Putting my pfSense Home Lab on an Extender
-
@stephenw10 Thanks for the reply!
Correct, the extender pulls its own IP from the core router (the Asus), and yes the pfSense router WAN is pulling an IP from the Asus (192.168.1.xxx network) as well and I can see it as a client in the Asus GUI.
Im trying to access the router gui and any device on the 192.168.5.0 network from a PC on the 192.168.1.0 network. No luck. I can access everything though from the 192.168.5.0 network, including the Asus GUI on the 192.168.1.0 network.
I have tried with NAT on the pfSense router turned on and off, no difference. Correct, I have a static route set to the 192.168.5.0 network.
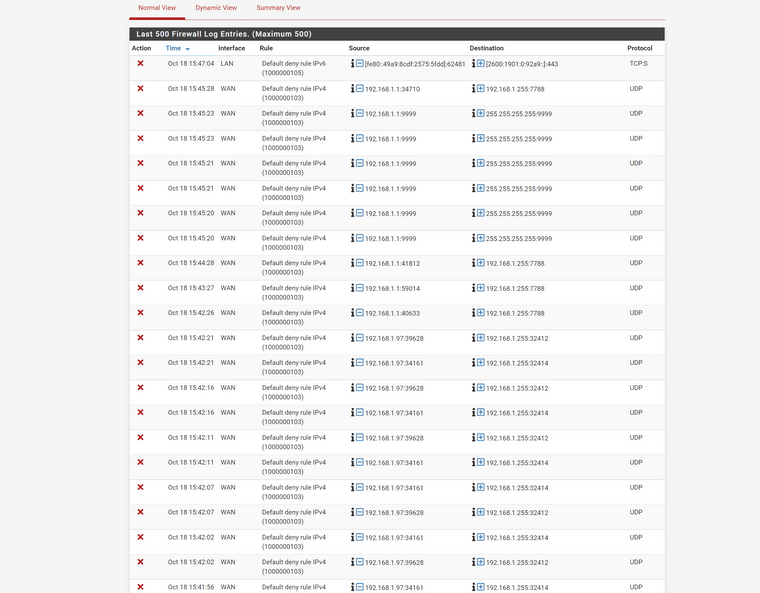
After further digding, I can see traffic hitting the pfsense WAN, but the firewall is blocking 192.168.1.0 traffic in. Give a "Default deny rule IPv4 (1000000103)"
Wireshark shows the following:

-
I meant the Extender might be NATing but that seems unlikely if you're seeing traffic from 192.168.1.X hit the pfSense WAN.
What rules do you have on the pfSense WAN?
What is 192.168.5.6? Is that internal host what you were trying to hit?
Can you access the pfSense GUI using it's WAN IP in the 192.168.1.X subnet?
What you have there is an absolutely classic asymmetric routing scenario. But that would have also been the case when it was wired so if it worked there it still should.
I would still be suspicious of the Extender doing something funky with MAC addresses.
-
@stephenw10 I dont think that extender has the ability to NAT, its settings are pretty basic.
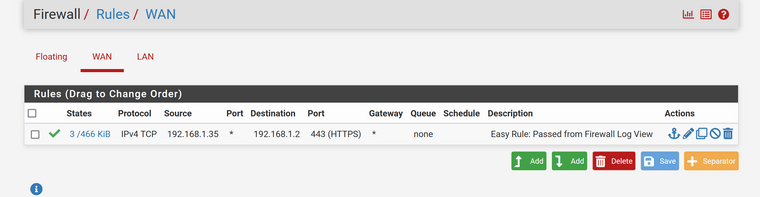
One one rule on the pfSense at the moment:
5.6 is an iDrac, but with the host powered on (192.168.5.12) I cant access it either.
The rule above allows one host to access the pfSense GUI, I cant get to to allow any client from 192.168.1.0 to access it, only works with a single host/IP.
When I check the MAC of the WAN interface and the MAC that the extender is picking up, they do match.
If I go a tracert from a client on the 192.168.5.0 to the router, it hits the pfSense router, then the Asus 192.168.1.1
-
Do you have port forwards for that traffic on the pfSense WAN?
If not, and it was working before, it must be all routed. So that would mean no NAT on pfSense and a static route in the Asus router to the 192.168.5.X subnet?
Most SOHO routers have no static route capability so....The fact you are seeing traffic hitting the pfSense WAN for 192.168.5.6 implies either it is routed or that you have a port forward (or 1:1 NAT) and that may be preventing you reach the pfSense gui.
-
Sorry @stephenw10 I was away on vacation.
The Asus router did have a static route to route 192.168.5.0 network traffic to the pfSense router (192.168.1.2).
Then the pfSense router had rules to allow 192.168.1.0 network traffic though.
I have tried to disable NAT on the pfsense router, but this made no difference.
-
@the_director Maybe you could use Powerline or MoCA adapters instead of that extender?
-
@robh-0 Powerline was actually my first choice, but the bedrooms are not on the same circuit. One room is on one breaker, and another room is one a different breaker
-
@the_director Actually it is OK if they are on separate breakers, they just have to be in the same phase in the panel. In other words, they need to be on the same vertical row.
-
Ok, if you have a static route and no NAT then you need a firewall rule on the pfSense WAN to allow traffic from 192.168.1.X to 192.168.5.X. Otherwise it will just be blocked there.
Also make sure the pfSense WAN does not have 'block private networks' set since that traffic is from a private subnet
Steve
-
@robh-0 Really! Ok then I may need to give this a try!
-
Thanks @stephenw10! Haven't had much time to play around with this (some unfortunate life events have been underway), but should get some thing this week! Ill test out all your suggestions and update the thread.
-
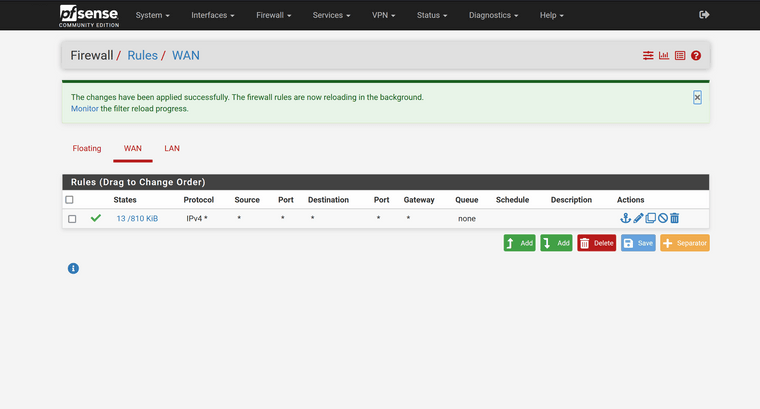
So I got a little time tonight to play around with it, but unfortunately still getting blocked. Below are some screenshots.
Even though I (believe) I set the firewall to all anything though, its still blocking it, which makes no sense to me.
The pfSense firewall rules:
The pfSsense firewall logs:
Current NAT settings:
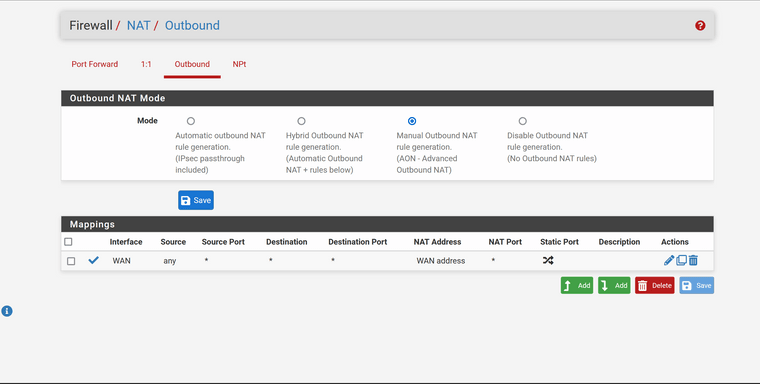
-
Hmm, that certainly seems like it should pass with that allow all rule on WAN.
Do you see any alerts in the GUI?
Go to Status > Filter Reload and reload the filter with the button there. Make sure it loads cleanly without any errors.
Steve
-
@stephenw10 will do when I get home from work this evening
-
@stephenw10 This is what I get from the Filter Reload:
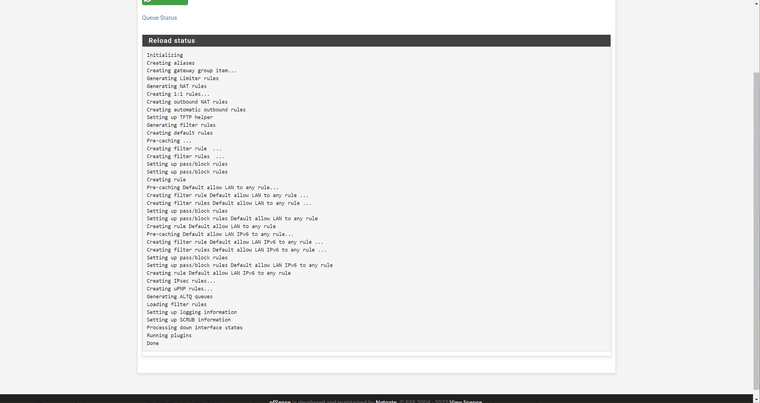
-
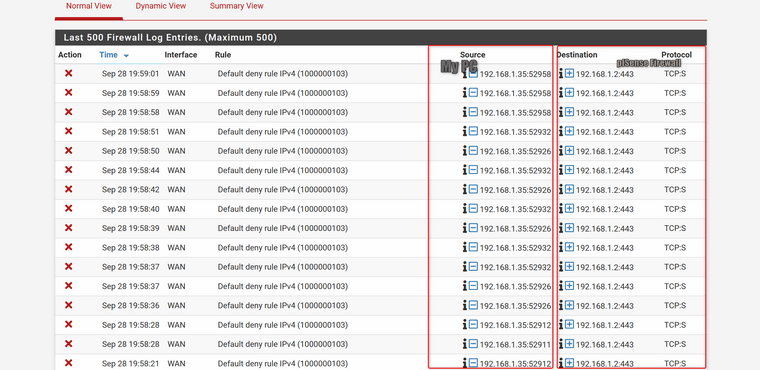
Looks fine. And you are still seeing blocked traffic in the firewall log on WAN like that?
-
@stephenw10 So if I try to access 192.168.5.6 (an iDrac that sits behind the pfSense box) I get "192.168.5.6 took too long to respond." but I dont see the firewall logging anything like it did before (see below). The 5.6 address is perfectly accessable by a laptop sitting behind the pfSense box, and the laptop can access the external web just fine.