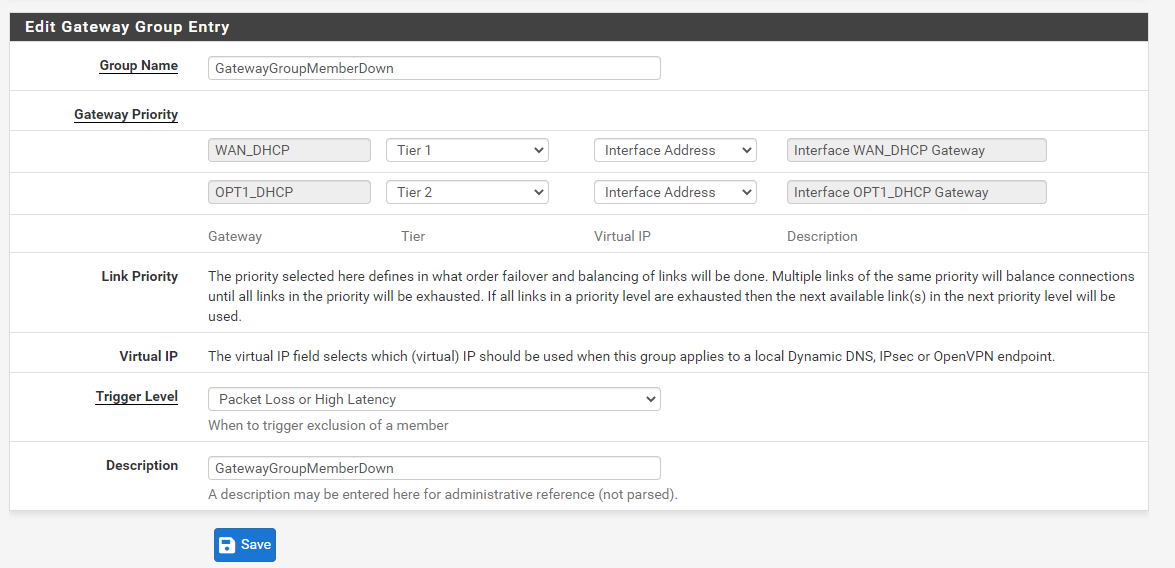
Failover to tier2 WAN when Tier1 WAN down
-
@umtsti
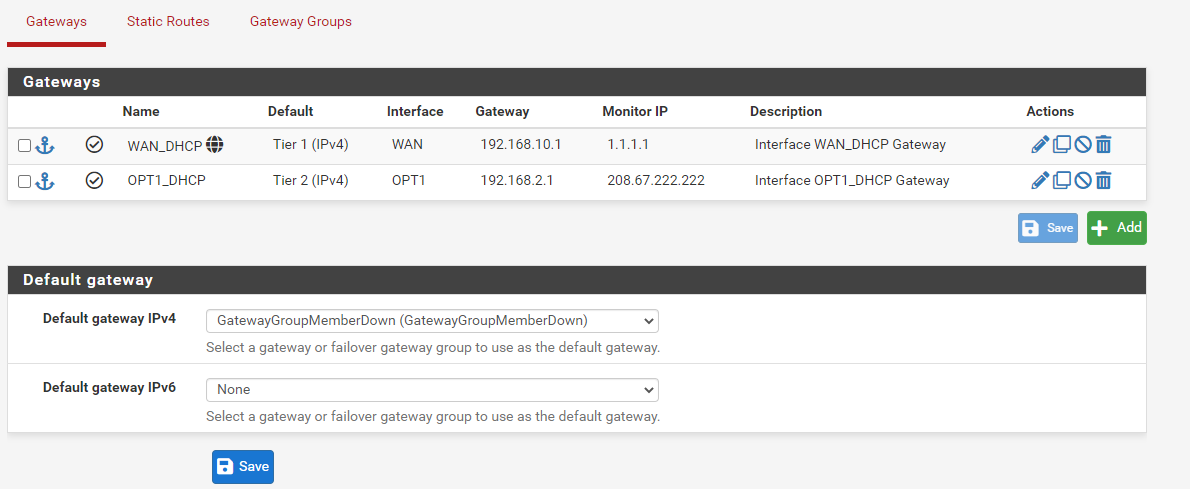
Is the outbound NAT in automatic mode?There is no need to state the gateway group in the firewall rules, since it is set as default gateway anyway.
This route directs any matching traffic to the actually used gateway. Hence you cannot access internal destination IPs, for instance if you use pfSense for DNS resolution. -
@viragomann Hello, I have checked the nat rule. Yes I think its in automatic mode. You can see the ss.
if default gateway set to gateway group, is it okay to delete gateway group firewall rule ?
-
By the way, I'm using windows DNS server which connects to dietPi as dns server.
-
@umtsti said in Failover to tier2 WAN when Tier1 WAN down:
if default gateway set to gateway group, is it okay to delete gateway group firewall rule ?
Yes, so the next rule will be applied, which uses the default gateway.
By the way, I'm using windows DNS server which connects to dietPi as dns server.
I guess, the DNS server is also within your LAN. So traffic between LAN clients and the DNS server will not pass pfSense and hence the rule doesn't affect it.
-
@viragomann Yes my dns server IP is 192.168.1.73. This is windows dns server and active directory in the same time. On Windows dns server, upstream dns server 192.168.1.77 diet pi is defined which used to block ads. On the dietpi, 193.192.98.8 and 212.154.100.18 defines which are are local internet provider's dns IP adresses.
On my dhcp server, 192.168.1.73 which is windows dns defines.

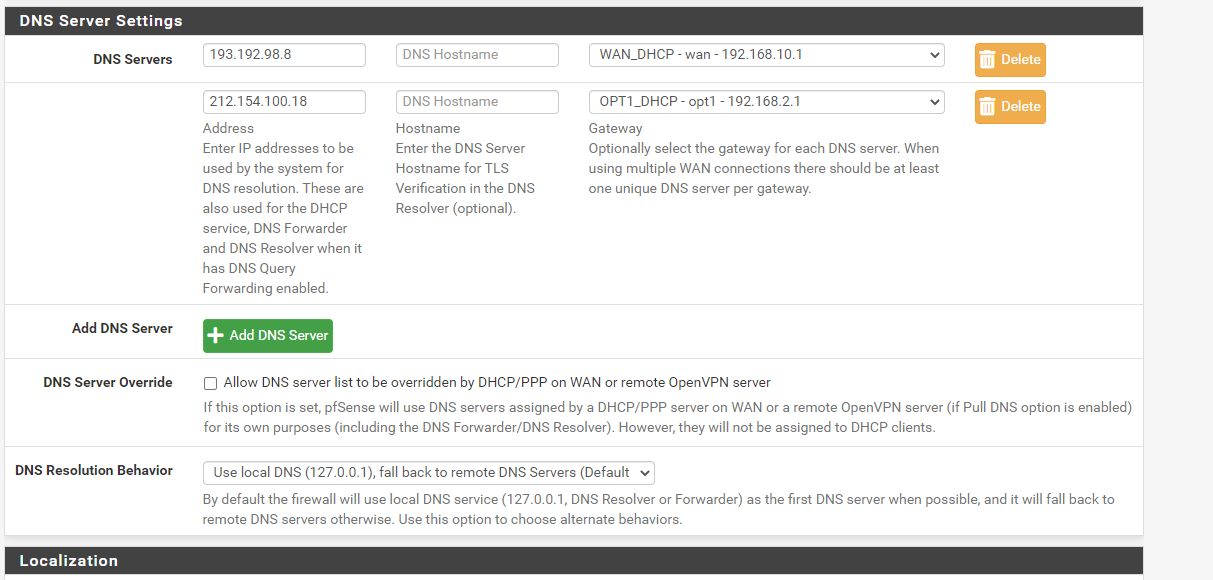
I'm not sure if this was the problem. On the general setup page DNS server settings were 192.168.1.73. Now I have changed them like below.
-
@umtsti said in Failover to tier2 WAN when Tier1 WAN down:
On the dietpi, 193.192.98.8 and 212.154.100.18 defines which are are local internet provider's dns IP adresses.
This could be an issue if the DNS server accepts only requests from inside the ISPs network.
I guess, the second WAN is outside of this network and you possibly not able to access the DNS servers. -
If this would be my setup I would more looking on two totally different points here, if you are doing load balancing
between or over this 2 WAN Ports/Lines you get fail over for "free" on top of all! If you balance the entire traffic over both gateways and one is failing all the traffic is going over the last one and if it come up again you load balance between them like before. You can chose between 3 methods;- policy based routing
- session based routing
- and service based routing
-
@dobby_
Yes it does make sense but why my config does not work that’s so interesting it think. How having internal dns server affects this setup that I don’t get it. I hope someone can give me a solution about this -
@umtsti
If not done right yet I would really try out read over this 3
websites to ensure that all if present and given to your set
up.Gateway Settings
Load Balancing and Failover with Gateway Groups
Policy Routing, Load Balancing and Failover Strategies -
@umtsti
As I mentioned already above, I suspect that you have a DNS issue.
So check if DNS resolution works when your internet is failing. -
@viragomann How can I check that ? I can reach both internal dns servers when tier 1 wan down. Am I checking right thing ?
-
@umtsti
The point is if the host name resolution is really working.The web browser should determine if it's a DNS issue. So possibly the error message gives hints.
However, I would take the hostname which you cannot access from the web browsers address line and try an nslookup (on Windows).
E.g.nslookup youtube.com -
@viragomann For the ones who can fase same issue, I think I found the solution. After filled the DNS information under System - General Setup like below, WAN failover workink how its supposed to be. Its insterestink its needs to be maintained in here
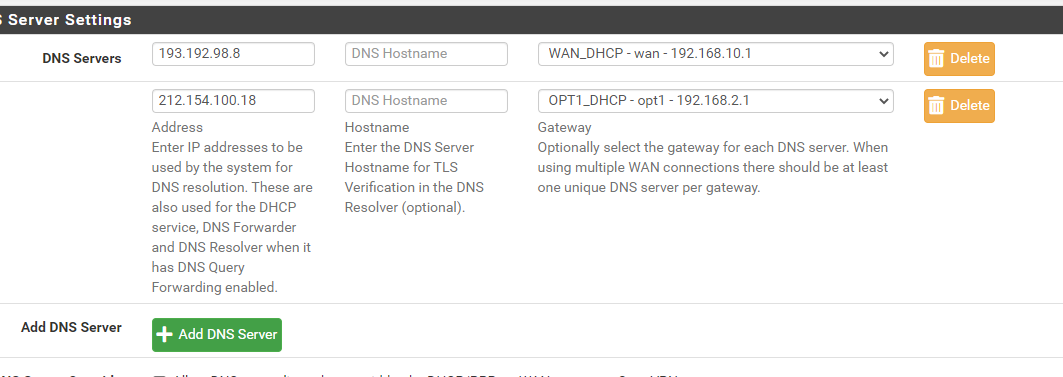
-
@umtsti
These are the same settings as you posted above.
So I'm wondering, why it would behave different now.Anyway, these settings only affects pfSense Name Resolution normally, If you have configured your Network as you said above.
However, there might some settings be different. That's why I suspected a DNS issued.