PFSense DNS cannot resolve outlook.ha.office365.com properly
-
@tdixler turn off pfblocker. can you resolve the name?
-
I disabled PFBlocker and it didn't change anything. That single domain is the only one that is not resolving properly. It's receiving an invalid response from PFSense's resolver.
DNS format error from 172.16.0.1#53 resolving outlook.ha.office365.com/HTTPS for 172.16.0.200#49608: Name trafficmanager.net (SOA) not subdomain of zone ha.office365.com -- invalid response
Is there a specific option in the resolver config that may be causing this?
-
@tdixler are you configured for dns resolver or dns forwarder?
-
@tdixler said in PFSense DNS cannot resolve outlook.ha.office365.com properly:
to what Google's public DNS server (8.8.8.8) is giving.
Why would you think they have to be the same? That is hosted off a CDN. They have lots of IPs that can be used for that specific FQDN. You also then have responses based on the source of the query and your location - so it points you to the closest one for where you at.
When you query 8.8.8.8 your doing a query to a anycast address, your not exactly sure which server - and where its located will respond..
So you have a IP A that does query for some fqdn, and then you have a different IP B (google) that resolves that IP from different part of the world or country your in - and guess what some different IPs might be returned.
Here you have my vps in the Netherlands doing the query, then on the right you have my local unbound doing it from the states.. I would expect that they could come back with different IPs.
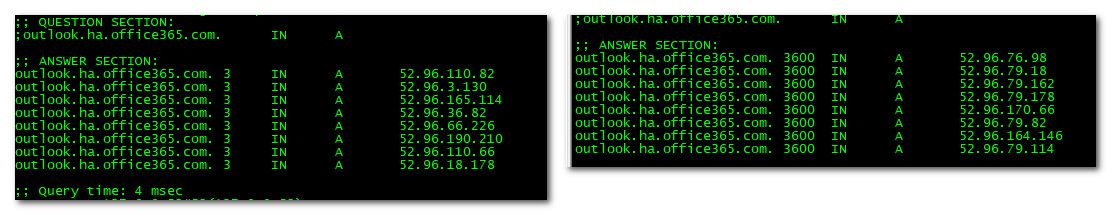
edit: So that first IP.. from my vps that is over in the EU... When I ping that first IP look at the response time, vs when I ping that same IP from my connection here in the states..
See the response time difference.
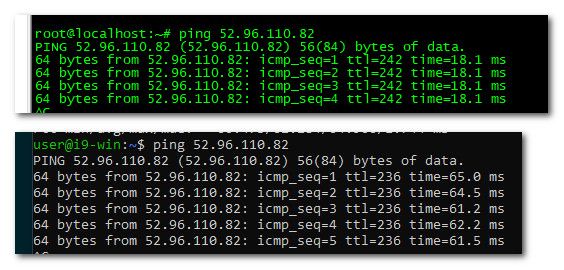
this is another problem with forwarding - you might not get the response you should be getting for what part of the world you in.. And you might be talking to a server way farther from you than it should be for whatever service your trying to use..
When I ping the IP that state resolver gets from eu vps - the times reverse.. EU is longer, states is shorter.
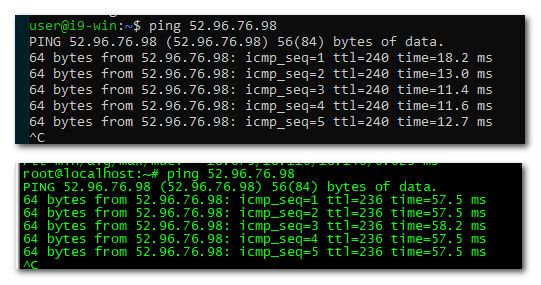
When you host stuff in the cloud, like these services by MS, or AWS or Cloudflare or Akamai you would expect to get back slightly different IPs based upon where you query comes from..
Notice the TTL in the ping response, this tells you how many hops away that IP is.. The lower that number the more hops away that IP is from where you pinging it..
-
@michmoor said in PFSense DNS cannot resolve outlook.ha.office365.com properly:
@tdixler are you configured for dns resolver or dns forwarder?
Both give me the same results :
C:\Users\gwkro>nslookup outlook.ha.office365.com 8.8.8.8 Serveur : dns.google Address: 8.8.8.8 DNS request timed out. timeout was 2 seconds. Réponse ne faisant pas autorité : Nom : LHR-efz.ms-acdc.office.com Addresses: 2603:1026:c06:149c::2 2603:1026:500:60::2 2603:1026:c06:141a::2 2603:1026:c06:1405::2 52.97.219.210 52.97.211.66 52.97.133.130 52.97.212.98 Aliases: outlook.ha.office365.com outlook.ms-acdc.office.comC:\Users\gwkro>nslookup outlook.ha.office365.com 192.168.1.1 Serveur : pfSense.my-pfsense-network.net Address: 192.168.1.1 Réponse ne faisant pas autorité : Nom : CDG-efz.ms-acdc.office.com Addresses: 2603:1026:c0a:8b6::2 2603:1026:c0a:1835::2 2603:1026:c0a:853::2 2603:1026:c0a:1834::2 40.99.220.146 40.99.217.66 52.98.224.178 40.99.153.130 Aliases: outlook.ha.office365.com outlook.ms-acdc.office.comLook the same to me.
And yes, I'm using pfblockerng-devel with some DNSBL feeds.
I never add DNSBL without manual inspection first, as it would be hilarious to use 'microsoft' products that need 'microsoft' host names to function correctly, and then block the access to 'microsoft' by selecting DNSBL that contain 'microsoft' hos names. -
I did some additional research on this specific error in my log and it means that the client tried to query (Check Domain name outlook.ha.office365.com, and type as HTTPS), but due to the domain zone setting being configured wrong, it displays the error I'm seeing.
The DNS Server checked the name server of the zone office365.com, to try and resolve "outlook.ha.office365.com/HTTPS", but in the end, the name server replied to the DNS Server and said that there's no such HTTPS record, and the zone that it managed is trafficmanager.net.
It seems like it's because there's a name server configured a CNAME to the subdomain of " trafficmanager.net".
I'm going to try and contact Microsoft and send this information to them as I'm positive a lot of Office 365 users are experiencing this same problem
-
I'm seeing the same error.
But here it is my bind9 (linux) reporting the error, on a request made from pfSense Unbound (192.168.11.1) , i'm 95% sure the request originates from SWMBO's work phone (WiFi), as they use Office 356 & Outlook.Dec 3 14:08:28 linux named[22754]: DNS format error from 13.107.206.240#53 resolving outlook.ha.office365.com/TYPE65 for client 192.168.11.1#12072: Name trafficmanager.net (SOA) not subdomain of zone ha.office365.com -- invalid response Dec 3 14:08:28 linux named[22754]: DNS format error from 13.107.222.240#53 resolving outlook.ha.office365.com/TYPE65 for client 192.168.11.1#12072: Name trafficmanager.net (SOA) not subdomain of zone ha.office365.com -- invalid response Dec 3 14:08:28 linux named[22754]: DNS format error from 13.107.206.240#53 resolving outlook.ha.office365.com/TYPE65 for client 192.168.11.1#53826: Name trafficmanager.net (SOA) not subdomain of zone ha.office365.com -- invalid response Dec 3 14:08:28 linux named[22754]: DNS format error from 13.107.222.240#53 resolving outlook.ha.office365.com/TYPE65 for client 192.168.11.1#53826: Name trafficmanager.net (SOA) not subdomain of zone ha.office365.com -- invalid response/Bingo
-
I sent all the information to domains@microsoft.com which is the email address associated with trafficmanager.net. The good news is Microsoft owns that domain so hopefully they will take the information and fix the DNS misconfiguration on their side. I am positive every Office365 subscriber is generating these errors in their logs, it just so happens I run my own DNS server and it was bugging me enough to do the research. Hopefully Microsoft will fix the entry and all of our errors will go away.
-
Check Domain name outlook.ha.office365.com, and type as HTTPS<<
HTTPS is not a valid DNS query type. Valid query types are - A, AAAA, CNAME, MX, NS, etc)
Are you confusing with DNS-over-HTTPS (DoH)?
-
@ahking19 said in PFSense DNS cannot resolve outlook.ha.office365.com properly:
Check Domain name outlook.ha.office365.com, and type as HTTPS<<
HTTPS is not a valid DNS query type. Valid query types are - A, AAAA, CNAME, MX, NS, etc)
Are you confusing with DNS-over-HTTPS (DoH)?
Hmmm ... See:
https://datatracker.ietf.org/doc/html/draft-ietf-dnsop-svcb-https-01#section-12.2Right now it seems like Apple IOS > 14.x, is using this type of queries.
Yddrfff .... DoH bypassing (resolver selection)

https://support.opendns.com/hc/en-us/articles/360049861971-DNS-Resolver-Selection-in-iOS-14-and-macOS-11