Replacing old router with a new instance of pfsense + BGP protocol to configure a dual link to the ISP
-
We did a hangout on configuring FRR: https://youtu.be/4IlKcB17rWk?t=2389
We also have the docs here: https://docs.netgate.com/pfsense/en/latest/packages/frr/bgp/example.html
It's really quite specific to your setup though. How is the current router setup? What is your ISP telling you to configure?
Steve
-
Wow! Thanks, the hangout is very interesting, thank you.
Also the official netgate docs are so useful.My ISP gave me one IP address on a /30 subnet for the point to point link with the upstream gateway and a range of public IPs on a /25 subnet.
The IPS provided also the ASN for the BGP configuration.I already simulated the future scenario in GNS3 and it works, but before going in the "real world" I would like to know if, in order to configure pfSense as a simple router with BGP, I should activate (or deactivate) some particular pfSense feature.
I read that, to reach my target configuration, I should do something like that:
https://blog.matrixpost.net/convert-pfsense-into-a-routing-only-platform/
(adding some other changes for the BGP).
In you opinion, is it really the right procedure to run pfSense as a router only?
I'm doing this kind of question because it is not an official netgate page.Thank you in advance.
Have a great day,
Mauro -
You would want to disable outbound NAT for that /25 subnet on the WAN since it's a public subnet.
You probably don't want to disable pf entirely because that disables the firewall and you would still want to be able to filter traffic.
Steve
-
-
Hello Steve,
I was able to do the work mentioned above in a real scenario.
Outbound NAT has been disabled.In this pfsense/router instance I have 4 interfaces:
WAN1 (/30 primary link to ISP)
WAN2 (/30 backup link to ISP)
PUBLIC (/25 public subnet behind the router
LAN (for the management of the pfsense instance itself).Do you think that I should enable the NAT only for the LAN?
And if yes, how can I do it?Thank you,
Mauro -
Yes, you will need outbound NAT for the LAN.
You can do that do that either by setting outbound NAT in manual mode and only adding rules for the LAN subnet via each WAN. And possibly localhost too.
Or by setting oubound NAT in hybrid mode and then adding do-not-NAT rules for the public subnet.You will probably want to setup both WANs in a gateway group and use that to provide failover or load-balancing for connections from LAN.
Steve
-
Hello Steve,
a short description of the current pfsense router configuration running in GNS3:
- WAN1 (192.168.1.2/30 primary link to ISP)
- WAN2 (192.168.2.2/30 backup link to ISP)
- PUBLIC (192.168.99.1/25 public subnet behind the router)
- LAN (for the management of the pfsense instance itself). 192.168.10.1/24
I decided to use HYBRID OUTBOUND NAT adding the do-not-NAT rules for the public subnet.
Could you please check if the NAT rules in the OUTBOUND NAT section are the right ones?
So, if everything is ok, LAN should be NATted and PUBLIC should not be NATted. Both the hosts on LAN subnet and the hosts on PUBLIC subnet are able to reach internet.
But how can I verify that NAT is actually disabled between PUBLIC and WAN1/WAN2 interface? Is there a way to do it using "packet capture" feature of GNS3?
The following lines have been added after reading carefully the official documentation
I think that I made a mistake in the previous configuration. I'm not sure, but I think that the INTERFACE field in the MAPPING section should be WAN1 and WAN2. Please correct me if I'm wrong again.

In this case, the hosts in the LAN subnet are still able to reach internet (thanks to the enabled NAT), but the hosts in the PUBLIC subnet are not.
What should I do to fix this problem?
Thank you in advance,
Mauro -
@mauro-tridici How do you map a NAT rule from WAN to LAN?
Its like everything is backwards....?
-
@cool_corona sorry, but I'm still a newbie, I'm at beginning. Could you please explain where is my error and the right solution to my problem?
Is It the first one I proposed (first screenshot) or the second one?
In addition, how can I check that NAT is working as expected ( maybe using the pf sense packet capture)?
Thank you.
-
@mauro-tridici No I an a newbie too in BGP but I dont get the NAT in regards to the public /25 that imho is the one that gets routed from WAN to LAN
-
@cool_corona ok, so let's see what @stephenw10 will say about that

-
No, the 'do-not-nat' rules should be on WAN1 and WAN2 for the PUBLIC subnet. You do not want to NAT traffic from PUBLIC as it leaves WAN1 or WAN2.
You can confirm that by runnig a pcap on WAN1 or WAN2 and you should see traffic from the PUBLIC subnet there.
I assume that you are using 192.168.99.0/24 just as an example here? The real subnet is actually public?
Steve
-
@stephenw10 thank you Steve, you helped me again :)
Yes 192.168.99.0/24 is just an example and the real subnet is a public subnet.Setting outbound NAT as in the second screenshot I was able to make it working.
Before it didn't work because I forgot to route the traffic from the ISP router to the public customer subnet (192.168.99.0/24).After adding, on each ISP upstream gateway, the following routes everything started working as expected:
on primary ISP upstream gateway
ip route 192.168.99.0 255.255.255.0 192.168.1.2on backup ISP upstream gateway
ip route 192.168.99.0 255.255.255.0 192.168.2.2This is the final GNS3 schema
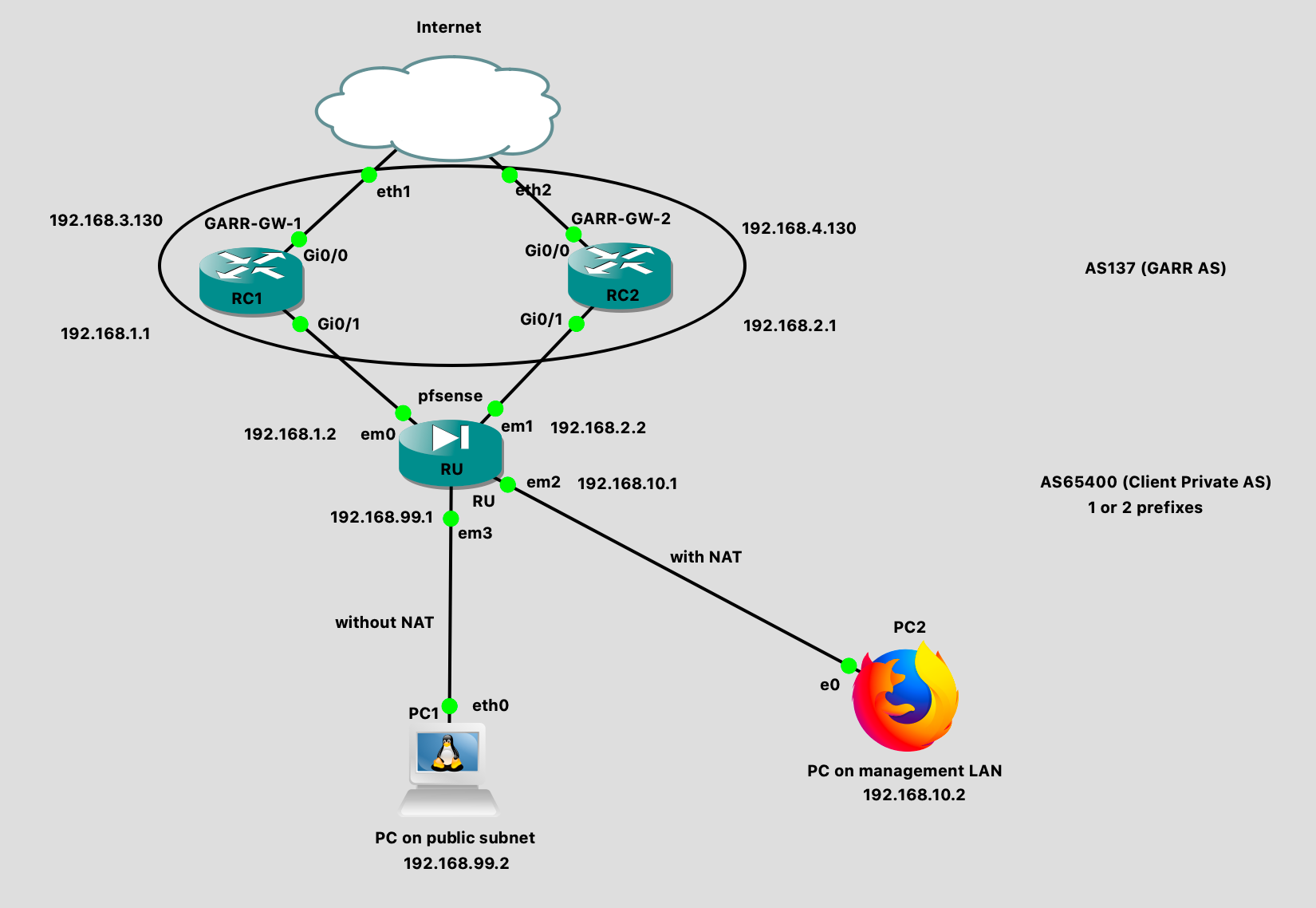
-
Public is internet.... pc is on LAN.
The /25 IP's are on WAN and not LAN. Unless you run a hotspot or internetcafe.
Otherwise I dont get the setup...
-
In my particular case, pfsense is acting as a "customer border router".
It is connected to the WAN (ISP AS) using em0 and em1 ports with two redundant PTP links.
Watching the schema, 192.168.1.2/30 and 192.168.2.2/30 are the IPs for the PTP links.ISP is routing the public subnet (192.168.99.0/24) to the pfsense router.
For this reason I need to disable NAT on pfsense.In the real scenario, the "PC on public subnet" will be replaced by a physical firewall. So, at the end, you will see something like that:
ISP RC1 + ISP RC2 <-> PFSENSE ROUTER <-> FIREWALL <-> LANs
-
@mauro-tridici Cant pfsense act as both router and firewall for the clients?
-
@cool_corona Sure, it can. But in our case, we prefer this kind of deployment.
-
Yes, I would expect that to work.
-
P Patch referenced this topic on
-
P Patch referenced this topic on