No WAN access from inside LANs...
-
@njaimo ....ahh... OK, so I've switched the laptop to the IOT network, 192.168.1.1, and got assigned a DCHP lease in pfSense of 192.168.1.18, and confirmed it in the laptop connection settings.
Interestingly, I can ping the switch, but I cannot ping the other PC in the network...
...nor can I ping 8.8.8.8
-
@njaimo You need to check the switch, are the ports configured correctly?
-
@jarhead yeah, I have reset the switch to factory settings, and everything else in that network, including this PC I am typing on now work fine. The networks I was on before the DMZ, did not have any switches, and still could not ping 8.8.8.8
I can also ping the two wireless access points 192.168.1.245 and 246, but cannot ping this PC at 192.168.1.100
-
@njaimo here are th efirewall rules for my IOT net, "HPDesk1_OIT is this computer I am typing on, but the first rule allows anything to go out.
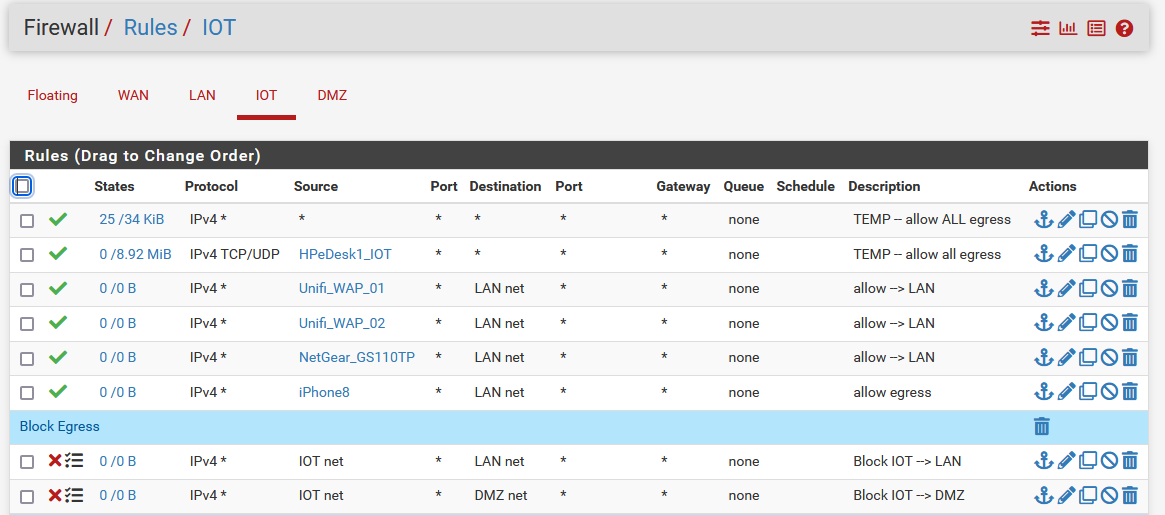
-
...starting to think the issue may be in the laptop ?... ping does not use TCP/IP, I think, but not sure how it is receiving its DHCP lease from the firewall... then again, not sure why I can ping the Unifi access points and the switch, but not this PC the access points have a PoE wired connection to a port in the switch, so it seems ping commands are getting out of the switch
-
@njaimo Starting to think that?? Yeah, my first post said not to look at the firewall.
Plug the laptop directly into the lan port and see if you can get out from there.
If all you're doing is ping tests, did you disable the firewall in the laptop? -
Ok, got some time until the next football game so I can actually put some effort into this...
So you say you defaulted the switch. How are you separating all these networks on it?
What ports have you been using when you switch networks? -
@njaimo said in No WAN access from inside LANs...:
Is there some reason pfSense is blocking this particular machine ?
I happen to have a T43 here, in addition to my E520, with openSUSE Linux on both. They work fine with pfSense, just like every other device I have. Given you can reach the LAN, it makes me wonder if you have the correct info from DHCP. What does ifconfig show? What happens if you use a static config.
-
@njaimo said in No WAN access from inside LANs...:
ping does not use TCP/IP
It uses ICMP over IP.
BTW, that IBM partition you mentioned earlier would likely contain Windows and some drivers, etc. for the computer.
-
@jknott said in No WAN access from inside LANs...:
What does ifconfig show?
I forgot you might not have that command available, as it's been deprecated. I had to add it to openSUSE. If not, you can use ip address to show the address assigned to that computer and ip route, to show the default route.
-
...sorry guys, of course when I left for a bit is when you were off football... :)
I've had the laptop sitting in a closet for years, so thought maybe the internal battery was dead and causing some troubles, so I just took it apart and checked the coin battery, and indeed it is at 1.3 volts instead of the 3v it is supposed to be at. Unfortunately I do not have a replacement right now. So put it all back and just turned it on, and of course all the BIOS setting have to be checked now, but that tell me that before the CMOS had been keeping up, so the battery was not the issue.
Give me a few minutes to check what happens when I plug directly into my ISP modem, without a firewall or router. ...be back shortly...
-
OK, bad news, when connected directly to my ISP modem, I do get out to the internet, ping 8.8.8.8 works, and YouTube on Firefox works just fine. So it seems my issues are with the firewall probably after all ?...
So in summary I have 3 networks, LAN (with switch A, and one PC), IOT (with switch B, one PC, 2 access points), and DMZ (no switch, no PCs). LAN -- 192.168.2.1, IOT -- 192.168.1.1, DMZ 192.168.4.1 I have DHCP on all 3 set up on pfSense, and pfSense shows the DHCP leases and the IPs match those shown on the laptop Debian networking app settings, so clearly the laptop is talking to the firewall DHCP server. It also appears to be able to get NTP updates from somewhere when it boots.
When connected to either LAN, or IOT, I can ping the switch, and the wireless access points, but not the PC on IOT net. Have not tried the LAN PC as it is in another room.
When in DMZ, where there is no switch, I still cannot ping the gateway in pfSense. Given this, I do not think the issue is with the switches, though I cannot explain why I can ping the switch, but not the PC on the same net, as the traffic goes from the laptop, to the switch, and then out to the PC, unless this has to do with DNS and pfSense ?
-
just rebooted pfSense, nothing changed
-
I previously asked you to show what the ip address and route are. Those may tell us something.
BTW, that coin battery in my T43 is bad too. It's too much trouble to replace, so I live with it.
-
Nope those are all standard log entries that appear at each boot. Try rebooting and check the new entries created.
Steve
-
@jknott ...sorry forgot to address your question. The info provided by the Debian network config app is the same as I have in teh DHCP in pfSense. i.e. while in the DMZ net (i.e. no switch) the IP is 192.168.4.11, 255.255.255.0, DNS 192.168.4.1, gateway 192.168.4.1, just as it should be. Or do I still need to look elsewhere ?
I just looked for the batteries in Amazon, 5.79 CAD (I'm in Canada), and while it took several screws to get to, I was able to undo and put back together in about half an hour.
https://www.amazon.ca/Compatible-CR2032-Replacement-Battery-Thinkpad/dp/B08252SSGD -
So I just ran some experiments that lead me to believe pfSense is blocking my laptop from entering the LAN, IOT and DMZ interfaces, and thus not allowing it to reach the WAN interface.
Using the PC I have on the LAN net, which has rules to allow access to the IOT and DMZ nets I was able to ping all devices, including the 3 pfsense interfacegateways, except for the PC on the IOT net, and the laptop currently connected to the DMZ net. I believe it is normal/standard for PC-to-PC ping not to work...? which explains why I cannot ping PC from the laptop while on the same net.
In order for the above to happen, the traffic had to go to the LAN switch, then the firewall, and down the other nets, and it worked fine.
Then, I connected the laptop to the same LAN net, got a DHCP lease fine, and then tried to repeat the above, but was completely unable to ping anything outside the LAN net, except for the switch on the LAN net.
This to me tells me that the traffic from my laptop is unable to enter the firewall, being blocked by pfSense. Also it would seem both switches are working fine. Actually, we can eliminate teh switches all together, because when I connect the laptop directly to the DMZ interface, where there is no switch at all, I still cannot ping the interface gateway, so the pring "request" is being blocked outright by pfSense, and I cannot get access to the internet.
So is it possible that at some point early on when I first tried to connect the laptop to the my nets, that pfSense decided the laptop was "persona non-grata" and then wrote its MAC address in a database used to block access to the interfaces on the firewall ?
-
@njaimo said in No WAN access from inside LANs...:
that pfSense decided the laptop was "persona non-grata" and then wrote its MAC address in a database used to block access to the interfaces on the firewall ?
No.. are you running a captive portal - if so then you could block a mac..
Does the laptop get a IP from pfsense dhcp server? Are you running static arp in the dhcp server? do you have anything set for deny unknowns or the like in dhcp server?
pfsenes doesn't have a db of macs that it just magically says not going to talk to this guy ;)
-
@johnpoz Thanks for the tips !
not running captive portal, but do have Static ARP option checked on the DHCP Server service page on all 3 interfaces, though not sure what I did, nor what it does.... should I uncheck it ?
..?
-
@njaimo said in No WAN access from inside LANs...:
though not sure what I did, nor what it does....
Then why would you of checked it?
Static as it clearly states - "Only the machines listed below will be able to communicate with the firewall on this interface."
Ie the ones you had created reservations for.. in the static mappings section at the bottom of the dhcp server settings page.
Yes you should uncheck using static arp - unless you clear on what it does and why you would want to use it ;)