Access device via openvpn through ipsec tunnel
-
@nick-loenders said in Access device via openvpn through ipsec tunnel:
FW2's local LAN is 10.0.2.0/24
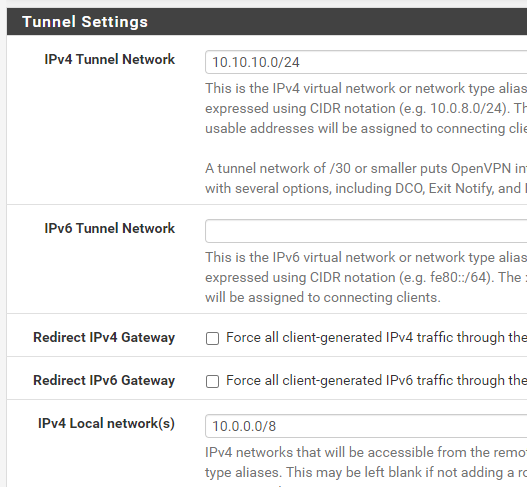
You need to add this network to the "Local networks" in the OpenVPN server settings to push the route to the client.
Further in IPSec you have to add an additional phase 2 tunnel to connect the site 2 LAN with the OpenVPN tunnel network.
So on FW1 set
Local network: 10.10.10.0/24
remote network: 10.0.2.0/24
and on FW2 the other way round. -
In openpvn server, I have the settings like that.
In the ipsec, I have to have two P2's then ? 1 with local subnet LAN and one local subnet the 10.10.10 ?
-
@nick-loenders
Yes. You need the second p2 also on FW2 to establish the tunnel. -
So on FW1:
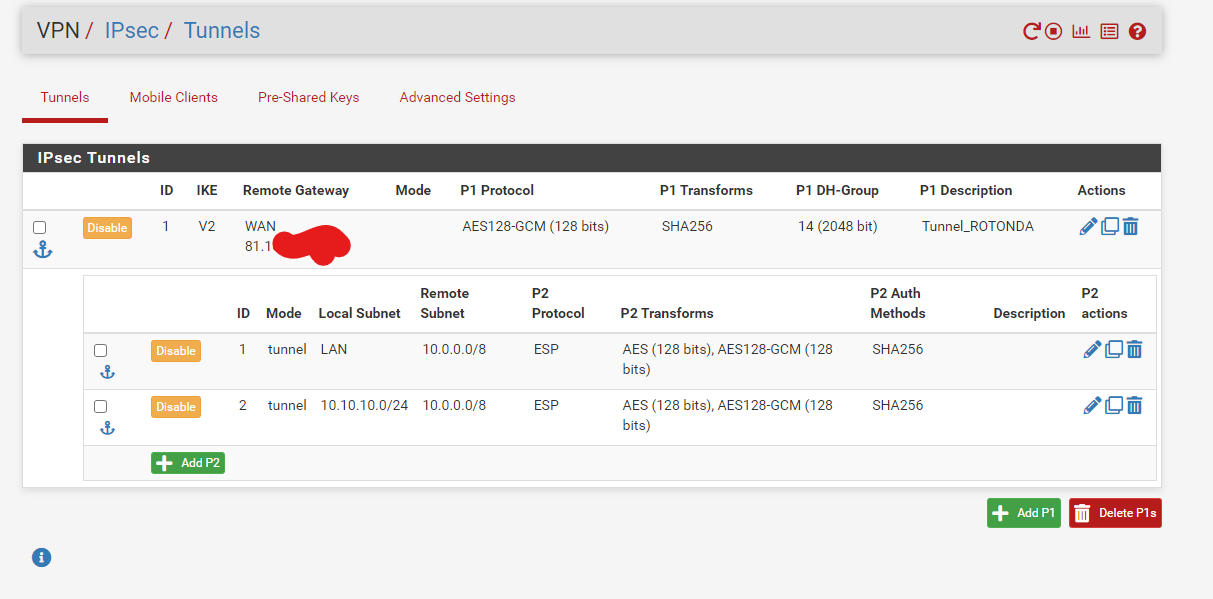
On FW2:
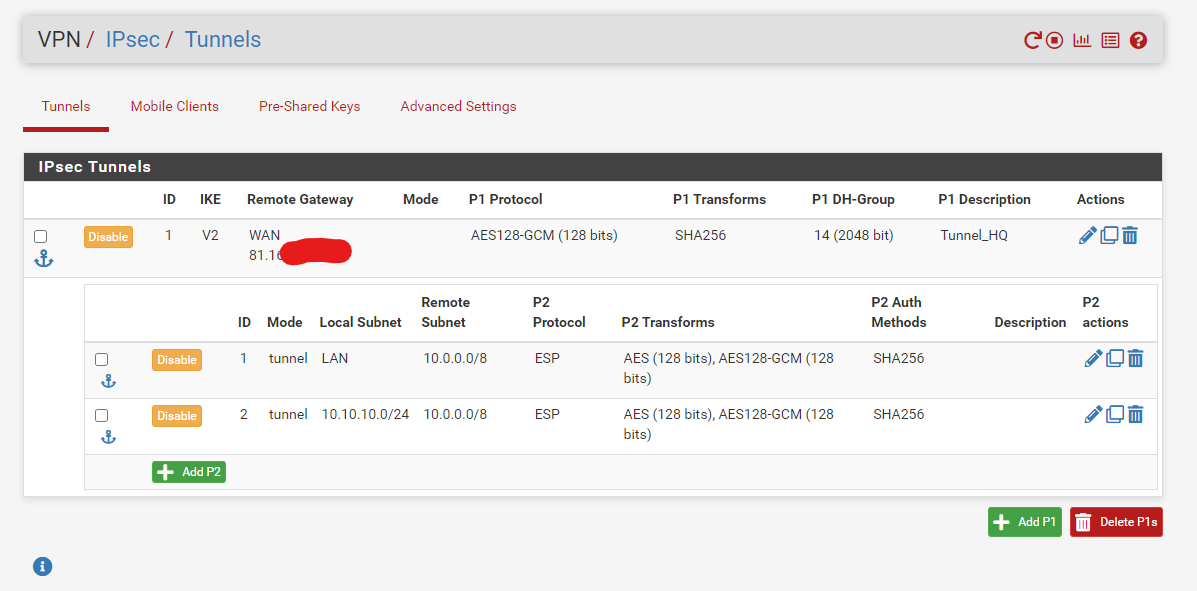
And in the openvpn on FW1:
I get a request timed out when I try to ping the device on site 1, allthough the firewall says it is ok:
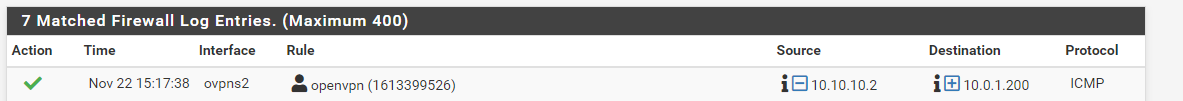
Also for the ping to the device on site 2 :

But I cannot ping it, or visit the webpage?? :(
Strangest thing is, before I could ping/access the device on site 1 ?
-
@nick-loenders
Why did you state 10.0.0.0/8 in your p2 for the remote site? And that on both sites.
That cannot work since the networks are overlapping.Configure the phase 2 with the correct networks.
-
So, on site 1:
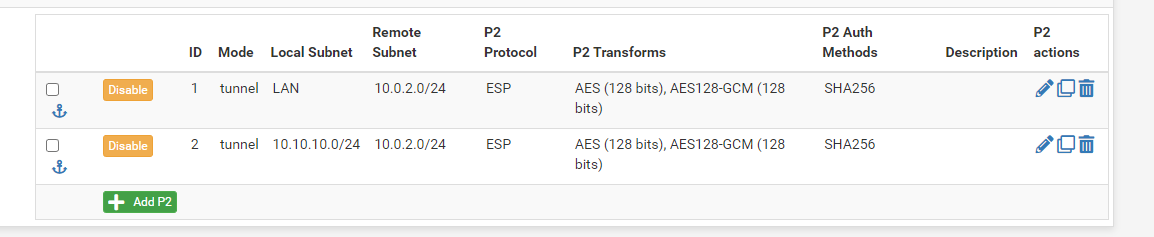
On site 2:
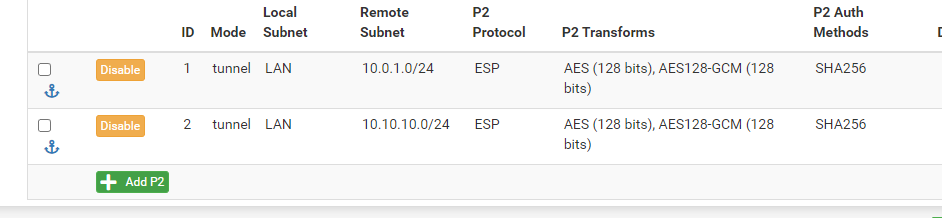
What if I have 8 sites? I cannot never do 10.0.0.0/8 on site 1 ?
-
@nick-loenders said in Access device via openvpn through ipsec tunnel:
I cannot never do 10.0.0.0/8 on site 1 ?
You can, but not if it's overlapping the local networks on the other site.
10.0.1.0/24 and 10.0.2.0/24 are both parts of 10.0.0.0/8. So if you state this in the p2 pfSense cannot route.
-
First to let you know it worked, for the 2 sites.
But for more sites, I need to do this then on site1: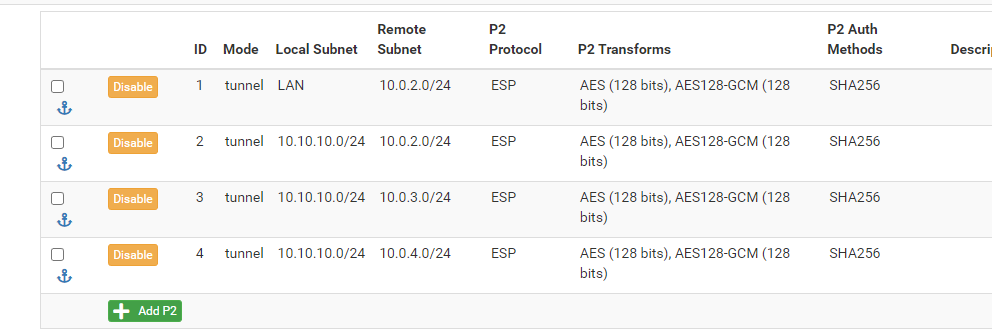
-
@viragomann
Nevermind the previous post... this is to another public ip, so is another P1 off course -
@nick-loenders
Anyway, if you have sequenced subnets like these you can embrace them in the p2 using an appropriate mask. But with a local LAN of 10.0.1.0/24 you run into risk of overlapping.So if the LAN here is 10.0.1.0/24 you could only merge tunnel 2 and 3 by stating 10.0.2.0/23 as the remote network.
If you have control over all involved site you should consider this when designing the networks.