Use a virtual Network in PFsense to redirect packages to device in another network
-
I'm using PFsense and i have this situation:
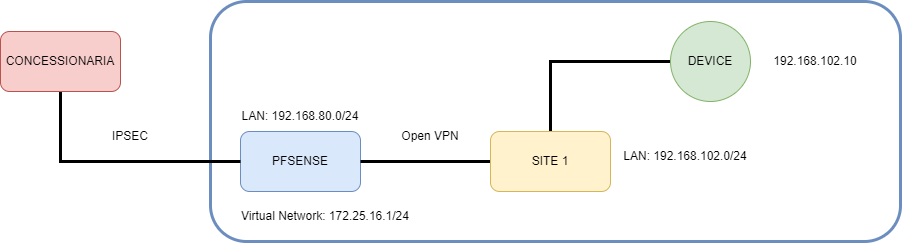
I have a PFsense already connected with "Site1" through OpenVPN. I can acess the "Device" normally in Pfsense network. I can make chances only in PFSense.
But now i have to make another VPN with "Concessionaria" but this network ask-me address in another range (172.25.16.0/24). Basically, the "Concessionaria" wants access "Device" through Pfsense using the address 172.25.16.5 (so, it's a virtual IP).
What i try:
In PFSense -> Firewal -> Virtual IPs -> Add IP Alias
Interface: LAN Address / 172.25.16.1/24Then i could make a IPSEC Túnnel using this address network in Phase2 with "Concessinaria". They can ping 172.25.16.1 normally.
So, i create a NAT 1:1 with these settings:
Interface:WAN
External Subnet IP: 172.25.16.5 (virtual address of "Device")
Internal IP: Any
Destination: 192.168.102.10
NAT Reflection: Enable
But the concessionária could not ping this IP. Missing some small detail ....
Any Ideas?
-
@felipefonsecabh
Don't configure NAT 1:1 for IPSec connections! IPSec provides its own NAT in the phase 2, which you should use here. -
Yup, you can't apply NAT to policy based IPSec like that. And that rule on the WAN anyway so can never match.
You need to configure NAT in the phase 2 as @viragomann said.
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/phase-2-nat.htmlIf they only need to access that one IP then you might be able to use a P2 with only that single IP in it. However they might not allow that and only bring up a P2 for the full 172.25.16.0/24 subnet. In that case you would need to translate 172.25.16.0:192.168.102.0 and that might be a problem because the 'device' will appear to be at 172.25.16.10 not .5.
Additionally the router at Site 1 will need a route back to the source IP of whatever the Concessionaria is using. If you cannot add routes at Site 1 you will need to outbound NAT that across the OpenVPN tunnel so Site 1 can reply.
Steve
-
@stephenw10 in my case the concessionaria wants access only 2 devices in Site1 through pfsense. Not necessary translate all network.
So, how woluld i configure phase 2 for this case?
And how would i make this outbond rule? Assuming for example, concessionaria network is 192.168.15.0/24?
In Outbound -> NAT Entry, i put :
Source: 192.168.15./24
Destination: 172.25.16.5And the fileds Address and PortRange in "Translation"?
Thanks a lot!
-
Can you have 2 Phase 2 policies over the IPSec tunnel? If so you can have one for each of the hosts at Site 1. If they only allow 1 Phase 2 it must cover the full Site 1 subnet and that means the last octet in the address must be the same. So: 172.25.16.10:192.168.102.10 for example.
In the outbound NAT rule the NAT address will be the pfSense OpenVPN address and the port will be 'any', you are not translating the ports.
I assume you cannot add routes at Site 1 then?
-
@stephenw10 yes, i can't add routes in Site1 and i could configure 2 Phase 2 policies.
-
Ah, in that case you should be able to do it exactly as they want. Just add a P2 for each device with the translation they are asking for.
If you can add a static route at Site 1 (probably in the OpenVPN config) to the Concessionaria subnet then you won't need an outbound NAT rule in pfSense.
That's a cleaner approach. the target devices will see the real source IP etc.Steve
-
@stephenw10 said in Use a virtual Network in PFsense to redirect packages to device in another network:
Can you have 2 Phase 2 policies over the IPSec tunnel? If so you can have one for each of the hosts at Site 1. If they only allow 1 Phase 2 it must cover the full Site 1 subnet and that means the last octet in the address must be the same. So: 172.25.16.10:192.168.102.10 for example.
In the outbound NAT rule the NAT address will be the pfSense OpenVPN address and the port will be 'any', you are not translating the ports.
I assume you cannot add routes at Site 1 then?
Sorry @stephenw10 , but i don't understand what IP or Network i have to put in Phase 2. The "Concessionaria" must have see devices with virtual IP (172.25.16.X) . In this case the outbound configuration above is correct?
-
The phase 2 entry for each device should use the IP address they specify in the 'NAT/BINAT translation' and the real address in the 'Local Network' field.
See: https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/phase-2-nat.html#example
You do not need an outbound NAT rule if you can add the route to the OpenVPN tunnel at Site1.
Steve