Static Route and SMB
-
Hello,
I have 2 recently migrated to a netgate firewall.
My network has 2 separated networks, one of which is an internal network that is only able to be accessed by approved devices.
I am using a static route and a LAN port on the firewall to give access to the secondary network.
I have found that the LAN configuration works as expected, however the static route is problematic and things such as SMB experience a high amount of jitter, to the point of which it becomes unusable. Ideally we would like all traffic to this secondary network to go via the static route, so this is not really viable in the long term.
Is this something that there might be a silver bullet for that I've missed?
Thank you!
-
@ndub27 SMB is never great when traversing networks.
Have you tried NFS?
-
@nogbadthebad thanks for the suggestion, I should add that I migrated off a FW with the same static route setup and did not experience any of the same issues.
I have not really tried NFS as we are a windows shop. I guess I can give it a go but unsure about the practicality of it.
-
@ndub27 said in Static Route and SMB:
I am using a static route and a LAN port on the firewall to give access to the secondary network.
so you have a downstream network - what is the latency to this network. While smb yeah can be slow over a high latency connection. If this network is only a few ms away.. There should be no issues.
Creating a route off your lan interface seems like you would have a asymmetrical problem to me.. There really should never be a route off your "lan" where other devices are. That might talk to this other network.
Other networks normally would be attached to pfsense, or would be accessed via a transit network (no hosts on this network) to this other router where the other network is.
Could you draw up your network - so can see how your getting to this other network.
-
@johnpoz thanks John I will work on getting a network drawing to you when I have the time in the next day or so.
Latency over wireless is 2 - 4ms so I don't believe that is an issue.
-
@ndub27 so it is a local network, that yeah asymmetrical would be the problem with something like that most likely.
You run into this issue.
When downstream is not natted and you have communications between downstream and hosts that sit on the transit network.
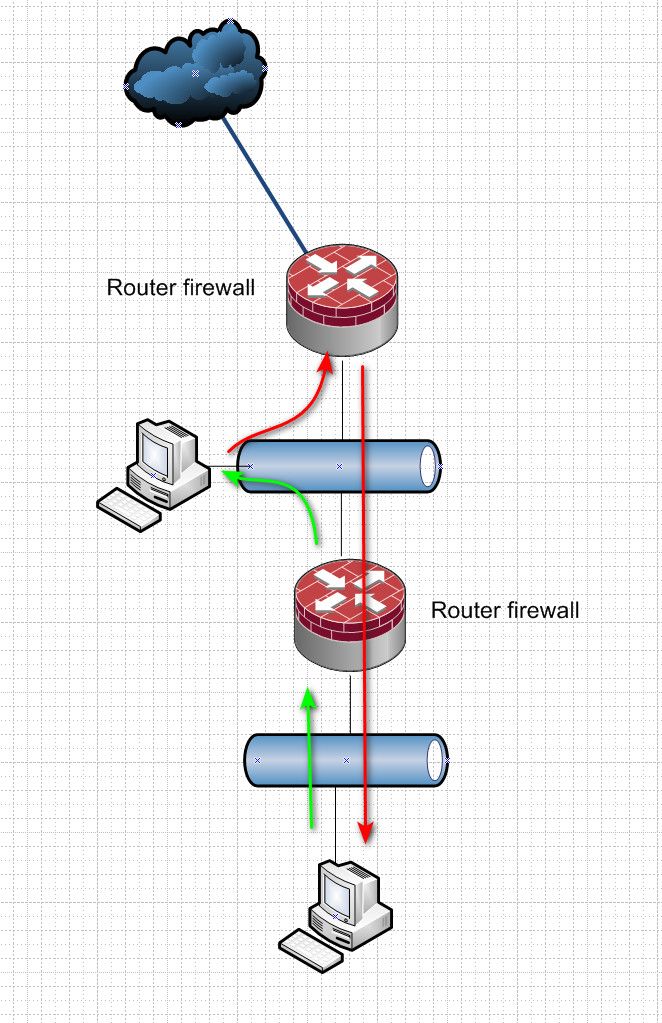
If your going to have hosts on your transit that will talk to this downstream network you either need to nat at the downstream router, or you need to create routes on the device in the transit. Or you have asymmetrical flow, this can be horrible for stateful firewalls and can just lead to bad connectivity as well.
-
Thank you very much for your informative message @johnpoz
I think I did not give enough information in my initial message, so my sincere apologies.
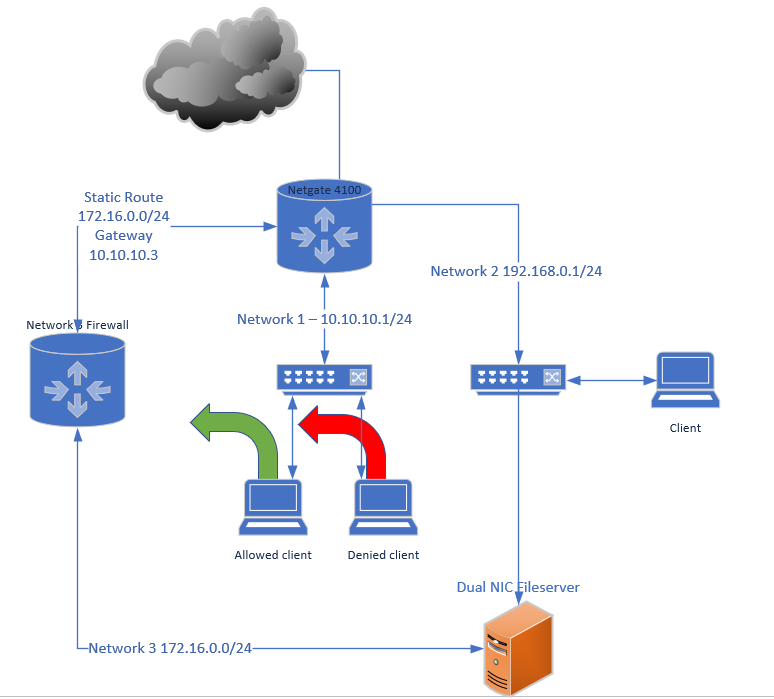
Would the below diagram also suffer from asymmetry issues you mentioned above?
If anything is not clear please let me know.
Appreciate your support once again :)
-
@ndub27 that drawing makes no sense at all.
Why would clients on this 10.10.10 not just route through your 4100 to get to the 192.168.0 network that shows your file server is attached.
But yes you have asymmetrical flow for sure. Lets say client talks to file server on 172.16.0.x address. Even if the server sends it back to the "firewall" vs sending it to pfsense on the 192.168.0..
And if does send it back via its default gateway 192.168.0.1?? Then its even worse..
If you want a downstream network 172.16.something this should be connected via a transit, not this 10.10.10 network that you have hosts on.
Why is the file server dual homed? That can be very problematic unless you specifically setup correct routing on the actual dual homed device - and it by its very nature of having legs in more than 1 network leads to quite often security holes.
-
@johnpoz Thank you kindly for your assistance, I will have to do some thinking and I will report back when I have resolved the issue.