Firewall rule: allow only internet
-
Hi,
I'm trying to setup a firewall rule that basically says: Allow traffic to any IPv6 that's not on my network. The challange is: I have to consider changing prefixes from my ISP :(In this ticket I understood, that this could be achieved by matching "! ::/56":
https://redmine.pfsense.org/issues/6626While this seams to work when configuring this on my VLANs, this doesn't work when configuring this for my IPsec or OpenVPN instance. It seams like this rule allows IPv6 traffic to everywhere.
Am I understanding something incorrectly? How could such a rule be accomplished?Thanks
-
@b_chris said in Firewall rule: allow only internet:
The challange is: I have to consider changing prefixes from my ISP :(
Do you have Do not allow PD/Address release checked?
-
@jknott
I can't find this option in my settings. Maybe because I have to use PPPoE to connect?
Either way: I have the official conformation from my ISP that (at least at the moment) they don't want to support static prefixes for end users :( So I'm pretty sure, that they intentionally hand out different prefixes after reconnecting -
On 2.6.0, it's located on the WAN page. It's elsewhere in the version that comes with Netgate gear, but I don't remember where. This isn't "static" addresses. It's still DHCPv6, but that setting, if honored, prevents the prefix from changing.
-
@jknott
I'm currently on pfSense+ 21.05.
In Interfaces->WAN I have no according option. Could be because of PPPoE (vs. "plain" DHCPv6) -
Then it's in the other location. Perhaps someone else can say where it is. I don't have that version here. I also don't use PPPoE, but I doubt that's the issue, as it's only used to establish the connection to your ISP.
When I started using pfSense, that option wasn't even available. If I did nothing more that disconnect/reconnect the WAN cable, I'd wind up with another prefix. However, since it became available, my prefix has been rock solid, surviving replacement of both my modem and the computer I run pfSense on. I've had the same prefix for almost 4 years, IIRC.
-
The option you're looking for is in System > Advanced > Networking. The option is "Do not allow PD/address Release". Checking the option should prevent dhcp6c from sending a release when the device is rebooting or the interface is reloading (unless you click the Release button in Status > Interfaces)
However, some ISPs don't care and will give you a new prefix anyway (mine does this; I get a new prefix every time my router reboots).
-
@b_chris said in Firewall rule: allow only internet:
I'm currently on pfSense+ 21.05.
21.05?
You should upgrade. There were two patch updates (one for specific issues) as well as two full updates since that was released.
-
I'm using tag/tagged to do something like this. For my LAN interfaces I have two groups, trusted and untrusted. An "in" floating rule matches untrusted and tags with "untrusted". An out floating rule then uses tagged to reject all marked untrusted packets from both trusted and untrusted interfaces. That works for ipv4 and ipv6. I didn't want to have to enter any addresses just interfaces.
-
@brukster
Could you post a screenshot of your rule(s) to do this? Thanks@rcoleman-netgate
I mean 22.05... I'm not the person hunting for uptime counters ;)Could someone explain, why the "! ::/56" rule works for my VLAN interfaces but not for VPNs?
-
Ok, I have 5 LAN interfaces in 2 groups. GUEST, IOT, and OBI (voip) interface are untrusted and I want to exclude them from any LAN interface, including each other. That leaves only the WAN interface for them to use.
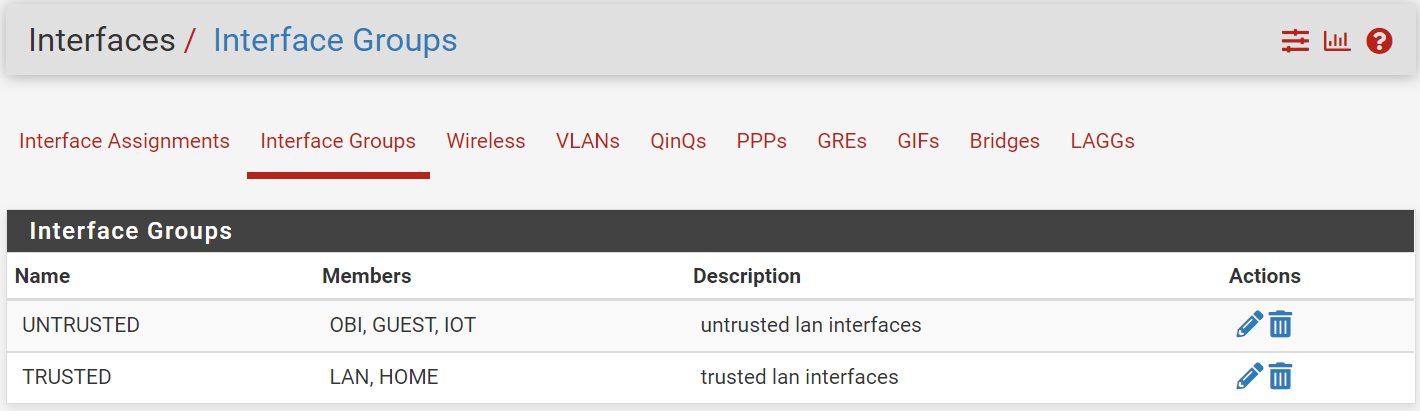
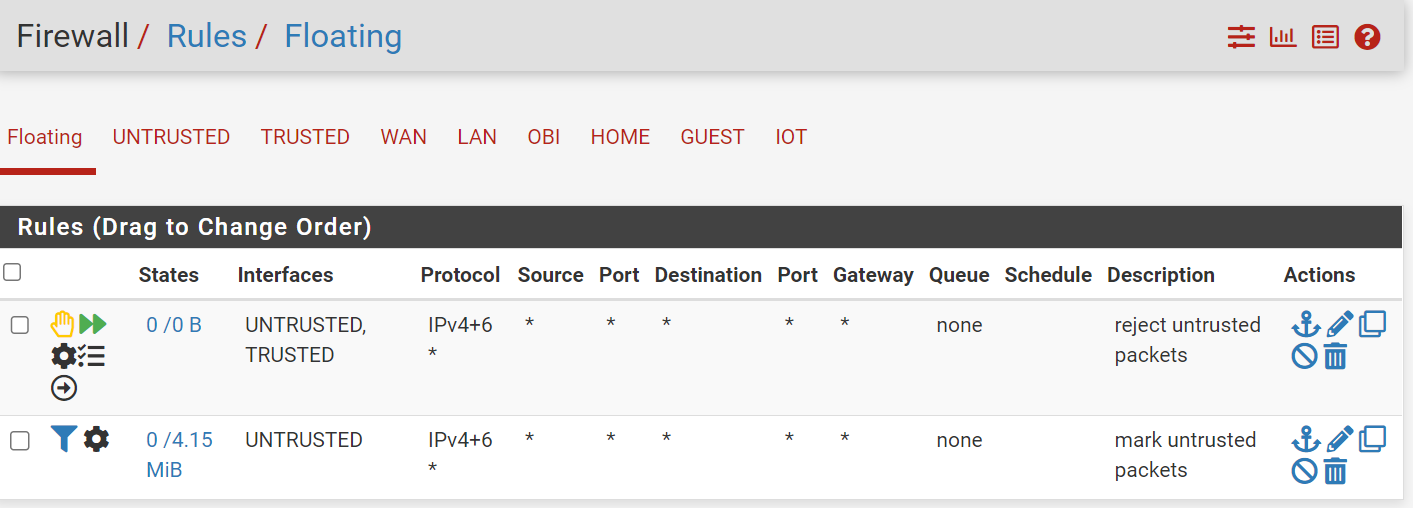
The bottom in rule matches interfaces in the UNTRUSTED group and tags the connection (packet?) with "untrusted".
The top outrule rejects all connections marked as UNTRUSTED from any LAN interface, i.e. TRUSTED + UNTRUSTED.
-
@brukster
I tried to replicate what you did with a variation and I failed ;) I'm not sure why...My approach: Tag everything from trusted Interfaces; allow trusted traffic to leave to WAN
Idea: I'd like to stick to the default deny logic and only allow specific traffic.I tried the following rules (test with only VPNs to minimize possible negativ effects...):

That resulted in the the following:
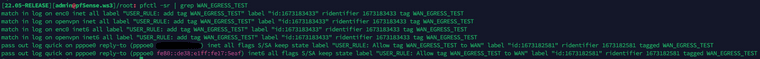
In the firewall log I see only the tagging (first rule) but no match for the second rule.
I not sure what I'm doing wrong. Either the out-logic is not working as I assume it does or the processing order is not as expected?Could someone please point me into the right direction?
Thanks -
@b_chris If you have allowed the VPN traffic earlier to pass the input rules, then it should make it to the out rule. If a default reject rule in input dropped the traffic it will never make it to the output side.
Try disabling the floating in tag rule. Add a pass rule in each of IPsec and OpenVPN that also tags with WAN_EGRESS_TEST.
Then add another floating out rule after the current out rule. Have that rule reject all tagged WAN_EGRESS_TEST from all other interfaces.
-
@brukster
Thank you! I'll test this out