Authenicated NTP
-
@johnpoz I'll rephrase. How can we fix this bug? :) The GUI is missing the key number field.
-
I would have to look into that RFC..
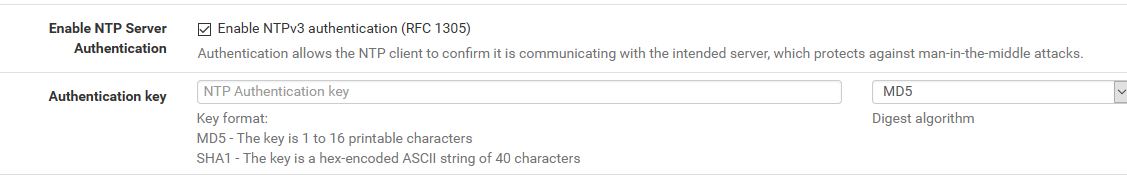
But if have discovered something that doesn't allow it to work.. Then yeah submit a bug report over at https://redmine.pfsense.org/
I would link to this thread...
Or if @jimp or maybe @stephenw10 check out this thread, and they feel its warranted they might open one..
edit: Wow you have to snail mail them or fax to get a key, how old school ;)
edit2: Without even trying to set this up, I could see another problem, what if you have different servers with different keys.. How could you setup your different servers in the gui to use different keys?
What if you want server A to use auth, and B not too? I don't see in the gui how you could set this up?
edit3: I found this over at redmine
https://redmine.pfsense.org/issues/8794You know what I am thinking is that setting is for just pfsense NTP server, and clients to auth to it.. And not as pfsense to be client and auth to servers.
notice this statement in the redmine
"pfSense NTP client still doesn't have authentication support, so I set the target version to 2.5.next"So it seems they are aware, and on their radar..
edit: I might play with this locally, just to play with it.. Never ran into the want/need to auth ntp.. But look interesting.
And btw - this seems like good enough section for this kind of discussion. Thanks for bringing it up.
-
I got authenticated NTP working. I made a diff file for those who feel adventurous.
Changes needed are in the function
system_ntp_configure()in the file/etc/inc/system.inc. The GUI doesn't support it yet, so I made the change a local variable $ntp_key. The original value was hard coded to 1, so I made that the default.--- /etc/inc/system.inc.original 2021-04-14 13:20:08.366622000 -0400 +++ /etc/inc/system.inc 2021-04-14 14:14:51.708673000 -0400 @@ -1772,6 +1772,7 @@ $driftfile = "/var/db/ntpd.drift"; $statsdir = "/var/log/ntp"; $gps_device = '/dev/gps0'; + $ntp_key = "1"; safe_mkdir($statsdir); @@ -1802,7 +1803,8 @@ /* set NTP server authentication key */ if ($config['ntpd']['serverauth'] == 'yes') { - $ntpkeyscfg = "1 " . strtoupper($config['ntpd']['serverauthalgo']) . " " . base64_decode($config['ntpd']['serverauthkey']) . "\n"; + $ntp_key = "12345"; + $ntpkeyscfg = $ntp_key . " " . strtoupper($config['ntpd']['serverauthalgo']) . " " . base64_decode($config['ntpd']['serverauthkey']) . "\n"; if (!@file_put_contents("{$g['varetc_path']}/ntp.keys", $ntpkeyscfg)) { log_error(sprintf(gettext("Could not open %s/ntp.keys for writing"), $g['varetc_path'])); return; @@ -1818,10 +1820,11 @@ if ($config['ntpd']['serverauth'] == 'yes') { $ntpcfg .= "# Authentication settings \n"; + $ntpcfg .= "enable auth \n"; $ntpcfg .= "keys /var/etc/ntp.keys \n"; - $ntpcfg .= "trustedkey 1 \n"; - $ntpcfg .= "requestkey 1 \n"; - $ntpcfg .= "controlkey 1 \n"; + $ntpcfg .= "trustedkey " . $ntp_key . " \n"; + $ntpcfg .= "requestkey " . $ntp_key . " \n"; + $ntpcfg .= "controlkey " . $ntp_key . " \n"; $ntpcfg .= "\n"; } @@ -1988,7 +1991,10 @@ } if (substr_count($config['ntpd']['noselect'], $ts)) { $ntpcfg .= ' noselect'; - } + } + if ($config['ntpd']['serverauth'] == 'yes') { + $ntpcfg .= " key " . $ntp_key . " "; + } $ntpcfg .= "\n"; } unset($ts);Before using this patch file, make sure to change the value of $ntp_key from 12345 to whatever your NTP key provider gave you (NIST in my case).
Apply patch, verify that it works:
[21.02.2-RELEASE][admin@your-sweet-pfsense-server-name]/root: ntpq -pc as remote refid st t when poll reach delay offset jitter ============================================================================== *ntp-g.nist.gov .NIST. 1 u 7 64 377 10.865 -0.019 0.738 ind assid status conf reach auth condition last_event cnt =========================================================== 1 64816 f61a yes yes ok sys.peer sys_peer 1Enjoy!
PS - Why authentication you ask?
-LamaZ
-
@lamaz said in Authenicated NTP:
PS - Why authentication you ask?
Nothing wrong with that... But run my own stratum 1 ntp server locally.. So yeah I trust it, and don't have any concerns.
While I agree this is neat shit, and could see the want/need - Your work could help them bring it to the masses faster (you would hope)
-
@johnpoz said in Authenicated NTP:
But run my own stratum 1 ntp server locally.. So yeah I trust it, and don't have any concerns.
 Much respect. Keep it local when you can.
Much respect. Keep it local when you can. -
Maybe if I get board at some point - I will send the snail mail to get access to that ntp ;)
How long did it take you to get info back? Curious.
-
@johnpoz I want to say it was like 2-3 weeks. I wasn't keeping an accurate timeline. I can tell you that you must send the initial request via snail mail. I tried faxing my initial request and never seemed to get anywhere.
Your answer will come via an email from NIST that will have you log into an HTTPS site (an Accellion appliance) to download your keys.
-
Status update. Just upgraded to 21.05. This still works pretty much as is. After upgrade I did:
cd /etc patch -u -b inc/system.inc -i /root/system.inc.ntp-auth.patchThe -b will create a backup file (system.inc.original) in case anything goes wrong. Then modify the value $ntpkey in your /etc/inc/system.inc, and restart the ntp service.
Done.
-
Just upgraded to 22.01/2.6.0 and happy to say that this patch still works.
At first I got excited when I read on the release notes that maybe this would get added:
https://docs.netgate.com/pfsense/en/latest/releases/22-01_2-6-0.html
“ Added: Support SHA-256 hash NTP authentication #12213” -
@johnpoz Thanks for the information on this
-
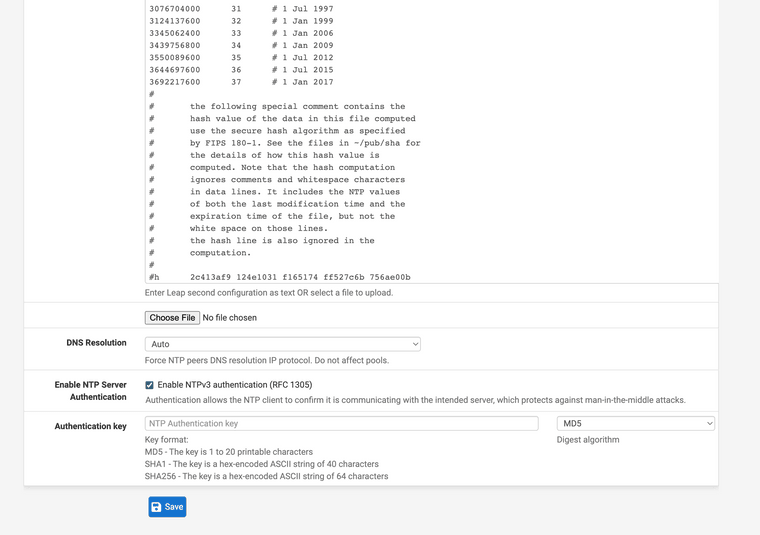
Just upgraded to 23.01-RELEASE. The patch above doesn't work at the moment.
After restarting the NTP daemon, something has changed and now /etc/inc/system.inc is overwritten every time NTP is (re)started. I haven't figured out what changed and where I can write permanent updates tofunction system_ntp_configure().I figured out the issue. Version 23.01 changed the syntax for calling GUI fields. Here is a patch for 23.01. Don't forget to change the ntp_key value from 12345 to your NIST provided key.
system.inc.ntp-auth.23.01.patch
--- /etc/inc/system.inc.orig.23.01 2023-02-20 11:07:17.000586000 -0500 +++ /etc/inc/system.inc 2023-02-20 20:05:49.538823000 -0500 @@ -1828,6 +1828,7 @@ $driftfile = "/var/db/ntpd.drift"; $statsdir = "/var/log/ntp"; $gps_device = '/dev/gps0'; + $ntp_key = "1"; safe_mkdir($statsdir); @@ -1857,7 +1858,8 @@ /* set NTP server authentication key */ if (config_get_path('ntpd/serverauth') == 'yes') { - $ntpkeyscfg = "1 " . strtoupper(config_get_path('ntpd/serverauthalgo')) . " " . base64_decode(config_get_path('ntpd/serverauthkey')) . "\n"; + $ntp_key = "12345"; + $ntpkeyscfg = $ntp_key . " " . strtoupper(config_get_path('ntpd/serverauthalgo')) . " " . base64_decode(config_get_path('ntpd/serverauthkey')) . "\n"; if (!@file_put_contents("{$g['varetc_path']}/ntp.keys", $ntpkeyscfg)) { log_error(sprintf(gettext("Could not open %s/ntp.keys for writing"), g_get('varetc_path'))); return; @@ -1874,9 +1876,9 @@ if (config_get_path('ntpd/serverauth') == 'yes') { $ntpcfg .= "# Authentication settings \n"; $ntpcfg .= "keys /var/etc/ntp.keys \n"; - $ntpcfg .= "trustedkey 1 \n"; - $ntpcfg .= "requestkey 1 \n"; - $ntpcfg .= "controlkey 1 \n"; + $ntpcfg .= "trustedkey " . $ntp_key . " \n"; + $ntpcfg .= "requestkey " . $ntp_key . " \n"; + $ntpcfg .= "controlkey " . $ntp_key . " \n"; $ntpcfg .= "\n"; } @@ -2049,6 +2051,9 @@ } if (substr_count(config_get_path('ntpd/noselect'), $ts)) { $ntpcfg .= ' noselect'; + } + if (config_get_path('ntpd/serverauth') == 'yes') { + $ntpcfg .= " key " . $ntp_key . " "; } $ntpcfg .= "\n"; }And the results showing valid auth
[23.01-RELEASE][admin@your-sweet-pfsense-server-name]/root: ntpq -pc as remote refid st t when poll reach delay offset jitter ============================================================================== *ntp-g.nist.gov .NIST. 1 u 68 64 377 5.806 -1.114 1.331 ind assid status conf reach auth condition last_event cnt =========================================================== 1 39518 f61a yes yes ok sys.peer sys_peer 1-LamaZ
-
@johnpoz you can fax them also I just did, I want to test this, I have seen time jumps during cyber security classes in the past. 10-15 min jumps. Maybe this will fix it again with the use of my firewall I have not seen that in a while. Still I want to check it out. "Users who wish to use this service should send a letter to NIST using the US mail or FAX machine (e-mail is not acceptable)."
-
@lamaz were you ever in the past having issues that's with time jumps 10-15 mins around noonish?
-
For one device in the network it will be perhaps acceptable, but if you one and only device is the time server for the entire network and "something" occurs, you have to do the hardcore "aftermath" job to count all different time stamps
for finding something out! If you now have one good time source and offer it to the entire network, they (all devices)
have the same time stamp and let us name it "problems"
can be faster and more easy able to find out. A good time
sync server may be good for any kind of scenario or problems have to be find out. -
@dobby_ I have the firewall serving all time now, I am going to attempt the authenticated stratum NTP servers, the only problem is I might not have the pool of 4-5 servers to do the offsets time math equations automatically anymore as the authenticated server comes with only key for access. Prior to the pool I noticed slight time jumps in the past during my breaks or quizes. Yes NTP is an older protocol and does have some bugs I have noticed. I only ever spotted the jumps with a manual clock, and yes it's not all of them. Again during a test, or quiz a jump of 15 mins is a huge amount of time, and something was causing this deleting time to rush the tests, only reason was to cause a stressful environment. Again, these are problems that the multi pool solved. Will authenticated servers come with a pool? That I hope to find out soon. My current pool and time is set up with the slowed earth leap second offsets that the scientific community has listed for use. I also hope that still works. I have very precise time. I flat don't like it messed with anymore. Precision is what makes the difference. Logs is what tracks unethical behavior so it can be reported. It's unethical to move time like that during someone's break and or during a quiz. I am waiting for my letter in the mail so I can learn about authenticated NTP it, I hope it comes with a pool also.
-
@dobby_ the pools work very well as "NTP will only sync if a majority of the servers agree on the time. For best results you should configure between 3 and 5 servers (NTP support pages recommend at least 4 or 5), or a pool. If only one server is configured, it will be believed, and if 2 servers are configured and they disagree, neither will be believed." if 4 are used if one moves a large amount the other 3 have to agree if they don't, the time that is served never changes, if they are still off by a couple seconds between servers it balances them with an equation. It's a really good solution, as abuse is pointed to only one server so it doesn't effect the pool. You have to NAT NTP to the firewall for everything that wants time. I have it inverted anything that doesn't request my firewall for NTP gets NAT(ed) to it without knowing, that's when the abuse stopped forever. They now required 3 out of the 4 time servers to agree to on what is served. PfSense is amazing software when you get into it. NIST servers fixed everything for me with the jumps. I can't wait to test out authenticated services.
(I need my key to make it more secure)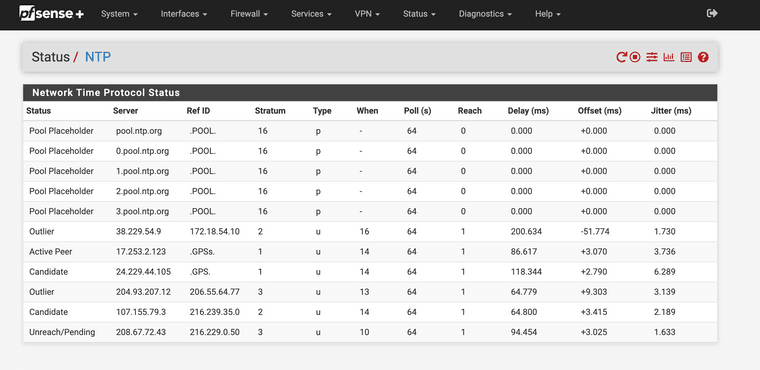
(Pool Running and moving to stratum 1)
(Leap seconds running successfully)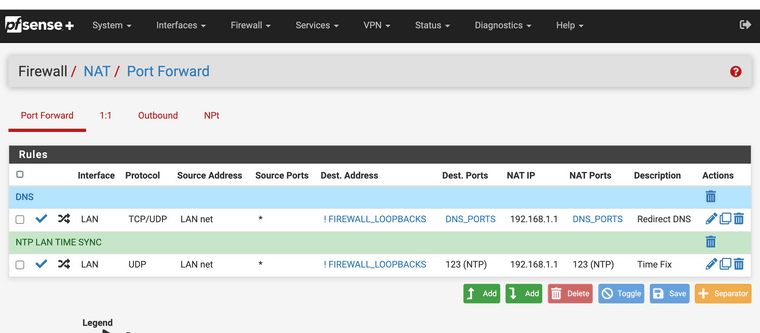
(Netgate runs my clocks down to the nano second now) -
Auth. NTP servers give you a bit more safe feeling, because they are knowing how many users are using that servers!
Its not like "tomorrow 15 million users" begin using that server and it is going down or responding slower, the delay is growing or the server is not any more responding.I use a mix of more then one NTP and also want to let it grow. At first I use NTP servers pool over WAN they are
connected to or based on an atomic clock. Might be the
best in my eyes. I have a fallback line over LTE for a
second chance to get the time over the internet.
The LTE modem has also a GPS antenna connected
so I got one more time source.The next way to set up was a miniCPIe GPS (only) card
inside of the pfSense and all is fine now.- wired internet
- wireless internet
- gps only
May be that auth. NTP server will be an option on top of all, because they know then the amount of users exactly
and can set up another one if the responds time goes down or will be lower and not anymore so fast. -
@dobby_ in the early 2000s we use to have to set the DTE and DCE clock rates for the network routers to work correctly, if they had no clock rates set they would not function. Imagine something like a Ciena or Juniper backbone system today, how perfectly in time they have to be to support supernet city to city communications. Time is amazing stuff as it is time of use specific.
-
@jonathanlee said in Authenicated NTP:
@lamaz were you ever in the past having issues that's with time jumps 10-15 mins around noonish?
Thankfully I've never seen this behavior. It would have driven me mad as well when taking the OSCP exam and I was down to the wire.
I haven't been using multiple servers.
Maybe I shouldI'll grow my list. There are only 4 servers that support authenticated NTP according to https://tf.nist.gov/tf-cgi/servers.cgi.Nice touch ensuring that no local hosts are trying to skirt around your NTP. I do the same thing with both NTP and DNS. Local DNS requests get re-mapped to my pfSense DNS which then does it over TLS. I watch my WAN and ensure no traffic is going out on UDP port 53 :).
EDIT: I did it. Thanks @JonathanLee for the informative posts on NTP. I learned something new today.
[23.01-RELEASE][admin@your-sweet-pfsense-server-name]/root: ntpq -pc as remote refid st t when poll reach delay offset jitter ============================================================================== *ntp-g.nist.gov .NIST. 1 u 62 64 3 5.755 +0.244 1.500 +ntp-c.colorado. .NIST. 1 u 65 64 3 44.843 +0.668 1.292 +ntp-wwv.nist.go .NIST. 1 u 64 64 3 45.135 -1.426 1.312 +ntp-b.nist.gov .NIST. 1 u 66 64 3 42.373 -1.416 1.486 ind assid status conf reach auth condition last_event cnt =========================================================== 1 30934 f61a yes yes ok sys.peer sys_peer 1 2 30935 f414 yes yes ok candidate reachable 1 3 30936 f414 yes yes ok candidate reachable 1 4 30937 f41a yes yes ok candidate sys_peer 1Full tinfoil hat.
-LamaZ
-
Folks,
In an effort to facilitate checking the status of authenticated NTP, I've added some columns to the NTP Status page to parse the output of
ntpq -c associationsas defined in the ntpq Command spec. Let me know what you folks think.The last 3 columns have been added (AssocID, Status Word, Auth). I only added those 3 to the GUI, but I added the plumbing for the most of the fields in case someone wanted to display them as well.
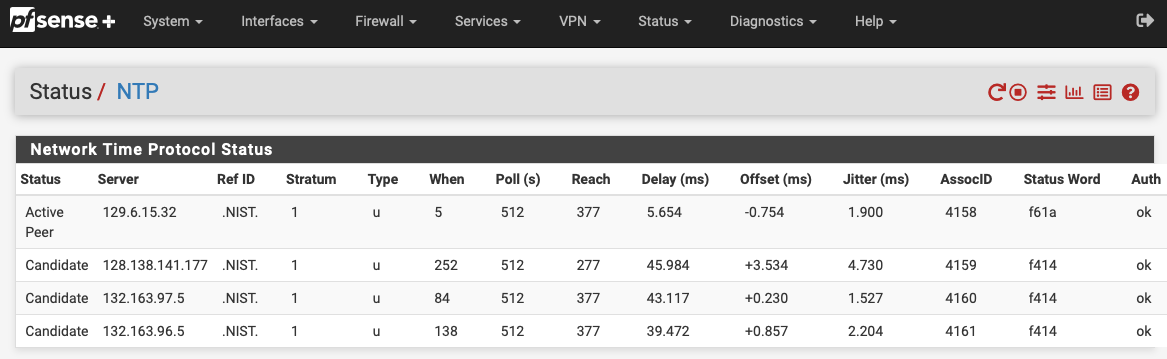
Patch file provided if you want to try it out. It worked for me :)
status_ntpd.php.auth.patchPS - I'm trying to unlock my Redline account to add this as full fledged feature request. Somehow I'm not getting the password reset email at the moment.
-LamaZ