I am fighting this same issue in Pfsense 2.6.0 and losing the battle. Help?
-
@kilted1 said in I am fighting this same issue in Pfsense 2.6.0 and losing the battle. Help?:
https://support.surfshark.com/hc/en-us/articles/360010789259-How-to-set-up-pfSense-2-4-4-with-Surfshark
That's not terrible. Some VPN providers instructions are... bad!
They don't have you remove outbound NAT to the WAN so it will still work.They do have you leave 'don't pull routes' unchecked so they are probably passing you a new default route when you connect.
None of that should stop the bypass rule working. It probably isn't matching. What do you have in the alias? How are you testing?
Steve
-
@stephenw10
I posted how I set up the alias above but, the two sites I have in it are Amazon and Bridgecomsystems.com.
Strangely, I just tried Amazon and it worked.
Bridgecom's site "mostly" works but, they do giveaways and they use "Gleam" for them??? Gleam still see's my IP address as coming from the vpn site instead of my home IP address. And Gleam refuses to accept the data center IP address.
That seems to me the my traffic to those sites (or at least the one) isn't working.
Yeah, this is rather specific to me but I'm hoping there is a way around it. I tried to "disable" the VPN out rule and lost ALL internet access so, that won't work.
I know it's got to be something simple and stupid otherwise, I probably would have won the battle already! LOL -
@kilted1 said in I am fighting this same issue in Pfsense 2.6.0 and losing the battle. Help?:
I set up the "alias" for "URLs" as the sites have multiple ip adresses and was hoping for the easiest fix to make this work.
You used URL aliases or you just entered URLs in the alias?
Just entering URLs can only work for small sites with fixed IPs. It cannot work for anything using a CDN like, for example, facebook, netflix, amazon, google etc.
To do that in any useful way you need to use IP lists or AS numbers directly. pfBlocker can do that and keep them updated. It's never 100% though.Steve
-
@stephenw10
IF I read the Netgate Docs correctly, would a "URL Table" work?
From what I understand (from what I read about them), I would have to make a URL Table for each site (ie... Amazon or Bridgecom) and then a rule for each table. Is that correct?Or would "pfblocker" be a better option?
-
@kilted1 said in I am fighting this same issue in Pfsense 2.6.0 and losing the battle. Help?:
I would have to make a URL Table for each site (ie... Amazon or Bridgecom)
Now read again :
@stephenw10 said in I am fighting this same issue in Pfsense 2.6.0 and losing the battle. Help?:
Just entering URLs can only work for small sites with fixed IPs. It cannot work for anything using a CDN like, for example, facebook, netflix, amazon, google etc.
Also read the pfSense documentation Aliases - see the very first Note.
Example : resolve amazon.com
You get a list with IPs :
*amazon.com has address 54.239.28.85
amazon.com has address 205.251.242.103
amazon.com has address 52.94.236.248A couple of moment later, this list will change, as amzon uses a lot of IPs. They are swapping their servers in and out al the time (upgrading, load balancing etc).
So, no, you can't capture the big players with an URL or a list of IPs.
And for very understandable security and commercial reasons, amazon will not (like never) publish the entire list of IPs they can use. -
Yes, you need to use an IP list or ASnumber. You can create those manually:
https://docs.netgate.com/pfsense/en/latest/recipes/block-websites.html#using-firewall-rulesBut I would recommend using pfBlocker because it will create them automatically and keep them updated.
Steve
-
@stephenw10
I did download pfBlocker.
Looking in the available documentation it "says" that there is a way to "allow" traffic to a site but, in the settings I'm ONLY finding "block or reject" for options.I'm trying to "allow" traffic to bypass my VPN, not "block" traffic to certain sites. Will this still work?
This is way more technical than I had hoped.
And reading through the material on it, has confused me more than I already was. -
Set your list action as 'alias native' rather than block or reject. Then use that alias in your VPN bypass rule.
You probably want to use ASNumbers. You might need several dependiong on what you;re passing:
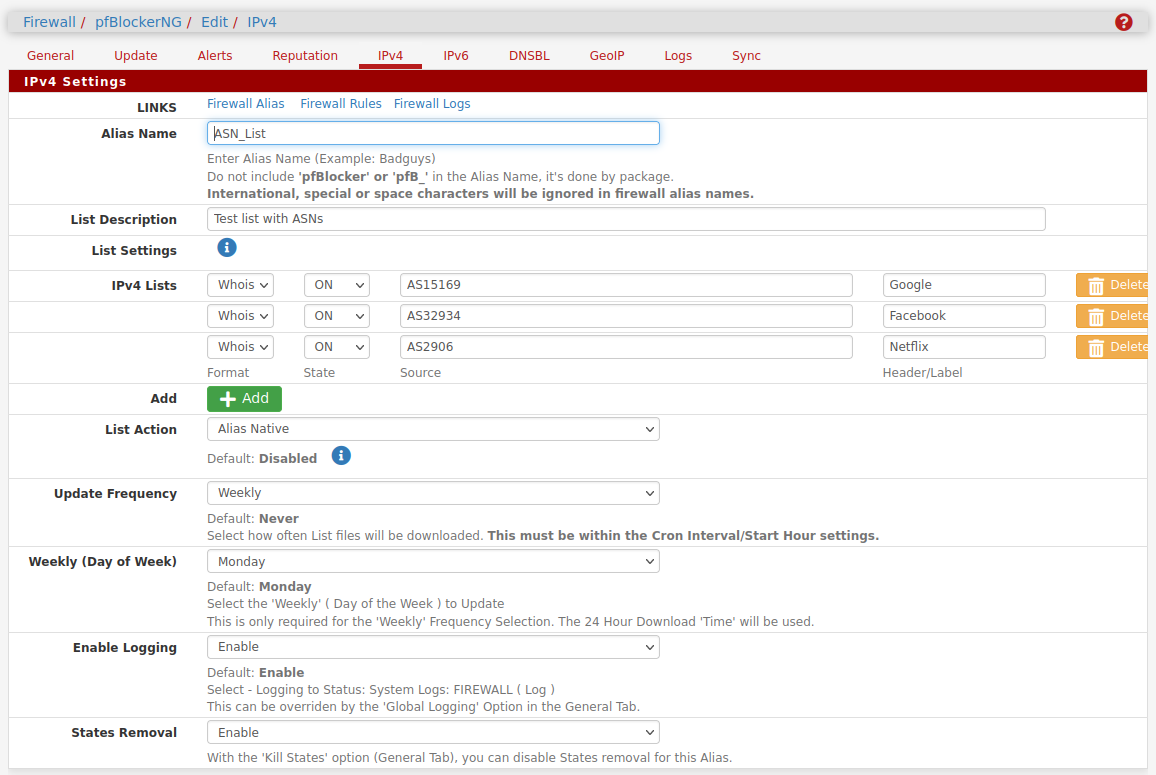
Steve
-
@stephenw10
Thank you for that and ALL of your help!I was poking round though and came up with another question.
I remembered (I was reading in the book about the rules) about the vpn having me go into the NAT and selecting "Manual Outbound NAT rule generation.
(AON - Advanced Outbound NAT)"Should I change that to the "Hybrid"?
With what I read, the manual setting completely ignores all of the auto generated rules and ONLY follows the manual one.
So to me that means, it's blocking every other access to the WAN that doesn't go through the VPN.Am I correct or just confused? LOL
I do realize that I will probably end up learning and using the pfBlocker for the alias's but, I'm wondering if this one setting is the Bigger brick wall (LOL)?
-
When you switch Outbound NAT to manual mode the auto rules are converted to manual rules at that point. From there if you added a new internal subnet no new rules would be created, as they are in auto mode, you would have to add them yourself.
In the instructions you linked it does not have you remove the rules after changing the mode (unlike many other VPN providers) so the rules to allow traffic to be translated on the WAN directly should still be present.Steve
-
@stephenw10
Again I thank you Sir!
That makes more sense than what I was thinking. I actually had hoped that was the case but, I've learned the hard way to be more pessimistic. LOLI will have to dig into the pfBlocker and do a lot more reading and might end up with more questions later.
I did figure out how to basically shut down the vpn to get to one of the sites that I wanted. I copied the VPN rule but aimed it toward the WAN (with this new rule under the VPN rule) so, when I want to go to the site that I haven't been able to up to now, I disable the vpn rule and turn it back on once I'm done with that site.
Absolutely not my preferred method but, it's working for now until I can work through a better fix.
Now at least, I don't have to worry about putting this into service. I'll just keep working on a better work around.
Thank you everyone for all of your help!
Talk about a steep learning curve. LOL -
@stephenw10 said in I am fighting this same issue in Pfsense 2.6.0 and losing the battle. Help?:
Set your list action as 'alias native' rather than block or reject. Then use that alias in your VPN bypass rule.
You probably want to use ASNumbers. You might need several dependiong on what you;re passing:

Steve
Steve,
I know this is a dumb question because I feel stupid right now but, where do I find those "ASN numbers" for pfblocker to make that list?
Thank you Sir!
Dale -
K Kilted1 referenced this topic on
-
Hmm, I think I just googled it. Like: https://asnlookup.com/organization/facebook/