Back to Back Firewall Configuration - Setting Up DNAT Across Dual pfSenses
-
Hi guys!
I do not have any experience with back to back firewalls but a project at work might soon require me to set up something similar so I am testing it out using two pfSense firewalls configured in line.
Here's a very crude network diagram (please refer to the diagram at the bottom with the two firewalls, FW 1 and FW 2):
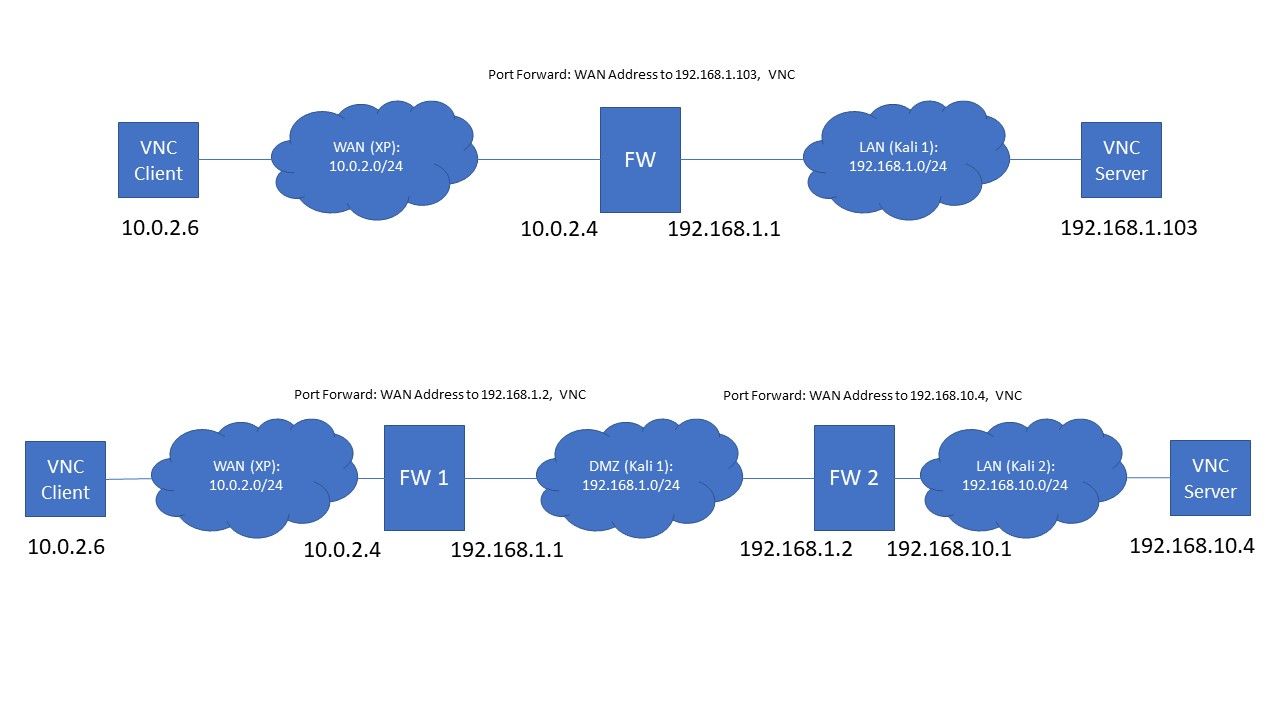
I have set up a VNC server on the LAN interface of FW 2 and I have a VNC client on the WAN interface of FW 1 which wants to interact with it.
If this was a single firewall, I would just configure a port forward as follows: Port 5900 from the WAN Address to the IP address of the VNC server on the LAN interface. This is something that I have tested and it works pretty good in combination with the appropriate ACL. I can VNC properly and the same works via telnet also.
Since my test configuration involves two firewalls set up back to back, I decided to port forward VNC from the WAN Address of FW 1 to the IP address of FW 2. I then set up another port forward inside FW 2 as follows: Port 5900 from the WAN Address to the IP address of the VNC server on the LAN interface. So the VNC Client on the WAN interface of FW 1 is mapped to the IP of FW 2 which is then mapped to the IP of VNC Server.
Although I can see in the firewall logs that this connection is being allowed, the VNC client cannot access the VNC server and the connection keeps failing.
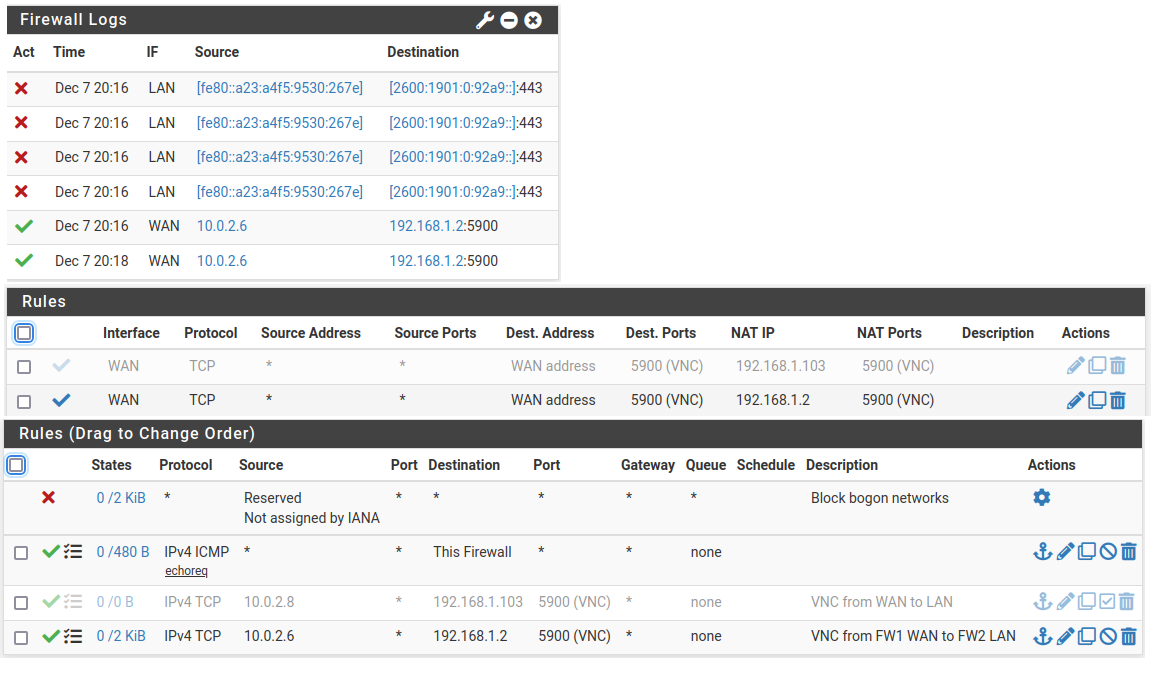
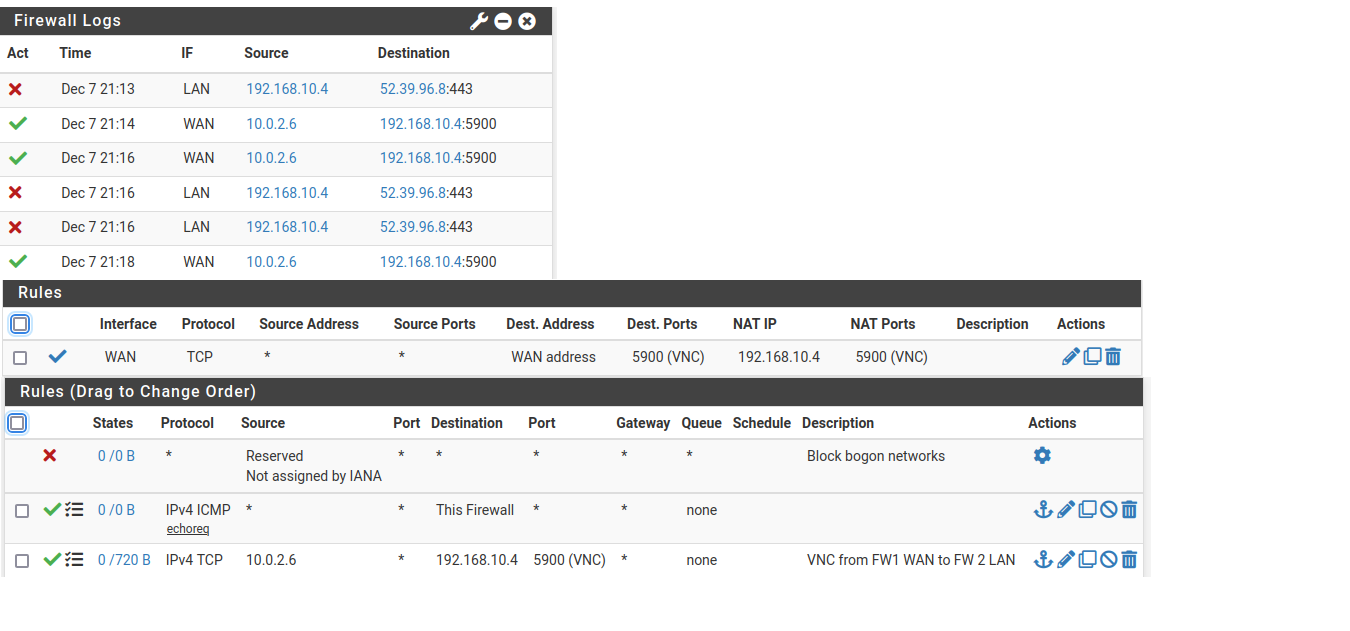
I am attaching the firewall logs along with the NAT rules + ACLs here.
FW 1:
FW 2:
Could somebody please tell me what I am doing wrong here? I even tried setting up a static route on FW 1 with FW 2 as the gateway with the LAN interface of FW 2 as the destination network and then adjusted the NAT rule to directly map the WAN address of FW 1 to the address of the VNC server i.e. 192.168.10.4 but the overall behavior is exactly the same i.e. pfSense seems to be forwarding everything correctly but the VNC client cannot open up a VNC connection.
The two strategies I have employed so far might not be the most efficient so I would also appreciate if you could guide me about how an inbound connection like this is normally supposed to be set up across two back to back firewalls.
Thank you very much for your help in advance.
-
@pfsensor666
You need a static route on FW2 for the client or his subnet and point it to FW1.It's also required that the server is configured to use FW2 as default gateway.
-
@viragomann Thanks. That did the trick. Could you explain why I need this static route from FW 2 to the WAN or external interface of FW 1?
-
@pfsensor666
The server addresses the response packets back the the client IP, which is 10.0.2.6.
So the server will direct the response to his default gateway, FW2.
To instruct FW2 to direct the packet destined for 10.0.2.6 to FW1 you need a static route, otherwise it will send the packet even to its default gateway.Instead of a static route you can also masquerade the traffic on FW1 by an outbound NAT rule. Which means the source IP in request packets gets replaced by the firewalls interface IP.
But doing this, the server will see the access coming from 162.168.1.1 instead of the real clients IP.