LAN routing to VLANS
-
@michmoor
Ok. I was assuming, that his L3 switch has set the pfSense LAN as default gateway and hence route all upstream traffic to it.
As I understood, he had a similar setup with a dumb router before. So the switch setup should already have worked in the past. -
@viragomann OP can chime in on that. I took it as the switch had a default route to the PFsense but the PFsense would need to know where to route to those 10nets on the way back.
-
@michmoor
Ah yes, you're absolutely right. The route is needed pointing to the switch, of course. -
@viragomann @michmoor
Hey guys, appreciate you both stepping in to help me.
Viragomann, sorry for not catching before the NAT outbound you suggested.Yes, the EX435 Switch and other equipment behind it worked perfectly before with the ASUS providing the routing between the WAN and the EX435. Yes I am aware I am doing a double NAT. With the network hardware on the 192.168.50.0 network and my clients connecting to one of the VLANS that are 10.x.x.x.
The Asus was a pretty simple setup but it has one fatal flaw in that it's only copper and an electrical spike killed one of those boxes already and luckily I had a spare that I put in it's place. So hence replacing it with this 7100 that has a fiber connection from the DMARC so I can avoid any electrical spikes in the future.
As I had replied to michmoor earlier I created a LAN gateway of 192.168.50.2 and setup a route for destination addresses of 10.10.x.x to that GW. Do I need this? all net traffic that I am doing currently is originating from internal and I don't want random external traffic onto my network obviously.
Virgomann, Did you have a typo when you suggested an outbound rule of 10.0.0.0/28? Wouldn't it be a 10.0.0.0/8 ? I did create that rule but it didn't get me anywhere from a 10x client.
-
@malicair said in LAN routing to VLANS:
Virgomann, Did you have a typo when you suggested an outbound rule of 10.0.0.0/28? Wouldn't it be a 10.0.0.0/8 ? I did create that rule but it didn't get me anywhere from a 10x client.
Yes, it should be 10.10.0.0/28. It's late here...
Yes I am aware I am doing a double NAT.
We were not assuming this.
This would mean, that your switch translates the source IP in upstream packets into 192.168.50.2?In this case you would neither need the manual outbound NAT rule, nor the static route. Because pfSense would only see 192.168.50.2 and there should be an automatic outbound NAT rule for the LAN subnet anyway.
-
@viragomann
On my EX435 switch I have a static route to 192.168.50.1 which "was" the ASUS router and is now the 7100. So I believe it is simply putting the 10.x traffic directly onto the 7100 which it knows nothing about. (note: I'm stretching my brain here...) -
@malicair
The route on pfSense for the 10.10.x would not impair the functionality even if it was not needed. Neither the outbound NAT rules did. In this case, pfSense would never get a packet for 10.10.x.However, you should know if your switch does nat.
If you default route on the switch is pointing to pfSense, packets should get directed to it.
So you could run a packet capture on pfSense LAN while you try to access an internet resource from a VLAN to see, what's going on. -
@viragomann
The 7100 is seeing 10.x traffic.Here is the results of a LAN packet capture:
18:28:16.793704 IP 10.10.8.12.29620 > 8.8.4.4.53: UDP, length 32
18:28:17.952164 IP 10.10.10.11.49268 > 8.8.8.8.53: UDP, length 59
18:28:17.952415 IP 10.10.10.11.64554 > 40.97.190.2.443: tcp 31
18:28:17.952794 IP 10.10.10.11.52456 > 8.8.8.8.53: UDP, length 59
18:28:17.952800 IP 10.10.10.11.63862 > 8.8.8.8.53: UDP, length 37
18:28:17.952807 IP 10.10.10.11.58518 > 8.8.8.8.53: UDP, length 37
18:28:20.972454 IP 10.10.10.11.64554 > 40.97.190.2.443: tcp 31And here is results from the firewall:
Dec 6 18:27:17 LAN Default deny rule IPv4 (1000000103) 10.10.10.11 17.253.5.202 ICMP
Dec 6 18:27:20 LAN Default deny rule IPv4 (1000000103) 10.10.8.11:47105 8.8.4.4:53 UDP -
@malicair
I see. Obviously pfSense doesn’t pass the packets.
You need a rule on LAN to allow it.
By default pfSense automatically creates a rule only for the LAN subnet. But 10.10.x.x lies outside of this.Additionally you need the route and outbound NAT rule as mentioned above.
-
I created a LAN gateway of 192.168.50.2 and setup a route for destination addresses of 10.10.x.x to that GW. Is this sufficient?
-
@malicair
Yes, but don’t state it in the LAN interface settings, only in System > Routing > Gateways.However, also this does only matter on inbound connections.
-
@viragomann
I did not change any settings in interfaces > LANI went to System > Routing > Gateway and created the following:
Interface: LAN
Gateway: 192.168.50.2Then into System > Routing > Static Routes and created the following:
Destination Network: 10.0.0.0 /28
Gateway: (selected 192.168.50.2)NAT > Outbound:
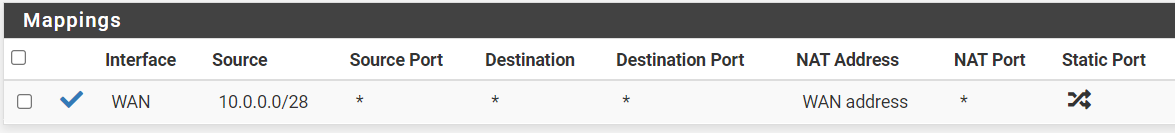
I'm still not getting connectivity.
When I look at the firewall log I see both LAN and WAN deny of 10.x clients -
@viragomann
FYI: It's late here.. going to pause until morning.Thanks!
-
@malicair said in LAN routing to VLANS:
When I look at the firewall log I see both LAN and WAN deny of 10.x clients
Can you post a screenshot, please?
-
@viragomann
Want to circle back with you regarding the /28 designation that you referred to previously. As I understand it a /28 only has 15 addresses so a 10.0.0.0 would have a range of 10.0.0.0-10.0.0.15. Whereas a /8 would provide a range from 10.0.0.0-10.255.255.255 which would cover all 10.x addresses. Shouldn't I be applying a rule with a /8 to cover each of the VLans I have within 10.10.x.x & 10.20.x.x (10.10.8.x, 10.10.10.x, 10.10.14.x, 10.20.0.0)? -
@viragomann
Here is a screen shot of the firewall syslog:
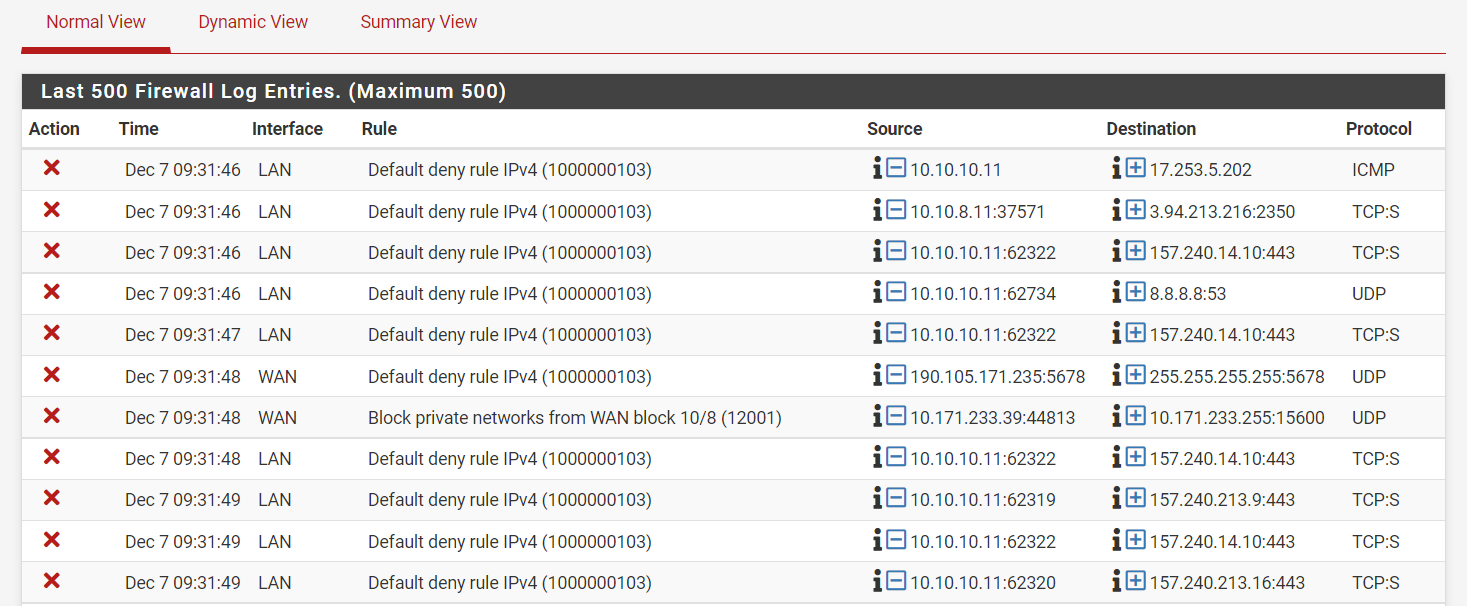
-
@malicair
Yes, I was tired yesterday evening.
For your networks you need at least 10.0.0.0/11 (10.0.0.0 - 10.31.255.255).
Or even add a separate route for each subnet.Also the blocks by the firewall results of the too small range.
-
@viragomann
OK, seems that I have full connectivity working now. :)I created rules for both the WAN and LAN interfaces allowing the traffic for the 10.0.0.0/8 network. Initially I had a mistake in only allowing TCP, which showed up in the syslogs so changed that to ANY and now my clients are connecting.
After multiple days of chasing the configuration I'm quite happy that it's now working. THANKS MUCH!!
Now onto my next step of getting the NORDVPN working. (AFTER SAVING MY CONFIG!)
Cheers and have a great day!