Bridge external to internal vlan
-
Hi,
I'am new here and i'm looking for a new firewall.
My question is:
Can you with pfsense splice a layer3 subnet and bridge them to a VLAN?
We use now SonicWall and we can for example splice a WAN /27 in /32 adressess and send them with DHCP to a internal VLAN off a customer with Traffic Shaping. this works fantastic.
Only we can't this also with our routed subnet on the same WAN. so i need a new Sonicwall for each subnet.
I am wondering if i can do the same with pfsense.
-
@rvdk92 I took your attachment and added it to your post.
If you have further trouble posting things please let us know :-)
You need a rep of 5 to skip past the spam filters. -
You may have to define 'splice' there.
You can bridge the WAN with another interface in order to use public IPs in the WAN subnet on other hosts. However it's generally better to avoid bridging if you can and use routed subnets instead.
Steve
-
@stephenw10 Hi thanks for you quick reply.
What i mean whit split the subnet here a example:
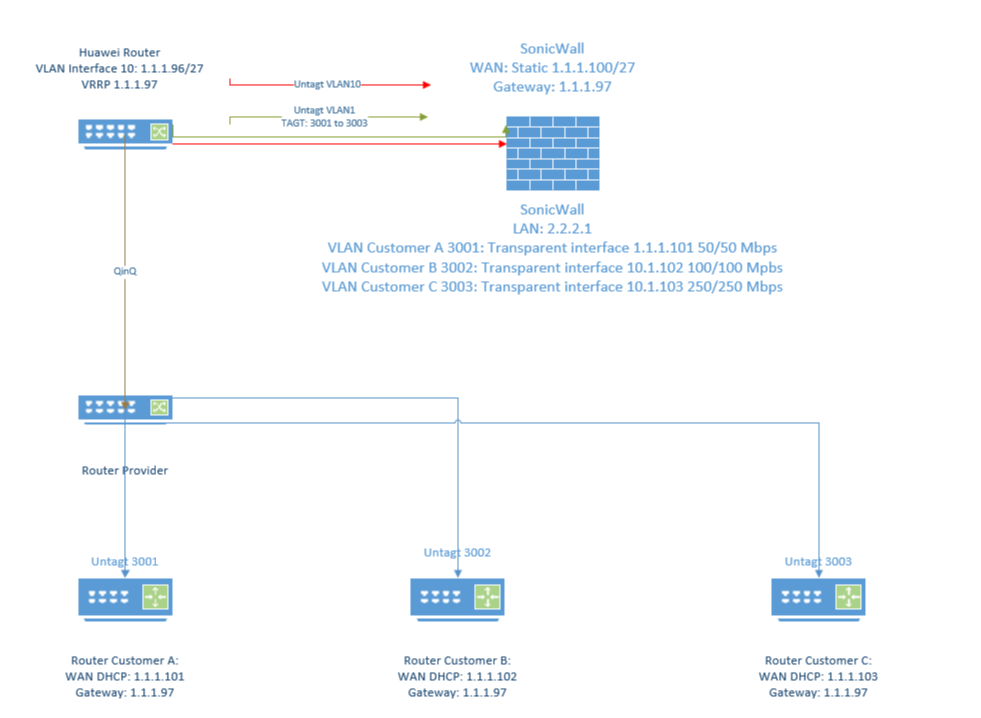
from ISP i get on VLAN10 subnet: 1.1.1.96/27
I wil use 1.1.1.97, 98 and 99 for my switches with VRRP and use 1.1.1.100/27 for WAN on the firewall.Than i like to give customer A IP 1.1.1.101 on VLAN 3001 and customer B IP 1.1.1.102 on VLAN 3001 and till to last IP.
The reason why i choose for this solution (by SonicWall.) i can give my customer a WAN IP with DHCP on there own VLAN, do traffic shaping and I need fewer ip addresses if I route a subnet everywhere from my switch.
-
Ok, if I've understood correctly you can't do that in pfSense. At least not yet.
Your customers see your firewall as their gateway? Or the ISP directly?
Is it your DHCP server handing out those IPs to the customers?
Steve
-
Hi,
Yes the DHCP server is also the firewall (SonicWall.)
I have configured now that the firewall of customer use the gateway of our routers. so the VRRP .96The only thing that the Sonicwall is doing, split the L3 subnet, send with DHCP a single WAN ip on a VLAN to customer with bandwith limit.
This works like a charm and looking for a same solution on another device.
-
Hmm, I wouldn't expect to be able to replicate that exactly in pfSense. You would need bridge WAN with all the VLANs and then filter appropriately. But if clients are using the pfSense IP as their gateway you would see asymmetric routing issues when the ISP can see the clients directly. You can work around it in various ways
You would also need to run the dhcp server on WAN and add appropriate filtering there. And I'm not sure it's possible to filter that exactly.
On top of that bridging to VLANs can introduce additional issues.If you have a test environment you could try it and see how much of that can be done. It might be enough.
Steve
-
Thank you for your answer.
To be clear, I've uploaded a picture of the situation now.
Do you see where I want to go?
-
Ok you have VLAN Customers B and C shown as 10.1.102 and 10.1.103 at the Sonicwall there. Is that just a typo?
But all the devices are using the upstream router as the gateway there which removes the asymmetric routing issue. But is also contradicts what you wrote earlier, or at least as I read it.
-
Sorry yes is typo! to quick!
But is this also possible with pfsense.. so if i can replace the SonicWall for a pfSense firewall?
-
Possibly.

It's not something I would normally advise doing. The traffic shaping could be problematic. The filtering to keep each customer separate will be...interesting.
But it might work I can only really suggest you try it if you can test it in something.
I will say that trying to run that virtualized will almost certainly fail without a bunch of additional tweaks. I would test on real hardware if you can.Steve