Outbound NAT - lose connectivity
-
@michmoor said in Outbound NAT - lose connectivity:
So i have a requirement to NAT connections when coming into my DMZ to a DMZ address. So if the DMZ network is 192.168.15.0/24 then I need to NAT to something in that range. So i created an alias of 192.168.15.200.
These statements are conflicting. The "DMZ address" is not anything in the DMZ range. It's the interface address of pfSense.
Why do you need to translate the source address at all?
I went into my outbound NAT policy and selectd the translation address of the alias. This breaks all connectivity. Cant ping or access resource in the DMZ from other vlans that are directly connected to the firewall.
That's expected.
If you translate the source address, the destination device will try to respond to this one. If the address is not assigned to the pfSense DMZ interface responses will never come back to the source device. -
@viragomann The statements arent conflicting. This is achievable on an ASA.
The requirement is that DMZ machines should only see local addresses in their subnet and not see anything outside.
Because the NAT is assigned to the firewall, the firewall should be able to do either a Gratuitous ARP or respond to an ARP message for that NAT within the vlan. -
@michmoor said in Outbound NAT - lose connectivity:
The requirement is that DMZ machines should only see local addresses in their subnet and not see anything outside.
Seeing the origin source IP on the destination device is desired in most cases. But I think, you will have good reasons for masquerading the packets.
Because the NAT is assigned to the firewall, the firewall should be able to do either a Gratuitous ARP or respond to an ARP message for that NAT within the vlan.
If the IP is assigned to the pfSense DMZ interface this should work though.
However, I'm wondering, why you state an alias then. In this case you can select the address directly from the translation address drop-down.So possibly you did something wrong. But without getting more details I cannot verify.
-
@viragomann The documentation states to use an Alias
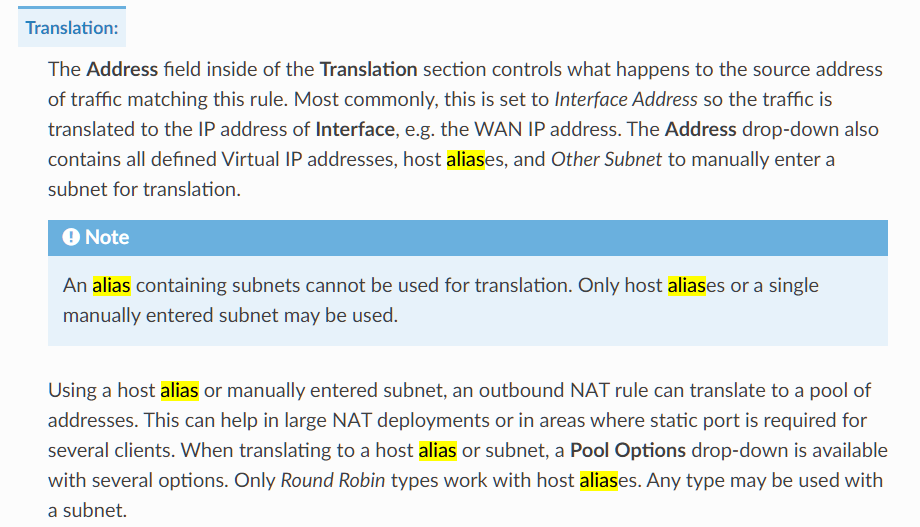
I should be able to pick any free IP in the range and use it but so far what works is using the Interface IP on the firewall.
-
@michmoor said in Outbound NAT - lose connectivity:
so far what works is using the Interface IP on the firewall
pfSense has to have the address, to receive the reply packets. Just like using NAT on WAN, the Internet replies to the WAN IP and pfSense translates that to the LAN IP.
Did you try adding your custom IP to the interface as a virtual IP?
-
@michmoor said in Outbound NAT - lose connectivity:
The documentation states to use an Alias
As mentioned here three times already, the translation address has to be assigned to the pfSense interface, either its's the primary interface address or a virtual IP.
You can state an alias though, but this condition has to be matched anyway.
Any IP assigned to pfSense interfaces can be selected from the drop-down. That's why I'm wondering that you were stating an alias there.You can also translate the source to any other address, but doing so, this IP has to be routed to pfSense on the destination device, which might not be the case in your network, I guess.
-
We do this all the time. It works.
You should post a screen shot of your Outbound NAT configuration. And the VIP configuration.
If this is just one address you should try it using the address instead of the Alias to eliminate any potential limitations there. With a VIP defined you should be able to select the VIP there and avoid using the alias entirely.
ETA (jinx)
-
You just need to add the IP as an IPAlias VIP on the DMZ and it will work fine.
As mentioned you can translate outbound to anything you like but without that, in this situation, the replies will fail.
Steve
-
I am with viragomann, I still don't get why a VIP should be uses if the IP is a private one, just use pfSense IP-address on that interface for NATing.
So probably I missed the usecase here. -
@bob-dig You certainly can do that.
-
Sure you can do that and it will work out of the box. But if you translate to a different IP you can see that on the destination so you could use it to identify traffic, for example.
-
@stephenw10 Creating an IP Alias was the ticket. Thanks everyone.
-
@stephenw10 said in Outbound NAT - lose connectivity:
Sure you can do that and it will work out of the box. But if you translate to a different IP you can see that on the destination so you could use it to identify traffic, for example.
This is pretty much one of two reasons why this was needed here.
-
@derelict Thanks for your help. I was using an Alias but NOT the IP Alias which is what was needed here. Thank you for your help here.