Multiple IPsec servers?
-
We have a setup in our data center where an IPsec VPN exists for one purpose/network. We have a request for a separate VPN to access a second network, which will be a separate subnet. If we configured that second network as an alias on LAN, is it possible to have two IPsec connections where the person/site connecting in has access to one network or the other but not both? I am having trouble finding that scenario online.
In other words, if Person1 logs in they get network1, and if Person2 logs in they get network2.
To add another layer, they would also like a site to site connection as well as PC to site.
Thanks,
-
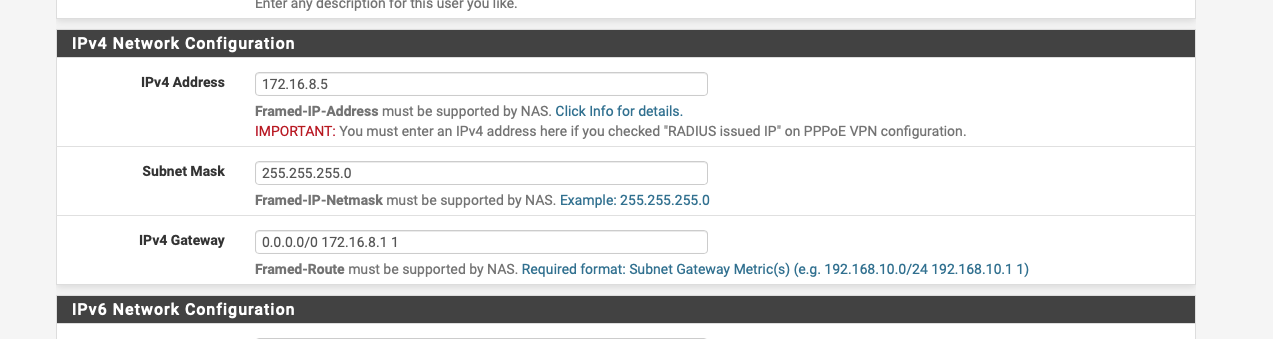
@steveits Maybe look at FreeRadius auth with framed-ip and firewall rules to allow / block access to specific subnets.
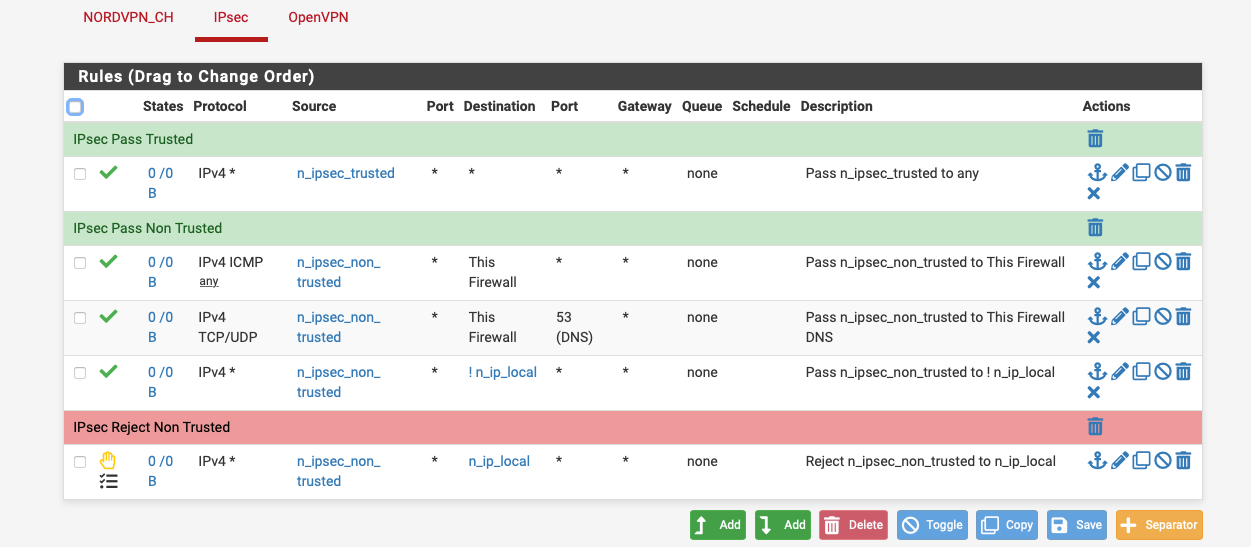
Also you can do a site to site connection.
-
@nogbadthebad OK I think I wrapped my head around that, though each person connecting would have to have a specific IP. So I'm correct that it isn't built in, but would depend on FreeRADIUS assigning the IP. Thanks.
-
https://forum.netgate.com/topic/115795/guide-ikev2-ipsec-per-user-firewall-rule-settings-with-freeradius
-
@nogbadthebad Ah, thanks. That uses static routes, I'm guessing because the IPs assigned aren't in the IPsec config? Same idea but doing it by network rather than individual IPs.
I had also found a video about how to set up FreeRADIUS and OpenVPN with rules.
-
@steveits said in Multiple IPsec servers?:
if Person1 logs in they get network1, and if Person2 logs in they get network2
I got this set up with freeRADIUS. The IP is assigned to the remote PC, and "Virtual Address Pool" is unchecked.
I set up a second phase 2, just like the first but with a different local subnet. Notably that local subnet does not yet exist on the router. It doesn't show on the remote PC (via "route print", Windows)...is that because it isn't handed out if it doesn't exist on the router? I can add it but will need to do so after hours.
To be complete, it seems to me each client (of which there is 1 right now, driving this) would need their own subnet. Then we can create rules to block access to other client subnets.
-
I had to let it percolate a bit to remember that way back when this was set up the PowerShell script adds a route for the subnet:
Add-VpnConnectionRoute -ConnectionName "name" -DestinationPrefix 10.2.2.0/24IPsec tab FW blocks from source IP to each subnet work great.
Thanks,
-
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on
-
 K keyser referenced this topic on
K keyser referenced this topic on
-
 K keyser referenced this topic on
K keyser referenced this topic on