"Non secure" pfSense URL
-
@jarhead Thank you for your answer.
Export from here:
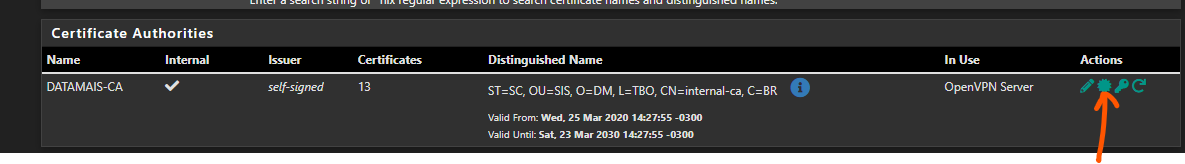
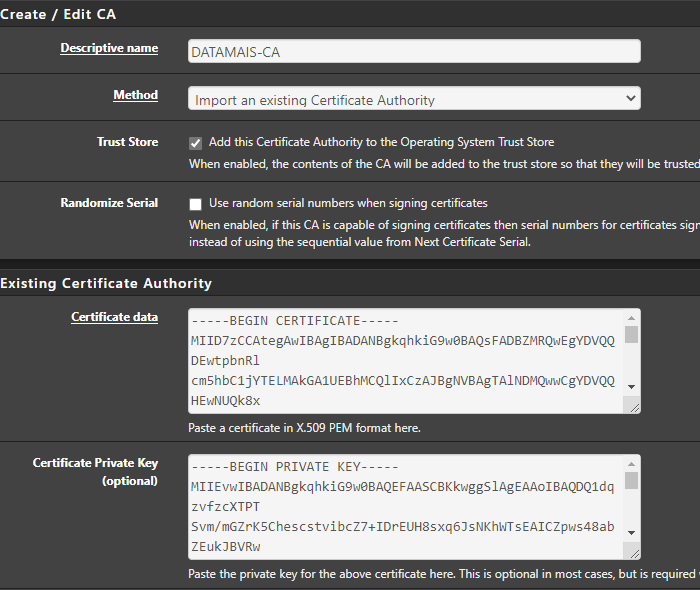
to here:
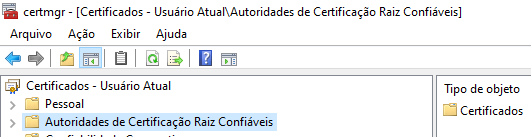
Autoridades de Certifcação Raiz Confiáveis = trusted root certificate authority
Don´t worked.
-
@hugoeyng well that is not the CA that signed off on your gui cert.. That is a CA for openvpn you must of created when you ran through the wizard for openvpn.
Create a cert with a CA you created, and trust.. Set your gui to use that cert and your browser will not balk at it..
I have gone over this multiple times to be honest.. Let me dig up one of the older threads with pictures. Here is one from 2019
-
Or realise that it isn't actually any less secure and carry on. In fact it can be argued that by having a server cert issued by a trusted authority you never actually check it.
If the cert changes your browser will still alert you to that and prompt you to accept the new cert. At which point you can start investigating if it wasn't something you expected.Steve
-
I am with steve, the self signed cert is just as secure as one signed by a ca you trust. Its just less annoying for your browser to bug you about it.
You could argue that if your just accessing it locally, who exactly would be sniff your traffic that you would need to worry about end to end encryption or even validation that it is in fact your pfsense ;)
-
@hugoeyng The cert validation verifies the hostname matches the certificate, and the certificate is valid (it is from a known good Certificate Authority). If you aren't using a hostname then an IP will never match the certificate. If you are using a hostname then the two options are to import your pfSense's CA certificate into your PC as mentioned above, or buy a valid certificate for the hostname...which will require using a public domain name.
Either way the connection IS encrypted, because the browser-to-web-server (router) encryption works...the browser is just complaining that it doesn't recognize the name and/or certificate, which is what it is supposed to do when you visit a site like that.
We also just accept the self-signed cert.
-
@steveits said in "Non secure" pfSense URL:
hostname then an IP will never match the certificate
Not actually true ;) if you have put in the IP in the SAN it can validate just fine.
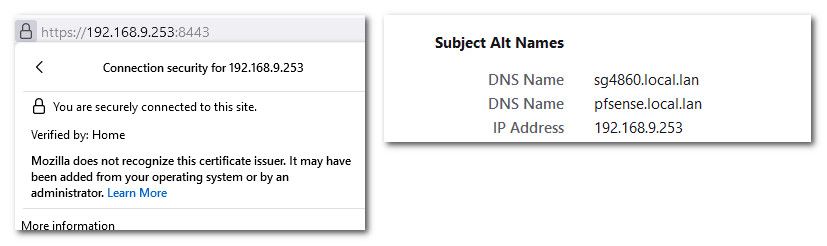
Nice thing with creating your own CA and signing your own certs with them, you can use whatever fqdn you want, and you can use rfc1918 IPs as SAN as well, etc. And if you had created them before the browsers got a stickily about age of the certs, you could have made them valid for pretty much how ever you wanted to make them.. Mine are good for 10 years.
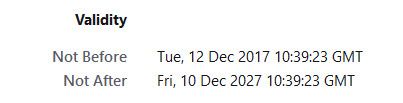
I still want to play with if I set time to before browsers put in that limit on age when create the cert and see if works ;) I will prob play with that when I finally get around to changing to home.arpa domain.
-
@johnpoz great. It worked fine.
Thank you very much. Your are the guy.
I hope to find so clear answer of how to install a patch or how to fix "dummynet: bad switch 21!" But this is another topic. Thank you again.
-
@hugoeyng said in "Non secure" pfSense URL:
dummynet: bad switch 21!
That is fixed in current dev snapshots but it's not something you can patch at run time to 22.05.
22.11 snapshots should be available very soon.Steve
-
@stephenw10 Thank you, Steve.
I will wait. -
If someone is interested in build their own PKI at home xCA
let you create your own certificates with much more abilities under your full control. xCAIt is available for MacOS, Windows and Windows portable.
-
@dobby_ why not just the cert manager in pfsense? You can create CA, sign certs.. etc. etc..
-
I agree with John. I even use it to create certs for other devices on my network.
-
@dobby_ said in "Non secure" pfSense URL:
If someone is interested in build their own PKI at home xCA
let you create your own certificates with much more abilities under your full control. xCAIt is available for MacOS, Windows and Windows portable.
It is nothing you must do. Only if you are interested.