SG-3100 switch weird behavior (resolved)
-
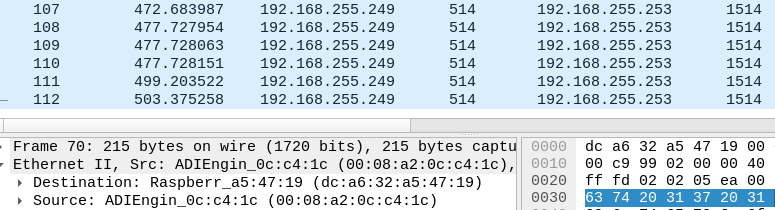
@stephenw10 It seems that its only going to LAN1..
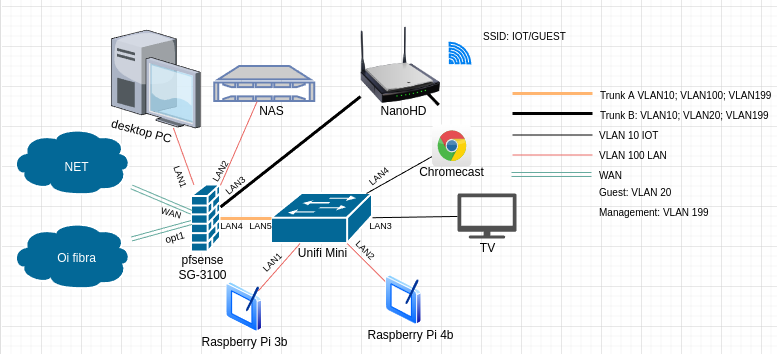
raspberry pi 3 in which you see the tcpdump above is connected to the switch unifi mini.
Let me perform this test again, but in the NAS which is connected to LAN2 of pfsense, one sec.
-
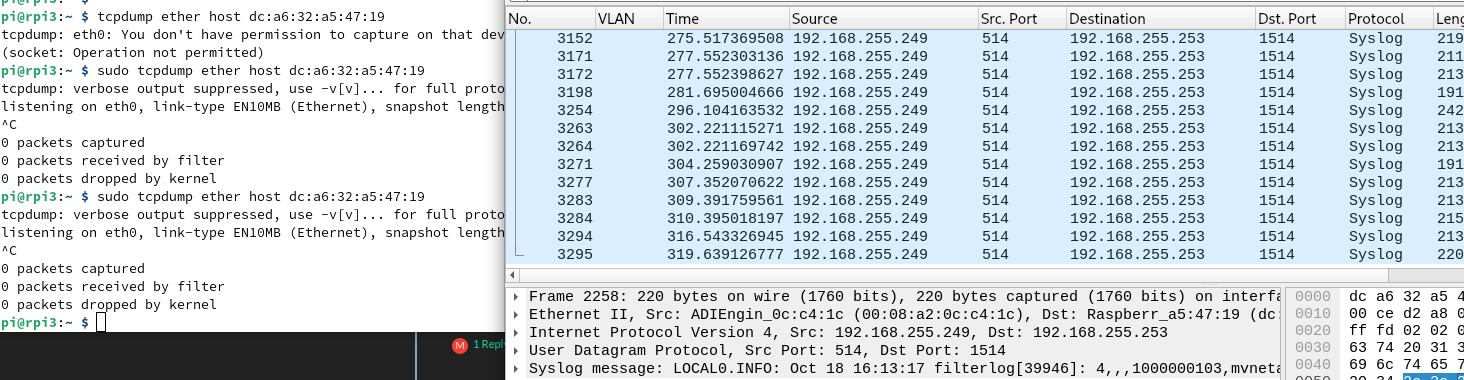
Hmmm, its going to port LAN2 of pfsense too:
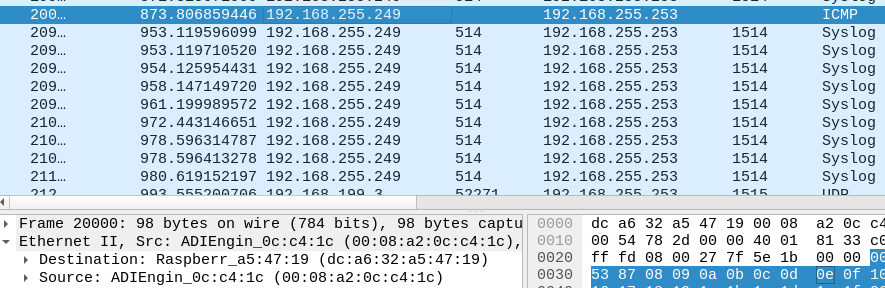
NAS IP is 192.168.255.252 (tcpdump) (LAN2 of pfsense)On the right, wireshark running on desktop (LAN1 of pfsense)
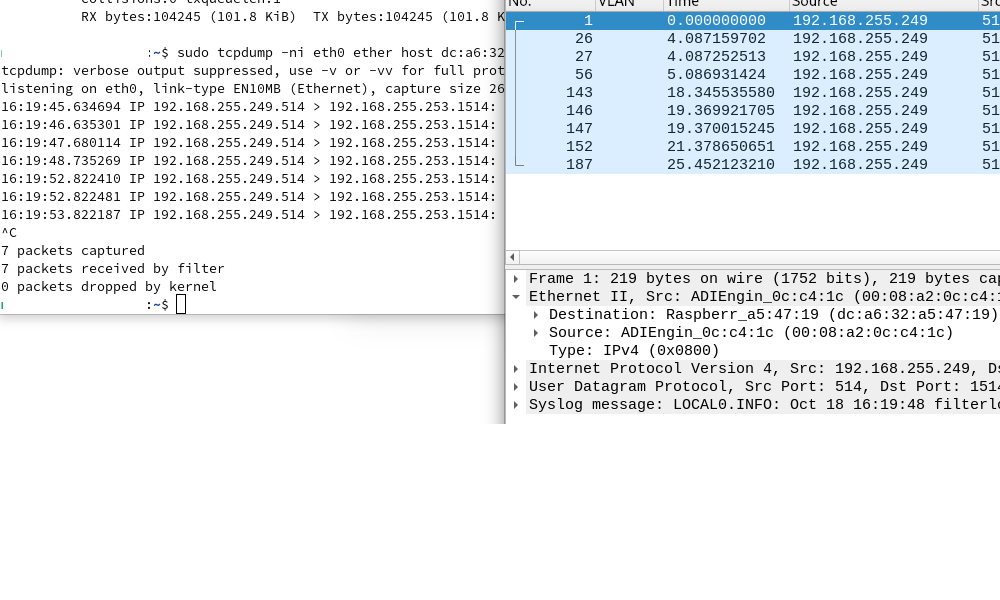
-
Aha, interesting. You wouldn't expect so see it on one of the other Unifi swtch ports because it should only send it out of the port that MAC is connected to. So to the RasPi4 there.
The same should be true of the switch in the 3100 The fact it seems to be sending it to all ports implies that it no longer has a an entry for the MAC address in it's table. If it was an incorrect entry as I speculated earlier then it would only send from port 1.
Because that traffic is UDP with no replies it never sees any traffic from the RasPi4 to repopulate the table. Is the RasPi configured with a static IP?It seems unexpected that the table entry has expired though. How long does it take to fail after sending some pings approximately?
Steve
-
@stephenw10 said in SG-3100 switch weird behavior:
How long does it take to fail after sending some pings approximately?
the default cache in pfsense is like 20 minutes, but maybe not for the switch mac table? Is there anyway to view the switches mac address table?
-
@stephenw10 said in SG-3100 switch weird behavior:
Because that traffic is UDP with no replies it never sees any traffic from the RasPi4 to repopulate the table. Is the RasPi configured with a static IP?
raspberry pi 4b its on dhcp, no services running on it, only graylog, which means that the device only receives UDP data.
It seems unexpected that the table entry has expired though. How long does it take to fail after sending some pings approximately?
I'll try to get that info right now.
-
@johnpoz said in SG-3100 switch weird behavior:
the default cache in pfsense is like 20 minutes, but maybe not for the switch mac table? Is there anyway to view the switches mac address table?
I'm really missing my old Cisco days, show mac-address table vlan x :)
-
@mcury hehe - yeah would be easy to see then.. Why I like my routers with interfaces, leave the switch ports to the actual switches ;)
-
@johnpoz said in SG-3100 switch weird behavior:
@mcury hehe - yeah would be easy to see then.. Why I like my routers with interfaces, leave the switch ports to the actual switches ;)
:) Yes, you have a point there ehhe
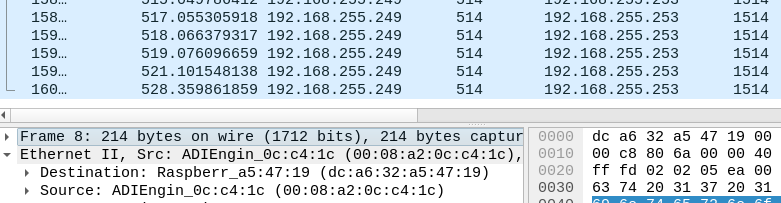
tcpdump in pfsense during the DHCP negotiation with raspberry pi 4b

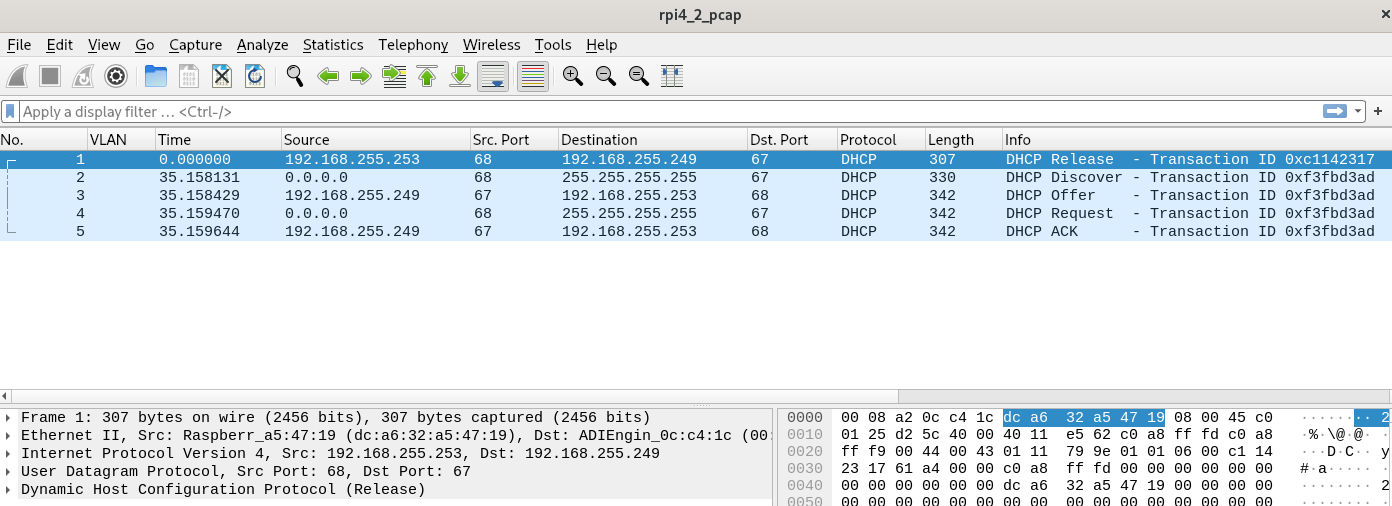
-
Yeah the pfSense ARP cache expiry time is completely independent of the switch MAC table. I don't believe there's any way to query the switch IC for the table or for the expiry time.
Steve
-
@stephenw10 said in SG-3100 switch weird behavior:
Yeah the pfSense ARP cache expiry time is completely independent of the switch MAC table. I don't believe there's any way to query the switch IC for the table or for the expiry time.
Steve
3 minutes exactly.
-
I recorded, not sure if its going to be useful..
arp_problem.zip -
Hmm, well that seems very precise. Unlikely to be random then. The Marvell 88E6141 has a 2048 address MAC table. I'm going to assume you don't have >2000 devices!
I guess it's feasible something could be generating random MAC continually and filling the table. You would see that in a pcap though.
I can't find a value for a default expiry time. I'm not sure why it would expire at all.
If the table were being reset I might imagine something else would be reset too. Are you seeing any other traffic interrupted at the 3min mark?Also can you confirm this is just unexpected, it's not actually failing to pass any traffic?
Steve
-
@stephenw10 said in SG-3100 switch weird behavior:
Hmm, well that seems very precise. Unlikely to be random then. The Marvell 88E6141 has a 2048 address MAC table. I'm going to assume you don't have >2000 devices!
Not even close.. 25 approximately..
If the table were being reset I might imagine something else would be reset too. Are you seeing any other traffic interrupted at the 3min mark?
No, everything is normal, I noticed it during a packet capture to check something else, otherwise I wouldn't even notice it..
Also can you confirm this is just unexpected, it's not actually failing to pass any traffic?
No, my network is running perfectly, the only issue is this, it seems that the marvell switch spams the packets to everyone since the mac table expired..
I'm thinking here, maybe install something in the Raspberry Pi 4b to force it to use the internet every 3 minutes?
Maybe a cron to run a single ping command? -
Yes, that would correct it. Doesn't have to be to something external, it just needs to hit the switch in the 3100.
You could set the ARP timeout in pfSense to <3mins. That way pfSense will ARP for the RasPi when it times out and the RasPi will respond refilling the switch table.
That's an easy test:[22.11-DEVELOPMENT][admin@3100.stevew.lan]/root: sysctl net.link.ether.inet.max_age=120 net.link.ether.inet.max_age: 1200 -> 120Steve
-
@stephenw10 said in SG-3100 switch weird behavior:
sysctl net.link.ether.inet.max_age=120
done:
[22.05-RELEASE][root@pfsense.home.arpa]/root: sysctl net.link.ether.inet.max_age=120 net.link.ether.inet.max_age: 1200 -> 120 [22.05-RELEASE][root@pfsense.home.arpa]/root: -
Strange, sometimes it doesn't take 3 minutes for the problem to happen.
I'm not sure if the Marvell mac address is really expiring, or if the problem is something else..I reverted the change, to 1200 and configured a cron job in rpi4
*/1 * * * * /usr/bin/ping 192.168.255.249
Lets see how that goes..
-
I expect that to solve it.
This has been interesting, I've never had to look into it too closely before. I can't find a specific value for the 3100 switch but for the switch in the 7100, which is from the same family of devices, the default MAC address aging time is 300s (5 mins). That has a larger table size so 3mins for the 3100 doesn't seem that unreasonable.
I suspect this might be simply the traffic pattern you have to the RasPi4. The fact it's mostly UDP where it never sends a reply.
Steve
-
@stephenw10 I believe that is the issue..
My cron is smashing pfsense with pings, let me change that cron to 1 minute -
This seems to be enough..
* * * * * /usr/bin/ping 192.168.255.249 -c 2 -
This solved the problem, 13 minutes of cron job running, no more problems..
Really thanks for the help @stephenw10 and @johnpoz :)