Failing back to a VPN connection
-
@jrhjr said in Failing back to a VPN connection:
(and the skip rules when gateway is down setting)That is not the default but you seem to know and have planed accordingly.
-
@bob-dig By default my WAN interface's gateway is being selected as the "Automatic" Default Gateway and that results in clients using the WAN (not the VPN) to get out. If I change the Default Gateway in System/Routing/Gateways to NordVPN no clients can communicate out at all. At least not at first (or second) glance. It doesn't seem like there's any sort of blocking firewall rule but I am not having any luck so far.
-
@jrhjr I meant if you create a rule to use nord (policy based routing) and that is offline, it would switch to WAN by default.
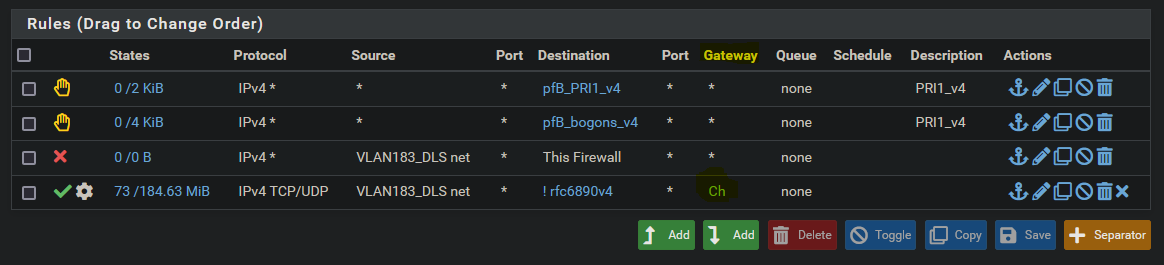
Btw you should in general select WAN as the default gateway, not automatic.
-
@bob-dig So this appears to be a bug in 2.6 (introduced in 2.5). There's a good discussion of it at the link below.
https://redmine.pfsense.org/issues/11570
Also - I backed up my config and restored it to the latest 2.7 build (pfSense-CE-2.7.0-DEVELOPMENT-amd64-20221121-0600.iso) and it worked like a champ - it fails over and back in less than 30 seconds which is very acceptable. The whole process of testing it took less time than writing this response - sheesh!
@bob-dig you did help me realize that if you specify a gateway in a FW rule (in my case a VPN) and the gateway goes down - it doesn't mean the rule isn't matched but rather that it just fails to the WAN - which is my desired behavior. I think I sort of was aware of this but I was so bogged down in the failback bug that I never bothered to digest it. It makes the config oh-so-simple which is my preference.
As for my pfSense journey - I don't know what comes of it. I hate to downgrade to 2.4 - especially on a router/firewall. I might just wait until 2.7 is released which seems like probably it'll be soon - a couple months ... Or I might just run on this development version - something I don't like doing. I know opnSense is an option but that seemed way buggier than pfSense - it had my head spinning. In any case I'm glad to have figured this out - I've been pulling the few remaining hairs out of my head for over a week now on this issue.
Incidentally the absolute killer feature I have to have that makes me want pfSense is the ability to use FQDN names in Firewall aliases ... That pfSense periodically resolves the names to IPs it then uses in FW rules is killer. This is helpful for sites like Spectrum TV which don't like VPNs ... It's relatively easy to determine the DNS names they're hitting - but an absolute nightmare to keep up with the IPs behind the names. This feature makes it a dream!
-
@jrhjr You can get the plus version of pfSense for free for home use. Just "buy" it on their website, it should be bug free.
-
@bob-dig I didn't know this, thank you. I'll probably go down this path then. Thanks again!
-
@bob-dig I'd still use gateway groups and have 3 NordVPN connections set up incase there is an issue with any one the VPN endpoints.
-
@nogbadthebad said in Failing back to a VPN connection:
I'd still use gateway groups and have 3 NordVPN connections set up incase there is an issue with any one the VPN endpoints.
Same here with my VPN-Provider.
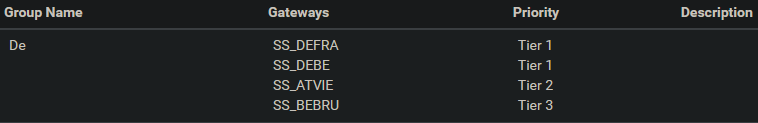
It is almost unusable without it, sadly.
-
@bob-dig Welp - unfortunately pfSense Plus 22.05 does not include the fix - it looks like it might not include it until 23.05 based on the comments. :( Oh well, the development versions do have the fix and upgrading to pfPlus helped me understand that using the development versions could be easier than I thought - just upgrade via the GUI.
-
@jrhjr No problem here, also I don't unplug my WAN cable...
Anyway, one other thing you can try is not failing back to WAN but to another VPN-Client. As far as I have understand you, it is not WAN failing but a VPN-Client. We, in this thread, do use Gateway Groups for VPN-Clients and it is working for us.
And btw. not every redmine ticket/issue is affecting everyone.