IPsec VTI - no traffic received
-
@dehaas are your IPSec firewall rules set to permit all protocols?
-
@gabacho4 Hi gabacho,
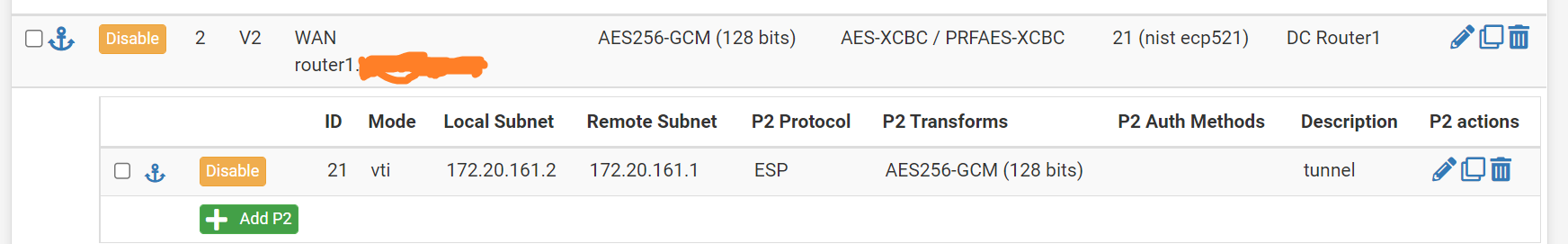
Please find the VPN configuration for the other side here:
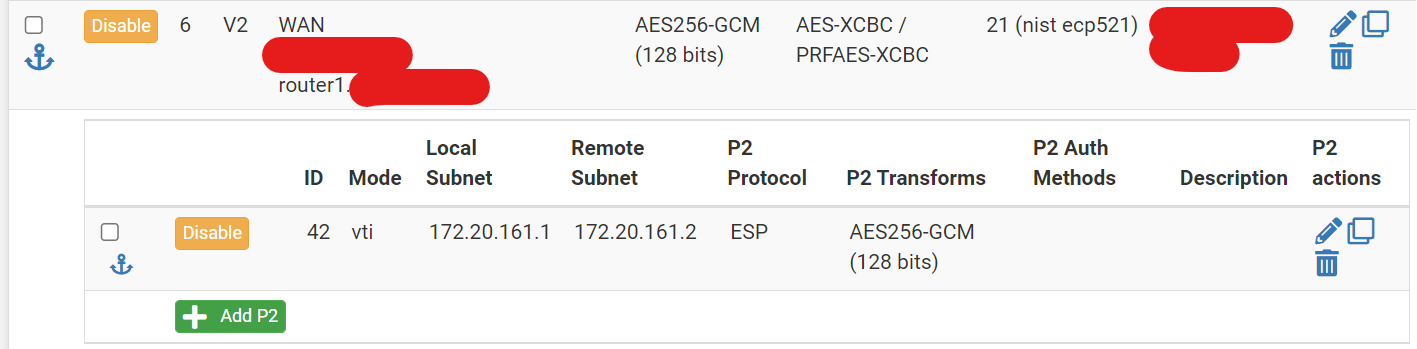
I have tried from computer to computer, but since routing information (ospf) is not arriving that does not work. I have tried with static routes instead, but same result. I have also tried router-router ping; nothing arrives.
On both ends, the IPsec Filter Mode is the default options filtering on the ipsec tab.
I have created interfaces and gateways for both ends.
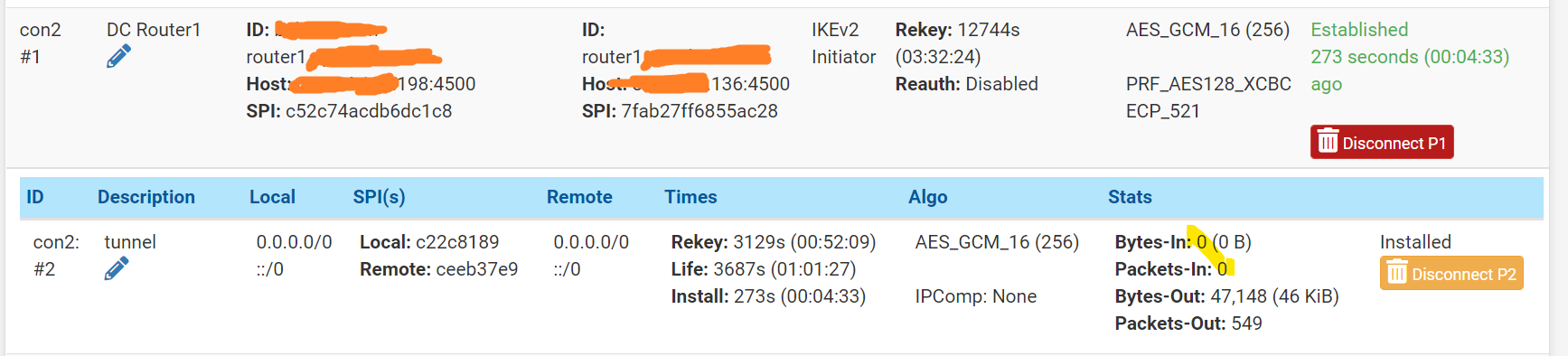
And yes, the current firewall rule is set to allow all protocols. I have also tried with a packet capture, which should show the traffic even if blocked by a firewall rule, but nothing is captured.
/ Christopher
-
@gabacho4 Sorry forgot to answer the NAT question. Neither firewall is behind NAT. They both have public addresses, with no other firewall in front.
/ Christopher
-
@dehaas try changing the filter mode to filter IPSec VTI or are you running traditional IPSec connections as well?
-
@gabacho4 I unfortunately cannot try that, as yes, I am running other traditional IPsec tunnels as well.
-
@dehaas rgr. I wonder if that might be complicating things for you. I’m stumped at this point but would probably try to redo the VTI configuration again for good measure. Your router firewall logs don’t show anything weird going on?
-
I’ve run VTI behind NAT on one end and used ospf to distribute routes so I know for certain you’re not asking it to do more than it can. There’s just gots be something in the config.
-
@gabacho4 I too am a bit stumbled and have tried re-creating the config on both sides out of desperation. Unfortunately, same result. I also do not see anything weird in the logs.
-
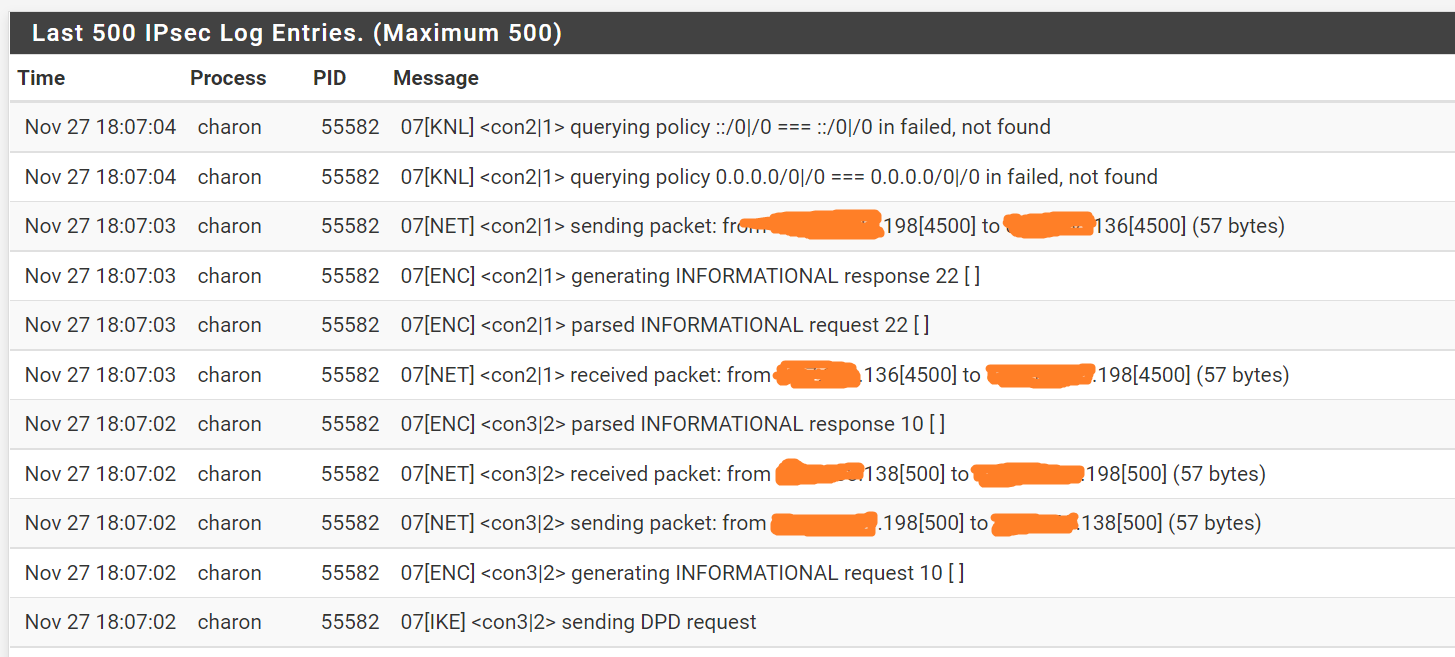
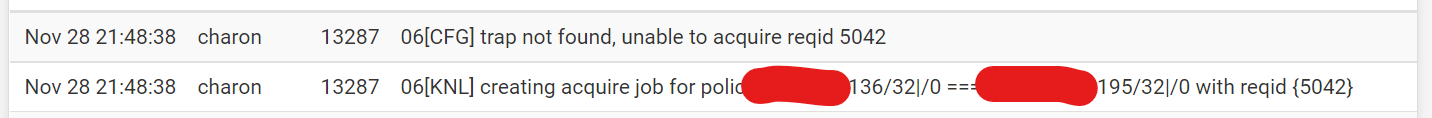
@gabacho4 I am seeing this message in the logs a lot. I guess it is related, but not sure how i relates to the configuration I have made.
-
@dehaas sorry for the delayed response. Had to go to bed for the night as it was 2330 were I live. So the one thing I can think of trying is to find time where you can have an outage. Then disable the policy ipsec connections and change that filter setting in the advanced settings. See if your VTI passes traffic at that time. If so, that would suggest that there’s a conflict having both types enabled or the router is getting confused about where to send responses/traffic to. That is the only way really that your config is different than mine. As you said, the IPSec connection appears to be successful, you’re just not getting traffic to pass. I really think somewhere in there the routing is being goofed up.
-
@gabacho4 Hi again. No worries at all, I am just glad you are willing to spend the time trying to help. I have tried disabling the non VTI tunnels on both sides. Unfortunately, that too does not fix the problem. I have checked the routing tables on both sides, and they look right.
-
@dehaas I had similar problems and changing the MTU to 1472 allowed traffic to pass