HA - NO ENOUGH WAN IP Addresses
-
@amoschb said in HA - NO ENOUGH WAN IP Addresses:
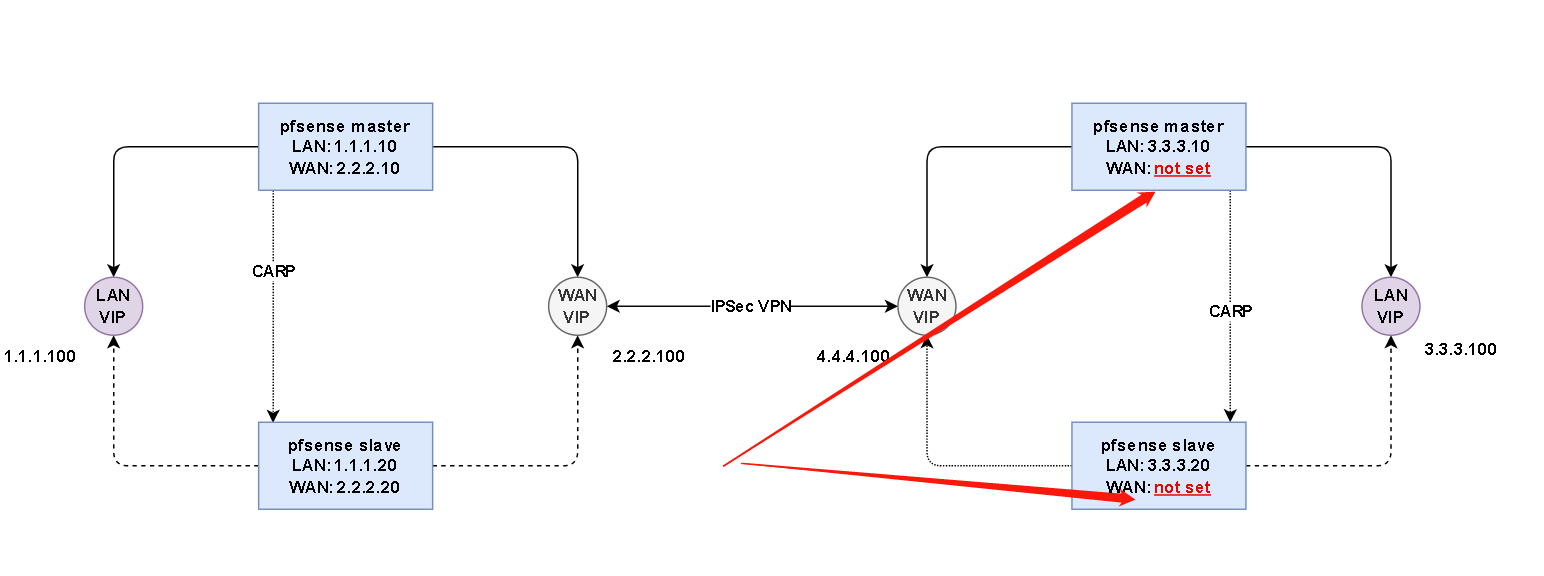
We didn't have enough WAN IP addresses on remote part of IPSec VPN, but still need to create a HA environment;
What do you mean?
You can add additional addresses if needed. -
Thanks for reply!
we only have 1 WAN IP address from ISP.
But from pfsense document, it shows that at least 3 available WAN IP address(1 for VIP, 1 for master node, 1 for slave node) are needed.
So the question is: if only 1 available WAN IP, can we build a HA pfsense?
-
@amoschb
You can assign private IP addresses to the WANs and hook up the public WAN IP as CARP VIP.However, this has limitations though, as only one device can actually use the WAN VIP. Hence without further configuration the backup node will not be able to access the internet, which is needed to install updates or packages for instance.
But you can circumvent this by routing out upstream traffic through the master. -
Thanks for reply, for this implementation ( WAN interfaces are configured with LAN IP, 1 WAN IP is configured as CARP VIP) , I think it's not necessary to configure each pfsense with 2 network adapters ( one is for WAN, the other is for LAN), am I right?
-
@amoschb
What? According to your drawing above, both boxes have to interface. And you're well done if you keep it this way to cleanly separate both networks.On the WAN interfaces assign another private network like 10.85.65.1/30 on the master and 10.85.65.2/30 on the secondary node.
There is no need to state a gateway.Then go to Firewall > Virtual IPs and assign the public IP as CARP to the WAN interface.
Go to System > Routing > Gateway and define the upstream gateway on WAN.
-
@viragomann Gotcha, let me try.
-
@amoschb How did it go?
I am also researching a similar solution:
at a customer we currently have a VDSL-modem in bridged mode, so the pfsense gets the official IPv4-IP set statically. Now the wish is there to set up a HA-cluster: I assume it would be better to have something like 3 official IPs for cluster and the 2 nodes? A /29 subnet?We can access the modem, and play with the settings, but I don't yet understand what to set. If I assign the 1 official IP to the modem WAN-side, there would be NAT involved, right? Bad, because we run websites on pfsense using HAproxy etc, I don't see how that would work with any NAT on the modem.
Hints welcome.
-
@sgw The ISP router could be configured to send traffic to a DMZ IP address which is the shared IP.
Also what ISP? Around here, Comcast/Xfinity routers in bridge mode also allow their default 10.1.10.x NAT subnet to work so the pfSense routers could have a shared public IP and their own private WAN IPs.
-
The ISP is NeckarCom, I am afraid you won't know them ;-) (?)
My customer already asked there for a /29, but that seems to lead to a rather expensive business account. We'll see.
Unfortunately there isn't much choice available in that particular place.Could you explain that DMZ-forwarding idea a bit more?
That should be the modem in place: modem
The idea above with the official IP as CARP-WAN-IP and the 2 WAN-IPs set to some "non-routed" RFC1918 adresses should also work. Although I still have to look up how to route the traffic from the standby node to the primary node (I think I did that somewhere years ago ...).
-
@sgw said in HA - NO ENOUGH WAN IP Addresses:
at a customer we currently have a VDSL-modem in bridged mode, so the pfsense gets the official IPv4-IP set statically.
CARP only works with a static IP. The cannot be pulled from a DHCP or PPPoE.
I assume it would be better to have something like 3 official IPs for cluster and the 2 nodes? A /29 subnet?
Yes, that would be the desired conditions.
-
@sgw re: DMZ, if the ISP router has the public IP and is providing NAT, I would think it would work to assign IPs like so:
router1 WAN - 10.1.10.10
router2 WAN - 10.1.10.20
shared CARP WAN - 10.1.10.2Then in the ISP router set 10.1.10.2 as the DMZ/passthrough/whatever so all inbound traffic is forwarded to 10.1.10.2. Outbound is facilitated through NAT because all have the ISP router LAN IP 10.1.10.1 as their gateway.
What we did for the client of which I'm thinking is similar:
router1 WAN - 10.1.10.10
router2 WAN - 10.1.10.20
shared CARP WAN - public_IP
Comcast ISP router - bridge mode -
@steveits Ah, I see. That might be possible in that modem, I have seen LAN and WAN and NAT tabs. I currently wait for the customer and his results from the ISP. We then might give your suggested approach a trial-and-error-session ;-) thanks!
-
@amoschb said in HA - NO ENOUGH WAN IP Addresses:
So the question is: if only 1 available WAN IP, can we build a HA pfsense?
Yes but the backup won't be active until the primary fails. It is also not supported by TAC so if you have issues, purchase TAC support, and come to us and we see that config we won't touch anything related to a HA issue with it.
Sometimes you can get your ISP to give you a single static and let you have two DHCP addresses (for the WAN on the two HAs) and go that route.