Allow LAN host to connect to other LAN host via its public virtual natted IP.
-
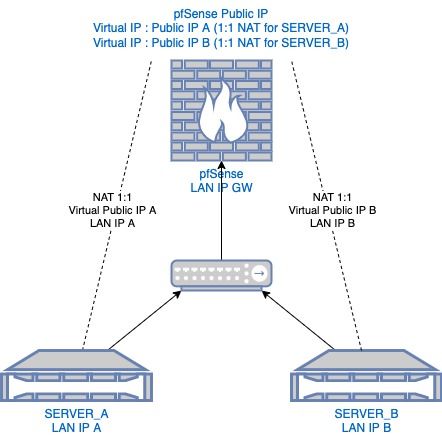
Hello,
I'm looking being able to connect from SERVER_A to SERVER_B using the PUBLIC VIRTUAL IP NATTED for SERVER_B (and vice versa).
Obviously SERVER_A and SERVER_B can talk together using their LAN IPs.
However, sometimes it might be useful that SERVER_A can talk to SERVER_B using its PUBLIC IP (for example when the DNS server returns SERVER_B public IP and you don't want to tweak the /etc/hosts file or using a local DNS server)Here is my configuration :
- One WAN IP + two VIRTUAL IPs
- 1:1 NAT created for first virtual IP to SERVER_A LAN IP
- 1:1 NAT created for second virtual IP to SERVER_B LAN IP
- Rules created to allow connections to SERVER_A and B from external
- Joining SERVER_A from external using its virtual IP works
- Joining SERVER_B from external works also
- Outbound NAT is set to automatic.
- SERVER_A can ping the PUBLIC VIRTUAL IP of SERVER_B but unsure that it's really the SERVER_B that is responding (maybe the pfsence itself) and vice-versa.
Where am I wrong ? (rules ? NAT ? outbound NAT ? Routing ?)
Thank you very much for your help.
Regards,
Polter
-
@poltergeist said in Allow LAN host to connect to other LAN host via its public virtual natted IP.:
SERVER_A can ping the PUBLIC VIRTUAL IP of SERVER_B but unsure that it's really the SERVER_B that is responding
No, it's pfSense, because it owns this IP.
If you only need to access the servers by their public host names, but not the IP itselft, best practice is to add a host override for the public host names to the internal DNS server and point it to the LAN IP.
On pfSense you can do this in the DNS Resolver settings and as well the Forwarder. -
@poltergeist i think the servers would have to be on separate networks/vlans to do this. then you you could change your nat from automatic to hybrid and add manual outbound nat rules for the lan interfaces they would exit.
-
@ipeetables
With a proper outbound NAT rule it will work if both servers are within the same LAN as well. But this has the drawback that the destination server doesn't see the origin IP of the request, but only the pfSense IP. -
@viragomann Thanks!
Indeed, pfsense is reponding to the ping, this is what I was suspecting.
Thanks for the DNS Resolver > Hosts override option tip. It clearly fixed my problem. Thank you ;)
However, I'm interested to know how I can solve this problem at NAT / Rules / Outbound NAT / routing level (for my personal knowledge) -
@viragomann Hello. Thanks for your help. However, different tests I've done has no good results. Can you help me about this?
This what I've tested without result:
Both, SERVER_A and SERVER_B are allowed to connect to "any" and are using their PUBLIC VIRTUAL IP that is natted.
I've created rules allowing SERVER_A to connect to SERVER_B (on the WAN interface) and vice-versa. (by the way, i've allowed SERVER_A PUBLIC IP as source to connect to SERVER_B LAN IP, like I'm use to do for other access from external).
What is missing to make it works? What should I do at the outbound nat level?
Thank you very much for you help. I'm looking forward to understand what I'm doing wrong.
Poltergeist
-
@poltergeist said in Allow LAN host to connect to other LAN host via its public virtual natted IP.:
However, I'm interested to know how I can solve this problem at NAT / Rules / Outbound NAT / routing level (for my personal knowledge)
There is no need for adding NAT rules manually. The "NAT reflection" option does that for you.
You can enable NAT reflection in the WAN NAT rule. Try "pure NAT" mode, if it doesn't work go with the proxy mode.
NAT reflection can also be enabled globally in System > Advanced > Firewall & NAT.
However, DNS overrides are the better solution in my opinion.
Edit: Ahh, you're using NAT 1:1 here. So NAT reflection can only be enabled or disabled in the rules.
But I never used it with 1:1. -
@poltergeist said in Allow LAN host to connect to other LAN host via its public virtual natted IP.:
I've created rules allowing SERVER_A to connect to SERVER_B (on the WAN interface) and vice-versa. (by the way, i've allowed SERVER_A PUBLIC IP as source to connect to SERVER_B LAN IP, like I'm use to do for other access from external).
From your map it's not clear to me if both servers are within the same L2 network. If they are, there is no rule need, because the traffic won't pass pfSense.
If they are in different network segments the rule has to be added to the internal interfaces, which the requesting server is connected to.
Do you use the public host name for accessing the other server?
Does it resolve correctly?Possibly it was still using the public IP due to DNS cache. Try to flush it.
-
@viragomann Thanks. I will try this ;)