pfsense port forwarding/ WAN Default deny rule IPv4 (1000000103)
-
@bob-dig sorry
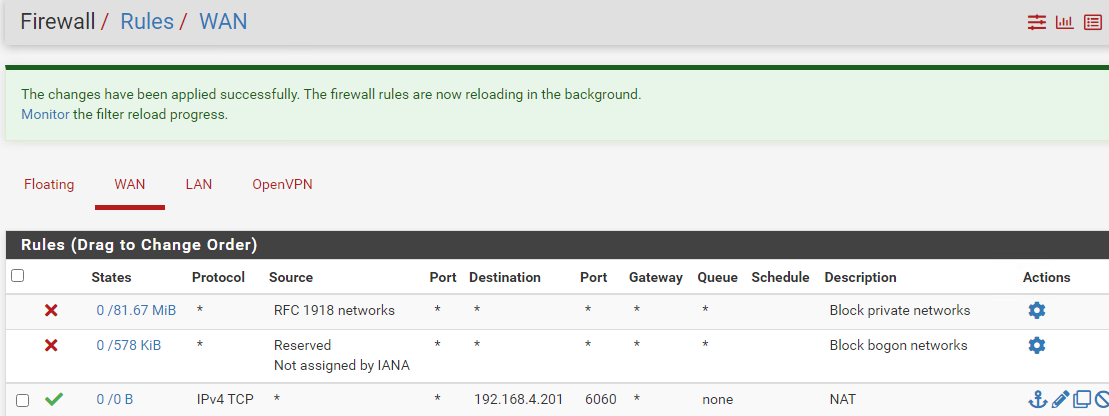
-
@learn Looking good so far so problem must be somewhere else, specific to your environment.
-
@bob-dig said in pfsense port forwarding/ WAN Default deny rule IPv4 (1000000103):
specific to your environment.
suchh as ?
please help !
-
@learn so is default deny your seeing actually to the port your trying to forward? You just show a deny, you don't so that port udp or tcp even that is being blocked.
From your firewall rule showing 0/0 B tells me that rule has never been evaluated. So no traffic has hit your wan that would match your port forward and firewall rule.
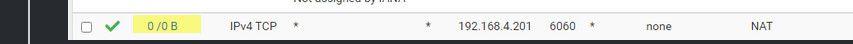
-
@johnpoz im trying to do a remote access so im using tcp with a custom port instead of 3389
-
@learn again you rule not showing any hits.
Here I setup a rule for port 6060, never going to work because my 192.168.9.100 forwarding too not listening on that port
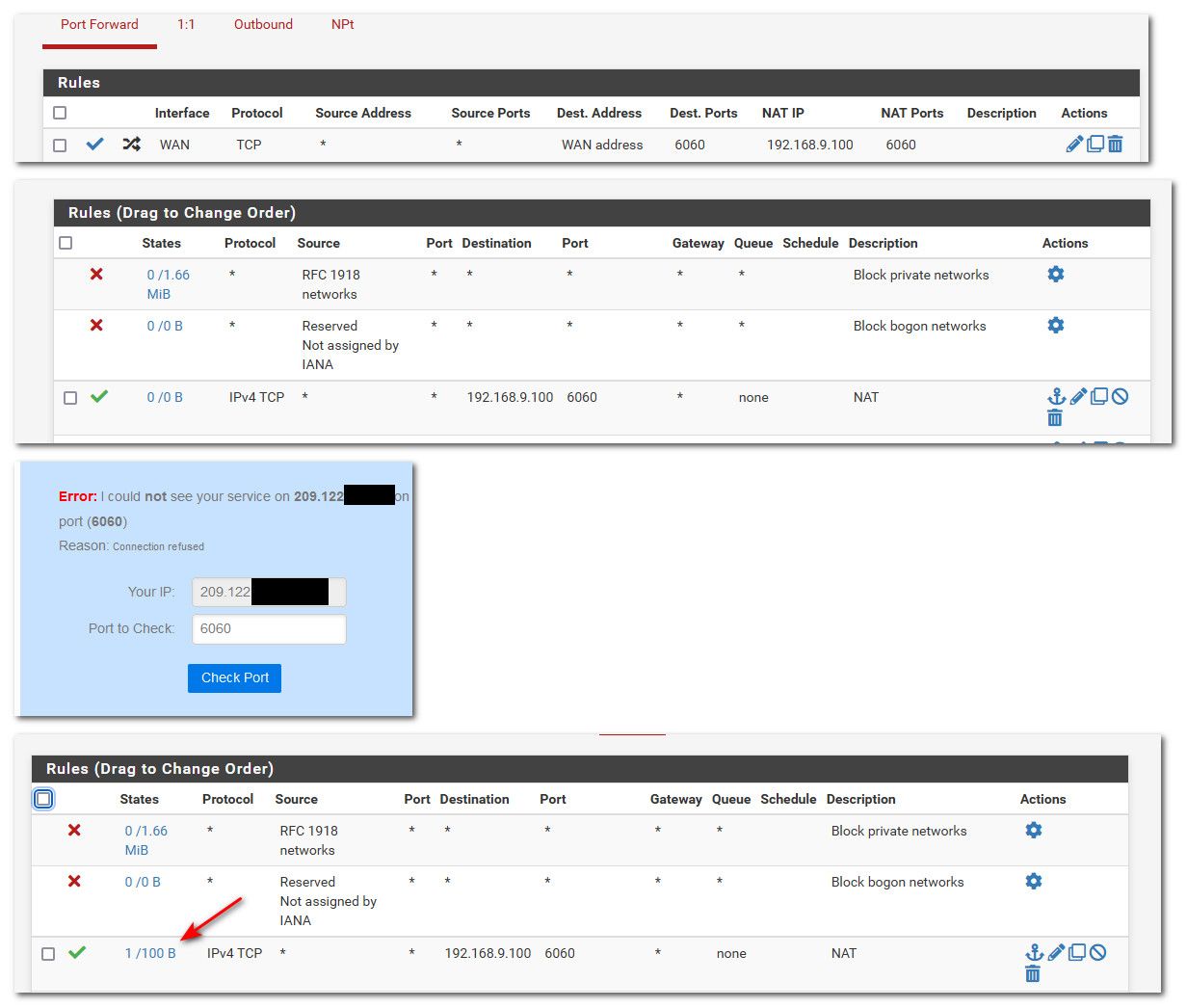
But notice when I try and go there (from can you see me . org), that after my rule shows it was evaluated, its no longer 0/0 B, but shows that it was used in the states table.
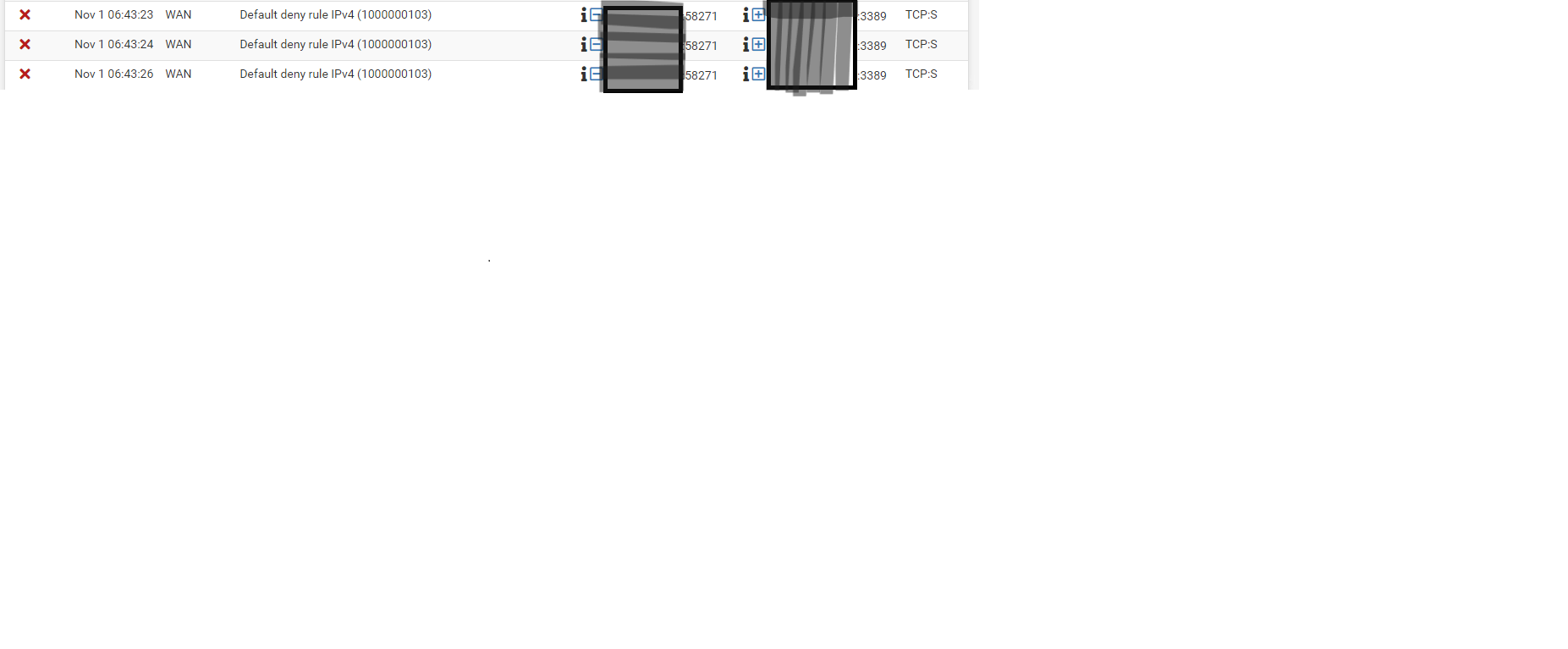
Your deny actually shows to your wan IP on the 6060 port your trying to access.. via TCP? You didn't show the full log, you just show "something" was denied..
-
@johnpoz i tried differnt ports even the deafult port and did a diagnostic test port
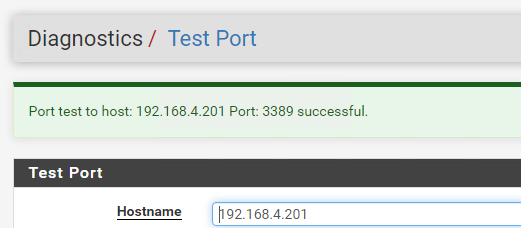 it shows the port is good but still not able to access
it shows the port is good but still not able to access -
@learn that is just a local test not remote..
Again - your rules is not showing any traffic actually hit it, that 0/0 B in the states column shows that pfsense saw no traffic to that port.
What was actually logged as blocked.. You just show a deny.. Here would be an actual block
Here is a log showing a block, see it is too my wan IP, I blocked out last 2 octets of my public IP.. But see there is the port is was going to, and that its TCP, and a SYN.

From your wan rule showing that 0/0 B shows that nothing has hit your public IP on that port to be forwarded. Or the numbers would change from 0/0 even if the port forward didn't actually work.
-
@johnpoz
 here what t shows in my log
here what t shows in my log -
@learn 3389 ain't 6060.
-
@bob-dig i changed to do port testing but none worked
-
@learn But it is important to test so test again towards 6060 and show the log and don't hide the beginning of those IPs!
-
@bob-dig did what you said it it the same result!
-
@learn does pfblockerng and openvpn can block portforwarding? im lost here
-
@learn no those do not block a port forward.
As mentioned that block is 3389, your port you forwarded was 6060.. if you are forwarding 6060 to 3389, then you need to hit pfsense wan on 6060, so it can forward it to 3389 on your end device.
Your port forward you posted was sending 6060 to 6060.. Not 6060 to 3389.
But that has nothing to do with it, your firewall rule allowing 6060 saw no hits, so no your port forward would never work no matter what port you wanted to send to your actual device behind pfsense.
If you want to remote desktop to something behind pfsense, and you want to use 6060 on the public internet, then your port forward should be 6060 to 3389, but you need to hit pfsense wan IP on port 6060..
On a side note, I would not recommend opening remote desktop to the public internet, be it you change the port or not. If your going to do that, you should make sure you lock down which source IPs can talk to pfsense on that port to be forwarded.
The proper way to remote into stuff on your network from the internet, would be to vpn to pfsense from your remote client.
-
@learn
Take note : when the pfSense NAT rule works, you have to check one last thing :
The firewall of the device (PC° where you want to use 3389 = probably MS Remote Desktop.Microsoft, by default, when MS remote desktop is activated, accepts only connections from it's LAN.
Example : if your PC has IP 192.168.1.10/24, then connections from any 192.168.1.x/24 are accepted. Others, like an IP from the Internet, are refused.
Solution : adapt the related Windows incoming firewall rule - or make your own rule.Again : just be ready to check and correct if needed.
edit : as said above : Microsoft has warned their OS users that MS remote desktop should not be used over public networks.
-
@johnpoz thank you so much for your help can you please show me the ideal way to port forward 6060 to 3389
-
@learn the ideal way would not be a port forward, and use a vpn. Unless you know the specific source IP you would be coming from and only allow it, opening up remote desktop to the public internet is not a good idea, even if you change the port.
But to forward port 6060 to 3389 is simple in your port forward just change the destination port to 3389
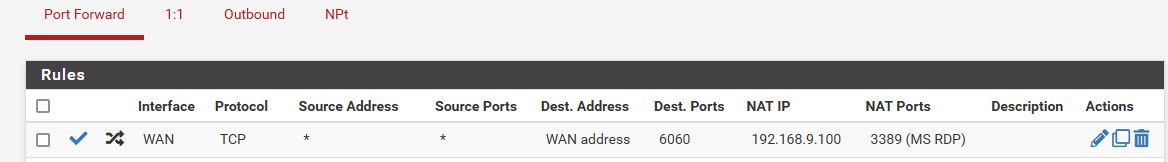
But again if your port on the public side is 6060, then for your rule to work no matter what port you send it to, you have to hit pfsense on that port. Your firewall rule you posted never showed any traffic to port 6060, the states column was 0/0
-
@johnpoz sorry for any inconvenience but nothing seems to be working
-
Like johnpoz, I created a NAT rule :
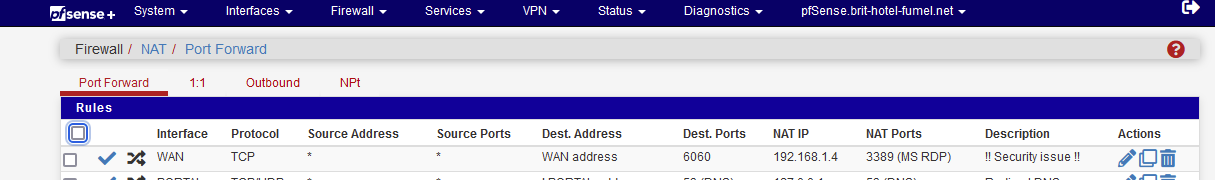
which creates a WAN pass firewall rule :
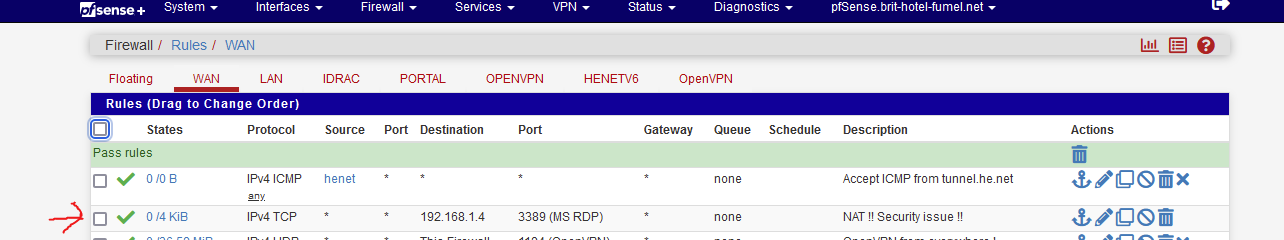
Note the IP 192.168.1.4 : an old 2008R2 Microsoft server - it has MSRDP activated on port 3389.
The firewall counter in front of the rule show traffic.
@home, I used a.b.c.d:6060 as the destination where a.b.c.d is my WAN IP, where the 2008R2 server lives (@work).I could access the remote desktop from my 2008R2 server just fine.
The creation of the NAT rule :
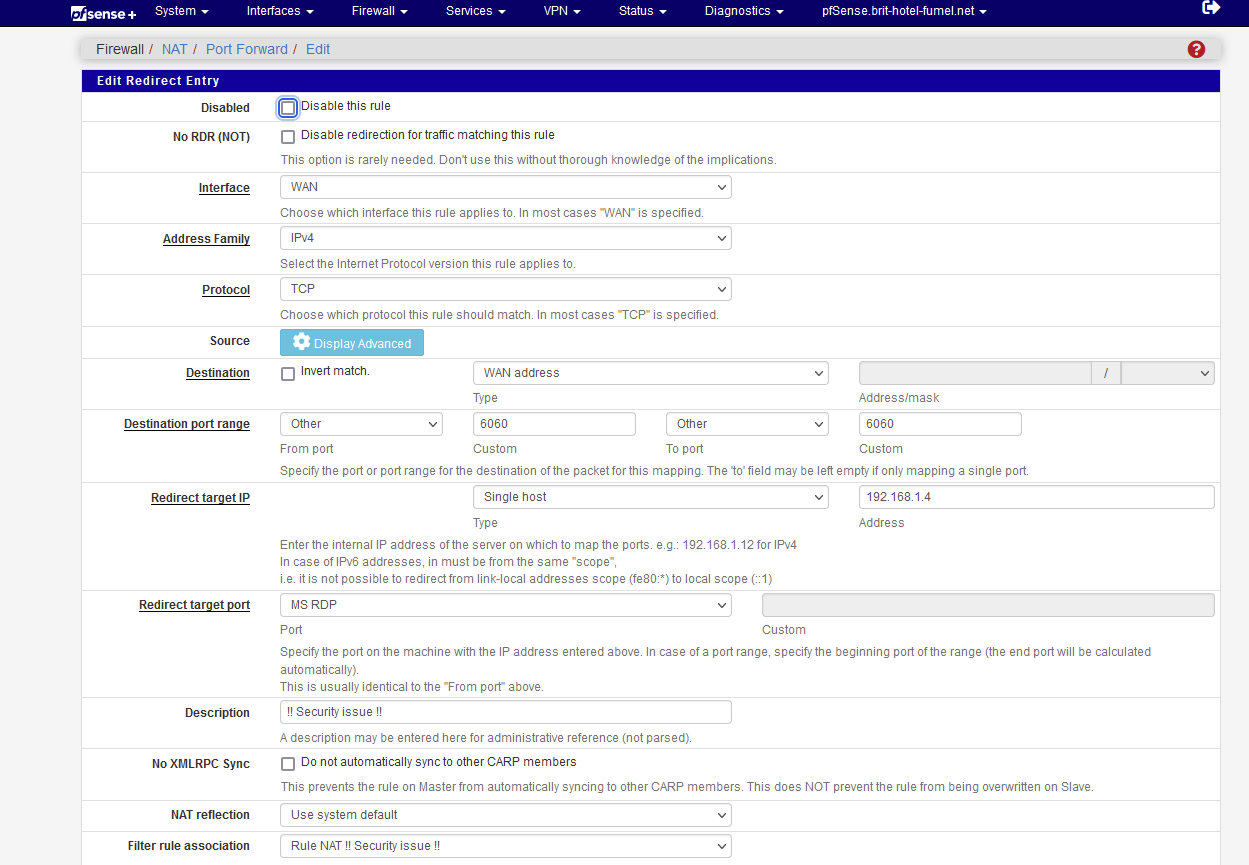
and I moved the related WAN firewall rule at the top, before the block rules (if any) - and save + apply.
Behind the screens, I had also to "NAT" my ISP router which is placed in front of pfSense, where I NAT port 6060 TCP to port 6060, to 192.168.10.3, my pfSEnse WAN IP.