Site-to-Site IPsec VPN pfSense - Microsoft Azure VPN issues
-
Hi,
pfSense CE 2.6I am experiencing issues with the Site-to-Site IPsec VPN: pfSense - Microsoft Azure VPN.
The VPN connection suddenly stops working and cannot be reconnected.
AWS VPN - pfSense - no issues at all.
Is that a well-known issue with Azure VPN or is this just pfSense - Azure incompatibility problem?
Tried multiple IKEv2 configurations - all failed after some time of workingThanks.
-
@lk777 Anything in the logs you can share? Theres a reason probably in there.
-
@michmoor For testing purposes, I have set up Strongswan behind the pfSense, Strongswan - Azure Site-to-Site VPN works. So this is definitely pfSense - Azure issue.
2022-12-20 15:12:32.126045-05:00 charon 9326 11[CFG] vici client 99 disconnected 2022-12-20 15:12:32.125830-05:00 charon 9326 08[CFG] vici client 99 requests: list-sas 2022-12-20 15:12:32.125712-05:00 charon 9326 01[CFG] vici client 99 registered for: list-sa 2022-12-20 15:12:32.125684-05:00 charon 9326 11[CFG] vici client 99 connected 2022-12-20 15:12:27.071091-05:00 charon 9326 12[CFG] vici client 98 disconnected 2022-12-20 15:12:27.070839-05:00 charon 9326 01[CFG] vici client 98 requests: list-sas 2022-12-20 15:12:27.070701-05:00 charon 9326 12[CFG] vici client 98 registered for: list-sa 2022-12-20 15:12:27.070671-05:00 charon 9326 09[CFG] vici client 98 connected 2022-12-20 15:12:22.984636-05:00 charon 9326 15[CFG] vici client 97 disconnected 2022-12-20 15:12:22.983303-05:00 charon 9326 01[CFG] vici client 97 requests: list-sas 2022-12-20 15:12:22.983177-05:00 charon 9326 15[CFG] vici client 97 registered for: list-sa 2022-12-20 15:12:22.983152-05:00 charon 9326 01[CFG] vici client 97 connected 2022-12-20 15:12:22.015192-05:00 charon 9326 05[CFG] vici client 96 disconnected 2022-12-20 15:12:22.014970-05:00 charon 9326 10[CFG] vici client 96 requests: list-sas 2022-12-20 15:12:22.014849-05:00 charon 9326 10[CFG] vici client 96 registered for: list-sa 2022-12-20 15:12:22.014828-05:00 charon 9326 05[CFG] vici client 96 connected 2022-12-20 15:12:16.956644-05:00 charon 9326 13[CFG] vici client 95 disconnected 2022-12-20 15:12:16.956427-05:00 charon 9326 06[CFG] vici client 95 requests: list-sas 2022-12-20 15:12:16.956310-05:00 charon 9326 13[CFG] vici client 95 registered for: list-sa 2022-12-20 15:12:16.956290-05:00 charon 9326 06[CFG] vici client 95 connected 2022-12-20 15:12:12.192654-05:00 charon 9326 13[NET] <con3|5> sending packet: from 69.X.X.176[500] to 4.X.X.189[500] (464 bytes) 2022-12-20 15:12:12.192617-05:00 charon 9326 13[IKE] <con3|5> retransmit 5 of request with message ID 0 2022-12-20 15:12:11.895356-05:00 charon 9326 08[CFG] vici client 94 disconnected 2022-12-20 15:12:11.895114-05:00 charon 9326 13[CFG] vici client 94 requests: list-sas 2022-12-20 15:12:11.894998-05:00 charon 9326 08[CFG] vici client 94 registered for: list-sa 2022-12-20 15:12:11.894973-05:00 charon 9326 13[CFG] vici client 94 connected 2022-12-20 15:12:07.007121-05:00 charon 9326 12[CFG] vici client 93 disconnected 2022-12-20 15:12:07.006796-05:00 charon 9326 11[CFG] vici client 93 requests: list-sas 2022-12-20 15:12:07.006655-05:00 charon 9326 12[CFG] vici client 93 registered for: list-sa 2022-12-20 15:12:07.006636-05:00 charon 9326 11[CFG] vici client 93 connected 2022-12-20 15:12:06.834537-05:00 charon 9326 09[CFG] vici client 92 disconnected 2022-12-20 15:12:06.834329-05:00 charon 9326 15[CFG] vici client 92 requests: list-sas 2022-12-20 15:12:06.834220-05:00 charon 9326 15[CFG] vici client 92 registered for: list-sa 2022-12-20 15:12:06.834200-05:00 charon 9326 09[CFG] vici client 92 connected 2022-12-20 15:12:01.774989-05:00 charon 9326 10[CFG] vici client 91 disconnected 2022-12-20 15:12:01.774751-05:00 charon 9326 05[CFG] vici client 91 requests: list-sas 2022-12-20 15:12:01.774623-05:00 charon 9326 10[CFG] vici client 91 registered for: list-sa 2022-12-20 15:12:01.774602-05:00 charon 9326 05[CFG] vici client 91 connected 2022-12-20 15:11:56.709783-05:00 charon 9326 14[CFG] vici client 90 disconnected 2022-12-20 15:11:56.709586-05:00 charon 9326 07[CFG] vici client 90 requests: list-sas 2022-12-20 15:11:56.709470-05:00 charon 9326 14[CFG] vici client 90 registered for: list-sa 2022-12-20 15:11:56.709450-05:00 charon 9326 07[CFG] vici client 90 connected 2022-12-20 15:11:51.646609-05:00 charon 9326 06[CFG] vici client 89 disconnected 2022-12-20 15:11:51.646338-05:00 charon 9326 08[CFG] vici client 89 requests: list-sas 2022-12-20 15:11:51.646224-05:00 charon 9326 08[CFG] vici client 89 registered for: list-sa 2022-12-20 15:11:51.646205-05:00 charon 9326 06[CFG] vici client 89 connected 2022-12-20 15:11:50.984223-05:00 charon 9326 12[CFG] vici client 88 disconnected 2022-12-20 15:11:50.984018-05:00 charon 9326 11[CFG] vici client 88 requests: list-sas 2022-12-20 15:11:50.983911-05:00 charon 9326 08[CFG] vici client 88 registered for: list-sa 2022-12-20 15:11:50.983891-05:00 charon 9326 11[CFG] vici client 88 connected 2022-12-20 15:11:46.581966-05:00 charon 9326 15[CFG] vici client 87 disconnected 2022-12-20 15:11:46.581739-05:00 charon 9326 09[CFG] vici client 87 requests: list-sas 2022-12-20 15:11:46.581398-05:00 charon 9326 15[CFG] vici client 87 registered for: list-sa 2022-12-20 15:11:46.581376-05:00 charon 9326 09[CFG] vici client 87 connected 2022-12-20 15:11:41.519183-05:00 charon 9326 01[CFG] vici client 86 disconnected 2022-12-20 15:11:41.518984-05:00 charon 9326 05[CFG] vici client 86 requests: list-sas 2022-12-20 15:11:41.518882-05:00 charon 9326 05[CFG] vici client 86 registered for: list-sa 2022-12-20 15:11:41.518860-05:00 charon 9326 01[CFG] vici client 86 connected 2022-12-20 15:11:36.453318-05:00 charon 9326 10[CFG] vici client 85 disconnected 2022-12-20 15:11:36.452938-05:00 charon 9326 07[CFG] vici client 85 requests: list-sas 2022-12-20 15:11:36.452822-05:00 charon 9326 05[CFG] vici client 85 registered for: list-sa 2022-12-20 15:11:36.452801-05:00 charon 9326 07[CFG] vici client 85 connected 2022-12-20 15:11:35.985348-05:00 charon 9326 14[CFG] vici client 84 disconnected 2022-12-20 15:11:35.985131-05:00 charon 9326 05[CFG] vici client 84 requests: list-sas 2022-12-20 15:11:35.985009-05:00 charon 9326 06[CFG] vici client 84 registered for: list-sa 2022-12-20 15:11:35.984986-05:00 charon 9326 05[CFG] vici client 84 connected 2022-12-20 15:11:31.390341-05:00 charon 9326 11[CFG] vici client 83 disconnected 2022-12-20 15:11:31.390123-05:00 charon 9326 08[CFG] vici client 83 requests: list-sas 2022-12-20 15:11:31.389992-05:00 charon 9326 12[CFG] vici client 83 registered for: list-sa 2022-12-20 15:11:31.389969-05:00 charon 9326 08[CFG] vici client 83 connected 2022-12-20 15:11:30.201790-05:00 charon 9326 12[NET] <con3|5> sending packet: from 69.X.X.176[500] to 4.X.X.189[500] (464 bytes) 2022-12-20 15:11:30.201703-05:00 charon 9326 12[IKE] <con3|5> retransmit 4 of request with message ID 0 2022-12-20 15:11:26.325152-05:00 charon 9326 13[CFG] vici client 82 disconnected 2022-12-20 15:11:26.324945-05:00 charon 9326 09[CFG] vici client 82 requests: list-sas 2022-12-20 15:11:26.324832-05:00 charon 9326 12[CFG] vici client 82 registered for: list-sa 2022-12-20 15:11:26.324812-05:00 charon 9326 09[CFG] vici client 82 connected 2022-12-20 15:11:21.261270-05:00 charon 9326 15[CFG] vici client 81 disconnected 2022-12-20 15:11:21.261053-05:00 charon 9326 15[CFG] vici client 81 requests: list-sas 2022-12-20 15:11:21.260934-05:00 charon 9326 01[CFG] vici client 81 registered for: list-sa 2022-12-20 15:11:21.260911-05:00 charon 9326 15[CFG] vici client 81 connected 2022-12-20 15:11:20.986186-05:00 charon 9326 10[CFG] vici client 80 disconnected 2022-12-20 15:11:20.985989-05:00 charon 9326 01[CFG] vici client 80 requests: list-sas 2022-12-20 15:11:20.985711-05:00 charon 9326 07[CFG] vici client 80 registered for: list-sa 2022-12-20 15:11:20.985692-05:00 charon 9326 10[CFG] vici client 80 connected 2022-12-20 15:11:16.194091-05:00 charon 9326 05[CFG] vici client 79 disconnected 2022-12-20 15:11:16.193891-05:00 charon 9326 14[CFG] vici client 79 requests: list-sas 2022-12-20 15:11:16.193775-05:00 charon 9326 06[CFG] vici client 79 registered for: list-sa 2022-12-20 15:11:16.193756-05:00 charon 9326 14[CFG] vici client 79 connected 2022-12-20 15:11:11.127708-05:00 charon 9326 11[CFG] vici client 78 disconnected 2022-12-20 15:11:11.127503-05:00 charon 9326 11[CFG] vici client 78 requests: list-sas 2022-12-20 15:11:11.127379-05:00 charon 9326 08[CFG] vici client 78 registered for: list-sa 2022-12-20 15:11:11.127358-05:00 charon 9326 06[CFG] vici client 78 connected 2022-12-20 15:11:06.864577-05:00 charon 9326 08[NET] <con3|5> sending packet: from 69.X.X.176[500] to 4.X.X.189[500] (464 bytes) 2022-12-20 15:11:06.864532-05:00 charon 9326 08[IKE] <con3|5> retransmit 3 of request with message ID 0 2022-12-20 15:11:06.070337-05:00 charon 9326 13[CFG] vici client 77 disconnected 2022-12-20 15:11:06.070132-05:00 charon 9326 08[CFG] vici client 77 requests: list-sas 2022-12-20 15:11:06.070026-05:00 charon 9326 09[CFG] vici client 77 registered for: list-sa 2022-12-20 15:11:06.070003-05:00 charon 9326 08[CFG] vici client 77 connected 2022-12-20 15:11:05.992780-05:00 charon 9326 12[CFG] vici client 76 disconnected 2022-12-20 15:11:05.992564-05:00 charon 9326 13[CFG] vici client 76 requests: list-sas 2022-12-20 15:11:05.992438-05:00 charon 9326 12[CFG] vici client 76 registered for: list-sa 2022-12-20 15:11:05.992416-05:00 charon 9326 15[CFG] vici client 76 connected 2022-12-20 15:11:01.016746-05:00 charon 9326 01[CFG] vici client 75 disconnected 2022-12-20 15:11:01.016480-05:00 charon 9326 01[CFG] vici client 75 requests: list-sas 2022-12-20 15:11:01.016321-05:00 charon 9326 07[CFG] vici client 75 registered for: list-sa 2022-12-20 15:11:01.016218-05:00 charon 9326 10[CFG] vici client 75 connected 2022-12-20 15:10:55.959514-05:00 charon 9326 05[CFG] vici client 74 disconnected 2022-12-20 15:10:55.959295-05:00 charon 9326 07[CFG] vici client 74 requests: list-sas 2022-12-20 15:10:55.959176-05:00 charon 9326 05[CFG] vici client 74 registered for: list-sa 2022-12-20 15:10:55.959157-05:00 charon 9326 14[CFG] vici client 74 connected 2022-12-20 15:10:53.903978-05:00 charon 9326 05[NET] <con3|5> sending packet: from 69.X.X.176[500] to 4.X.X.189[500] (464 bytes) 2022-12-20 15:10:53.903946-05:00 charon 9326 05[IKE] <con3|5> retransmit 2 of request with message ID 0 2022-12-20 15:10:50.902672-05:00 charon 9326 11[CFG] vici client 73 disconnected 2022-12-20 15:10:50.902468-05:00 charon 9326 05[CFG] vici client 73 requests: list-sas 2022-12-20 15:10:50.902354-05:00 charon 9326 11[CFG] vici client 73 registered for: list-sa 2022-12-20 15:10:50.902333-05:00 charon 9326 06[CFG] vici client 73 connected 2022-12-20 15:10:49.985572-05:00 charon 9326 09[CFG] vici client 72 disconnected 2022-12-20 15:10:49.984086-05:00 charon 9326 11[CFG] vici client 72 requests: list-sas 2022-12-20 15:10:49.983979-05:00 charon 9326 11[CFG] vici client 72 registered for: list-sa 2022-12-20 15:10:49.983955-05:00 charon 9326 09[CFG] vici client 72 connected 2022-12-20 15:10:47.706759-05:00 charon 9326 08[CFG] vici client 70 disconnected 2022-12-20 15:10:46.700891-05:00 charon 9326 11[NET] <con3|5> sending packet: from 69.X.X.176[500] to 4.X.X.189[500] (464 bytes) 2022-12-20 15:10:46.700839-05:00 charon 9326 11[IKE] <con3|5> retransmit 1 of request with message ID 0 2022-12-20 15:10:45.848065-05:00 charon 9326 13[CFG] vici client 71 disconnected 2022-12-20 15:10:45.847814-05:00 charon 9326 15[CFG] vici client 71 requests: list-sas 2022-12-20 15:10:45.847673-05:00 charon 9326 15[CFG] vici client 71 registered for: list-sa 2022-12-20 15:10:45.847645-05:00 charon 9326 15[CFG] vici client 71 connected 2022-12-20 15:10:42.696407-05:00 charon 9326 13[NET] <con3|5> sending packet: from 69.X.X.176[500] to 4.X.X.189[500] (464 bytes) 2022-12-20 15:10:42.695981-05:00 charon 9326 13[ENC] <con3|5> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] 2022-12-20 15:10:42.695907-05:00 charon 9326 13[CFG] <con3|5> sending supported signature hash algorithms: sha256 sha384 sha512 identity 2022-12-20 15:10:42.695858-05:00 charon 9326 13[CFG] <con3|5> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 2022-12-20 15:10:42.690554-05:00 charon 9326 13[IKE] <con3|5> IKE_SA con3[5] state change: CREATED => CONNECTING 2022-12-20 15:10:42.690542-05:00 charon 9326 13[IKE] <con3|5> initiating IKE_SA con3[5] to 4.X.X.189 2022-12-20 15:10:42.690499-05:00 charon 9326 13[IKE] <con3|5> activating IKE_AUTH_LIFETIME task 2022-12-20 15:10:42.690492-05:00 charon 9326 13[IKE] <con3|5> activating CHILD_CREATE task 2022-12-20 15:10:42.690484-05:00 charon 9326 13[IKE] <con3|5> activating IKE_CONFIG task 2022-12-20 15:10:42.690476-05:00 charon 9326 13[IKE] <con3|5> activating IKE_CERT_POST task 2022-12-20 15:10:42.690465-05:00 charon 9326 13[IKE] <con3|5> activating IKE_AUTH task 2022-12-20 15:10:42.690457-05:00 charon 9326 13[IKE] <con3|5> activating IKE_CERT_PRE task 2022-12-20 15:10:42.690450-05:00 charon 9326 13[IKE] <con3|5> activating IKE_NATD task 2022-12-20 15:10:42.690442-05:00 charon 9326 13[IKE] <con3|5> activating IKE_INIT task 2022-12-20 15:10:42.690434-05:00 charon 9326 13[IKE] <con3|5> activating IKE_VENDOR task 2022-12-20 15:10:42.690426-05:00 charon 9326 13[IKE] <con3|5> activating new tasks 2022-12-20 15:10:42.690418-05:00 charon 9326 13[IKE] <con3|5> queueing CHILD_CREATE task 2022-12-20 15:10:42.690409-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_AUTH_LIFETIME task 2022-12-20 15:10:42.690400-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_CONFIG task 2022-12-20 15:10:42.690391-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_CERT_POST task 2022-12-20 15:10:42.690382-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_AUTH task 2022-12-20 15:10:42.690373-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_CERT_PRE task 2022-12-20 15:10:42.690364-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_NATD task 2022-12-20 15:10:42.690352-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_INIT task 2022-12-20 15:10:42.690326-05:00 charon 9326 13[IKE] <con3|5> queueing IKE_VENDOR task 2022-12-20 15:10:42.690229-05:00 charon 9326 08[CFG] vici initiate CHILD_SA 'con3' 2022-12-20 15:10:42.690196-05:00 charon 9326 08[CFG] vici client 70 requests: initiate 2022-12-20 15:10:42.690016-05:00 charon 9326 13[CFG] vici client 70 registered for: control-log 2022-12-20 15:10:42.689992-05:00 charon 9326 08[CFG] vici client 70 connected 2022-12-20 15:10:42.631913-05:00 charon 9326 07[CFG] vici client 69 disconnected 2022-12-20 15:10:42.631803-05:00 charon 9326 10[CFG] vici client 69 requests: list-sas 2022-12-20 15:10:42.631584-05:00 charon 9326 10[CFG] vici client 69 registered for: list-sa -
@lk777 So the pfsense was getting as a router in your test case? Hmmm..
What was the configuration of strongswan? Same as pfsense?Also, when you say it stops working and cannot be reconnected, do you mean it wont reconnect unless you send interesting traffic across the tunnel again?
-
@michmoor pfSense port-forwards 500 and 4500 to the strongswan machine. The same configuration (at least, seems similar):
ss_azure_vpn_ikev2 { # IKE major version to use for connection. version = 2 # Local address(es) to use for IKE communication, comma separated. local_addrs = %any # Remote address(es) to use for IKE communication, comma separated. # remote_addrs = %any remote_addrs = 4.X.X.189 # Comma separated proposals to accept for IKE. proposals = aes256-sha256-modp2048,default # Interval of liveness checks (DPD). dpd_delay = 30s # Timeout for DPD checks (IKEV1 only). dpd_timeout = 180s # Use IKE UDP datagram fragmentation (yes, accept, no or force). fragmentation = accept # Connection uniqueness policy (never, no, keep or replace). unique = no # Time to schedule IKE reauthentication. # reauth_time = 0s # Time to schedule IKE rekeying. rekey_time = 8h # Section for a local authentication round. local-1 { # Authentication to perform locally (pubkey, psk, xauth[-backend] or # eap[-method]). auth = psk # IKE identity to use for authentication round. id = 69.X.X.177 } # Section for a remote authentication round. remote-1 { # IKE identity to expect for authentication round. id = 4.X.X.189 auth = psk } children { # CHILD_SA configuration sub-section. ss_azure_vpn_ikev2 { esp_proposals = aes256-sha256-modp2048,default local_ts = 10.10.5.0/24 # Remote selectors to include in CHILD_SA. remote_ts = 10.39.0.0/16 # Time to schedule CHILD_SA rekeying. rekey_time = 8h # IPsec Mode to establish (tunnel, transport, transport_proxy, # beet, pass or drop). mode = tunnel # Action to perform on DPD timeout (clear, trap or restart). dpd_action = restart # Action to perform after loading the configuration (none, trap, # start). start_action = start } } } secrets { # IKE preshared secret section for a specific secret. ike-3 { # IKE identity the IKE preshared secret belongs to. id-1 = 69.X.X.177 id-2 = 4.X.X.189 # Value of the IKE preshared secret. secret = "<secret>" } } # Include config snippets include conf.d/*.confpfSense never reconnects after the first drop.
-
@lk777 what are the rekeying intervals set at?
-
! > Connection name: S2S-VPN-AzVD-pfSense ! > VPN Gateway name: a1430077-9202-45ef-XXXX-221a8802a32c ! > Public IP addresses: ! + Public IP 1: 4.X.X.189 ! > Virtual network address space: ! + CIDR: 10.39.0.0/16 ! - Prefix: 10.39.0.0 ! - Netmask: 255.255.0.0 ! - Wildcard: 0.0.255.255 ! > Local network gateway: pfSense-LGW ! > On-premises VPN IP: 69.X.X.176 ! > On-premises address prefixes: ! + CIDR: 10.10.5.0/24 ! - Prefix: 10.10.5.0 ! - Netmask: 255.255.255.0 ! - Wildcard: 0.0.0.255 ! ! [2] IPsec/IKE parameters ! ! > IKE version: IKEv2 ! + Encryption algorithm: aes-cbc-256 ! + Integrityalgorithm: sha256 ! + Diffie-Hellman group: 14 ! + SA lifetime (seconds): 27000 ! + Pre-shared key: <secret> ! + UsePolicyBasedTS: False ! ! > IPsec ! + Encryption algorithm: esp-aes 256 ! + Integrity algorithm: esp-sha256-hmac ! + PFS Group: none ! + SA lifetime (seconds): 27000 -
Re: Site-to-Site IPsec VPN pfSense - Microsoft Azure VPN issues
It seems that the problem was caused by the pfSense configuration.
Initially, I used 'LAN subnet' in the phase2 configuration:
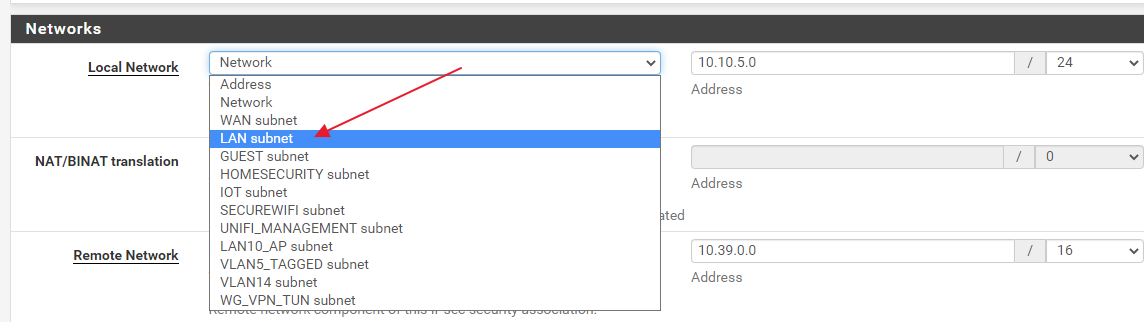
It must be "Network", like on the following picture:
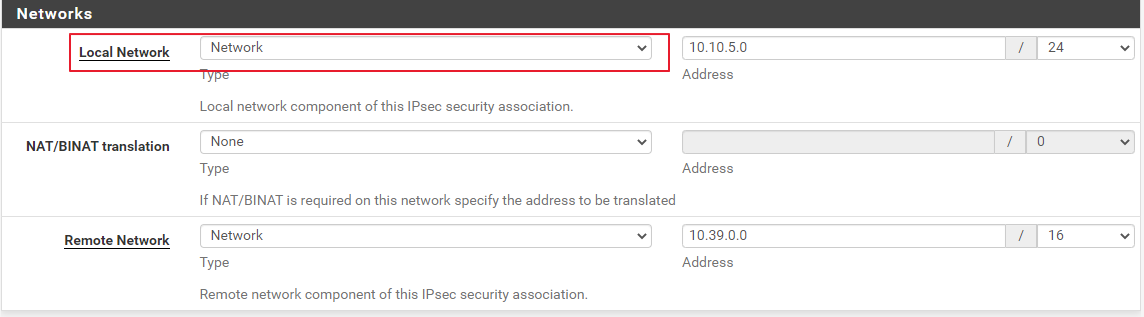
That 'LAN subnet' is a bit confusing, the subnet address is correct but it just doesn't work with some routers/services.
At least, for now, that made Azure VPN happy.
-
@lk777 I agree completely. it is confusing. The documentation says one thing but as you can clearly see choosing either one the tunnel still comes up. Would be helpful to have an info button somewhere that quickly shows the pros/cons of selecting each one.