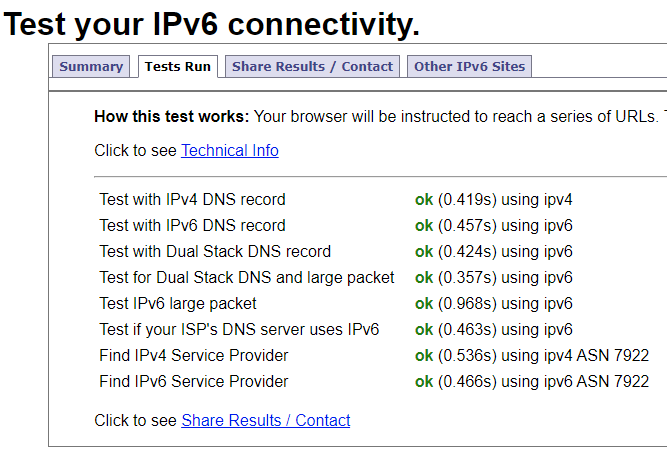
Given that the other one shows that ICMP was not tested - I am not going to worry about it.
-
ICMP is required for IPv6 but the default firewall rules should pass it:
# IPv6 ICMP is not auxiliary, it is required for operation # See man icmp6(4) # 1 unreach Destination unreachable # 2 toobig Packet too big # 128 echoreq Echo service request # 129 echorep Echo service reply # 133 routersol Router solicitation # 134 routeradv Router advertisement # 135 neighbrsol Neighbor solicitation # 136 neighbradv Neighbor advertisement pass quick inet6 proto ipv6-icmp from any to any icmp6-type {1,2,135,136} ridentifier 1000000107 keep stateYou probably need to filter by ipv6-icmp if it was being blocked by pfSense. However it shouldn't be possible to block the 4 icmp types as the rule is 'quick' and high up in the rules table.
Steve
-
-
My mistake it's actually logged as
ICMPv6:Sep 26 13:40:20 WAN Default deny rule IPv6 (1000000105) [xxxx:yyyy:7282:101:20d:b4ff:fe0c:aed6] [xxxx:yyyy:7282:101::2000] ICMPv6 Sep 26 13:40:21 WAN Default deny rule IPv6 (1000000105) [xxxx:yyyy:7282:101:20d:b4ff:fe0c:aed6] [xxxx:yyyy:7282:101::2000] ICMPv6 Sep 26 13:40:22 WAN Default deny rule IPv6 (1000000105) [xxxx:yyyy:7282:101:20d:b4ff:fe0c:aed6] [xxxx:yyyy:7282:101::2000] ICMPv6Echorequest/replies are blocked by default like that but the 4 required types should never be.
Steve
-
-
Not blocked in pfSense then. So either it just wasn't tested, as it seems to imply. Or it's blocked upstream.
Steve
-
@stephenw10 @jimp @Patch @Gblenn
Thanks again everyone for your help.
I am going to run this like this for a while - and take weekly backups. When I am ready to move to Proxmox - I will install fresh and then restore the last backup.
Right now I have another issue... suddenly the 4-port card that I put into the HP Z240 prevents the machine from booting. I can take it out and put into another machine and that one boots just fine. Boots all the way to Windows server 2019, is seen and all 4-ports are there.
Put it in the HP and I get 3 slow-beeps and RED power light, then 2 fast-beeps and white power light. I have a ticket with the folks at HP. It is an HP card 331T card.