2 weeks still nothing.
-
@pfsensenewbie1 said in 2 weeks still nothing.:
I then bridged the connections and
That's the point where the OMG exclamation enters.
Easy life saver : Do not bridge. Even if think you need bringing : stay away from it.
Or do the easy bridge : replace pfSense for a dumb switch, and connect one or more APs to it.Btw : a router has two interfaces. Otherwise it isn't a router.
The easy way would be : two physical wired NICs. That's the reason why we all slam these into our pfSense boxes.
Or even better, why we use these devices.Your trick of creating a VLAN right after install was the way to do it.
Most often, these devices do not contain any Wifi functionality, as FreeBSD supports only a (very) limited set of Wifi adapters.
I know, our ISP have made effort to integrate a wifi nic, a switch, some VOIP and a subscriber line interface (fiber, phone, ADSL, Cable, whatever) into one "box". Very nice for a typical home solution. But it doesn't do all the extra goodies pfSense offers.IMHO, the most known network install is :
A ISP router (modem) upfront.
This is what I do. I've shut down the phone capabilities (our company already has 6 ISDN lines),
I've shut down the 'TV' capabilities.
I've shut down the wifi of the box.
I've shut down the IPv6 capabilities as my ISP only offers a /64, worthless for a company.After the ISP router : pfSense, with a WAN and one or more LAN's.
For me :
A LAN with my trusted devices. This LAN contains some APs for my trusted BJOD (that is : my own Phone, and some wireless credit card terminals etc)
Another LAN for my non trusted devices : clients that walk in and want to use our wifi.
pfSense also handles my IPv6 needs.This network is easy to maintain and pretty straight forward.
Stay away from complicated stuff, make your network simple. This way, when something goes wrong, you can re create your network in a couple of minutes to get basic Internet up again.
-
Ok I seem to have made it harder by trying anything I could to make it work.
I was reading tutorials in the beginning and each said use a bridge between interfaces and set a single Nat rule - that clearly isn’t the case.
I’ll be removing the bridge - I did think it was required for the 2.1 to 1.1 connection 192.168.2.x -> 192.168.1.x.
Next I assume trace route is the best way to detect if the dns is being routed correctly? I have been clearing cache to eliminate possible issues. If so my traceroute currently shows gateway first then asterisks for next 2 hops then Internet address space ip’s.
If the bridge removal doesn’t fix things I’ll bite the bullet and reinstall from the beginning. I will also record it to make sure I didn’t miss a step or do anything wrong. I’m glad my vlan trick was the way to go.
Someone asked why my setup, well it seemed correct for the way it was as I’m adding onto an existing network and reason for not using pfsense for all wireless clients is exactly because of what was mentioned, that Wifi support is poor in bsd. I just bought a cheap mini pc for pfsense routing as this was cheapest way to get what I need and have further expandability in the future (like moving the dns server to it etc). As for connecting the dns to the pfsense - unfortunatly the dns server is on a pi atm which has no wireless so cannot connect directly to pfsense. Not ideal but it works. My modem/router only has 4 Ethernet ports but very good wireless and as it is also the modem it made a good choice for the gateway.
Again thank you for the replies, I will update if there’s any news.
-
@pfsensenewbie1 said in 2 weeks still nothing.:
Next I assume trace route is the best way to detect if the dns is being routed correctly?
Huh??? Where would you have gotten that idea from?
Traceroute has to do with the network path your taking - that has zero to do with who you ask for what is the ip of www.netgate.com
So in the big picture - you want to expand your wifi, and you thought pfsense was the best solution? Seems a 20$ old wifi router used as an AP would be a much better fit for what your trying to do.
The only thing dns has to do with a traceroute - is if in the traceroute your wanting to resolve the PTRs of the IPs along your path.. Or if you use a fqdn as to where your tracing too vs an IP.
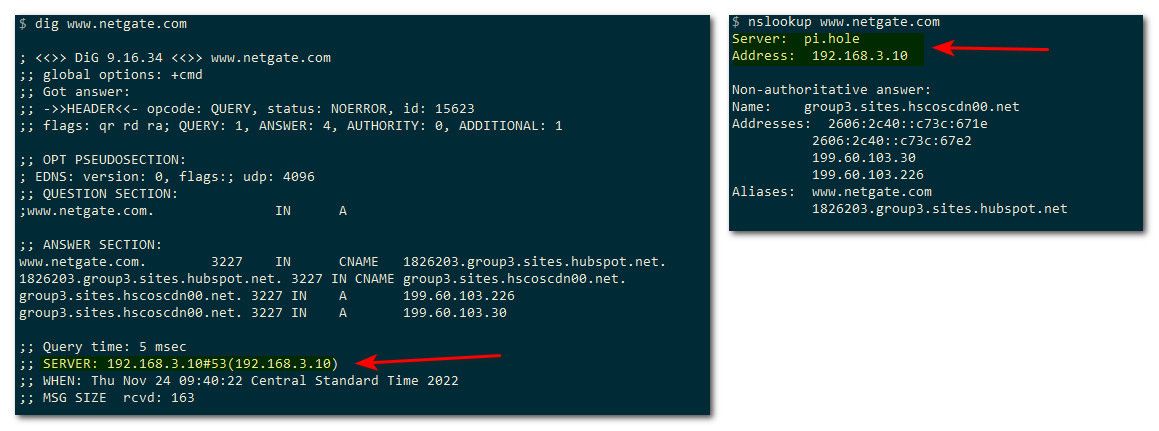
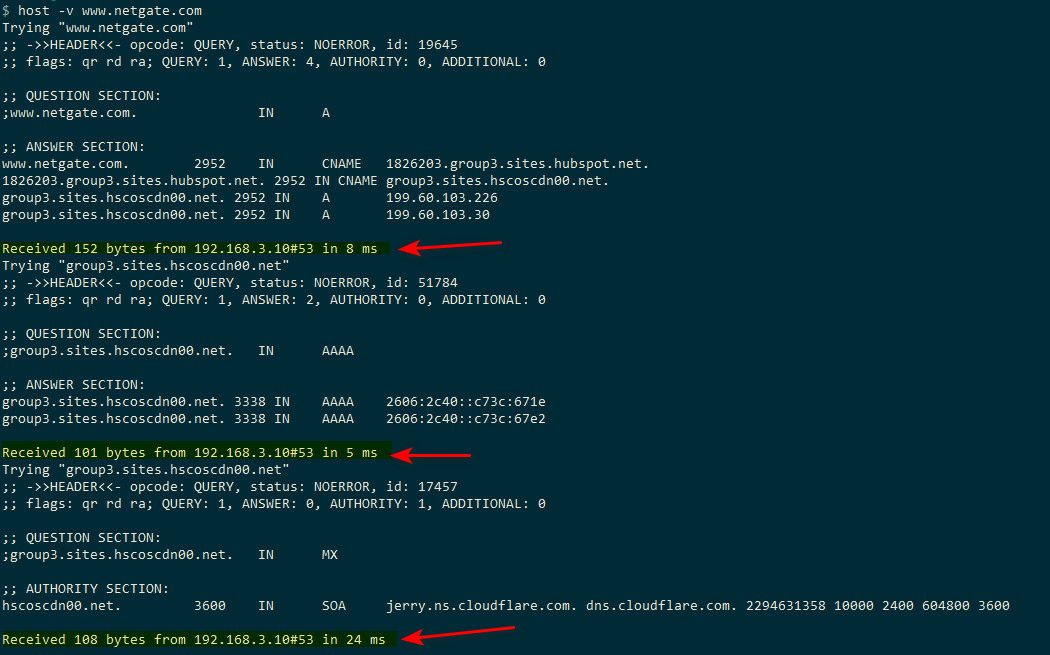
user@NewUC:~$ traceroute www.netgate.com traceroute to group3.sites.hscoscdn00.net (199.60.103.30), 64 hops max 1 192.168.2.253 0.596ms 0.186ms 0.200ms 2 69.47.60.1 20.122ms 19.230ms 9.810ms 3 216.80.79.9 13.406ms 12.512ms 15.430ms 4 207.172.18.116 31.214ms 15.457ms 16.177ms 5 207.172.19.255 14.927ms 18.085ms 13.353ms 6 208.115.136.180 19.068ms 16.339ms 22.470ms 7 172.70.176.2 16.507ms 18.613ms 12.932ms 8 199.60.103.30 21.435ms 17.625ms 21.402ms user@NewUC:~$ traceroute www.netgate.com --resolve-hostnames traceroute to group3.sites.hscoscdn00.net (199.60.103.226), 64 hops max 1 192.168.2.253 (sg4860.wlan.local.lan) 0.730ms 0.227ms 0.236ms 2 69.47.60.1 (d47-69-1-60.col.wideopenwest.com) 14.747ms 9.375ms 12.144ms 3 216.80.79.9 (static.rcn.com) 14.484ms 11.982ms 28.447ms 4 207.172.18.48 (hge0-0-0-14.core2.chgo.il.rcn.net) 13.457ms 17.367ms 11.223ms 5 207.172.19.141 (hge0-0-0-3.border2.eqnx.il.rcn.net) 21.958ms 19.420ms 16.802ms 6 208.115.136.180 (13335.chi.equinix.com) 13.663ms 14.947ms 13.875ms 7 172.70.128.2 (172.70.128.2) 21.985ms 23.804ms 14.090ms 8 199.60.103.226 (199.60.103.226) 20.734ms 16.899ms 11.529ms user@NewUC:~$See in the 2nd one it comes back with names for some of the IPs along the path..
To see what your using for dns, nslookup or dig or host - whatever your fav dns tool is.
-
@johnpoz I presumed that traceroute would show the full path that packets would take and should have taken into account dns. Clearly I don’t know enough about networks, but while your help is useful and I’m appreciative of, the attitude is not. I ask you please tone down your critical responses, to just be information, Im having a hard enough time getting this to work as it is. I’m here to learn and clearly I have a lot still to learn. I’ll give those tools a look when I’m at home. Do any of them exist in pfsense interface?
-
@pfsensenewbie1 said in 2 weeks still nothing.:
packets would take and should have taken into account dns.
DNS is not in the "path".. has nothing to do with the "path" that your traffic takes from getting from A to B..
DNS is a phone book.. It has nothing to do with how traffic is routed from point A to B.
pfsense has all of them on it to use from the cmd line.. And traceroute, and a gui dns lookup and traceroute interface as well.
But if your looking to see the path that is taken from a device "behind" pfsense you would want to run the tool on that device - then pfsense would be in the path. If your wanting to see what device is using for dns - you would want to check again on the device. Maybe it defaults to googledns, or your dhcp is handing out something other than what you want it to hand out, etc.
Out of the box pfsense would hand out its own IP for dhcp clients behind it to use for their dns. It would then resolve vs forwarding. If you want all your clients to use your PI for dns - then you either need to tell them to use that directly, or have pfsense forward to it vs resolving. None of which would be in the actual path that traffic takes.
-
@pfsensenewbie1 There are such tools in the Diagnostics menu.
@johnpoz I think you’re confusing the normal use of DNS and OP is asking how the traffic routes to the internal DNS server.
Traceroute would help you see that yes. But, using the default setup it should work, just as if the wireless device tried to talk to 8.8.8.8 or some other DNS server. pfSense knows where your DNS server is (its WAN) so routes the packet there.
The downside to not bridging is the wireless devices aren’t in the same broadcast as the devices in your LAN (pfSense WAN) and while they can connect (e.g. by IP) they aren’t going to auto discover devices on another network.
I have not looked but I would almost expect there is software to make a PC into an access point…
-
@steveits said in 2 weeks still nothing.:
wireless devices aren’t in the same broadcast as the devices in your LAN (pfSense WAN)
If that is what he wants - pfsense is not what should be used here then. He should pickup an actual AP, or find some wifi router and use it as an access point.
Be like trying to use a corvette for delivering stuff - sure it can do that, but it has very little storage for the stuff your delivering. Gets horrible gas mileage, and insurance on it way more than some say delivery van ;)
Pfsense is a layer 3 firewall/router - while sure it can bridge, and sure it can even be wifi AP if you will. But if the goal adding wifi to some area, and you want those devices to be on the same L2 as your other device - it is not the correct choice.
-
@johnpoz thank you. I didn’t quite follow the analogy but from the discussion it sounds like I will need bridging. My original intent was to use the box to route all traffic, hence the reason for the expense. Now I know I can’t do that I just have to make it work until I have a better option. I kinda like the vette analogy.
if this software is like a corvette and is not suitable for the task, does that mean the software is specifically designed for larger networks where many advanced features would be used regularly? I honestly want to redo my network entirely and the pi is barely suitable for the dns server, so I was going to have it all on one box then forward all traffic and actually use the firewall features as well hence the box. If I didn’t need the modem/router for the wireless range it offers and obviously the modem features I would ditch it and use pfsense box for the lot with a switch for the wired connections. Unfortunately cash is short this time of year so buying anything is out of the question, I simply need to make this work or totally forget all about it.
With that said removing the bridge had no effect so I’m now going to dig into the tools to check dns forwarding etc.
-
@pfsensenewbie1 and in fact removing the bridge I now have no access to the firewall interface. I did last night now I don’t.
Both wan and lan are set to dhcp yet both are on the same subnet - how is this possible if they must be on separate subnets?
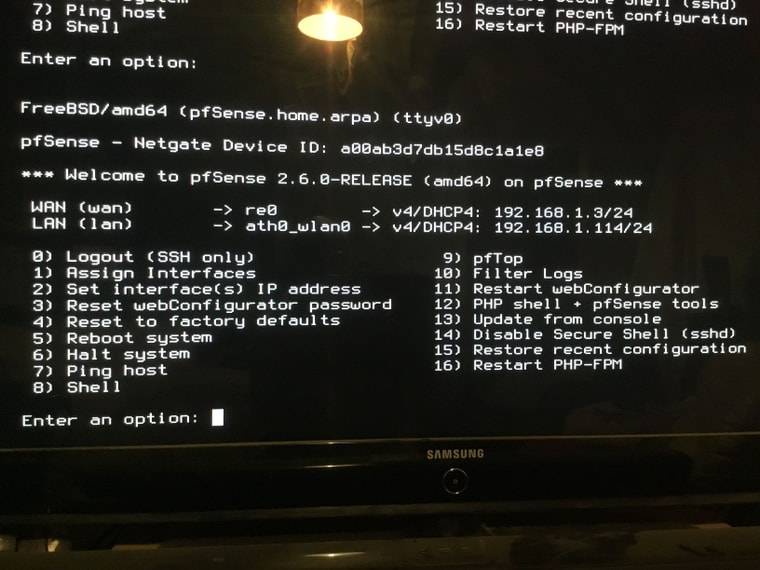
I’m going to reboot everything - when it fails I’m starting from scratch, I’m not putting much more effort into this especially as I can’t make it do what I need.
In case this is my last post I thank you for trying to help.
-
Ok I’m done. Totally lost access yet still got dhcp in the same subnet with no changes other than enabling dhcp and enabling Wifi. This is not supposed to happen so I’m taking your advice and trying something else.
-
Just catching up here...
This sort of setup should be quite simple as long as you have WAN and LAN in separate subnets.If you need the wifi clients to be in the same subnet as the WAN they must be bridged. However if you do that you can't apply layer3 forwarding rules to redircet DNS traffic. You would have to use layer2 rules, like the captive portal does, and there's no facility to do that in the pfSense GUI. Yet.
Steve
-
@A Former User said in 2 weeks still nothing.:
at least fairly proficient with networks.
Dunning-Kruger in action ;)
-
@A Former User said in 2 weeks still nothing.:
when it fails I’m starting from scratch, I’m not putting much more effort into this especially as I can’t make it do what I need
Just accept what is proposed by default.
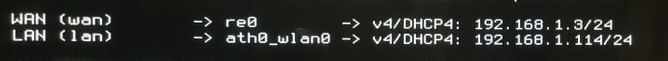
"Default" is : A DHCP client on the WAN interface.
This way, pfSense will grab an IP, actually a lease, from an upstream, probably ISP router, just like any other device already present on your ISP router network. This is a plug and play operation.The LAN interface has to be set to a static IP, like the default 192.168.1.1/24
And you have to think now.
if your WAN network is already using 192.168.1.1/24 (many ISP router do !) then you have to ** set your (static) LAN interface to, for example, 192.168.2.1/24 - it could be any network, but not 192.168.1.1/24
Adapt DHCP server settings for this LAN interface accordingly.See it like this : a router can not route between two identical networks.
** like this : your see a red light ? Stop the car. Don't ask why for now.
If you think this is what you need, please reconsider, ask advise, write down what you want. We'll help.
-
@gertjan As I said earlier, he doesn't have things connected correctly.
If I had to guess, I'd say the WAN and LAN are both connected to his ISP router. -
@jarhead he left.. Deleted his account..