When Do/Don't VLAN Tags Get Applied?
-
I think I'm missing a piece or two from the puzzle.
Setup for context (multiple external IPs);
- Internet
-
- Modem
-
-
- Physical pfSense Firewall
-
-
-
-
- UniFi Managed Switch
-
-
-
-
-
-
- Physical Server
-
-
-
-
-
-
-
-
- VM - HelloWorld
-
-
-
-
So, I have;
helloworld.contrado.cloud --> 1.2.3.4 (Public IP)--> 192.x.x.x.x (Private IP) via pfSense NAT --> UniFi Managed Switch --> Physical Server --> VM - Hello World
I've noticed an interesting behaviour. That when I do/don't configure a Native Network (but has VLAN traffic managed for VLAN X, Y, Z etc.) within the Port Profile within the UniFi Managed Switch layer that things either do or don't work.
Now, I'm fairly sure the reason for this is that as usual in IT that 'it depends'. i.e. it depends on if the network packet does or does not have a tagged VLAN or not.
The HelloWorld VM is on VLAN X.
So, my conclusion is that in the scenario where there is no Native Network configured (but has VLAN traffic managed for VLAN X, Y, Z etc.);
- Traffic from AnotherVMOnVlanX would route traffic through to HelloWorldVM fine as it routes up from the VM to the UniFi Managed Switch (where the VLAN tag is applied) then sends the network packet on it's merry way
- Whereas, traffic from the Internet, because pfSense has NAT then that is sending the traffic untagged straight through to UniFi Managed Switch (untagged) and hence UniFi Managed Switch then drops the packet because there is no default Native Network configured so it doesn't know what to do with it, even though the VM is on VLAN X - ultimately the packet doesn't get through and the HelloWorld index.html page doesn't load.
I think I've come to the correct conclusion here. But posting the question more to clarify my own thoughts and to make sure I've come to the correct conclusion and/or I'm completely wrong and there is something I'm not understanding correctly.
Side note: I do wish there were better debugging tools to trace things through the entire Request/Response life cycle across every step along the journey. It's an extremely challenging task to track the real basics with finding where the problem is.
-
@michaelcropper VLAN tags are applied when they are going through a tagged interface for that VLAN. Pretty straight forward... traffic comes in on port 2 which is VLAN 100 (natively) and it goes out on port 1 which is TAGGED 100, the traffic comes out of port 1 tagged. Traffic for VLAN 100 comes in port 1 tagged and if it is going to Port 2 it comes out untagged.
Basically if you have a VLAN for the VM it is tagged traffic all the way to the VM host, where it comes in on a single dedicated vNIC untagged, or it comes on a trunked vNIC tagged. or untagged, depending on how your VM is processing that traffic.
-
@rcoleman-netgate This is the setup at present;
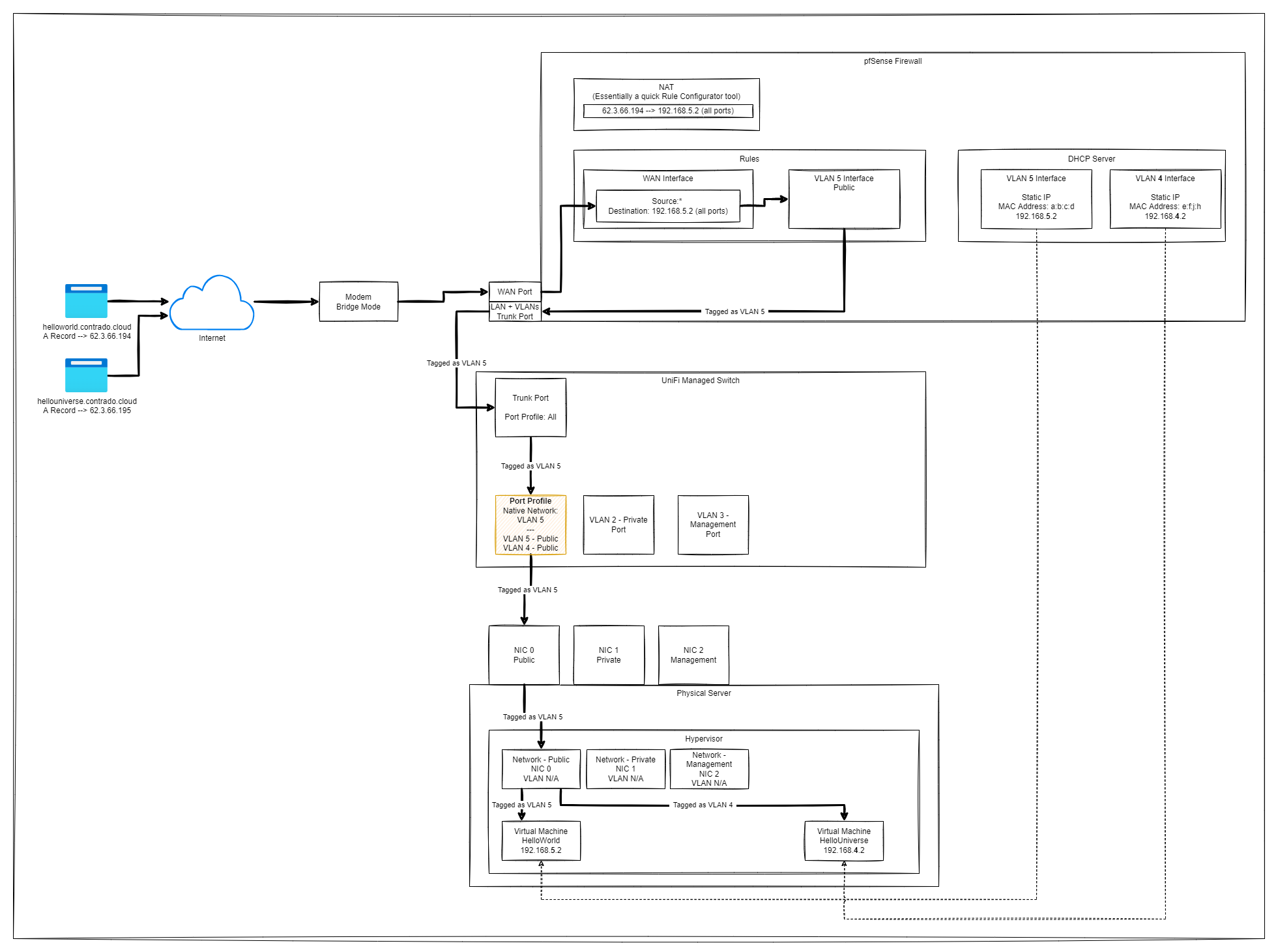
What is behaving weirdly which I'm struggling to get my head around is the orange box highlighted on the diagram. When that has a Native Network of VLAN 5 (plus the VLAN 4), this works. But if I remove the Native Network and just have VLANs 4 and 5, it doesn't work.
I'm thinking I've got something not quite configured correctly at the bits beneath this.
At present, the two websites are both configured within the same VLAN 5. What I want to test next is to split them out each onto their own VLAN for added security.
I even just tried creating a new vNIC on the Hypervisor and configured that as VLAN 5, attached that to the VM. Updated the static IP mapping in pfSense to use the new MAC address, but that didn't work, the website didn't load. Perhaps I needed to configure something at the Linux level and didn't.
Feels like I'm just missing a piece or two of the puzzle that isn't quite lining up correctly in my brain. Hopefully the diagram helps to set the scene and hopefully identify the thing that is obviously wrong in that diagram that I'm just not seeing.
-
If you need to set the PVID on that port to 5 to be able to get two way traffic then the traffic is arriving on it from the hypervisor untagged when it shouldn't be.
It might also be leaving untagged from the switch if you set that. I'm unsure what takes priority in a Unifi switch. It can't be tagged and untagged on VLAN5.
That would make more sense though because trying to arrange the hypervisor interface to be tagged on way only is probably difficult!So I'd guess the physical NIC on the hypervisor is not using VLAN5 as it should be.
Steve
-
Thanks for the info @stephenw10
I've cross-posted this questions in all the forums for tech in the stack. Here's what the UniFi community has had to say so far, this one I'm just trying to get my head around yet, https://community.ui.com/questions/When-Do-Dont-VLAN-Tags-Get-Applied/cce6859a-1b7d-40d4-80f7-6b894fe3fe45#answer/563f8575-942a-4687-a833-9a2d0b1d08b7 - Sounds like you're saying something similar when you say "It might also be leaving untagged from the switch if you set that."
Summary diagram for ease;
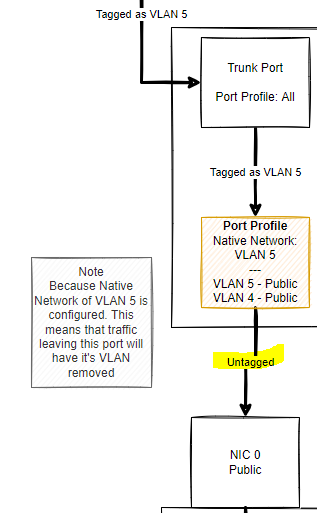
Terminology: PVID = Port VLAN ID
So at present there are 4x physical cables going from the UniFi Managed Switch to the physical server with the hypervisor installed.
So I have created 4x networks initially on the hypervisor, just so that I could figure figure out which physical NIC mapped to which physical cable and hence which VLAN it should be using;
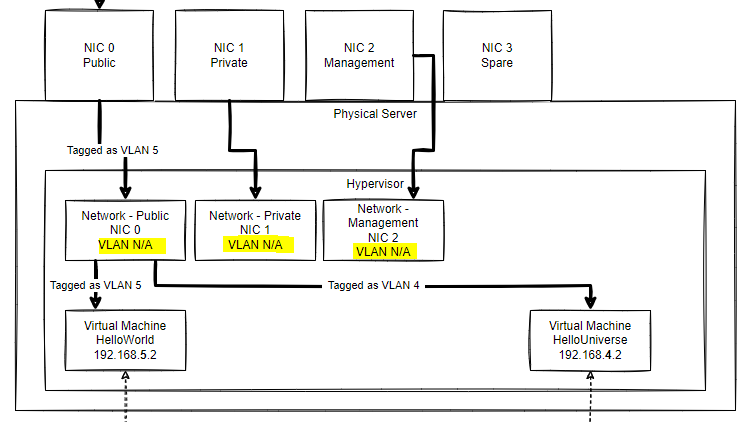
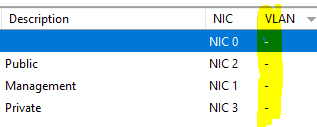
As you'll see in the above though, those networks do not have a VLAN configured. This is the snippet from the hypervisor (the numbers don't line up to the diagram, but you get the idea)
My understanding around networking across the different physical and virtual layers is that 'things' should be tagged at every step along the journey.
I'm going to try this next;
- Create a Hypervisor network - Public VLAN 5, tagged as VLAN = 5, on NIC 0 (diagram, not screenshot)
- Spin up a new VM with that new network attached + install OS (easier than messing around with Linux networking)
Feels like this is a step in the right direction.
-
Yes this is almost certainly because the hypervisor is not actually using VLAN5 for the interface linked to that VM so you actually need to untag it at the switch to make the connection. Which is what you were unintentionally doing by setting VLAN 5 as the 'native VLAN' for that port.
So, yes, set the hypervisor interface to VLAN5 on NIC0 there. Unset VLAN5 as native for the switch port.
Additionally you can probably choose to pass the traffic tagged to the VM in the hypervisor but you'd need to actually set VLAN in the VM then which you usually wouldn't do.
Steve