Unable to illegal DNS record from pfsense (DNS-resolver corruption)
-
@asadz well yeah if clients asks for something and gets back a IP that is not local - it would try to get their via its gateway.
The question is here is why/how is it getting this 100.2.3.4 address for what is being asked..
Where does AD get its answers when what is asked is not in your namespace? Does it forward, to where - does it resolve? Tell you right now .local would not resolve on the public internet.
You would get back a SOA for the roots because .local is not a valid TLD. There should be no way anything .local should be resolvable to anything outside your network.
Your 2 example sb.scorecard or sb.scorecodesearch.com do not resolve to 100.x on the public internet either. So somewhere you have it setup to return that 100.x address for something, be it a host entry in unbound or your AD, or some sort of wild card, etc. when there is a .local tld
100.x which is no the correct PTR record for this zone.
Not understanding your thought process on how that has anything to do with anything..
To get to the bottom of this - just take pfsense and your AD talking to each other out of the equation. Again what is your AD dns setup to do when you ask it for something it is not authoritative for - its either going to forward, or its going to resolve. If forwarding to pfsense change that so it forwards to say gooledns or cloudflare or something.. On pfsense remove any domain overrides for .local etc..
Now query each of them for your fqdn that is returning the bad 100.x address.
-
This post is deleted! -
@asadz flush the entries where? Not sure why you care about connections and traceroutes - if stuff your client want to talk to are resolving to this IP address, then its a give they will attempt to make these connections.
Those all go away when you have correct resolution of what your actually trying to get to - so now there is a proxy as well - proxies unless transparent will resolve things for where the client asks them to go, resolution is done by the proxy not the client when proxy is explicitly set on the client.
-
@johnpoz yes using HAPROXY but its for reverse proxy , I don't think it will effect how for addresses that local e.g .local.
-
I don't have much to add to what Johnpoz wrote, but I did a Google search and found the following that might help:
See [0022]:
https://patents.google.com/patent/US20070195800 -
@bbcan177 said in Unable to illegal DNS record from pfsense (DNS-resolver corruption):
I don't have much to add to what Johnpoz wrote, but I did a Google search and found the following that might help:
See [0022]:
https://patents.google.com/patent/US20070195800Thanks bbcan177, but this is not a design issue in my view all was working fine on Dec-14, you can see in dns-reply.logs above where the 100.2.3.4 first appear.
I tested with my vpn client DNS addresses set to 8.8.8.8/4.4.4.4 and on DNS resolver there is no static mapping or override for
pingme.mydomain.local
but still i'm getting response from 100., I think this is due to stale state table entry for 100. can i get ride of them without restarting firewall?. Thankyou
-
@asadz said in Unable to illegal DNS record from pfsense (DNS-resolver corruption):
I think this is due to stale state table entry for 100
No it has nothing to do with a state... You still have not answered the basic question of where does your AD point to??
-
@johnpoz you mean the DNS server it uses?
-
@johnpoz it points to itself as primary and as alternative to pfsense
-
@asadz said in Unable to illegal DNS record from pfsense (DNS-resolver corruption):
No that is NOT what I mean, and DC should never point to anything but itself.. Or its the other DC running dns running in your network.
Where does it go when a client asks it for something not in its namespace.. You setup MS dns to either forward or resolve - just like you do unbound in pfsense. The dns set on the interface has nothing to do with that.
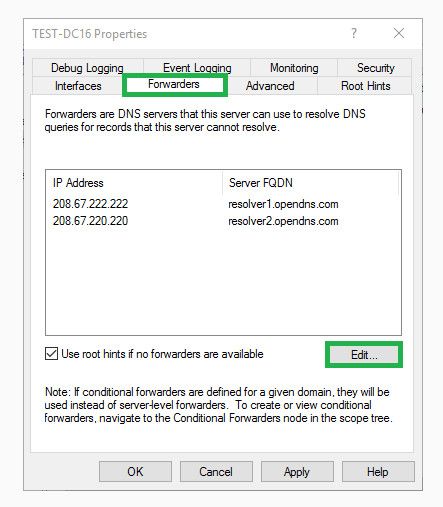
-
@johnpoz pls see the output the second ip is pfsense interface (web-ui). First is second DC.
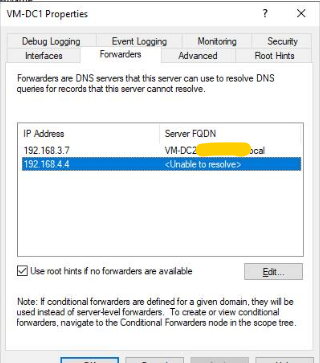
-
@johnpoz should i check DC2 settings as well, which is second domain controller..
-
@asadz also i checked DC2 points to PFsense infra interface (don't know why) should it not point to DC1 server IP address?
-
@asadz and what is this 192.168.4.4?
And yes you need to check both of them.
If they are not set to forward to pfsense.. And you still resolve your whatever to 100, then you prove to yourself its your AD dns issue..
Forward them to say google dns - these are the name servers used for resolving stuff not in your name space - they should not point to your AD for dns.. These are used to resolve the internet stuff, not stuff you are authoritative for forwarding to AD.. When then does what with it when asking for say www.google.com - forwards it back to the other one?
-
@johnpoz great makes 100% sense let me try this variation now.
-
@asadz
test done on DC1, DC2 i removed all pfsense IP put 8.8.8.8 in DC2,
in fwd section of DC1 i have put IP address of DC2, and I also tried put 8.8.8.8 with no reference of DC2, still resolves to 100.* :( -
@asadz said in Unable to illegal DNS record from pfsense (DNS-resolver corruption):
still resolves to 100.* :(
Because you have an issue with your AD, that was what I have been saying since the start..
in fwd section of DC1 i have put IP address of DC2
Pointless.. If client asks dc1 for say www.google.com which you are not authoritative for, what good is it to forward that to dc2? It is not authoritative for google.com either - so it would just have to forward that query as well.
The forwarders in your AD dns should point to what can resolve stuff you are not authoritative for.. The dns set on the server itself should point to itself, and the other AD dns running in your network..
My guess to your issue is you have a wildcard in your AD dns, do you have a * as a record.. this would resolve anything.otherthing.whatever.something.local to that IP.. Anything that does not have a specific record say host.local or sb.whatever.local to what that wildcard entry.
So if a client happens to ask for sb.scorecard.com.local - then it would return the wildcard record.
But now that you are not forwarding to pfsense, and your client directly asks your AD dns for whatever - and it returns that 100.x address you know for sure its an issue in your AD dns.. Or where your AD forwards.. but .local should never return anything on the public internet - it is not a valid tld.. And the 2 examples you gave of sb.domain.tld sure do not resolve 100.x on the public internet - one is not a valid domain, and the other resolves to public IP addresses that do not start with 100.
-
Because you have an issue with your AD, that was what I have been saying since the start..
but it was the pfsense according to dns-reply.log that return the bad ip address, on 14th dec the AD 192.168.3.6 did request for sb.scorecardsearch.com and it was returned that address. So, it behave as expected for ip/domains not under its control it fwd as expected.
My guess to your issue is you have a wildcard in your AD dns, do you have a * as a record.. this would resolve anything.otherthing.whatever.something.local to that IP.. Anything that does not have a specific record say host.local or sb.whatever.local to what that wildcard entry.
any specific place to check (please note im not an AD guy), i checked in forward and reverse lookup section found none with
*in itBut now that you are not forwarding to pfsense, and your client directly asks your AD dns for whatever - and it returns that 100.x address you know for sure its an issue in your AD dns.. Or where your AD forwards.. but .local should never return anything on the public internet - it is not a valid tld.. And the 2 examples you gave of sb.domain.tld sure do not resolve 100.x on the public internet - one is not a valid domain, and the other resolves to public IP addresses that do not start with 100.
Yes, i get your point AD is not forgetting this mapping , it is holding on to something also the TTL value 0 was a indicator as well, the request is not leaving the network (and going to internet)
what about stale records? also i'm able to resolve hostnames correctly with local nslookup/ping from DC, but that shouldn't matter as its local. -
@asadz on DC this is output of nslookup
Default Server: VM-DC1.dummy.local Address: 192.168.3.6 > sb.scorecardsearch.com Server: VM-DC1.dummy.local Address: 192.168.3.6 Non-authoritative answer: Name: sb.scorecardsearch.com Address: 100.2.3.4 -
@asadz said in Unable to illegal DNS record from pfsense (DNS-resolver corruption):
but it was the pfsense according to dns-reply.log that return the bad ip address
well yeah if pfsense asks your AD, and it returned that 100 then it would be cached.. This is why separation now allows you to figure out where the problem is.
Clear your AD dns cache.. if it still returns that address then you need to figure out why.. Sniff to see if your AD forwards that fqdn and gets back that answer. Or if when you client asks it just gets returned..
And again I would highly suggest you turn on debug when you do your nslookup - so you can validate exactly what is getting asked.
That "Non-authoritative answer" points to that being in cache.