Need help troubleshooting DNS after upgrade to 22.05
-
Situation:
After upgrading to 22.05 from 22.01, having intermittent DNS problems.Problem description:
DNS will work generally but sometimes stop resolving certain domains for example yahoo.co.jp, bricklink.com, ghacks.net, dynatron.co etc. (just few examples I noticed). not all at the same time or consistency and so it is hard to detect when the problem occurring because it will stop resolving only certain domain names, not always same domains and what seems to be random times, noticed that problem sometimes fixes by itself in time (30min to 2 hours)
The problem is 100% with pfsense DNS resolver as restarting unbound service fixes the problem, also manually changing DNS to something else on client fixes the problem.Unbound logs does not show anything unusual.
Diagnostics directly from pfsense DNS lookup menu also cant find problematic host names so it's not client problem, also it occurs on entire network multiple clients different OS (windows, linux, android, ios).
There were other topics about slow dns or dns problems in 22.05 with various suggestions
things I tried:
Disabling DHCP registration (did not help)
Disabling DNSSEC (seems to have reduced occurrences but did not solve problem)
putting in custom option
server:
do-ip6: no
did not help.any tips for diagnosing this problem that would provide useful diagnostics when problem occurring? to help troubleshooting and finding root cause.
-
I am getting this same issue after the exact same upgrade. I have a Netgate 2100.
I am starting to look at packet captures but have not discovered anything yet.
Please let me know if you found a fix. -
@camg there's no fix it seems that it's bug in this particular version of unbound used in 22.05. this bug seems to be somewhat fixed in latest version of unbound but for that you will need to wait for either new version of pfsense or for netgate to allow unbound update in current version. 22.01 or 2.6 not affected by this so there is also downgrade option.
-
S SteveITS referenced this topic on
-
@vbjp I switched the resolver off and the dns forwarder on (using my ISP's DNS servers) and everything on my network functions again. I'm wondering how this isn't a larger problem and why a fix hasn't been pushed out to netgate users.
-
We had a weird issue with unbound, a short time ago.
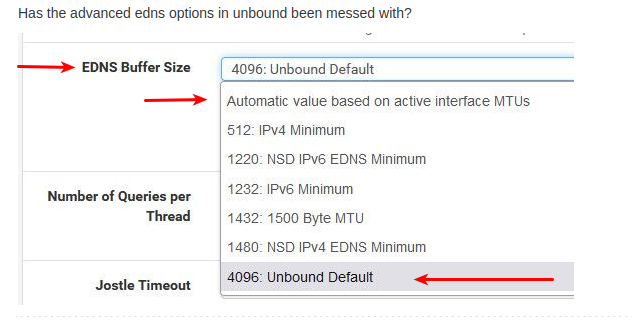
See : https://forum.netgate.com/post/1064550There it seemed like the "Unbound EDNS Buffer Size" was set to :
512 , and that created an issue with some sites,Changing it to 4096 - Unbound default, solved the issue for the poster.
To change goto : Services --> DNS resolver --> Advanced
Scroll down to
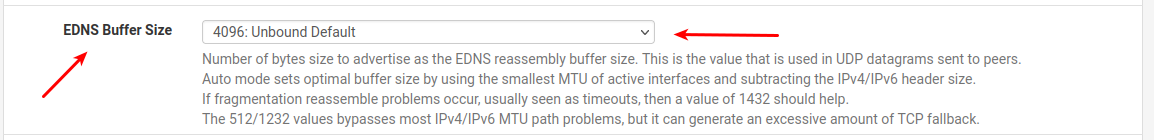
And if not set to 4096 Unbound default , change it to that value.
It's worth a try.The OP in the other thread could also solve it by changing to the forwarder, but that was a circumvention. Not a solution.
Edit:
According to this
https://forum.netgate.com/post/1064607
The new "Install" default should be : Automatic based on interface MTUWhat is your value set to, right now ??
/Bingo
-
@bingo600
hmm I wonder if problem was with MTU all along my WAN interface is
PPPoE (lots of ISPs in Japan uses this if you want IPv4) and require MTU of 1454changed EDNS buffer size setting to 4096 Unbound default
need to wait to confirm if this fixed it as problem was intermittent but it happened at least 3-6 times per day so in next 24 hour I will know.
-
@bingo600 changed setting Unbound EDNS Buffer Size to Unbound default and at least for now the problem seems to be gone. need longer time to say for sure but results seems promising.
-
@vbjp I tried this. It reduced the occurrence somewhat but not completely. I switched back to the DNS forwarder and everything resolved quickly and completely again.
-
@camg sorry to hear that. For me it has been running without any problems after changing buffer size. I also have ipv6 disabled.
-
@camg
If you can run your own Unbound DNS on separate machine you will not be having all these issues.
I have Synology NAS and I compile and build my Unbound straight from Unbound repo. Current version 1.17.
It is a solid solution is you can do this.Problem with pfsense including Unbound is that there is no way a user can update just Unbound itself. Over this year Unbound released 4 version. You are always behind if you use supplied Unbound binaries with pfsense.
I have used that typo of architecture (separating Unbound DNS) for years. Never had any issues. For these people that use pfBlocker - you can do all domain blocking just using Unbound RPZ. Its easy .
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
S scottlindner referenced this topic on
-
S scottlindner referenced this topic on
-
S scottlindner referenced this topic on
-
S scottlindner referenced this topic on
-
S scottlindner referenced this topic on
-
S scottlindner referenced this topic on